What are the dumbest passwords in the world?
Here are the great five: 123456, password, 12345, 12345678, qwerty. If you find a password for your mail or Internet bank in this list, change it right now to some other (but not from the list!), And return to reading cards.
2
Why are these passwords so dumb?
Because these passwords are the most popular in the world. Accounts with such passwords are hacked by brute-force combinations - there is special programs... Actually, brute-force cracks not only these passwords, but these are the easiest to break.
3
What kind of overkill?
Brute force is a system that allows you to iterate over many options in order possible password... Let's say you use 5 digits in your password. There are only 100 thousand combinations. The computer will cope with this task before you finish reading this material. Good postal services usually do not allow infinite input wrong passwords, but such a system is not available everywhere.
4
And if there are 10 digits?
It's a bad password anyway. It will take a fraudster (or rather, a computer) several hours. The more digits, the more time it will spend, but still it is better to make the password more cunning.
5
Is a rare word good for a password?
No, it won't do at all. An attacker can use a variety of dictionaries to brute force. The system will eventually find the right word.
6
And if a rare word and numbers?
Such a password is more difficult to guess, but still possible. Modern systems bruteforce allows you to search not only numbers and words, but also word combinations and combinations of words and numbers.
7
So what's the best password?
This password must contain many characters - at least a dozen. These must be different symbols - numbers, uppercase and lowercase letters, punctuation marks. Combinations of letters should not form words, even if it is k0rovA.
Most attackers don't bother with sophisticated password-stealing methods. They take easy-to-guess combinations. About 1% of all currently existing passwords can be found with 4 attempts.
How is this possible? Very simple. You are trying the 4 most common combinations in the world: password, 123456, 12345678, qwerty. After such a passage, on average 1% of all "chests" are opened.
Let's say you are among those 99% of users whose password is not so simple. Even so, the performance of modern hacking software must be taken into account. The free, freely available John the Ripper program verifies millions of passwords per second. Selected examples of specialized commercial software claim a capacity of 2.8 billion passwords per second.
Initially, the cracking programs run through a list of the statistically most common combinations, and then refer to the complete dictionary. Over time, users' password trends may change slightly, and these changes are factored in when these lists are updated.
Over time, all sorts of web services and applications decided to forcibly complicate passwords, user generated... Requirements were added according to which the password must have the minimum required length, contain numbers, uppercase and special symbols... Some services have taken this so seriously that just generating a password that the system would accept becomes a really tedious and annoying task.
The key problem here is that almost any user does not generate a truly brute-force password, but only tries to meet the system's requirements for password composition to a minimum. If the cracker knows these minimum requirements, then the situation is only getting worse. As a result, passwords are obtained in the style password1, password123, Password, PaSsWoRd, password! and incredibly unpredictable [email protected] Imagine you need to remake your spiderman password. Most likely it will look something like $ pider_Man1. Original? Thousands of people will change it using the same or very similar algorithm. It is for this reason that the imposed requirement to make passwords more complex does not always provide the best security, and often creates a false sense of increased security.
The easier the password is to remember, the more likely it is to end up in cracker dictionaries. As a result, it turns out that a really strong password is simply impossible to remember, which means that it needs to be fixed somewhere. According to experts, even in this digital age, people can still rely on a piece of paper with passwords written on it. It is convenient to keep such a sheet hidden from prying eyes location. For example, in a wallet or wallet.
However, the password sheet does not solve the problem. Long passwords are difficult not only to remember, but also to enter. The situation is further aggravated virtual keyboards mobile devices. The chasm between the rosy dreams of experts and the harsh reality is easily felt by the example of one person. To store the password, he used a simple sticker that was attached to the monitor. The password was not a complex combination - it was a two-word phrase, without numbers and special characters. He could not remember even such a simple password. In reality, people not only prefer insecure passwords, but also have big problems remembering them.
When interacting with dozens of services and sites, many users leave behind a string of identical passwords. They try to use the same password for every site, completely ignoring the risks. In this case, some sites act as a nanny, forcing the combination to be complicated. As a result, the user simply cannot remember how he had to modify his standard uniform password for this site.
The scale of the problem was fully realized in 2009. Then, due to a security hole, the hacker managed to steal the database of logins and passwords of RockYou.com, the company that publishes games on Facebook. The attacker placed the base in open access... In total, it contained 32.5 million entries with usernames and passwords to accounts. Leaks have happened before, but the scale of this event showed the whole picture.
The most popular password on RockYou was 123456. It was used by almost 291,000 people.
Men under 30 more often preferred sexual themes and vulgarities.
Older people of both sexes often turned to a particular area of \u200b\u200bculture when choosing a password. Epsilon793 doesn't seem to be such a bad choice, only this combo was in Star Trek. The seven-digit 8675309 appeared many times because this number appeared in one of the Tommy Tutone songs.
In fact, creating a strong password is the easiest task in the world. It is enough to make a combination of random symbols. You won't be able to come up with an ideal-random combination in a mathematical sense in your head, but this is not required of you. There are special services that generate truly random combinations. For example, random.org can generate passwords like this:
- mvAWzbvf;
- 83cpzBgA;
- tn6kDB4T;
- 2T9UPPd4;
- BLJbsf6r.
This is a simple and elegant solution, especially for those who use a password manager to store passwords.
Unfortunately, most users continue to use simple weak passwords, ignoring even the rule “ different passwords for each site ". For them, convenience is more important than safety.
Situations in which password security can be compromised can be divided into 3 broad categories:
- Random, in which a person you know is trying to find out the password, based on his own knowledge about you. Often, such an intruder only wants to play a joke, find out something about you, or trite to spoil.
- Massive attacks, when absolutely any user of certain services can become a victim. In this case, the use of specialized software is mandatory. The least secure sites are selected for the attack, allowing multiple password variations in a short period of time.
- Purposeful, combining the receipt of hints (as in the first case) and specialized software (as in a mass attack). In this case, there is an attempt to get really valuable information, and only a sufficiently long random password will help to protect yourself here, the selection of which will take time comparable to the duration of your life.
As you can see, absolutely anyone can become a victim. Words like “my password will not be stolen, because nobody needs me” do not work, because you can get into a similar situation quite by accident, by coincidence, without any apparent reasons... Just no luck.
It is worth taking even more seriously the protection of passwords for those who are connected with a business, are in conflict on financial grounds with another person, or have valuable information. Division of property in the process of divorce, business competitors and so on.
Once Twitter (in the understanding of the entire service) was hacked only because the administrator used the word happiness as a password. In 2009, a hacker found the administrator password for Twitter and posted it on the Digital Gangster, which led to the hijacking of the accounts of Obama, Britney Spears, Facebook and Fox News.
Acronyms
As in any other aspect of life, we always have to find a compromise between maximum safety and maximum convenience. How to find the middle ground? What password generation strategy will allow you to create strong combinations that can be easily remembered? For now the best way is the conversion of a phrase or expression into a password.
A set of words that you always remember is selected, and a combination of the first letters from each word is used as a password. For example, May the force be with you turns into Mtfbwy.
The ideal password crafting scheme will work even if everyone starts to use it. Since the most famous ones will be used as the initial phrases, programs will eventually get these acronyms in their lists. In fact, the acronym contains only letters, and therefore is objectively less reliable than a random combination of characters.
To get rid of the first problem will help right choice phrases. Why turn a world famous expression into an acronym password? You probably remember some jokes and phrases that are relevant only among your close circle. Let's say you heard a very catchy phrase from a bartender at a local establishment. Use it.
The acronym password you generated is unlikely to be unique. The problem with acronyms is that different phrases can be made up of words that start with the same letter and appear in the same sequence. Statistically, in various languages, there is an increased frequency of the appearance of certain letters as the beginning of a word. The programs will take these factors into account, and the effectiveness of acronyms in the original version will be reduced.
Reverse way
The way out can be the opposite way of generation. At random.org, you create a completely random password, and then turn its characters into a meaningful memorable phrase.
Usually, services and sites give users temporary passwords, which are the very same perfectly random combinations. You will want to change them, because you will not be able to remember, but as soon as you look at them a little, it becomes obvious: you do not need to remember the password. For example, let's take another option from random.org - RPM8t4ka.
Although it seems pointless, our brain is able to find certain patterns and correspondences even in such chaos. To begin with, you can notice that the first 3 letters in it are uppercase, and the next 3 are uppercase. 8 is twice (from English t - twice) 4. Look a little at this password, and you will definitely find your own associations with this set of letters and numbers.
If you can memorize nonsense sets of words, then use that. Let the password turn into revolutions per minute 8 track 4 katty. Any conversion that your brain is better at will do.
The advantage of the reverse is that a random password is the gold standard in information security... It is, by definition, better than any man-made password. The disadvantage of acronyms is that over time, the spread of such a technique will reduce its effectiveness, and the reverse method will remain just as reliable, even if all people on Earth have been using it for a thousand years.
A random password will not be included in the list of popular combinations, and an attacker using a massive attack method will only brute force such a password.
Let's take an uncomplicated, random password that takes uppercase and numbers into account - that's 62 possible characters for each position. If we make the password only 8 digits, then we get 62 ^ 8 \u003d 218 trillion options.
Even in the absence of limits on attempts within a certain time period, the most commercial specialized software with a capacity of 2.8 billion passwords per second will spend an average of 22 hours on guessing such a password. To be sure, we add only 1 additional character to such a password, and it will take many years to crack it.
A random password is not invulnerable, as it can be stolen. The options are myriad, from reading keyboard input to having a camera on your shoulder. A hacker can hit the service itself and get data directly from its servers. In this situation, nothing depends on the user.
One reliable foundation
So, we got to the main thing. What random password tactics to use in real life? From the point of view of balancing reliability and convenience, the "one strong password philosophy" will do well.
The principle is that you use the same basis - a super strong password (its variations) on the services and sites that are most important to you. Remember one long and difficult combination for everyone.
Nick Berry, an information security consultant, accepts this principle, provided the password is very well protected. Malware is not allowed on the computer from which you enter the password. It is not allowed to use the same password for less important and entertainment sites - simpler passwords are quite enough for them, since hacking an account here will not entail any fatal consequences.
It is clear that the reliable framework needs to be changed somehow for each site. As simple option you can add one letter to the beginning of the stem, which ends the name of the site or service. If we go back to that random RPM8t4ka password, it will turn into kRPM8t4ka for Facebook authorization. An attacker, seeing such a password, will not be able to understand how the password for your bank account is generated. Problems will start if someone gains access to two or more of your passwords generated in this way.
Secret Question
Some hijackers ignore passwords altogether. They act on behalf of the account owner and simulate a situation when you have forgotten your password and want to restore it with a secret question. In this scenario, he can change the password at will, and the true owner will lose access to his account.
In 2008, someone got access to e-mail Sarah Palin, Governor of Alaska, and at that time also a presidential candidate. The burglar answered the secret question, which sounded like this: "Where did you meet your husband?" After 4 years, Mitt Romney, who was also a US presidential candidate at the time, lost several of his accounts on various services. Someone answered a secret question about the name of Mitt Romney's pet.
You have already guessed the point. You cannot use public and easily guessed data as a secret question and answer. The question is not even that this information can be carefully fished out on the Internet or from people close to you. Questions like "animal name", "favorite hockey team" and so on are perfectly selected from the corresponding dictionaries of popular options.
As a temporary option, you can use the tactic of the absurdity of the answer. To put it simply, the answer should have nothing to do with secret question... Mother's Maiden Name? Diphenhydramine. Pet name? 1991. However, such a technique, if found widespread, will be taken into account in the corresponding programs. Absurd answers are often stereotyped, that is, some phrases will be encountered much more often than others.
In fact, there is nothing wrong with using real answers, you just need to choose the question correctly. If the question and the answer to it are known only to you and cannot be guessed after three attempts, then everything is in order. The advantage of being truthful is that you won't forget it over time.
PIN
Personal Identification Number (PIN) is a cheap lock that our money has been entrusted with. Nobody bothers to create a more reliable combination of at least these 4 numbers.
Now stop. Right now. Right now, without reading the next paragraph, try to guess the most popular PIN. Is it done?
According to Nick Berry's estimates, 11% of the US population uses the combination 1234 as a PIN (where it is possible to change the code yourself). Hackers do not pay attention to PIN codes because without the physical presence of the card, the code is useless (this can partly justify small code size).
Berry took lists of passwords that appeared after leaks on the Web, which are combinations of 4 digits. The person using the 1967 password is likely to have chosen it for a reason.
The second most popular PIN is 1111, and 6% of people prefer this code. In third place is 0000 (2%).
Suppose that a person who knows this information is in the hands of someone bank card... 3 attempts to block the card. Simple mathematics allows us to calculate that this person has a 19% chance of guessing the PIN if he sequentially enters 1234, 1111 and 0000. Probably, for this reason, the vast majority of banks set PIN-codes for issued plastic cards themselves. However, many people protect smartphones with a PIN code, and here the following popularity rating applies: 1234, 1111, 0000, 1212, 7777, 1004, 2000, 4444, 2222, 6969, 9999, 3333, 5555, 6666, 1313, 8888, 4321, 2001, 1010.
Often, the PIN represents a year (year of birth or historical date).
Many people like to make PINs in the form of repeating pairs of numbers (and pairs where the first and the second differ by one are especially popular).
Numeric keypads of mobile devices display combinations like 2580 in the top - to type it, it is enough to make a direct pass from top to bottom in the center.
In Korea, the number 1004 is consonant with the word "angel", which makes this combination quite popular there.
Total
- Go to random.org and generate 5-10 candidate passwords there.
- Choose a password that you can turn into a memorable phrase.
- Use this phrase to remember your password.
A password is a string of characters used to access information on a computer. Passphrases are long passwordsthat improve security and contain many words that make up the phrase.
Passwords and passphrases allow you to exclude unauthorized access to files, programs and other resources.
When creating a password or passphrase, make them reliableso that they are difficult to guess or hack.
It also doesn't hurt to use strong passwords for all accounts on your computer. If you are using a corporate network, your administrator may need to use a strong password.
Note: AT wireless network protected wi-Fi access Protected Access (WPA) supports the use of a passphrase. The passphrase is converted into a key that is used for encryption (this process is invisible to the user). additional information for WPA security keys, see?
What makes a password and passphrase secure
Strong password: |
Strong passphrase: |
|---|---|
|
|
And passphrases contain characters that fall into four categories:
A password or passphrase can meet all of the above requirements and still be unreliable... For instance, Vaccinated B7! meets all the characteristics of a strong password, however, it is not strong because it contains a whole word. Password Priv1t B 7! is an reliable option - in the word, some letters are replaced by numbers, and the password itself contains spaces.
How to remember a strong password or passphrase:
Create an acronym from a block of easy-to-remember information... For example, choose a phrase that makes sense to you, like My son's birthday is December 12, 2004... Using this phrase, you can create a password like Dnms12 / Gr, 4.
Replace letters or words with numbers, symbols and spelling errors in an easy-to-remember phrase. For instance, My son's birthday December 12, 2004 can turn into DnN @ r M0g0Sun @ 12124 (you cannot use spaces in passwords).
Associate a password with a hobby or favorite sport... For example, I like to play badminton can turn into Any # 8B @ dm1nt () n.
If you want to write down your password so you don't forget it, do not mark it as a password and keep it in a safe place.
Passwords using ASCII characters
You can also create passwords and passphrases containing extended ASCII characters... Using extended ASCII characters will help secure your password or passphrase as the number of characters you can choose to create a password increases.
Before using extended ASCII characters, make sure the password or passphrase is compatible with the software you use at home or work. Use extended ASCII characters with caution in passwords and passphrases if your company uses multiple operating systems or other versions of Windows.
Additional ASCII characters can be found in the character table. Some additional characters ASCII should not be used in passwords and passphrases. Do not use a symbol unless a keyboard shortcut is specified for it.
Windows passwords can contain significantly more characters than recommended above (eight). In fact, the password can be up to 127 characters long. However, if you are on a network to which computers under windows management 95 or Windows 98, use a password that is 14 characters or less. If the password is longer than 14 characters, it may happen that you cannot log on to the network from computers running these operating systems.
We often speak in step by step instructions site site that passwords need to be created strong, long and complex. But what does all this mean in practice?
Let's take a look at the topic of creating strong passwords right now and learn how to create good passwords that hackers can't crack.
Immediately, we note that none of the following tips provides 100% protection against hacking or theft. There is no such way in the world that would guarantee accurate protection against fraudsters!
If hacking professionals want to get your password, they will, but strong passwords can weed out some newbies and non-specialists, complicate the task of hacking your account and greatly spoil the nerves of attackers, and therefore good passwords still make sense.
How do scammers find out the password
There are several ways to get your secret password:
1. Simple theft, theft, password theft:
- through special programs,
- on the Internet,
- through dummy sites,
- through fake programs,
- through access to your computer or leaf on which you write down passwords,
- finally, through blackmail, torture and interrogation (the latter is a joke, of course, but some girls actually use these ways to elicit passwords of their boyfriends in order to control the correspondence!).
Often, such scammers can disguise their goals as completely harmless, for example, you are asked to provide your profile login information to enter the program or to confirm your registration or unblock your profile.
2. Social engineering. The essence of the method includes a logical approach and analysis of your person with the identification of your personal information (year of birth, names of loved ones, passport data, phone numbers, last names of relatives, nicknames of pets ...).
3. Simple search in dictionaries. The simplest and most stupid way that still manages to crack simple passwords consisting of dictionary words, popular combinations like 123456789 or abcdef or qwert. Here, in fact, a program with a built-in dictionary is launched and dictionary combinations are searched.
4. Rough brute force. Similar to the previous method, but includes all possible combinations in general. The system goes through any values, and the fraudster hopes for luck that some options may coincide.
If we take into account the speed of such a search (about 100,000 or even 1,000,000 combinations per minute), the probability of coincidence is quite high.
How to create / think of a good password
A strong password should:
a) consist of letters and numbers;
b) have 8 or more characters;
c) contain both uppercase (uppercase) and lower case;
d) include symbols (not alphanumeric characters);
e) do not match any vocabulary word (in all languages).
To quickly create a good password, we would advise you to take a catchy phrase or expression that has nothing to do with your person, and type it without spaces in english layout.
Along the way, it is necessary to dilute this phrase with simple symbols and numbers, but in such a way that it is illogical. After that, all that remains is to replace a few lowercase letters with uppercase ones, and the job is done, a good password is ready. But all this is easier to understand with examples.
EXAMPLE of creating a good password # 1
Step # 1
Let's take the same phrase "strong password", type it in the English layout, we get "yflt; ysq gfhjkm".
Step # 2
Now we remove the space between the words and replace a couple of lowercase letters with capital letters, we get "yflt; ysQgfhjKm".
Step # 3
Now let's add a couple of numbers, for example, at the beginning and end of the phrase, we get "2yflt; ysQgfhjKm1"
TOTAL: our password has 16 characters, there are uppercase and lowercase letters, there are numbers and symbols, there are no dictionary words! This is a good and strong password that can be easily remembered by the phrase "2 strong password1" (only without the space in the center).
EXAMPLE of creating a good password # 2
Step # 1
Let's take the following phrase "peace at home", type it in the English layout, we get "vbh ljve".
Step # 2
Now we remove the space between the words and replace a couple of lowercase letters with capital letters, we get "vBhljVe" (replaced the 2nd from the left and 2nd from the right letters in the phrase).
Step # 3
Now let's add numbers, for example, at the end of the phrase, we get "vBhljVe21".
Step # 4
Let's complicate the password phrase with some symbol, but not between words, but after the first letter, so that it is illogical, we get "v ~ BhljVe21"
TOTAL: our password has 10 characters, there are upper and lower case letters, there are numbers and symbols, there are no dictionary words. This is how the phrase "peace at home" turns into a cool and complex password! And it's easy to remember.
The more illogical and unusual your methods of creating a password, the higher its reliability will be!
It's that easy to create a complex and strong password that will protect your profile well from simple hacking. It is worth remembering that different passwords must be created for different sites, and all of them must comply with the above requirements.
If you ignore these tips, you will use simple combinations, personal data or vocabulary words, the same passwords everywhere and everywhere, do not be surprised at hacking of your profiles, we warned you….
And in any case, do not enter passwords on sites or programs that cause even the slightest doubt! After all, it is easier for an attacker to steal your password than brute force it.
Today, when almost every resident of the city uses the Internet, it is very important to comply with all security measures. After all, a person has a page in social network, mail, bank accounts or electronic money. No one will like it if someone hacks into an account and thereby gains access to confidential information.
Alas, very often hacks are possible precisely because a person has set an unreliable password. You can understand a person, because always setting a complex password is very a big problem... It's easier when there is one single password, when it is easy to remember. This is how people make a mistake, especially if they have not only a simple password, but when it is the only password that is suitable for mail, and for an account on a social network, and even for a service where there is electronic money.

Before you put a password on your Wi-Fi, you need to figure out what it is for and what functions it should perform. Installing a home network on your computer is not such a difficult task, since for this they usually purchase a device loyal to the user.
Data protection in the local network

Usually, users purchase a router that is not focused on solving any complex tasks, most often they choose a router from a popular by ASUS... Masters in automatic tuning can connect your network without any problems, and at the same time they will also choose an excellent encryption method, and will also give advice on how to put a normal password on your Wi-Fi that meets all the necessary requirements.
Many users will not store in their home network any super important files. This is due to the fact that usually not many people install local area network between several devices, and therefore the path to important files on the computer is already initially closed. In truth, you shouldn't oversimplify your home network password anyway, even if there aren't any important files there.
Although the Internet is spreading around the world at a high speed, in many territories the Internet speed still does not exceed 1 Mbps. If you do not set a password at all, then anyone can get access to your router, the channel of which is not too wide, and therefore the speed of your network will approach a critical point, in general it will be bad.
What password can I come up with?

In order to prevent such a sad outcome from happening, it is necessary to put a high-quality password on Wi-Fi, which will be very difficult to crack, but at the same time such a password should be convenient to use. You can't come up with a password that cannot be cracked at all, but a combination of 8 characters, which includes uppercase and lowercase letters, a also, various symbols and numbers will be quite effective and will require a burglar about 11 months to sort through possible combinations.
No hacker will spend so much time hacking into one single home network, where it is unlikely that there will be some important information... In this case the best option the password will be a combination of letters of different register and different numbers. Using symbols would be a bad idea in this case, since if you go with mobile device into your home network, it will be very frustrating to enter them every time.
But understanding how to set a password on Wi-Fi is still half the battle. It is also necessary to make sure that the password is not, at the same time, too common. Following the above tips, you need to abandon the use of dates, names, and widely used character combinations in the password.
Use a password generator
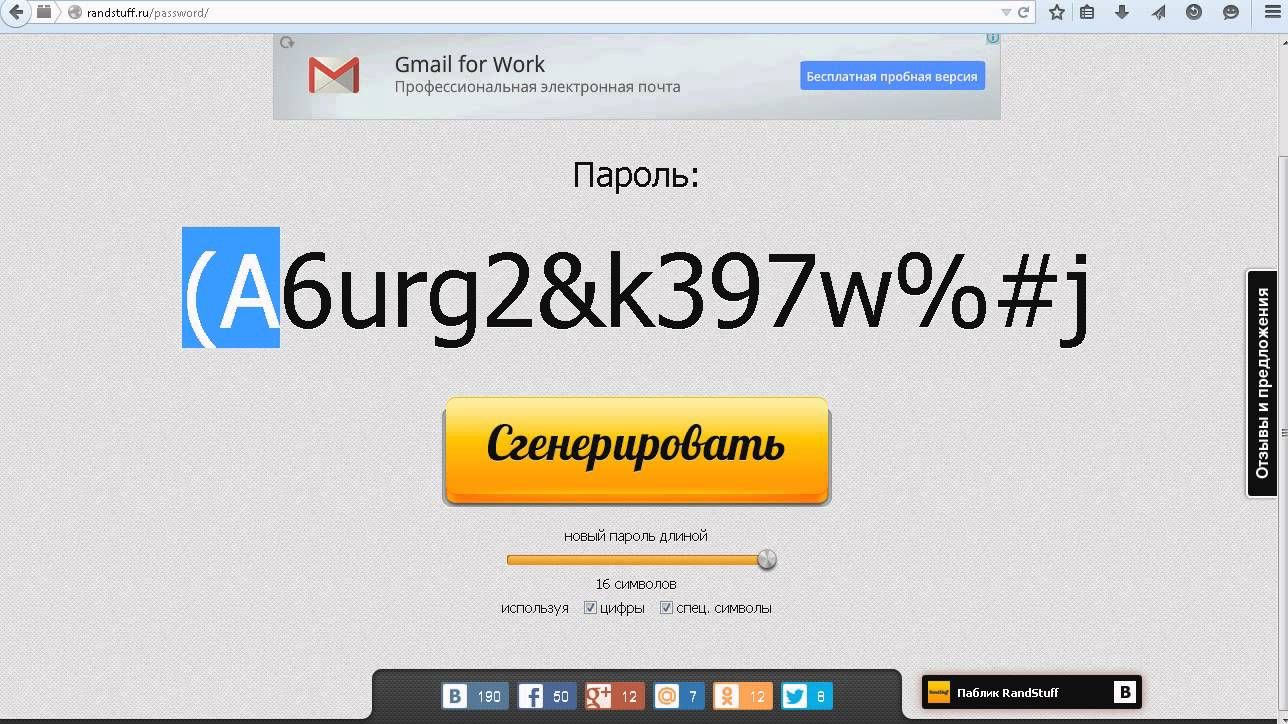
You don't have to bother with password guessing, but just use the generator. After setting the necessary settings, the password generator will give you a good combination that is resistant to cracking, which will be quite convenient to use.
Unfortunately, one of the most common passwords on the Internet is still - 12345. This is used by hackers who have software, which can simultaneously brute-force passwords to many mailboxes at once, and if such primitive passwords consisting only of numbers are set there, then attackers will easily gain access to the mailbox. And they can use it in different ways. Sometimes the box is used to distribute SPAM, and sometimes to extract certain information, so that it is possible to access the owner's computer or even electronic account.
Common wifi passwords
Of course, even the most simple passwords are words. For example - love, password, qwerty, etc. Strange, but despite the obvious changes in security and computer literacyHowever, many users still set similar passwords. In Russia, banal words are often established, but simply in Russian, which is also easily selected.
Password guessing using a brute program

In general, the technique of guessing a password for any system is programs like Brute-Force. The bottom line is that to mailbox, ICQ, social network account, etc., different passwords are selected. There is a whole database of passwords - sometimes several million. Obviously, all numerical combinations and commonplace words are there.
To this you need to add also the obvious things: you do not need to use the date of birth, numbers mobile phones, names and surnames of relatives and friends, etc. personal information, which, in principle, is quite easy to find out.
Secure password - use both Cyrillic and Latin; and big letters, and small. You also need to use numbers, special characters and, of course, a space. It will be quite difficult to find such a password. Here is an example of a good password - FdLjдв393ДФ _) !!) # (# (ldldmv44mvm.
Password storage software

Of course, this is difficult to remember, but there are already solutions. At the moment there are various programsthat store passwords in separate databases and use them as needed.
The use of this software is necessary insofar as it is almost impossible to remember complex passwords. And password managers make things a lot easier and more secure.
Since there are many password managers, it makes no sense to name everything, and the functions are almost identical. The most famous example is KeePass Password Safe ( free program). With this program, you can save all passwords in one place. An automatic password entry function is also available.
But there are situations when you still need to remember the password, for example, to access your account on a social network or mail. Here you can really come up with something memorable. But you should always remember that it is better to insert letters and Cyrillic, and Latin, numbers and special characters. Let it be 8-9 characters, but the password will be safe.