How to recover your Windows XP account password
Forgot the password to log on to Windows XP? Well, it happens. To restore or reset the user's login password, there are a lot of tools, but you can access them only by booting from an external media. There are two main methods:
- password recovery by brute force;
- reset or soft reset.
The first option is not always fast and convenient, and not as effective. It should be resorted to only when you need to know the password without changing it. For example, if the account under which you are logging in is not your account. In all other cases, it makes no sense to save the password, it is easier and quicker to reset it and assign a new one.
Where does Windows XP store passwords from accounts? The main part - in a special storage - the database that connects to the registry. It is located in the file C: Windowssystem32configSAM (without the extension). Simply so to pull out therefrom any password it is impossible, as they are stored in the form of hash-sums, that is are ciphered. The process of hashing is irreversible, but knowing the hash-sum of the password, it can be calculated in ways based on the search method. How long this process takes will depend on the complexity of the password. Relatively simple - in the form of a combination of numbers or known words, are selected quickly. Complex - alphabetic combinations, sometimes this method can not be learned. Or rather, it can take a decent time.
Password cracking (selection)
As we said, this method allows you to find out the password without changing it. If you have enough time, you can use the following tools:
- Proactive Password Auditor from the developer Elcomsoft;
- LCP from Lcpsoft;
- SAMinside from InsidePro Software.
Proactive Password Auditor
Shareware utility, in the trial period can select only simple passwords on the local or remote computer. Supports. Before you begin, you must import the account store into the program.
Proactive Password Auditor implements several ways of hacking: by different types of hashes, dictionary, mask, brute force, etc. It's easy to use the program. Its interface is intuitively understandable even for the inexperienced "hacker". There is a built-in help.
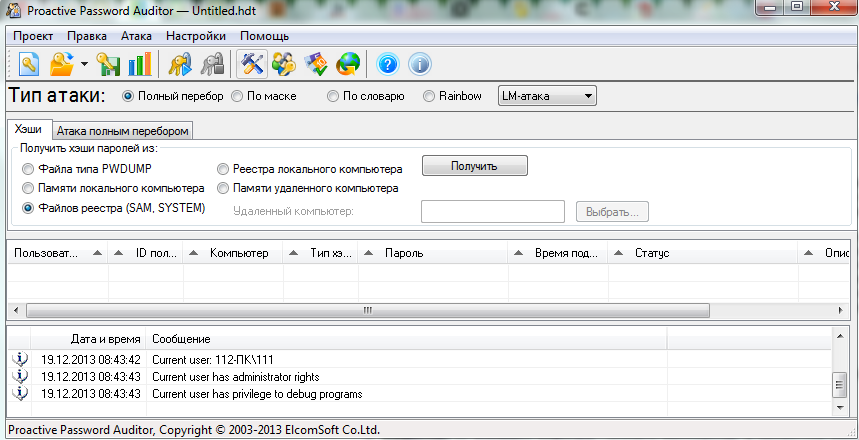
LCP
A powerful, free tool with a Russian interface. As well as the previous utility, it works with databases of local or remote computer (across local area network). Fully supports Windows XP.
Works with different types of hashes and uses three different hacking techniques: brute force, dictionary attack (calculating hashes for each word from the dictionary and comparing it with a password hash) and hybrid dictionary attack (when you compute hashes, other symbols are added to the words from the dictionary).
The program is supplied in Russian.
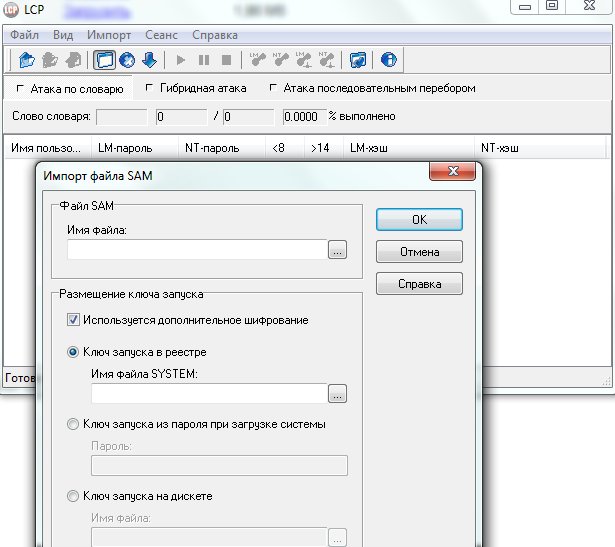
SAMinside
Conditionally free utility, in the trial version is also limited in functionality. Included in the software suite the boot disk for - Alkid Live CD.
Before you can crack a password using SAMinside, you need to import the local machine account store in the "File" menu. The program can work with different types of files that store hashed passwords. The methods of hacking are also somewhat: by dictionary, by search, by mask and by Rainbow-tables. The method is selected from the "Wrench" or "Audit" menu.
The management of SAMinside is intuitive. Work with the utility is carried out in three stages:
- import of databases;
- search for accounts in the repository;
- choice of the method of hacking and, accordingly, its launch.
There is a built-in help file.

Reset and assign a new password
You could not find out the password, but do you still need to enter Windows XP? In that case, I forgot - I have not forgotten, it remains only to reset the old password and install a new one. For this, too, there are means, but you can use the usual command the Windows string, which, in our opinion, will be loaded before entering the system.
Programs for resetting the password exist much more than for hacking, and they all have similar functionality. Their choice, as they say, is a matter of taste. And we, since we have an Alkid Live CD bootable, will use what's on it.
Active Password Changer
One of these utilities. It is very easy to manage, for use it is enough to select your account from the list and follow the instructions of the wizard.

Search for the necessary data is done automatically. By clicking "Next" you just need to make sure that you are logged in (the Windows folder on your hard drive) and selected your account. It remains to mark "Clear this User's password" and click "Apply Changes".
Password Renew for NT's
No less simple means than the previous one. To reset the password after the utility starts, sign in to Windows XP - click the "Select a target" button and go to the the Windows folder on the hard disk.
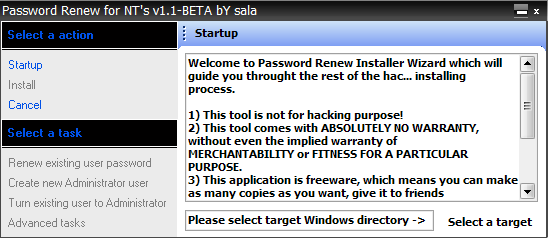
Then click the Renew existing user password button in the left panel. Select from the list of the desired user. Enter the new password and repeat it in the "Confirm Password" field. Confirm the entry. The password for the Windows login will be changed.

ERD Commander 5.0
If you have a universal disk restore Windows XP - ERD Commander 5.0, you can also easily reset password protection to your account login. To do this, from the "Start" - "System Tools" menu select the tool " Locksmith«.
In the "Account" list, select the required account, type and confirm the new password.

Command line
To start the command line before starting Windows XP, you need to perform a little more action. This option is suitable for you if you do not have anything near at hand, except for another Windows version of any version installed on the same computer, or a bootable Live CD "Windows Portable Edition". This method, as well as the previous ones, will not let you know forgotten password - you can only change it.
Booting from a Live CD, the first thing to do is to change something in windows Registry XP - the one where you want to reset the password.
- Start the Registry Editor: press the Windows and R keys, enter the command "Open" in the "Run" program regedit and click OK.
- In the left side of the Regedit window, select the HKEY_LOCAL_MACHINE section, open the "File" menu and click "Load Hive".
- Open the file C: WindowsSystem32configSYSTEM (without the extension) through the explorer.
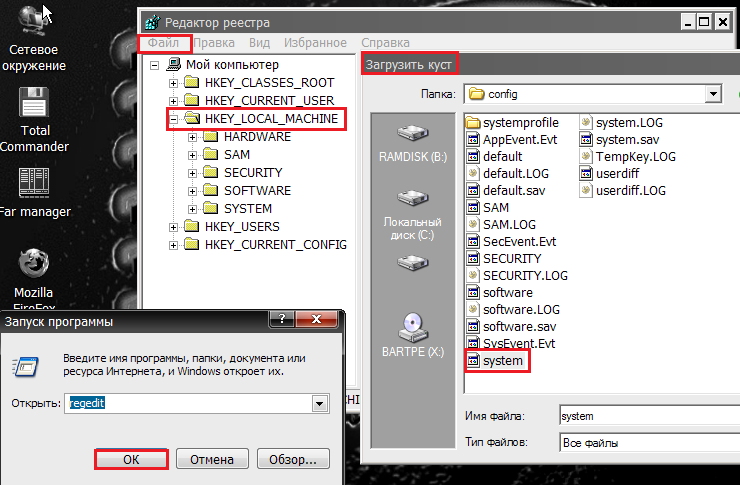
- Give the bush any name and open it. Highlight the "Setup" section (on the left side of the window).
- Next, on the right side of the window, change the value of the two parameters (right click on the parameter and select "Change"): CmdLine on cmd.exe, a SetypType on 2 .
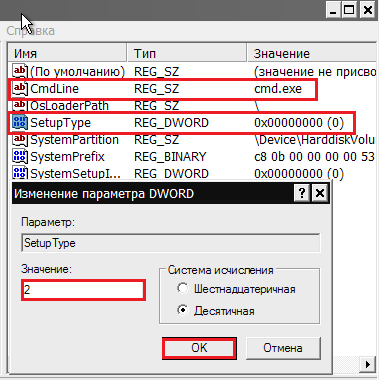
- Unload the hive from the file menu and load Windows XP.
- AT command line, which opens instead of the password input window, enter the command net user, eg:
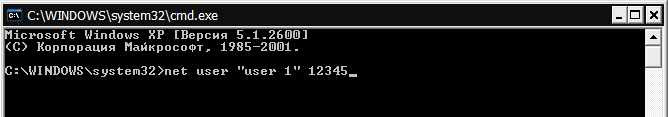
where - User account (Russian characters and words with spaces are written in quotation marks), and - New password.
- After logging in, do not forget to change the registry values to the old ones. All is ready.
We elevate privileges to system privileges using KiTrap0d, and we also pull out the administrator's password using PWdump and L0phtCrack.
So, I will state the essence of the matter. Imagine a very familiar situation (for students and secretaries): the administrator account is locked from the curved hands with a password, and we are in the usual (guest) account. Without knowing the password or having administrator rights, we can not roam on the admin desktop (such as "C: \\ Users \\ admin" - Access is denied), we can not change the Program Files folder and Windows ... - but we really need it! What to do?
1. KiTrap0D forever! - we raise privileges right up to System
In early 2010, the hacker T. Ormandy published a 0-day vulnerability, allowing to increase privileges in any versions of Windows. This solid is called KiTrap0d and in the current databases of antiviruses it is included in the section of type Win32.HackTool ("hacker tool").
A description of the vulnerability from the first hand can be read at:
So, we disable the antivirus (well, you trust me!). Then download the files from my documents to the address (password nagits - so that the antivirus does not swear) or look for a site called Tavis Ormandy. The compiled file consists of 2 files: the vdmexploit.dll library and the executable vdmallowed.exe. When you click on the exe-shnu, it starts up and opens the cmd.exe command line with the system privileges NT AUTHORITY \\ SYSTEM!
And now, as they say, the flag is in your hands! Having such rights, you can copy the files you need, find out valuable information ...
2. Recognize the password for the administrator account
..., but still it will be much more useful to learn the administrator's password.
Account passwords in Windows are stored as hashes in special branches of the registry HKLM \\ SAM and HKLM \\ SECURITY and access to them is closed even to administrators. The corresponding files of the Security Account Manager database are located in the% SystemRoot% \\ system32 \\ config folder in the SAM and SYSTEM files, but they will not be copied just like that, however, more on this later. Therefore, it is so important that we obtain system rights.
I'll talk about two approaches to obtaining a known password. One concerns, as you probably understand, the registry - a dump of passwords. The second approach, as the captain advises, is to obtain a SAM file.
2. Method 1: Dump the passwords
We will use a fairly well-known utility pwdump, which you can download from My documents at the address (password nagits). Switch to the command line cmd.exe with system permissions and run pwdump.
At the command
C: \\ pwdump.exe localhost\u003e C: \\ pass_dump.txtthe utility will reset the dump of passwords to a file.
For example, pass_dump.txt might look like this:
No history available Uzver: 1001: NO PASSWORD *********************: NO PASSWORD ***************** **** ::: VirtualNagits: 1000: NO PASSWORD *********************: 32ED87BDB5FDC5E9CBA88547376818D4 ::: Completed.
It can be seen that Uzver - common user, is not protected by a password, and VirtualNagits is an administrator, and a hash of its password is given.
I'll use the l0phtcrack program for an example. You can download the hinged box at.
Starting with Windows NT 3.1 (July 27, 1993), passwords are stored in the so-called. NTLM-hash. Unfortunately, the l0phtcrack program will agree to attack NTLM hashes only after registering / purchasing the software product. By the way installation should be started with administrator rights - at least. therefore installation file run from under the cmd.exe with the rights of System.
So, I have an installed and registered l0phtcrack v5.04 and pass_dump.txt: 

In the l0phtcrack program, press the Import button:
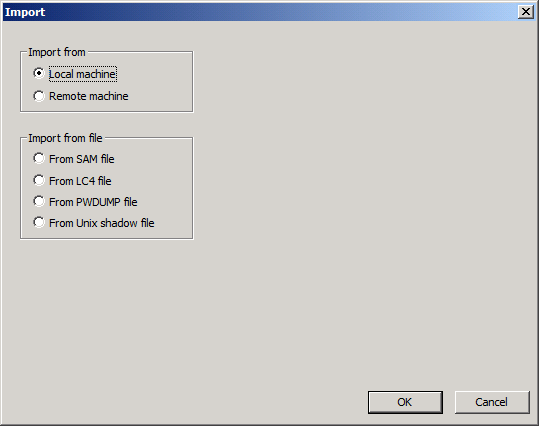
Select the import from the PWDUMP file (From PWDUMP file), specify our pass_dump.txt.

Now it is necessary in the options to note the breaking of NTLM passwords:
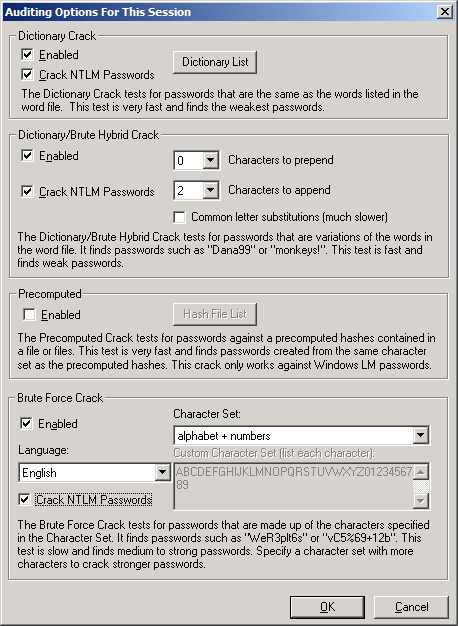
Confirm the selection by clicking OK and click Begin Audit.
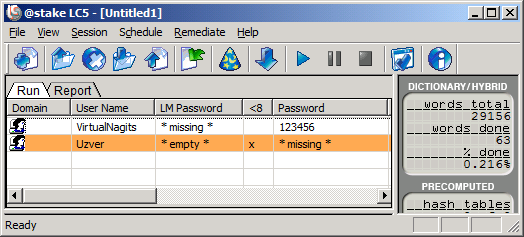
There is! A clever password "123456" administrator received!
2. Method 2. We get passwords from the SAM file.
In general, you can not copy the SAM file from C: \\ windows \\ system32 \\ config \\ even under SYSTEM, because they are "occupied by another application". The task manager does not help, because if you even find the culprit responsible for the Security Account Manager process, you can not complete it, because it is a system process. Basically, all of them are copied using a boot disk, in which case we do not even need admin rights. But often in the hands of no LiveCD ...
This is very well described on the website
Using an administrator account, you can make important changes to the system: install programs, configure security, and the like. By default, guest accounts and a simple user do not have such privileges. To prevent unauthorized entries and unwanted changes, many protect the administrator account with a password.
In Windows 7, you can create user accounts with administrator rights. In addition, the system defaults to the built-in administrator, which is not reflected in the welcome screen and with its help usually solve any specific problems. But, this password is not required for this entry.
How to find out without resetting
Alas, with the help of standard windows tools 7 you can not find out the password from the administrator account. By default, they are stored in encrypted SAM files. And if you forget the password, you will have to use third-party programs. But with their help you can learn not too much complex password, which contains Latin letters and numbers. One of the popular ones is SAMinside. Its advantages are a Russian-speaking and understandable interface.
If you do not have access to the system, the course of action is as follows:
- download and install the Windows XP Live CD on the USB flash drive - it will be bootable;
- there also install a program for hacking;
- boot the system from the Windows XP Live CD;
- run the SAMinside program;
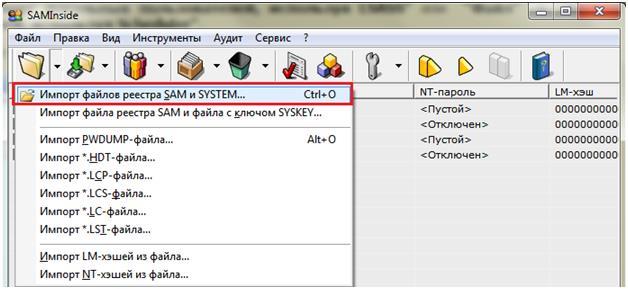
- export SAM and System files (they contain the necessary information) from the registry - for this click on Open - From: WindowsSystem32config.
- Then it remains to decipher SAM files and perhaps they will find the desired value.
It should be noted that any program does not give one hundred percent chance of decryption. The harder the password is, or the longer the password, the harder it is for the utilities to cope with it. And there are cases when they can not find out the password with their help.
Resetting the administrator password for Windows 7
If you forget the password and there is no possibility to restore it, you can simply reset it. This will require installation disk with Windows 7 or an installation flash drive. The type of media is not principled and plays no role. By default, the first in the download is hDD, on which the system is recorded. Therefore, first you need to go into the BIOS and in order of starting the devices move the installation disk or USB flash drive to the first place.
To perform the reset, we insert the media into the computer and select the system restore.
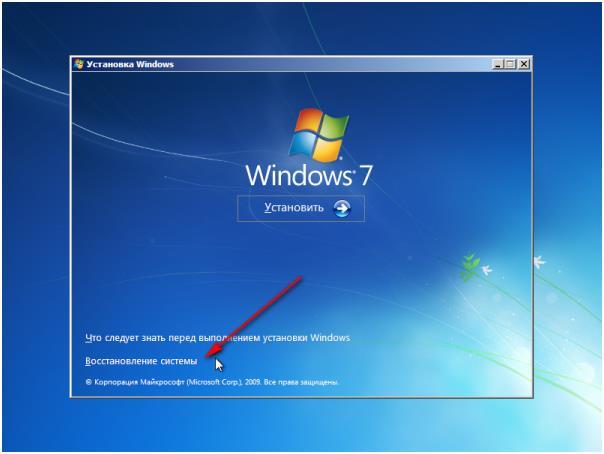 The program then starts searching installed Windows and this can take an unlimited amount of time. After the search, click "Next" and select the command term in the parameters.
The program then starts searching installed Windows and this can take an unlimited amount of time. After the search, click "Next" and select the command term in the parameters.
In the line, you would write the following command "copy C: \\ Windows \\ System32 \\ sethc.exe C: \\". By default, drive C is system disk, but not all users have a system on it, so instead of C you need to specify the system partition.
This command copies the file sethc.exe. It is he who displays the window that appears when you press the Shift key five times. By default, the file starts sticking keys, but you can set any other value for it.
Now you need to change the command for five times pressing Shift. We need it to include not a sticking of keys, but a command line. This way it can be opened when the system asks for the password.
In the open command line, write: "copy C: \\ Windows \\ System32 \\ cmd.exe From: \\ Windows \\ System32 \\ sethc.exe". If everything went well, the following message will appear:
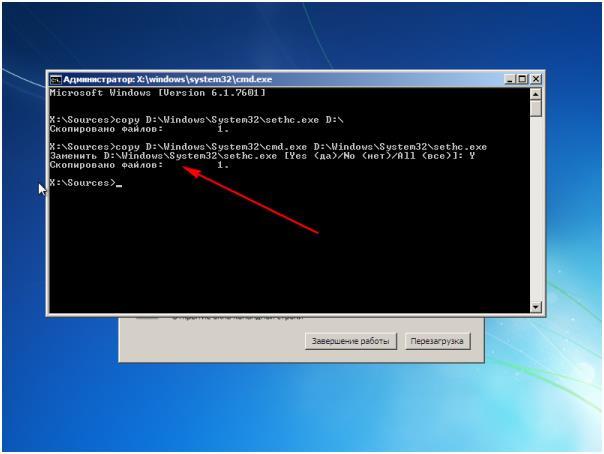 Close the line and click on the reload. We change the order of loading devices in the BIOS again and reboot again. After the restart, the start screen appears, where you are prompted to enter the password from the account. We press on Shift five times and at us the command line opens, and with the maximum access. In it we write "net user User 12345 ». User should be replaced with the user name, and 12345 is the new account password.
Close the line and click on the reload. We change the order of loading devices in the BIOS again and reboot again. After the restart, the start screen appears, where you are prompted to enter the password from the account. We press on Shift five times and at us the command line opens, and with the maximum access. In it we write "net user User 12345 ». User should be replaced with the user name, and 12345 is the new account password.
Close the command line, enter a new password and quietly go to Windows. At will, now you can completely remove the password in the Control Panel.
Floppy disk reset
If you often forget passwords, you can create a reset disk in advance. To do this, go to the Control Panel, click on "User Accounts" and select the account that needs to remember the password.
 We insert the device into the computer and point the way to it. Next, the program asks for the password. After some time, the reset floppy is complete. Now the main thing is not to lose the drive.
We insert the device into the computer and point the way to it. Next, the program asks for the password. After some time, the reset floppy is complete. Now the main thing is not to lose the drive.
Alternative methods
As one of the options, you can learn the forgotten password by brute force, usually a person uses two or three combinations and if you are looking for a password for your device, then this method can work.
Another way is very similar to the one described above. It also requires an installation disk / flash drive, but in time it will take more time, will require intervention in the registry and many different actions. Through the command line everything is much easier.
And the most cardinal way is to reinstall the the Windows computer. You certainly will not recognize the password, but you will receive full access to the system. Truth without the saved files. After installing the system from scratch, by default the password will not be available.
In this article I'll tell you and show you how to find out windows password 7, or Windows XP (meaning the password of the user or administrator). At 8 and 8.1 did not check, but I think it can work too.
Earlier I already wrote about how it is possible, including without using third-party programs, but, you see, in some cases it's better to learn the administrator's password than to reset it. Update 2015: The instructions for the local account and the Microsoft account may also be useful.
Ophcrack is an effective utility that allows you to quickly learn the Windows password
Ophcrack is a free utility with a graphical and text-based interface that allows you to easily find Windows passwords consisting of letters and numbers. You can download it as a regular program for Windows or Linux or as a Live CD, in case you can not log in. According to the developers, Ophcrack successfully finds 99% of passwords. We will now verify this.
Test 1 - a complicated password in Windows 7
To start, I downloaded the Ophcrack LiveCD for Windows 7 (for XP on the site there is a separate ISO), set a password asreW3241 (9 characters, letters and numbers, one uppercase) and booted from the image (all actions were performed in a virtual machine).

The first thing we see is the main menu of Ophcrack with the proposal to run it in two modes graphical interface or in text mode. For some reason, the graphical mode did not work for me (I think, because of the features virtual machine, on an ordinary computer everything should be in order). And with the text - everything is in order and, probably, even more convenient.

After selecting the text mode, all that remains is to wait for the end of the Ophcrack work and see what passwords the program has been able to identify. It took me 8 minutes, I can assume that this time will be reduced by 3-4 times on an ordinary PC. The result of the first test: the password is not defined.
Test 2 - a simpler version
So, in the first case, it was not possible to find the password for Windows 7. Let's try to simplify the task slightly, in addition, most users still use relatively simple passwords. We try this option: remon7k (7 characters, one digit).

Boot from the LiveCD, text mode. This time it was possible to find out the password, and it took no more than two minutes.
Where can I download
Official site Ophcrack, where you can find the program and LiveCD:
If you use LiveCD (which I think is the best option), but do not know how to write ISO image on a flash drive or disk, you can use the search on my site, articles on this topic.
conclusions
As you can see, Ophcrack still works, and if you are faced with the task of determining the Windows password without dropping it, then this option is definitely worth trying: the probability that everything will work out. What is this probability - 99% or less difficult to say for the two attempts made, but, I think, is quite large. The password from the second attempt is not that simple, and I assume that the complexity of passwords for many users is not much different from it.