After some calm, a wave of questions on the topic "The page does not open ..", "I can not enter the site ...". The rule here is one - start checking with the hosts file.
What is the hosts file?
To begin with, each site has a text name and a corresponding unique digital code. Usually in the address bar we write the text address of the site, because it's more convenient for us. Once we have entered the name of the site, immediately a special DNS server will convert this name into a numeric code - an IP address.
Use of the service. Do you connect or listen to the port ?: No. Services that depend on this service: no service is not dependent on this service. Comments: This service is needed in different environments. For example, if it is not running, it may not work correctly if we are in a domain. For some online games, you may even need to work. As with other services, you must be careful with the file name associated with that service.
This process is called resolving computer names. They are listed in order of priority from the highest possible to the minimum. Typically, this is the last way to generate redundant traffic on a network with a significant number of computers. And look at the search directory for this file.
The hosts file is designed to speed access to the site bypassing the DNS server. That is, if we register the IP-address and the site name here, then we will not access the DNS server.
Now you understand that if you register this pair incorrectly, then the transition will not be the place you expected or did not go anywhere at all.
This feature is used malware, adding in the hosts the wrong pair - IP address and site name.
The device must be configured for the domain function, otherwise it simply will not work. Indicates that the device is a domain controller. . The last character is a hexadecimal code that identifies the network service. In this case, the folder appears instantly without asking for a password. # The domain name of the network or workgroup.
Enable support for encrypted passwords. # encrypt passwords = yes. # If your server will use the printer, put it instead of the bootable printer = no. # Maximum access log size: maximum size log = 50. # If the files are read-only, install. If in the files # someone can handle, leave.
Fix the hosts file.
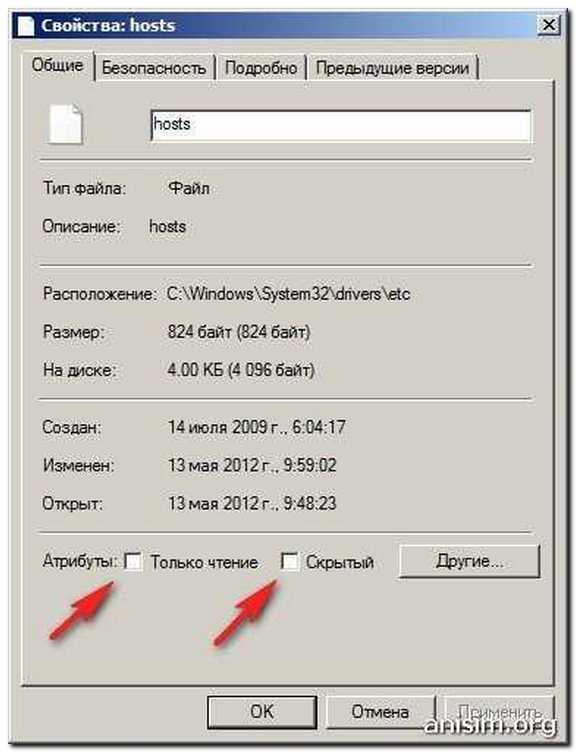
The hosts file is a text file and can be easily fixed by yourself. It is located at
C: / windows / system32 / etc
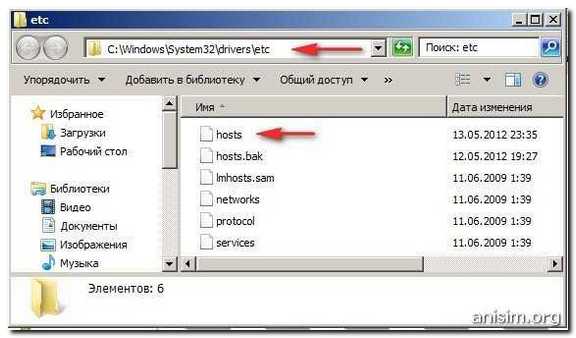
ATTENTION!! In folder etc In addition to the hosts file, there are other files that are intended for network configuration. These are networks, protocol, services, hosts, lmhosts.sam. DO NOT REMOVE this folder at all !.
# Indicates the level of the operating system #. level = 100. # If the folder is public, leave it public = yes read only = No. If there is a server on the computer itself, we will get access to the internal server; otherwise we will not get anything. The use described below is a deviation from its function to block access to certain sites.
How to change a host file
What is the method of modification
Another useful thing is to add sites that you need to block. Select this. Of course, you can add as many addresses as you want. There are also ready-made lists of hosts. If you want to use a large hosts file, disable this service.You can fix the hosts file with:
- microsoft Fix it utility - go to the site to its creators and do it with two mouse clicks.
- utility AVZ - very much about this written.
- when you check your computer with free utility CureIt -.
- manual correction.
When fixing the hosts file, you should know that there are pitfalls here. Virus writers use simple but effective tricks to slip us a dummy hosts file. Therefore, if you can not open the site and are going to check the hosts file, be extremely careful.
Some addresses must be blocked by your firewall. In short, if you encounter one of these addresses from the correct columns, the computer will redirect it to 1. Try to insert line 1 in Explorer to see the result. If you have any questions about information security, go to the bottom of the report and use the comments section. The column answers the questions left by readers every Wednesday.
My question is whether this method of access is absolutely safe. Camila, we better not work with the notion of something "absolutely safe." If an attack on your ISP redirects the site from the bank, you are still vulnerable. The problem is that there is no final legislation in Brazil yet. There are recommendations, but there are no legal obligations. Some telephone service providers and carriers do not store these reports, while others can not correctly list them.
Which hosts file are you running?
If you check your hosts and either do not find it at all, or think it's right, perform additional analysis. You will need an additional skill, a bit more than the usual possession of a notebook. But - nothing complicated.
In this section, the most common tricks are collected, with the help of which intruders try to prevent the user from fixing the hosts file.
This does not mean that there is a technical impossibility, especially when adopting the relevant legislation. Depending on your provider, it can already properly store the records. The supplier will be able to identify the customer. The following questions are relevant to this issue.
Is it right to have 2? Fernando Morgado. You do not need to bother with these files, and even if you do, nothing will happen to the system. Why? If there is only this line and no, it means that the file of your hosts has already been changed earlier, perhaps by some kind of security program. Even then, if there is a problem, simply activate the service, leaving the "Automatic" launch and restart the computer.
Trick 1 - redirection in the registry
If you can not log in to the site, and your hosts file is correct or you do not find hosts in the folder C: \\ windows \\ system32 \\ drivers \\ etc \\, then the virus changed the location of the file in the registry key.
To get rid of the virus, follow these steps:
1. Start - Run - regedit.exe.
2. In the Registry Editor window, locate the branch -
\\ HKLM \\ SYSTEM \\ CurrentControlSet \\ Services \\ Tcpip \\ Parameters
3. In the tab Parameters the menu with the file name, its type and value appears in the right part of the window. Check the value of the parameter DataBasePath. Should be % SystemRoot% \\ System32 \\ drivers \\ etc. If this is not the case, then right-click on this line, select Edit, and enter the correct value.
What address would you like to redirect? João Paulo. This can slow down the download of some sites. You need to use it only when creating local sites that replace blocked addresses. But this has nothing to do with what was said in the column, which even explains that software do not need to install.
Is it possible to do this from what you said? Carlos Pires. Yes it is possible. In some cases this may not work, because the configuration called "virtual host" depends on the computer that will receive the redirects. Today's package is here. On Friday, the column returns with a news bulletin of the week. At the moment, leave your question or suggestion on the proposal in the comments field below.
![]()
Even if you have hosts where you need to, but operating system uses the file whose path is specified by the DataBasePath parameter.
Trick 2 - inserting empty lines.
To detect unnecessary lines in the hosts file was more difficult, they are written to the very end of the file after a large number of empty lines.
He created and edited a Security Line, a security site and a forum that offers a free digital pest removal service, among other activities. The technique that we will consider will allow you. Links to these sites can be found on the pages you visit, nicely saying that they are "sponsored". To exit, if you find, for example, that access to security sites is prohibited to you. Some pests actually use this method to block sites that bother them.
However, this unknown technique is very easy to implement. It is free and does not require any software or additional tools. You have everything you need at your fingertips to apply it in practice, and the icing on the cake is absolutely safe and reversible, so you can get as much fun as you want with your host's file.
At first glance, this file looks normal and at a glance we can not notice anything, but you should always pay attention to the scrollbar slider in Notepad:
If the slider is present, then it must be lowered to see the contents of the file completely. Often this is useful, because At the bottom of the file we can find unpleasant surprises:
This is a universal format for marking a resource on the Internet. This is exactly what you do when you call: you will consult your phonebook to translate the caller's name to a phone number, and it is by his phone number you set the call.
Make sure the extensions are displayed
You guessed it, this is your hosts file. The name of this file is "hosts" without any extension. It's in the folder. Make sure the file extensions are displayed correctly, otherwise you will be dirty. This option should never be checked, it will help to avoid unpleasant surprises. it backups, which he performs during vaccination. To prevent attackers from writing to this file, some applications or even blocked it for read only. think about the change, you will need to temporarily unlock it.
Trick 3 - hiding the file.
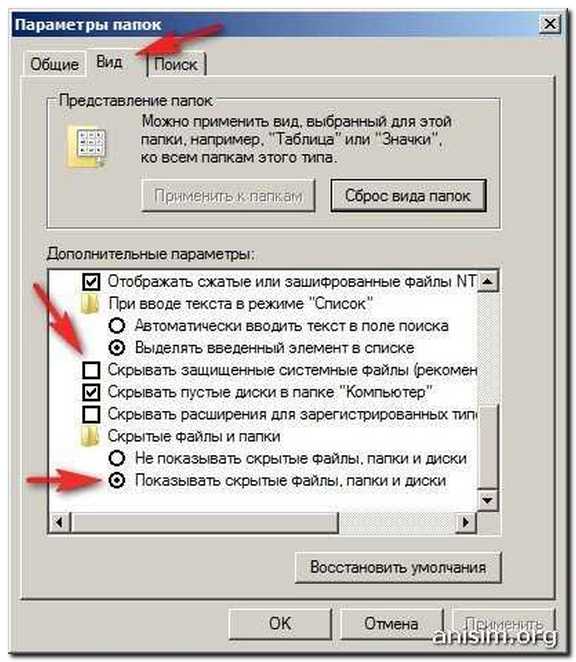
The hosts file is assigned an attribute Hidden, and it becomes invisible - there is no file hosts. And since by default hidden files and folders are not displayed in Explorer, then the user may not find this file, and therefore can not and edit it.
If you do not have the hosts file, then we need to make it visible. To do this in Windows XP, do the following: Start - Control Panel - Folder Options - View Tab - set the characteristic Show hidden files and folders - click Ok (in Windows 7 everything is the same, but instead of Folder properties the item is called Folders settings).
If it really does not exist, create it
The following two lines are other examples of locking
This line will not be taken into account. You think that some pests know about this and use it. Or to forbid access to certain sites. Listen to sites that bother them. As you can see, you can not connect to your favorite online scan pages, update your antivirus or download the necessary cleaning tool.Or divert your surfing
You will receive a classic message "Can not display the page" or "Login error" or "Could not connect". On another page, selected pest. Whenever you want to connect to your favorite site, you will be redirected to another site. Needless to say, this site was absolutely not an accessory pest, it does not prevent you from ever reaching the desired site. Nothing would stop the pests from distracting you to a much less innocent site.
A false file is created without an extension, but has a similar name, for example, a file host. And the current hosts file does this hidden.
In this case, we again edit the false file, but the present one remains unchanged. Such a file (host) can also be safely deleted!
Possible various methods. It all depends on how often you want to access it. The Notepad window opens with a blank editing space. At the bottom of the form in the "Type Files", first select "All Files". Select it and click the "Open" button. After changing the contents of the file, be sure to save the file after the change.
Using a small batch file
This is part of my toolkit. This is the easiest way if you do not want to browse folders. Regardless of whether the key is to find it. A window with a black background opens, do not worry and do not close it, you do not have to interfere. It closes when you leave the laptop.
Trick 5 - change the extension.
A false hosts file is created, which unlike the current file has an extension (for example, .txt). And since by default for registered file types the extensions are not displayed, then the user and therefore we can easily confuse the files and edit the wrong file at all.
Do not forget to save the file after changing
Using this shortcut, you will get direct access to editing the file in Notepad. You can turn off the line without deleting it. Simply insert the # at the beginning of the line. This line will be considered only if it ends with carriage return. However, it will not allow you to change or add a line in the current version.
It will not allow you to modify or add a line directly, except through a notepad. There is a special software. They are more or less practical and often english language. In my opinion, this is not very useful, because it is enough simple notebook. Lists of ready hosts.
Trick 6 - you can not edit the hosts file.
And one more thing, which is too hasty often do not pay attention.
You found the correct hosts file, found extra lines in it, you start to edit, but the changes are not saved. And all because your hosts file is assigned the "Read only" attribute.
When the number of registrations is exaggerated, communication with the sites is likely to be significantly slowed down. Note that the host name and computer name are two different things. By default, in the microsoft network, the hostname and computer name are the same. It is very important to distinguish between two concepts, especially in resolving names.
We could not open the file, and we recommend the appropriate software to open or convert these files. It uses tabs to write large sequences of genetic data, also called genomic sequences or maps.
Trick 7 - setting up a proxy.
I will not bother with the proxy, just check your browser settings.
Opera: General settings (Ctrl + F12) - Advanced - Network - button Proxy
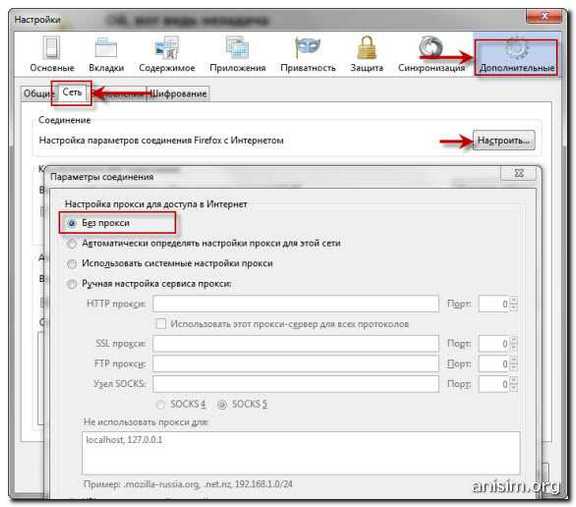
Firefox: Settings-\u003e Advanced-\u003e Networking tab - Configure
Below we see an example of a configuration. You can specify the default domain for authentication in the command line assistant. The following options are available for this helper. We still can not explain the reasons for this annoying problem. Solution: use squid. . This is due to the fact that the user has the right to register on a small number of workstations, but not on a proxy server.
Decision. . For some, it may not be easy to understand this concept of "name resolution", so there is a short explanation. Click Start, type the notepad in the search box, right-click the link, and select Run as administrator. Any changes made to the host file have an immediate effect after saving the file, so you do not need to restart the system.
By default there is a tick "use system settings proxy ", switch to" No proxy ", try to save the settings and restart the browser.
If manual configuration is required and the proxy server address is registered, you did not install it: save the address, delete it, put it into the "no proxy" mode.
Open our registry editor (use Win + R), press CTRL + F (search) and paste the saved address, then - find more ... All the keys with this address will need to be changed, namely delete the assigned value of our address.
Restart Windows and check.
Use hosts for their own purposes.
Method 1 - to speed up access to the site with the help of hosts.
If we often visit a site (for example, yandex.ru), you can add the following lines to the end of the hosts file:
87.250.250.11 yandex.ru
87.250.250.11 www.yandex.ru
Browser, discovering these lines, will not access the DNS server, which means that the process of downloading this site will be faster.
How to find out the IP site?
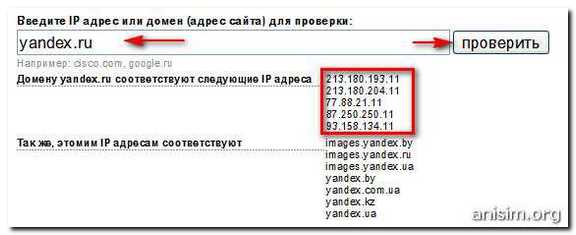
Method 2 - deny access to the site.
You can block unwanted sites by assigning a local IP 127.0.0.1 against their name. or the IP of some other site.
For example, according to the magazine, you see that the child plays for hours in tanchiki. The lines in the hosts file are:
127.0.0.1 tankionline.com
127.0.0.1 www.tankionline.com
generally closes access to this site (error message on connection).
A line of the form
81.176.66.163 kiss.ru
works more sophisticated. When you try to enter a kiss.ru in the browser, it will connect to IP 81.176.66.163, i.e. with the library of Moshkov.
As you can see, we can do the same as viruses, but with benefit.
It is possible to block the most harmful banner exchange networks and other hotbeds of advertising garbage. For example, a string like this:
127.0.0.1 www.bannerdrive.ru
will disable the download of banners from www.bannerdrive.ru. In principle, on the Internet you can find very large (up to 1 MB) hosts files, in which thousands of ad servers are blocked (blocked).
But do not get carried away with this especially - large (from several tens of KB) hosts files require a considerable amount of time to view them, which slows down the work. But you do not need to save too much - files up to 10 KB do not brake anything even on older machines, and 10 KB is many hundreds of lines.
Features of editing the hosts file in Windows 8.
In Windows 8, unlike previous versions, the order of editing the hosts file has been changed. The developers paid much more attention to this issue. And this is due to the more stringent requirements for system security and the protection of such an important file from encroachments from outside.
This protection is provided by the built-in windows anti-virus Defender - when making any changes to the hosts file, Windows 8 will automatically remove them, protecting the system from attacks by intruders. But for more experienced and self-confident users, there is one way to bypass this protection.
- Open the window of the defender himself. To do this, go to the startup screen and call the sidebar of the Charms Bar. If you have time to dress up your system and have installed windows 8 themes such that the system has changed beyond recognition, then use the combination Win + C
- Go to the search and enter the query " Defender».
- We click on the displayed line. A window will open in which you need to go to the " Options", Select" Excluded files and locations "and click the" Overview».
- Find the path to the file C: \\ Windows \\ System32 \\ Drivers \\ etc \\ hosts and click OK.
- Now, to add this file to security exceptions, you need to click the " Upload"And" Save Changes. "
Now you can start editing the file itself. However, keep in mind that you can change the file only on behalf of the administrator. To do this, turn on application search - Win + C -\u003e Search Icon -\u003e enter the query " Notebook«.
Start Notepad and select the icon with the heading " Run as Administrator».
The usual notebook will open and you can as usual.
Finally.
After you successfully fixed your hosts, be sure to check the computer for viruses and change the passwords from the mailbox.
tell friends
In contact with
The meaning of using the Lmhosts file was to convert NetBIOS names using the netbt driver. sys without broadcast requests. The Lmhosts file is normal text file, which lists the host names and IP addresses. Consider an example of this file with information about three servers, two of which are domain COMPANY controllers.
# LMhosts file for Domain COMPANY 10.1.1.10 DC01 #PRE #DOM: COMPANY 10.1.1.20 DC02 #PRE #DOM: COMPANY 10.1.1.3 0 PR03 #PRE 10.1.1.100 PR04 #PRE #BEGIN_ALTERNATE #INCLUDE \\\\ PR03 \\ PUBLIC \\ ETC \\ Lmhosts #INCLUDE \\\\ DC02 \\ PUBLIC \\ ETC \\ Lmhosts #END_ALTERNATE
The "sharp" symbol (#) performs two functions.
■ It is used before the standard parameters of the Lmhosts file (#PRE, #DOM and #INCLUDE).
■ Perceived as the start of a comment, if there is no parameter after the character.
Consider the standard parameters for the Lmhosts file. The parameter must be written in uppercase. Otherwise it is considered a comment.
■ #PRE. This option causes the system to load the appropriate entry into the NetBIOS name cache during the boot process. This allows you to speed up the initial transformation of names.
■ #DOM. This parameter marks the entry as corresponding to the domain controller. The domain name is specified after the colon. If the Lmhosts file is used in a domain, this parameter is required because it tells the local client the addresses of the authentication servers.
■ #INCLUDE. This parameter causes the tcpip driver. sys download the Lmhosts file from another computer. The #INCLUDE option supports a single central copy of the Lmhosts file that all workstations will use within the workgroup. The record is in UNC format, for example \\\\ SRVl \\ Public, where Public is the name of the resource. It is worth paying attention to the trap existing in this mechanism. The UNC name has a NetBIOS name, so this name must be written to the local Lmhosts file.
■ #BEGIN_ALTERNATE and #END_ALTERNATE. These parameters are used to separate multiple records within the # INCLUDE parameter. If there is only one # INCLUDE parameter in the file, these parameters are not needed.
Using the Lmhosts file
The Lmhosts file must be used only as a last resort. Such static recordings become time bombs and pursue an administrator as the crocodile pursued Captain Hook. Once the administrator forgets about the created record, and bangs - it worked at the wrong time.
As mentioned earlier, there are several common uses of the Lmhosts file. For example, some administrators use the Lmhosts file to convert names for dial-up connections. With a dial-up connection, you can use the WINS conversion, but often this conversion is not enough
Effective and requires too much effort to configure. A short entry in the Lmhosts file on the dial-up client allows you to store information about domain controllers and servers that the client is constantly using when establishing connections.
Instead of using the Lmhosts file to convert a name to a mounted drive, you can specify the IP address directly in the UNC name. For example, instead of connecting a resource named \\\\ Srvl \\ Users \\ LLuthor and using the Lmhosts file to convert \\ Srvl to 10.1.1.43, you can specify the name \\\\ 10.1.1.43 \\ Users \\ LLuthor. If you change the server's IP address, users will need to reconnect the network share, but this is usually easier than making changes to the Lmhosts file.