Having opened the "Task Manager", the Windows user can see what's happening in the system processes and close those that seem suspicious to him. To protect their programs from detection, the authors of Trojan programs and ad-aware try to hide them in every possible way. processes.
Instruction
To make the most of the capabilities of the "Task Manager", you should configure it correctly. Open the utility (Ctrl + Alt + Del), select "View" - "Select columns". Tick the boxes: "Process ID", "CPU Load", "Memory - Usage", "USER Objects", "Username". You can not see the hidden processes, but more detailed information about the visible is also very useful. For example, many simple Trojan programs are disguised as the svchost.exe process. The original process in the "User Name" column is marked as SYSTEM. The Trojan process will have Admin status, that is, it is running as administrator.
If something went wrong or does not correspond to the planned, you can return the system to its previous state. In addition, you can count on the help of applications designed to evaluate and clean up invalid entries or that are no longer automatically used in the registry. It is worth trying for free or.
Then the Registry Editor window will open, and you will need to search for the key that you want to delete. Obviously, you should also know the name of the key you are looking for, or your address when searching for a folder by folder. The left pane contains the folders and the right keys. Pay attention to the keys that will be displayed in the right part of the window, and when you find the one you want, right-click on it, select Delete - check, erase no important key - and click Yes.
Almost any competently written Trojan is now capable of hiding its presence from the Task Manager. Is it possible to detect it in this case? Here come to the aid of special tools that allow you to identify hidden processes. Very convenient program AnVir Task Manager, allows you to identify many dangerous programs. The program has a Russian interface, it can be downloaded for free on the Internet.
Follow this software
Some applications may lead to more serious problems, such as limited communication and malfunctions. After you finish playing, do not hesitate to re-activate these applications. Antivirus applications. If the problem persists, try disabling or temporarily removing the program to check the problem. For some applications, restarting the system may be required after it is turned off or deactivated. Make sure that important services are not running in sandbox mode.
Accelerator programs and download managers
Virtual Private Network Software
Runs when an administrator solves a problem.- If you encounter such problems when installing this program, remove it.
- Alternative: We are currently studying a solution to this problem.
Very good opportunities for finding hidden processes have a simple and easy-to-use program Process Hacker. With this utility you can see the running processes, services and current network connections.
One of the best programs for finding hidden processes is Spyware Process Detector, its 14-day trial version can be downloaded from the link at the end of the article. The program has a wide range of mechanisms for searching for hidden processes, which distinguishes it from many other similar utilities.
To do this, select the entry and click "Disable". Scroll down the list and click “Choose icons to display in the taskbar” to open the next window. It helped me, and hopefully it will help too. If this does not help you open the registry editor and go to the next key.
Follow the troubleshooting steps below to resolve many installation issues, including. Error in any of the following types: this program has performed an illegal operation and will be closed.
- Empty or blinking dialog.
- Cursor or locked screen, blue filter or unexpected restart.
A small utility HijackThis can be a useful help in the fight against Trojan programs. The utility is designed for fairly experienced users. Guidance on its use you can see below in the list of sources.
All modern multitasking operating systems, including Linux, run several processes to perform each of the tasks. Using notepad, terminal window, SSH server, SSH connection and so on are all separate processes. The operating system, in our case Linux distributes system resources (CPU time, memory, I / O), between processes, so that each process can work.
After starting the task, try restarting the installation to make sure that your problem is solved. Keep track of the results. Take into account the tasks you perform and their results, including errors and other problems. Reboot after each installation attempt or error. Always restart the computer after a failed installation or an error occurs to update its memory.
- Perform the task in the specified order.
- Follow the troubleshooting procedures described in this document.
- Try to set each task as a result.
- If not, go to the next troubleshooting step.
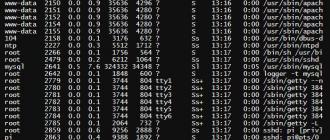
To view a list of currently running processes, use the ps utility:
The aux parameters indicate to the utility that it is necessary to output all system processes with information about the user from which they were started and the call command.
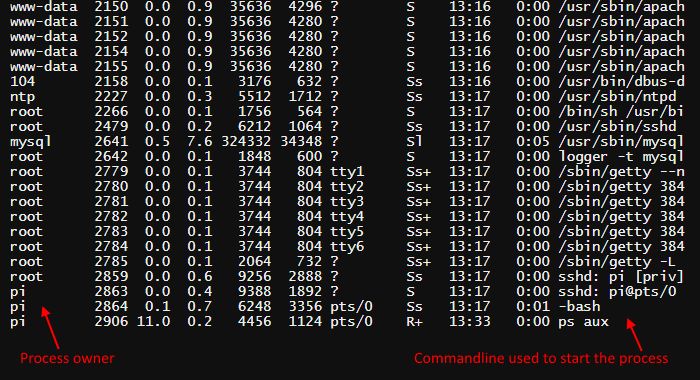
As you can see, the list contains processes belonging to various users, including pi - the default user in Raspberry Pi, root and www-data. Here is another screenshot that shows the processes and information about their startup command and parameters:
Make sure your system meets the minimum system requirements.
Read the data in this dialog box to see if you want to continue. If you decide to cancel the dialog box, you cannot continue the current troubleshooting step.
Deleting previously installed application files
To remove files from a previous installation attempt, follow these steps:If your disk is damaged, contact your dealer for a replacement product. Some system components, such as device drivers and anti-virus protection utilities, conflict with the installer. They may result in incomplete installation or installation failure. To prevent these conflicts, install from the desktop.
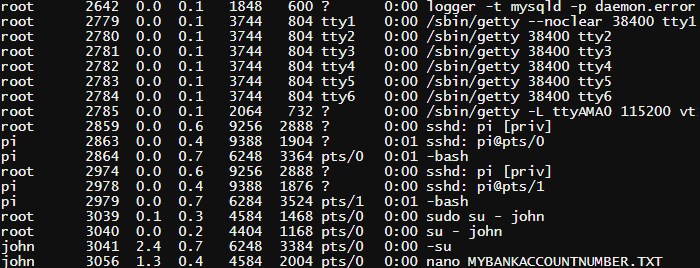
If you look at the bottom of the list, you will see the command nano MYBANKACCOUNTNUMBER.TXT executed by the user john. This data is provided to all users of the system and can be used for malicious purposes.
In the kernel version 3.2 and above, the function of prohibiting the user from viewing information about processes that do not belong to him is implemented. The ps command receives information about processes from the / proc file system. A new parameter, hidepid, has been added which is used when mounting the file system. It allows you to hide information about processes from users who do not have access to them.
If the tasks in the previous section do not resolve the issue, try the following intermediate troubleshooting tasks. In simplified mode, non-standard device drivers and software to run are disabled. To reinstall in simplified mode, follow these steps:
Installation as administrator
By setting the installer to run as an administrator, you bypass the security settings and allow the application to write data to protected areas.
Installing to a folder on the root level of the hard drive
Create a folder at the root level of the hard disk. Make sure that the folder name does not contain more than 8 characters and does not contain special characters, for example #.- hidepid = 0 is the default value, all users can read the / proc / pid files
- hidepid = 1 - users can access only their own / proc / pid subdirectory, but the cmdline, io, sched *, status files are available to all
- hidepid = 2 - all / proc / pid subdirectories are hidden from users
The / proc file system can be remounted on the fly using the mount option of the mount utility. To test hidepid, you can use the following command:
Starting installation in a new user account
Create a user account that has the same rights as the account used when the problem occurred. If the problem does not recur, the original user account may be damaged. In the section Create a New User or Contact a System Administrator.
Disable user access control
Updating video card driver updates. In general, video card manufacturers often update software drivers. If you have not recently updated the driver for your video card, contact the video card manufacturer to get the updated driver or download it from the manufacturer's website.sudo mount -o remount, rw, hidepid = 2 / proc
Then we try to execute ps again:
Now we will see only processes running from user pi.
To make these changes permanent you need to edit the / etc / fstab file. This file controls the mounting of file systems at startup.
sudo nano / etc / fstab
Find this line:
proc / proc proc defaults 0 0
For the video card manufacturer, view the properties of the card in the device manager. You can usually determine if the video driver is out of date by changing the color depth and resolution of the video adapter. You can also determine if it is outdated by disabling hardware acceleration of graphics.
If you are not sure about the integrity of your system and want to know whether some processes were hidden without your knowledge, there is a handy tool. Then there are a bunch of parameters, but roughly speaking, here are the standard tests. 
This is the most effective solution. . In the summer morning. Wake up with the light, feeling more rested. Sunrise modeling gradually awakens you. Natural sounds will wake you gently, the choice between two sounds. The repeat snooze function and 10 light intensities are enabled.
And replace it with:
proc / proc proc defaults, hidepid = 2 0 0
Close the editor with the keyboard shortcut Ctrl + C and restart your computer. After reboot, / proc will be mounted with the correct options. To check mount options, use the mount and grep commands.
mount | grep hidepid
Now try running ps:
As you can see, only the processes belonging to the current user are visible. But there is one remark. The superuser can still see all call processes and parameters.
View and delete hidden and locked files
Just as some legitimate system processes can be disguised by the system itself. Of course, this method has drawbacks, but hey, it remains a simple programming method. Check the log file. . You can use programs like.
However, if you want to perform a search, it is difficult, since you need to click on each of the processes. This is an advanced task manager. . Thus, there are as many resources as there are services that use it. To get to the directory, you will be required.