So, we will try to hide from the user's eyes in the manager windows tasks. The way in which we will achieve this is extremely simple with respect to those that are based on intercepting nuclear (often undocumented) functions and on creating your own drivers.
The essence of the method: Search for the Task Manager window -\u003e Search for a child window (list) in it containing the names of all processes -\u003e Delete our process from the list.
As you can see, no manipulations will be carried out with our process: it worked as it did and will work for itself. Since the standard private windows userAs a rule, does not use any other tools to view the running processes on his computer, this will only play into our favor. The process will not be detected in most cases.
What was used for research:
1) Spy ++ from Microsoft (to study the hierarchy of child windows Task Manager)
2) OllyDBG to view the functions used by the dispatcher to get a snapshot of processes.
3) Actually, myself taskmng.exe(Task Manager)
For writing code, we will use the Delphi environment. Rather, Delphi will be more convenient in our case than C ++. But this is only my humble opinion.
Well, first of all we will try to find out what the list of processes is and how it works. From a half-view, it is clear that this is a normal window of the SysListView32 class (list), which is updated at a frequency of 2 frames per second (every 0.5 seconds). We look at the hierarchy of windows:
As you can see, the list of processes, in fact, is the usual window of the class “SysListView32”, which is a child of the “Processes” window (tab), which is also a child of the main window of the Task Manager. We have only a double level of nesting. In addition, the list has one child window of the “SysHeader32” class, which, as it is not difficult to guess, is the title (field marker) for the list of processes.
Since we have a regular list, we have a whole set of macros at our disposal to manage its contents. Their diversity, at first glance, delights. But many of them work only from the parent process, that is, in order for us to use them, it will be necessary to imitate, as if they are executed in the parent process. But not everyone has such a property, in particular, the ListView_DeleteItem macro command, which deletes an item from the list-window (the “SysListView32” class).
We will use it in the process. of our applications. This function is the second parameter gets the index of the item to be deleted.
Now we need to somehow figure out what kind of index the element has with the label of the hidden process in the task manager. To do this, we need to somehow pull out all the elements from the list of processes in the task manager (labels with the names of the processes) and consistently compare them with the name of the process that we want to hide.
Using macro commands of the ListView_GetItemText type, our actions would be approximately as follows:
1) Memory allocation in task manager process (VirtualAllocEx)
2) Sending the Task Manager child window a message LVM_GETITEMTEXT (SendMessage)
3) Write to the selected memory area of the Task Manager information about the item in the list (WriteProcessMemory)
4) Reading from the dispatcher’s memory the information that interests us about the process (ReadProcessMemory)
Using this method, you can easily “shoot yourself in the foot” by counting the offset bytes from the beginning of the various structures used in the code. Also, this method will be quite difficult for those who are not particularly deep in WinAPI, so we immediately remove it to the side. In other matters, find implementation of this method on the Internet will not be difficult. Instead, I will suggest that you form your own list of processes, and already focusing on it, look for the cherished process index in the Task Manager process list.
Microsoft decided not to worry about the tool called Task Manager, and used the usual WinAPI functions to get all the processes in the system. Superficially look taskmng.exe under the debugger:
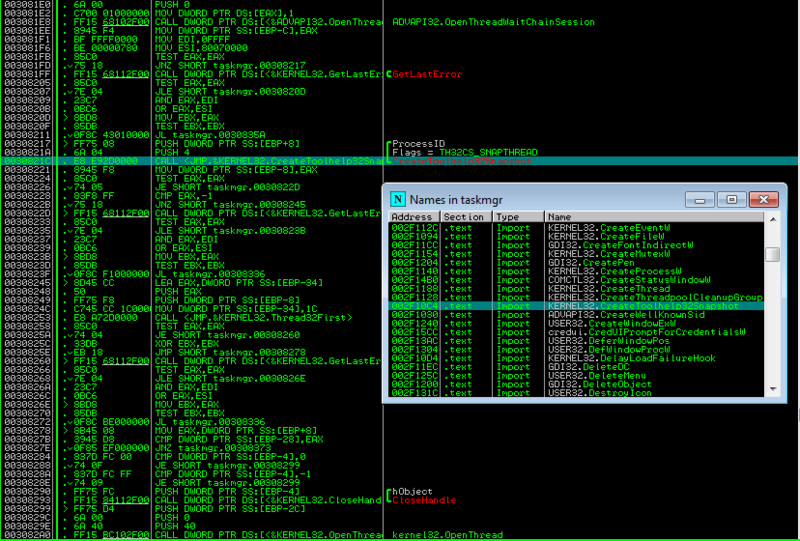
We see the use of the WinAPI CreateToolHelp32SnapShot function.
Everyone knows that “this function can be used not only to obtain a snapshot of processes, but also process flows or modules, for example. But in this case it is unlikely. They will hardly use something in the enumerator of processes (EnumProcesses).
We stopped at the fact that we want to create our own list of processes and look for our process in it. To do this, use the function found in the debugger. If we open the task manager on the Processes tab, we note that all processes are sorted alphabetically for easy retrieval. Therefore, we need to get a list of names of all processes in the system. and sort them by increasing alphabetically. Let's start writing code in Delphi.
To begin with, we will create a demo window application with two timers: the first one will reshape the list with processes with the same frequency with which the Windows Task Manager does it (every two seconds); the second one will be triggered 1000 times per second and will serve to track the update of the list of processes in the manager and, therefore, the appearance of our hidden process. Also add a button to the form.
Code:
var ind integer; h: Thandle; last_c: integer; procedure UpdateList (); var th: THandle; entry: PROCESSENTRY32; b: boolean; i, new_ind: integer; plist: TStringList; begin // Process list plist: = TStringList.Create; // Create a list of processes th: = CreateToolHelp32SnapShot (TH32CS_SNAPPROCESS, 0); entry.dwSize: = sizeof (PROCESSENTRY32); b: = Process32First (th, entry); while (b) do begin plist.Add (entry.szExeFile); b: = Process32Next (th, entry); end; // Sort it so that the indexes of the elements // match those in the task manager plist.Sort; last_c: = plist.Count; // Search the index of our process "explorer.exe" for i: = 1 to plist.Count-1 do if (LowerCase (plist [i]) = "explorer.exe") then new_ind: = i-1; // Remove an object from the list if (new_ind<>ind) then ListView_DeleteItem (h, ind); ind: = new_ind; plist.Free; // Start the update tracking timer in the process list if (Form1.Timer2.Enabled = false) then Form1.Timer2.Enabled: = true; end; procedure TForm1.HideProcessButton (Sender: TObject); begin // Look for the child window of the class "SysListView32" h: = FindWindow (nil, "Windows Task Manager"); h: = FindWindowEx (h, 0, nil, "Processes"); h: = FindWindowEx (h, 0, "SysListView32", nil); // Start the process list re-formation timer Timer1.Enabled: = true; end; procedure TForm1.Timer1Timer (Sender: TObject); begin UpdateList (); end; procedure TForm1.Timer2Timer (Sender: TObject); begin // Search for changes in the list if (ListView_GetItemCount (h)\u003e last_c) then ListView_DeleteItem (h, ind); last_c: = ListView_GetItemCount (h); end;That's the whole code.
We hide, for example, in the Task Manager the process of the Task Manager itself:
Here it is:

And by clicking on the "Hide process" button, the process disappears from the list:
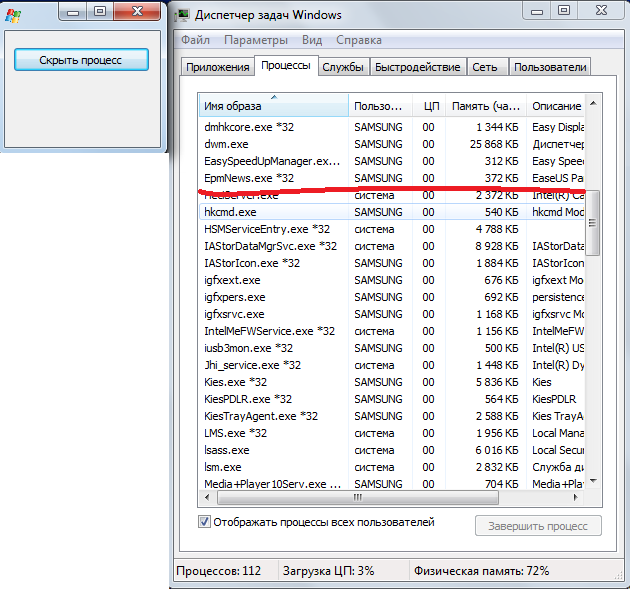
All traces of presence in the system are erased, and he calmly runs as usual somewhere in the depths of the processor :)
Outro
Well, I think this way deserves to exist, though it requires minor improvements. Yes, of course, it cannot be used to hide the process from the system itself, but hiding in the standard Windows tool, which is used by the lion’s share of all users, is not bad either.I hope I managed to interest you at least a little bit with this topic.
See you later! And may the power of anonymity be with you ...
Tags:
Programs that are active on the computer can always be viewed by opening the Task Manager. However, sometimes it may happen that you need to make the execution of a program invisible. If you also have such a desire, you will probably begin to look for an answer to the question of how to hide the process in the Windows Task Manager.
Learn how to hide the Windows Task Manager process.
Of course, the anonymity of the execution of some programs will allow to monitor those who are overly cluttered personal Computer. This is especially important when multiple users have access to a PC.
Also, the desire to hide the process arises among those who install their own program and strive to ensure that advanced users cannot in simple ways reveal her presence.
Any program execution is a process that needs a certain part of the RAM. Processes are divided into:
- systemic;
- anonymous;
- custom;
- related to the internet.
It is not recommended for those who do not have practical experience and the necessary technical knowledge to interfere with system processes, since such an unwise introduction can provoke extremely undesirable consequences. One of these consequences may be the failure of a subsequent launch. operating system.
It is possible to learn how to hide any user programs, and you will not need to make great efforts, just read our recommendations carefully. We draw your attention to the fact that even an advanced engineer who is unaware of your “creative deeds” will not notice the “left” process.
Action algorithm
If you needed to hide a software application, you first need to figure out whether it is simple, whether it starts up additional processes that can simply issue it, no matter how you try to hide the program.
If, indeed, your program is simple, if it is displayed in the Task Manager in a single line, we suggest that you hide the process in the simplest way. To do this, you just need to rename it.
So, we will help you figure out how to rename the process in the Task Manager so that the program continues to function perfectly in anonymous mode.
Step 1
Initially, you should go to the folder where the execution file of a specific program is located. If you know where it is located, then use your usual “route” by opening the “Computer” window, going to the system drive C, and then following to its root folder.
If you do not know where the execution file is hidden, it doesn’t matter, you only need to find this process in the list displayed in the Task Manager, right-click on it, and then select the line “Open file storage location” in the window that opens.
![]()
Step 2
After such your actions, you will open the folder you are looking for; in it you only have to find the execution file. Search will be easy, because this file has the exact same name as in the list of processes in the Task Manager. In addition, this file has the extension "exe".
Step 3
To rename a file, click on it again with the right mouse button, and then select the line "Rename". Now that you have managed to assign a new name to your software application, open the Task Manager, see that this rename has been displayed there.
![]()
Of course, it will depend on what name you think up how your program will become “veiled” for other PC users. An unfamiliar process with a new name will even more quickly arouse suspicion and force a technical engineer to figure out what program is running on a PC.
For this reason, many experienced users recommend coming up with names that at first glance do not arouse any suspicion.
In particular, the open Chrome browser creates several processes at the same time, just like Windows. It is desirable to take the same process name, but since the system will not allow two processes of the same name to function simultaneously, it is recommended that a small trick be used when renaming. Instead of some English letters, it is as if accidentally registering Russians in the title. Outwardly, it is impossible to distinguish Russian from English letters, and the system will distinguish, therefore, it will allow programs with conditionally the same names to work.
Results
So, as you have managed to notice, you can make some software anonymous without much difficulty. Of course, there are still quite advanced methods that allow you to hide any process more reliably, but they are based on writing complex codes and programming skills. If you do not set such complicated goals, then hiding working software applications by renaming is an acceptable option.
There are situations when you need to install and use the program in secret from another person who understands computers and often looks at the Task Manager processes when a device hangs or is unstable. Sometimes you want to activate the tracking computer, so as not to clutter up unnecessary files. In other cases, it is required to trace the person. There can be a lot of reasons, each has its own.
What are processes?
A process is a program that runs on a computer and occupies a specific place in random access memory.
Processes are divided into:
Systemic (programs and utilities that are components of the operating system and any emergency termination of one of them may entail negative consequences, such as a failure in Windows).
Anonymous (extremely rare, they are files of programs that run as auxiliary due to user manipulations, without asking for permission to launch).
Network / Local (processes in Task Manager related to local area networkInternet and registry are important programs and components of Windows).
Custom (programs that are run by the user).
Is it possible to determine the "left" process?
It is not always possible to determine the "left" process. If the person who created it and thoroughly disguised it, it is unlikely that even an experienced computer engineer will be able to calculate it without receiving a hint of this fact and a detailed study of the behavior of each process.
However, a person who is sure that an extra program hangs on a computer, and that it is also poorly disguised, will be able to calculate it in a matter of minutes.
How to hide the process in the task manager?
The easiest option to hide the process is to rename the main executable file. But it is worth considering how the program works and whether it creates additional processes that produce it.
If there are no extra processes, then you can proceed:
1. Open the folder with the executable file. This can be done in several ways: if you know where the file is located, you can go to the folder with it, or right-click on the process and select the item “Open file location”.
2. After moving to the folder, find the executable file, it should match the name of the process in the manager.
3. Rename the file so that it is difficult to determine the replacement name. You can rename through the same item context menu. The file extension still must be an executable file (.exe).
4. Go to the task manager and look at the process that you yourself have changed.
Everything went fine, but the process is visible and it should be disguised so that no one would guess about its real purpose? To do this, it is worth considering a few nuances that may allow you to hide the process in the task manager without any help.
The process should be similar to the program that creates many own copies and it is always on. A clear example of this is that all browsers on the Crome engine, or permanently running program Windows, which does not cause suspicion.
Names can be changed with switching Russian-English letters, for example, replacing English with Russian and correcting foreign letters: a, b, d, e.
In conclusion, it should be noted that it may be necessary to rename a few more files that are “subprocesses” of the program.
We hope you understand how to hide the process in Windows. Experiment, hide, learn.
By opening the Task Manager, a Windows user can see what is going on in the system. the processes and close those that seem suspicious to him. In order to protect their programs from detection, the authors of Trojan programs and ad-aware are trying by all possible ways hide them the processes.
Instruction
To make the most of the “Task Manager” features, you should configure it correctly. Open the utility (Ctrl + Alt + Del), select "View" - "Select columns". Tick the boxes: “Process ID”, “CPU Load”, “Memory - Usage”, “USER Objects”, “Username”. You can not see hidden the processes, but more detailed information about the visible is also very useful. For example, many simple Trojan programs are disguised as the svchost.exe process. The original process in the column "Username" is marked as SYSTEM. The Trojan process will have the status of Admin, that is, run as administrator.
Almost any competently written Trojan is now capable of hiding its presence from the Task Manager. Is it possible to detect it in this case? Here come to the aid of special tools that allow you to identify hidden the processes. Very convenient program AnVir Task Manager, which allows to identify many dangerous programs. The program has a Russian interface, it can be downloaded for free on the Internet.
Very easy to find hidden processes has a simple and easy-to-use program Process Hacker. With this utility you can see the running the processes, services and current network connections.
One of best programs To search for hidden processes is Spyware Process Detector, its 14-day trial version can be downloaded at the link at the end of the article. The program has a wide range of mechanisms for finding hidden processes, which distinguishes it from many other similar utilities.
A small utility HijackThis can be a useful help in the fight against Trojan programs. The utility is designed for fairly experienced users. Guidance on its use you can see below in the list of sources.
One way to detect viruses on a PC is to view running processes in the Task Manager. Not always antivirus software they cope 100% with the tasks assigned to them. Sometimes you have to catch viruses manually.
Many viruses hide their presence in the Task Manager - they are invisible. In this case, alternative task managers come to the rescue. Any of them can be downloaded online and enjoy. Built-in Windows, its own Task Manager is uninformative and does not show hidden processes. Third-party, similar utilities are deprived of this disadvantage and show hidden processes. If there are no processes in the standard dispatcher that appear in the analysis window of an alternative utility, then you need to pay careful attention to these processes, perhaps this is malicious applications. It is necessary to look at the manufacturer of the process, usually it is always clearly and clearly indicated, and also how much resources this process consumes. If a lot, compared with others, then it is extremely suspicious.
Such an inspection should be done when the applications are turned off, that would remain standard processes and viruses, of course. Best done in Safe mode . Very good, when you just installed Windows, take a snapshot of the Task Manager page with standard processes so that you can compare the differences. The snapshot is due to the saved file with the screen, and not the snapshot by the camera (made by pressing the Print Screen button on the keyboard, who does not know how to do it, ask in the comments).
So, consider the standard processes:
- Sistem - system processes no extension exe.If such a process you have with the extension - this virus is disguised as a system process.
- Smss.exe -process managing the launch of user accounts. If you have enabled, at the moment one session account, and Smss.exe processes more - draw the appropriate conclusions.
- Csrss .exe. - the process governing the creation of windows, it must be, always one.
- Winlogon.exe. - is responsible for the authoritarian user login. Only one.
- Services.exe. - provides the operating system services, runs on behalf of the System, also one.
- Lsass.exe. - ensures the safety of the OS, always one.
- Svchost.exe. - run Dll-files (dynamically connected library, this includes drivers, ActiveX controls) user name: LOCAL SERVICE, NETWORK SERVICE and SYSTEM, should be a maximum of six.
- SYSTEM - is responsible for the keyboard layout and language bar on the taskbar. Must be one.
- Explorer.exe. - manages the desktop (labels, icons, etc.), its interface. Runs once.
- Spoolsv.exe. - puts objects in the print queue. One. No printer - and you can turn off the process is not critical.
- Wdfmgr .exe. - is responsible for the correct operation of the media player driver, is also not a critical process.
- Taskmgr.exe. - Task Manager itself
- Well, the latest - Idle system. Shows free resources.
In normal mode, in addition to these processes, you will have processes running applications, drivers. To disable a suspicious process, select it and click Stop Process.
This is one of the ways that is safer than, let's say, experimenting with the system registry.