CCleaner is not just a program for, but a large set of various utilities for system maintenance. Some components are hidden quite "deep". And, unfortunately, rarely become heroes of reviews and descriptions of the famous application from the company Piriform. Let's correct the situation by reviewing the component intended for reliable erasure of disks.
By default, the disk is cleared using the pattern bit "00". This is the easiest and quickest way to clean the disk. You can select another bit-pattern, as well as the number of times the disk should be written to this bit-pattern. However, it is unlikely that any user-defined method will be considered sufficient to disinfect the disk. The main goal is to provide a simple and quick solution for erasing.
US Department of Defense Standard 22-M
For convenience, there are options for recording the industry number in each sector of the disk and for recording the user signature at the end of each sector. In accordance with this standard, data must be eliminated by writing a bitmap on the disk. Disks are disinfected by writing a different bitmap to disk in three stages.
Full erasing of discs: mission (not) possible?
A file erased in the usual way (Delete key, or item context menu "Delete") does not disappear from the drive: at first it is placed in the Trash. Restoring this file is a matter of a second. But even when cleaning the system storage for supposedly deleted files, in the skillful hands of the destroyed information - it's a matter of a few minutes. By the way, the same developers offer for this free tool Recuva - one of the best in its class.
Discs containing top secret data can not be cured in this way; they must be physically destroyed or the disks should be demagnetized, completely changing the magnetic patterns used to store data on the disk, and turning the disk into an inoperable state.
In the first 6 steps, each record changes the order of the bits of the previous record. This method is safer than just wiping with 6 steps of the same bit pattern. Several rewriting steps with the same pattern tend to be self-reinforcing, but there are advanced hardware recovery methods that can output data that has been overwritten. Recording interleaved bit patterns, such as the one used in this template, hinders the recovery process.
The fact is that when the command to delete the file is not physically erased from the disk. Only the service information is deleted, and the contents remain on the sectors - until the computer writes over the old data something new. After that, the data is lost irrevocably. Nearly.
It is believed that very skillful hands + high-end equipment, like an electromagnetic microscope (standard arsenal of special services), are able to recover information from the HDD, even if it is written over it. It is said that after the grouting the magnetized sectors contain some analog signals that indicate the ex-contents of such a sector. It is known that large commercial firms engaged in information recovery, are able to revive the hard drive after a fire or air crash.
This method of erasing data is widely considered safe. Security expert and internationally recognized author Bruce Schneier recommends that you rewrite the disc seven times. The first step overwrites the disk with the bit pattern "11", the second one with "00" and the next five with a randomly created bit pattern.
Peter Gutmann is an Honorary Research Fellow at Computer Science at the University of Auckland, an expert in the development and analysis of cryptographic security architectures. His research on safe removal These magnetic carriers are the final work on this issue.
How to erase a disk forever: CCleaner tools
Developers of specialized solutions for data destruction offer to erase all the contents of deleted files. Write a new piece of information over the remote sectors. If necessary - several times:- simple overwriting (1 layer of new information over the old one);
- overwrite using DOD 5220.22-M (3 pass-overlay);
- nSA algorithm (7 passes);
- gutmann algorithm (35 passes).
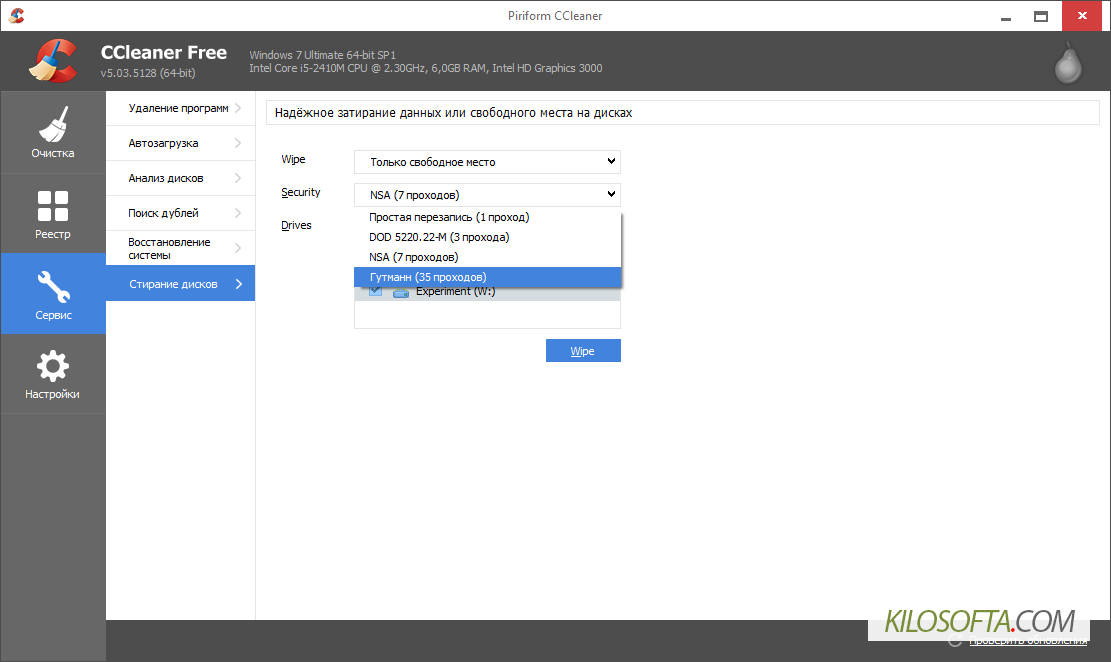
All about methods of mashing information CCleaner
The table summarizes data on the methods of erasing hard disks and possible ways information recovery. The cleaning time was calculated on an external HDD with USB 3.0 interface, in cases of multiple passes - with the help of an approximate calculation by the program itself.
| Method | Number of passes | Cleaning time | Who can restore | Recovery Tools | Recovery speed |
|---|---|---|---|---|---|
| Deletion to Trash | 0 | 1 second | User with minimum skill | 2 clicks on Trash | 1 second |
| Cleaning the Trash | 0 | 3 sec | User with average skills | specialized software | 3 min |
| Formatting | 1 | ~ 9 min | Advanced user | specialized software | A few hours or days |
| Easy dubbing | 1 | ~ 25 min | Special services, commercial firms | Spetssoft, special equipment | Unknown |
| Overwrite DOD | 3 | 1-2 hours | Probably, special services | Spetssoft, special equipment | Unknown |
| The NSA algorithm | 7 | 3-4 hours | No one?... | Does not exist (?..) | Unknown |
| Gutmann's algorithm | 35 | 1-2 days | Absolutely no one, probably | Does not exist (?) | Unknown |
Only the "free" part of the disk (87 GB) is erased, the uninstalled files remain untouched. The speed depends solely on the performance of the HDD: the processor and other components are almost not loaded. Competitor programs work on similar algorithms, and therefore the speed and principle of operation are about the same.
Its algorithm performs a total of 35 steps of rewriting and is considered the most modern method for data destruction. Most of us believe that the file is removed from the computer when we put it in the computer's recycle bin and then clean it; In fact, deleting a file does not delete it at all. When this is done, the computer will simply make the file invisible to the user and mark part of the disk that the file was saved as "available", which means that the operating system can overwrite the file with new data.
So it may take several weeks, months or even years for the file to be overwritten with new data. Until this happens, this "deleted" file will still be on your disk; it is invisible only for normal operations. With a little work and the right tools, you can still get it back. In fact, computers do not usually "delete files"; they allow only the space that these files occupy are replaced with something else at a later time.
What method to use to erase a disk
- 1 pass is comparable with the formatting (not "fast", but full), although after normal formatting the file structure is recoverable in many cases. This method is suitable for transferring second-hand HDD to a non-advanced user - for example, on a child's computer or remote from IT relatives.
- After three passes, the information is not recoverable (at least under normal conditions, even with high user skills). The method is best used when selling an old disk.
- 7-fold number of passes is necessary for final calm. This procedure takes too much time. However, if the drive can get into the hands of interested employees of the state security, then the time costs are completely justified.
- 35-fold passage. Probably, for the sale of retired old FSB agents to CIA employees?
At last
In the remarkable book of S. Lukyanenko there is an episode about the problem of erasing a hard disk. When one hero-hacker proposes to drill a hole in the case and pour acid into it, not relying on formatting and purlins, another character recommends giving the drive to schoolchildren - they say that for a week the kids are "rocking" the HDD so that no acid can cope better with them.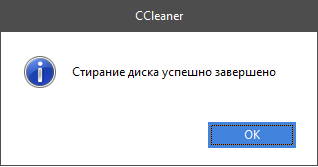 And was it successful? ...
And was it successful? ... Periodically, there is a need to increase the availability of free space, which allows you to improve the performance of the OS. The release of space from the used information allows to increase the speed of new records. For this you need to know how to clear hDD completely. By simply deleting files located on the hard drive, through the recycle bin and erasing the disk, the question of how to clean the hard disk completely can not be solved. In this case, there is an entirely different algorithm of actions, and the level of the erasure process must have a value corresponding to a reliable, high. All classified information can be destroyed using a method that has a greater number of passes. A complete deletion of information from the hard drive is required when updating the PC fleet, when it becomes necessary to completely clean the data contained in it. To do this, it is sufficient to re-record the disks on which the information is stored several times and the hard disk can be put up for sale. There are other ways to clean it, including the preservation of the right to restore data.
Warning about the limitations of secure deletion tools
In this way, the best way delete the file forever - this is to ensure that it is immediately overwritten, so it is difficult to recover what was written there. Complete Instructions available here. First, keep in mind that the above recommendation only applies to deleting files that you use on your computer's disk. To safely delete a file, you need to delete all copies of this file, wherever it is stored or sent. In addition, once the file is stored in the cloud, there is no guarantee that it will be permanently deleted.
Destruction of data on the hard drive is required not only when selling a computer device, either when the server is compromised or when the mobile electronic gadget with confidential information is in the wrong hands. Perform a full cleaning hard drive can different ways, from the use of special computer programs and ending with its physical destruction with the help of the press and other devices.
Unfortunately, there is another limitation of the safe exception tools. Even if you follow the above recommendation and delete all copies of the file, there is a possibility that some traces deleted files can be stored on your computer, not because the files themselves have not been deleted properly, but because some part of the operating system or some other program intentionally tracks them.
There are many ways to do this, but two examples are sufficient to clarify this possibility. In practice, there must be dozens of programs that behave like this. It is difficult to understand how to cope with this problem. Overwriting the entire disc is the only 100% safe way, ensuring that the file name has been deleted. Some of you may ask: "Could you find the source data on the disk to see if there are any copies of the data?" The answer is yes and no. A search on the disk will tell you if there is data in text form, but will not tell you whether any program was compressed or encoded.
Because the usual deletion of files, through the means of the operating system does not guarantee the complete destruction of information, specialists invented a whole list of ways to remove unnecessary information. Various means of completely removing information give a different level of possibility of its recovery.
Manually overwrites the hard drive
Complete destruction of data on the hard disk by overwriting it is available to everyone. This method is considered the simplest. It is perfectly suitable for routine cleaning of the hard drive, which is required, for example, when selling a computer device. If it is correctly executed, it guarantees 100% removal of all information on the discs. It can not be restored.
Also, be careful that your own research does not leave a record! The probability of saving the contents of the file is low, but not impossible. Overwrite the entire disk and run clean installation operating system - this is the only way to be 100% sure that the entries in the file have been cleared.
Safe removal when dropping old equipment
Therefore, before selling or processing a computer, be sure to overwrite your media with scrawls. If you have a computer that has already run out of service and is no longer in use, even if you do not get rid of it immediately, it's safer to clean your hard drive before storing it in a corner or in a closet. Some complete software to encrypt the disk can destroy the master key, which makes the encrypted contents of the hard disk incomprehensible. If you have not previously used full disk encryption, you will need to overwrite the entire disk before you get rid of it.
To begin with, you need to remove all the necessary files using the standard OS facilities. Then we fill the rest of the logical partition with any information. After that, the files used to fill the section can be deleted. In order to no longer be able to recover deleted information, it is better to perform this procedure several times. Thus, you eliminate the residual magnetization of the hard disk.
Therefore, it is best to use protection in terms of protection, because even if the file is still on the disk, it will at least look as strict for the one who will take it; this person will not be able to force you to decrypt the disk. Continue reading if you want to know why it's so hard to delete data.
At a higher level, wear resistance works as follows. The space on each disk is divided into blocks, something like the pages of a book. When a file is written to disk, it is transferred to a specific block or set of blocks. If you want to overwrite a file, all you need to do is specify the disk to overwrite these blocks. Each block can be cleaned and rewritten only a limited number of times before it no longer works. As a consequence, occasionally, instead of cleaning and writing to the block where the file was originally saved, the drive will leave this block labeled as invalid, and then write the modified file to another block.
The complete destruction of information on the hard disk will allow you not to worry that the personal photos, videos or confidential data contained in the computer will become public. The manual rewriting of the hard disk several times performed will allow you to get rid of the compromising information once and for all, without the right to restore it.
It would be like to leave the page in the book unchanged, write the modified file on another page, and then update the index of the book to specify a new page. All this happens at a very low level in the electronic disk system, so the operating system does not even realize that it happened.
Therefore, it is recommended that you first delete all data in order to prevent getting into the wrong hands. Even if you do not sell your laptop, it is recommended that you perform data cleaning to maintain good performance of your computer. When a virus or other malware attack your computer, data cleaning is always a good idea. Here are the situations when it is useful to clear the data.
Complete destruction of data on the hard disk it is recommended to perform this method. It allows you to completely remove confidential information from your computer without damaging the hard drive. This method is good if the data is deleted in a planned order, for example - when selling a computer device. If cleaning hard disk is required in emergency order, then it is better to resort to other ways of removing the information contained on it by means of its physical destruction or special computer programs.
Sometimes, when you accumulate a lot of data on your computer, your productivity suffers from this and becomes too slow. When a virus affects your computer, the only option is to clean up your computer's data, that is, its formatting. This will prevent fragmentation and many other problems. If you are going to connect or create new section, you may need to delete an existing partition on your computer. Therefore, you will need to erase the old data on your disk to go to the new installation.
- Data cleaning increases the performance of your computer.
- This will leave your hard drive similar to the new one.
- To keep your hard drive in good condition, you should clean it regularly.
Software for data destruction on HDD
Destruction of information onhdd maybe both planned and emergency. Scheduled cleaning of the hard drive is most often required when selling a computer device, and emergency - with unauthorized access to it by third parties. There are several effective ways to do this. The use of special computer programs is one of them.
However, before data is cleared, there should always be backup copy data. When the computer restarts, you will see an option to select the launch mode. On the next screen, you will see various configuration options and a list of partitions on your computer. Select the drive - and the partition - you want to clear and select the Exclude selected partition option. If there is more than one partition, you can select and delete all partitions.
It will automatically format your disk and reboot again. The operating system will be installed on the previously selected partition and will be loaded automatically. Some settings vary between operating systems, but the steps for clearing the data are exactly the same. Now you can choose whether to use a new operating system installation or an existing installation on your computer.
A faster and more reliable destruction of information on the hard disk can provide special utilities. The principle of operation of such programs is like multiple manual rewriting of a partition, but all procedures are performed in an automatic mode. Thanks to this you will save a lot of time, and the probability of a complete data deletion will be much higher. Some programs to remove the whole hard information disk use different algorithms, depending on the information carrier. But in software, it is not always possible to delete information 100%. For example, in system sectors where up to 20% of your information can be stored. The program can not access these sectors, access is possible only at the physical level.
You, of course, do not want to lose your data, which can become unrecoverable after they are removed from the computer. After the new screen appears, select the appropriate option. Select to clear and reinstall operating system. After that, your computer will reboot with the new installation, and you just need to restore the original backup data.
However, before you perform this process, you will need administrator rights. Personal information such as name, home address and address email, phone number. Photos and videos of your family or friends. These files include personal data. In case of disclosure of information, you can find dangerous things or see the severity.
A complete erasure of data from the hard drive without the possibility of their recovery can be performed using a special program Eraser HDD. This is necessary in the case of selling a hard drive. So you will be 100% sure that the new user has access to your text files, video and photo will not be.
Physical rapid destruction of hard drives
As it is guaranteed to destroy the hard drive in order to be 100% sure that the information recorded on the HDD will be completely deleted, it is necessary to destroy the hard drive itself. Immediately warn that the destruction of files in such ways leads to the disabling of the hard drive, so they should be used only in extreme cases.
Complete destruction of data on disk in the case of unauthorized access to them by third parties, it is best to carry out this method. It allows you to completely remove all compromising information, but also the hard drive itself. The possibility of data recovery in this case will be zero.
How can we prevent or prevent the possibility of the information carrier getting into third parties?
AT modern systems there is the possibility of entering under duress. Probably, this will be enough, but to hope that your opponent will be poorly educated and illiterate means to give oneself (more precisely your information) to the "will of the waves". It is better to overestimate the possibility of the enemy now than to subsequently receive "dividends" from the leakage of information of value to you.
For recycling hard disks, today the following devices are used: punches, shredder and press.
Punching tools are special mechanical devices that pierce magnetic pancakes in one or several places. Their main advantage is that you can even damage your hard drive even while the computer is running. The main disadvantage is the incomplete destruction of the magnetic pancake. Therefore, specialists, with due diligence, can recover some of the information from the HDD destroyed in this way.
The most reliable erasure of files provides a shredder - a device that simply grinds the hard drive into small pieces. It is impossible to restore even a part of the information from the recycled drive, even with the help of the most advanced equipment.
Press is designed to crush the hard drive, so that magnetic pancakes are strongly deformed. The reliability of destruction in this case is lower than that of the shredder, however, the process of recycling, in this case, occurs much faster.
Physical destruction guarantees complete deletion of information from hdd without the right to be restored, but it is better to resort to it only in extreme cases, when the data that has become available to the public can seriously harm you, depriving business, financial well-being, social status or even freedom. In all other cases it is recommended to use more sparing methods of removing information from the hard disk.
We re-magnetize and destroy the information from the HDD
To remagnetize hard disks, special devices are used, based on either permanent powerful magnets or electromagnetic coils. Devices with permanent magnets can not be combined with a working HDD. Therefore, the emergency destruction of data on the disk, to date, is done by electromagnetic systems, which can be installed in the computer's case in advance and, if necessary, applied. The reliability of this means of complete information removal is close to 100%. Te provides virtually guaranteed removal of information from the hard disk.
Complete deletion of data from disk It is required at sale of the computer device or at suspicions on intervention in its work of the third parties. The methods described in this article will allow you to completely remove confidential information within minutes, without the right to restore it.