The operation of the Windows operating system is a complex process, which is possible only with the proper functioning of all software components. MacOS is also quite difficult to work with, but users do not have the ability to monitor system processes. In Windows, you can view all executable files in the "Task Manager", and some inexperienced users can scare them. A vivid example of a file that triggers an alarm is svchost.exe. Quite often in Windows svchost.exe loads memory or processor, and there is a feeling that it is a virus. Is this true? Let's understand.
How to protect yourself from re-infection
This does not mean that all programs of this color will be malicious or that all viruses are such, but first it is worth checking them. Putting the mouse over the programs, you will know the full location of the file. In the case of services, you will find out which services are working in this process. These are programs that perform tasks in the background. They are necessary for the proper functioning of the system. To identify suspicious programs, it is also useful to include signatures. In this case, you will see a new column with information about the company responsible for the program, and if the information was checked successfully.
Svchost.exe: what is this process, what are its functions and why?
The common view is that svchost.exe is a virus that has under itself the basis, but in practice, most often, this process does not carry any threat in itself. If you understand the functional responsibilities assigned to the this file, it is necessary to connect dynamic DLLs to programs and services that can not work without them. Each program uses its own svchost file, which can be located in different folders of the Windows operating system. 
How to get infected from this malicious program?
Generally speaking, viruses do not have a valid signature. Again, this does not mean that all unsigned programs are malicious, but this only reduces the amount of software that you need to suspect. The column just quotes this to confirm the strength of the instrument. Internet connections, performance, memory.
When you right-click the process and select "Properties", you can access a series of information. Try changing the "Memory" option. You can search the contents of the program memory. Click the "Process Memory" tab. Check the "Virtual Size" and "Working Set Size" parameters. Because of how the memory manager works, there is no single value for "memory usage" of the program. These two values-the virtual size and the working set-respectively determine the total usage of program memory and the approximate value of the actual amount of memory that the program uses.
The most common file svchost.exe can be found at the following addresses:
- C: \\ WINDOWS \\ system32
- C: \\ WINDOWS \\ Prefetch
- C: \\ WINDOWS \\ winsxs \\ amd64_microsoft-window
- C: \\ WINDOWS \\ ServicePackFiles \\ i386
If the file svchost.exe is located in other folders - this is an excuse to sound the alarm, but not an indicator that it is a virus. This rule also works in the opposite direction, if svchost.exe is even located in one of the above folders, it may well be a viral software.
Pay more attention to the working set, but if the value in the "virtual size" is too large, be careful: the program can suffer from a memory leak, which means that eventually it will pull out the memory that it does not need. Identify the process responsible for the window. If you want to know which process list is responsible for the window, you can use the "sights" next to the binoculars. You need to click and hold the mouse button, and then place the pointer in the desired window.
This is due to the fact that the program, while working on the file, should inform the system that it will do it. Two programs can not open the same file at the same time to prevent corruption or loss of data. There the file is locked before restarting. By clicking on the binoculars, you can enter the name or part of the file name.
Determine in which folder the currently active svchost.exe processes are located very simply. To do this, follow these steps:
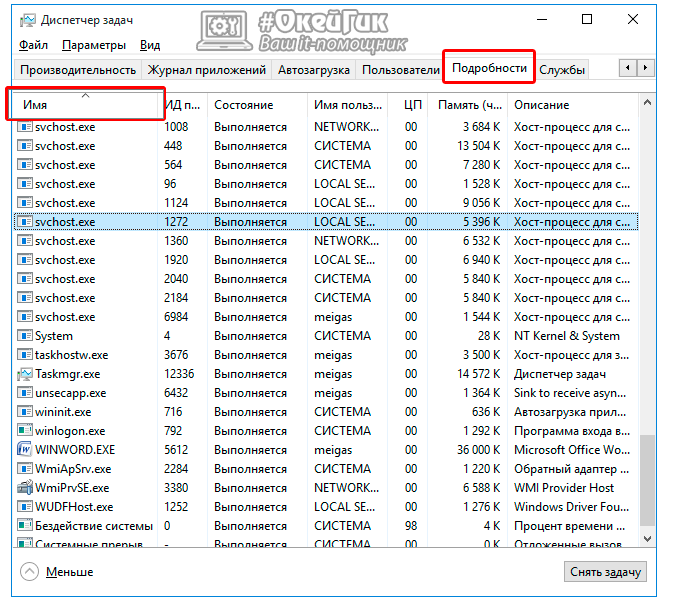
On Windows 8 and Windows 10 operating systems, you can see through the "Task Manager" a list of services that use the svchost.exe process. To do this simply - you must click on the suspicious process with the right button and select the "Go to services" item. It is worth noting that the names of many services are unlikely to be able to tell an ordinary computer user about something.
You can find out which one is open. You can double-click on the result that appeared. You immediately go to the process, and the file is "locked." But be careful: if you still need data from this file, it is better to close the program than forcefully close the file. If you have any questions about security, you can use it to use the comment area below.
All comments are read. He created and edited a Security Line, a security site and a forum that offers a free digital pest removal service, among other activities. This includes any other software that is open on the taskbar. 3 Disconnect the computer from the Internet. You can do this by right-clicking on the My Computer icon and selecting Properties. Then, on the System Restore tab, select the Disable system restore on all drives check box. This is important, you will also need spyware infections with a good full solution that will protect you from all Internet threats.
 The svchost.exe process may not be a virus, and if it loads the system, you should consider 2 scenarios:
The svchost.exe process may not be a virus, and if it loads the system, you should consider 2 scenarios:
- The computer is infected with a virus that sends out spam, extracts crypto currency for its creators or transfers other data to intruders;
- Due to inattention, the user does not notice that the malicious process is only hidden under the guise of the svchost.exe system library, in fact it is not.
If the computer is infected with a virus, and because of this the svchost.exe process loads Windows 10 or an earlier version of the operating system, you should check your computer for popular antivirus software. Be sure to install Firewall, which will provide network security for your computer.
Do you currently have a high-quality and comprehensive solution to protect against all types of malware that can get to your computer? Detects and blocks the latest and most dangerous forms of viruses and spyware. Consists of several levels of protection, protects against the latest cybercrime strategies, regardless of the type of attack or infection of your computer.
In this case, you will have to restart the service that it is working with. If you put the cursor over processes, you'll see which services are running. The information in this Knowledge Base article is addressed to a working environment where the system administrator is able to follow the instructions described below. If your antivirus program can effectively eliminate the virus and update all affected systems, reading this article will be redundant.
In the second case, you should recognize the malicious file svchost.exe, which is not, and then delete it.
How to distinguish svchost.exe from a system file
If the svchost.exe process loads memory or the CPU, you should verify the validity of the file it refers to. To do this, carefully check the name of the executable process. Below, we give a few tricks of intruders, which substitute the process svchost.exe for another, but close by name. Most often, the following schemes are used to disguise the virus:
If your computer has been infected with this worm, it may not be symptomatic or that one or more of the following symptoms occur. Among them are the following. Use secure passwords Administration, which are unique for each computer. Do not log on to computers using domain administrator credentials or other credentials that allow access to all computers. Make sure you have installed latest updates security for all systems. Deleting any overflow permissions for shared network resources, including the rights to write to the root of each resource. The self-cleaning tool can also remove this infection.
The above list only the most common options to disguise the virus, but there may be others. Take a close look at the process called svchost.exe and all the letters were spelled out in Latin.
In case you find a process that is masked by svchost.exe, but it is not, it should be deleted. It's quite easy to do this if you use the AVZ program.
A malicious program represents a user who logged on to the system and accessed network resources using the credentials of the user who launched the login. The server service must be temporarily disabled when the malware is removed from the environment. This is especially true for production servers, since this affects the availability of network resources. Once the environment is cleaned, the server service can be reactivated. If you incorrectly modify the registry, this can cause serious problems, and then carefully follow these steps: create more protection backup copy Registry before its modification, so you can restore it if there is a problem.
- This behavior can spread malware.
- Create a server service.
- This section, method, or task describes how to modify the registry.
How to remove svchost.exe from the AVZ program
Known antivirus utility AVZ is able to detect and remove unwanted programs, including viruses. It is distributed free of charge and has many useful functions. The AVZ program's plus is that it does not need to be installed on system disk. AVZ can be launched from a flash drive, external hard drive or directly from the downloaded archive.
Checking system cleaning
To check, compare the list in the service table with a similar system in which the infection is present. Pay attention to the name of the malware. This information will be required in the following order. Notes to the table of services. Replace the permissions for all child objects with the appropriate permissions specified here.
- Add these permissions to those listed here.
- Quit Registry Editor, and then restart the computer.
- One of the launch paths was not deleted.
To delete the svchost.exe file using the AVZ utility, you must do the following:
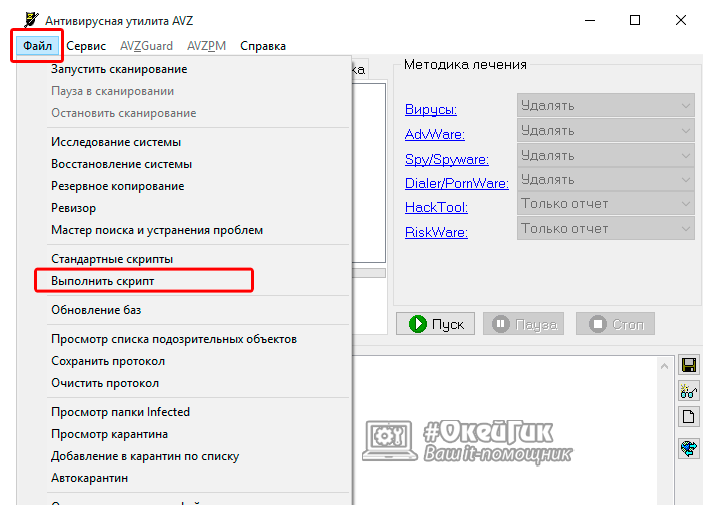 begin SearchRootkit (true, true); SetAVZGuardStatus (True); QuarantineFile ("path to the virus", ""); DeleteFile ("path to the virus"); BC_ImportAll; ExecuteSysClean; ExecuteWizard ("TSW", 2,3, true); BC_Activate; RebootWindows (true); end.
begin SearchRootkit (true, true); SetAVZGuardStatus (True); QuarantineFile ("path to the virus", ""); DeleteFile ("path to the virus"); BC_ImportAll; ExecuteSysClean; ExecuteWizard ("TSW", 2,3, true); BC_Activate; RebootWindows (true); end. Instead of the words "Path to the virus" highlighted in red, it is necessary to register the location of the svchost virus process. Above we have already told how to determine where the virus file is located, which is masked by svchost.exe. Copy the path to it (or write it manually) and paste in place of the highlighted red words. Attention: You can not remove quotes from the script - only letters marked in red.
After complete purification of the environment
Scroll to the end. . The following table lists the default permissions for each operating system. These permissions apply before the changes proposed in this article are applied. These permissions may differ from the permissions in your environment, so it is recommended that you take your permissions into account before making any changes. This is necessary to restore the settings at the end of the virus removal process.
Issues that are fixed in this update
Attention! However, translation is not always ideal. It contains errors in the binding of words, sentence composition or grammar, just as foreigners make mistakes when speaking in Czech. Microsoft is not liable for inaccuracies, errors or damages resulting from translation errors, or using incorrectly translated instructions in the client article.
Method 1
Method 2. Beware, this operating system is poisonous.
After successfully deleting the file that posed as svchost.exe, we strongly recommend that you scan the computer for viruses. There is a high probability that one of the programs generates new files that automatically start in processes and pretend to be svchost.exe.
Dangers lie everywhere. A bad driver may cause the entire system to malfunction. Incomplete applications leave a mess of the registry, which is the source of new problems. There is no panic. The chip will show you step by step how to perform a detoxification treatment that will return your physical form to your system. In addition, we will take precautions to ensure that systematic toxicity in the future is not so simple. How did you know that your system was poisoned? The processor is still heavily loaded, the windows open too slowly, the system startup is tedious, you need to wait a long time.
Wrote in the delete on tuesday, February 9, 2016
Malicious website blocked by svchost.exe virus ?
SvcHost stands for the service node. svchost.exe is an executable file, labeled as Generic Host Process for Win32 Services or, in other words, runs process SvcHost a bunch of Windows services, each of which has a specific purpose. svchost.exe is nothing more than an executable file that groups related Windows services. The process is used to store one or more operating system services, and this requires Windows file, which comes in handy when loading the required DLL files. So far, is it all right? Nothing stated so far entails a reaction "Oh, no! I found svchost.executable on my computer! "Well that's where it gets harder. Yes, there is svchost.executable, which is legal and necessary. But there is one that is fake, which only hurts your system and jeopardizes your privacy. So, how can you say that there is something? There is a way. A legitimate one should only be found in the C: WindowsSystem32 folder. If you find a file with the same name nowhere, it's a fake one! Do everything that you can get rid of fake files hosted on your computer! To get rid of it as soon as possible! But keep in mind that manual removal will be quite difficult, if not impossible. Think of the file as a plague that refuses to go. He simply refuses to leave your system. Even if you are sure that you have got rid of it today, you can be unpleasantly surprised by its appearance the very next day. They refuse to leave. The easiest way to do them is to turn to the help of a legitimate tool. Do what you should, but delete the file as fake, harmful as soon as possible.
Control: how much is the system infected?
And shut down the computer is not as fast as before. Healthy windows should close for a few seconds, sometimes it takes a minute. If you do nothing on your computer and do not need an operation in the background, use should be very low, about 5%. If more than one user is working on the computer, you need to mark "Show all users". Depending on the name of the process, you can guess what the process is. This identifies the application that is blocking your system.
How to get infected from this malicious program?
Fake SvcHost can represent and computer the Trojan horse. But as sneaky as it can be, it can not just pop up on your screen one day as if by magic. There's nothing magical about his sudden appearance. An infection, like one, using a fake .exe file as the front, is usually shown on your PC, resorting to old, but gold penetration methods. Their usually antics include the most common methods, like Hitching to ride with freeware or corrupted links or sites. In addition, pesky infections can slide their way in by copying their executable into the Windows folder or Windows systems. After that, it moves on to the next step, which makes changes to the registry to run this file with every single system startup. Whichever method of infection, the infection decides to appeal to, after it invades your computer, you will be bombarded with questions. Do not spend a lot of time and energy dealing with your everyday messes, stopping it hitting in the first place. Do your best to keep it away from the computer. Be careful and considerate of what exactly you are allowing into your system. Take your time when you install a tool or update and always do your due diligence. Who knows? Perhaps with a bit of luck, you will be able to save fake svchost.executable from your system.
If you find that this process is not necessary or even harmful, right-click it and select "Exit from the process." This will be won before the next computer startup - the process is most likely to be started with the system startup. You also need to remove it from the auto start. A list of the services that are on the system is displayed. It's not always so simple. Sometimes a bad driver is to blame, and you will not find it. Then you need to look for problems in the reports generated by the system. The Event Viewer is started, in which all messages are stored.
Why is Tisza dangerous?
SvcHost is component of Windows important. Perhaps that's why many malicious tools choose to disguise themselves as the SvcHost process. But do not despair! There are ways, you can determine the authenticity of this process. The best thing is to look into where exactly the file is located.exe. Initial system file - this can be found in the C: WindowsSystem32 folder or c: winntsystem32, or even in the DLL cache folder, depending on the Windows version you are using. Any other file with the same name located elsewhere is an impostor. It's more of a malicious program, using the name as the front to hide, and wreak havoc undetected. Well, once you determine the .exe file on your computer is fake, do not let it stay and wreak havoc. The bad thing is that any virus can load itself into memory using the process of legal windows svchost.exe , the most important is to identify all the services running on your computer and determine if there is one sneaky.
If you are looking for a problem with the driver, select "System." Here you need to look for warnings and errors. With some luck, you can find error reports in the driver. Then you will find out where the buried dog is. The advantage is that the system will not fail you and will not completely diagnose the problem. If he does not write, what's the problem, write at least an error number. First, create a system restore point. Do not forget about the security of the system.
Make sure that you have all the fixes on your operating system. We also suggest using an application that will regularly take care of your system. If you can find the problem, its solution is a bit. Especially often the drivers are updated frequently, so you just need to download a new one. If this is a software problem, the easiest way is to find an alternative. That's why they are trying to track your personal information with spyware. We regularly inform you on how to lay the tracks behind you.
Your computer is most likely infiltrated by a virus or trojan. And the virus or Trojan said for the appearance of fictitious Windows services. After starting the service, the infection you are stuck with, you can choose to connect to a malicious website and either transfer personal information that it has stolen from you or to download additional malicious software. So, the question is: are you ready to play with your personal and financial information? Are you willing to risk it falling into the hands of unknown third parties from hidden agendas? Are you ready to open your system more unwanted malicious tools? And, for how long do you think that this will last before it gives and welcomes you with blue screen of death? Are you ready to find out? Here's a hint: not. Protect yourself and your system, and do what's best for you and your future PC: remove the fake executable right away! This is for the best.
Virus removal procedure svchost.exe
Warning, multiple anti-virus scanners have detected possible malware in svchost.exe.
| Antivirus software | Version | Detection |
|---|---|---|
| Tencent | 1.0.0.1 | Win32.Trojan.Bprotector.Wlfh |
| Malwarebytes | v2013.10.29.10 | PUP.Optional.MalSign.Generic |
| NANO AntiVirus | 0.26.0.55366 | Trojan.Win32.Searcher.bpjlwd |
| VIPRE Antivirus | 22702 | Wajam (fs) |
| Baidu-International | 3.5.1.41473 | Trojan.Win32.Agent.peo |
| VIPRE Antivirus | 22224 | MalSign.Generic |
| Dr.Web | Adware.Searcher.2467 | |
| ESET-NOD32 | 8894 | Win32 / Wajam.A |
| Kingsoft AntiVirus | 2013.4.9.267 | Win32.Troj.Generic.a. (Kcloud) |
| K7 AntiVirus | 9.179.12403 | Unwanted-Program (00454f261) |
| McAfee | 5.600.0.1067 | Win32.Application.OptimizerPro.E |
| Qihoo-360 | 1.0.0.1015 | Win32 / Virus.RiskTool.825 |
svchost.exe behavior
- svchost.exe deactivates the installed software.
- General behavior of svchost.exe and some other text emplaining som information related to behavior
- Change the desktop and browser settings.
- Redirecting the browser to infected pages.
- Distributes through paying for the installation or bundled with third-party software.
- Inhibits Internet connection
- Steals or uses your sensitive data
- Displays fake security alerts, pop-ups and advertisements.
- svchost.exe shows commercial advertising
- Install itself without permissions
- Modifies the user Home Page
svchost.exe runs on Windows OS
- Windows 10 30%
- Windows 8 40%
- Windows 7 19%
- Windows Vista 7%
- Windows XP 4%
Geography svchost.exe
Eliminate svchost.exe from Windows
Remove from Windows XP svchost.exe:
Remove svchost.exe from your Windows 7 and Vista:
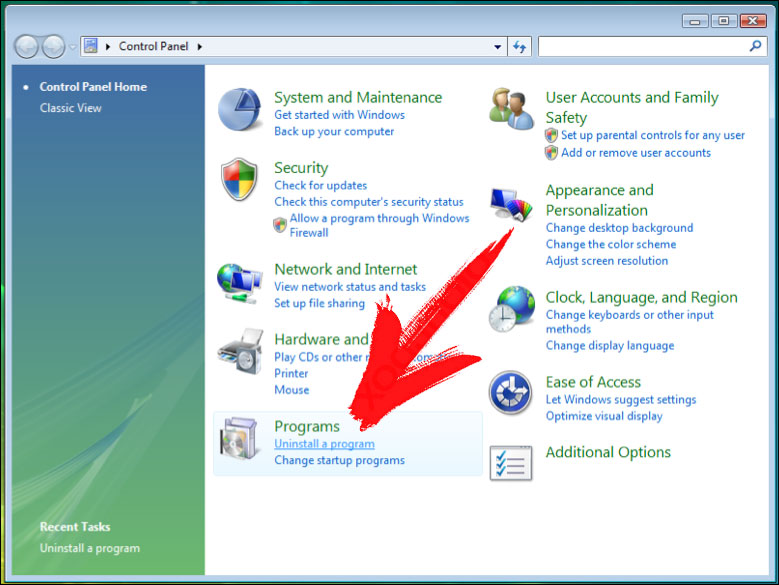
Delete svchost.exe from Windows 8 and 8.1:

Remove from your browsers svchost.exe
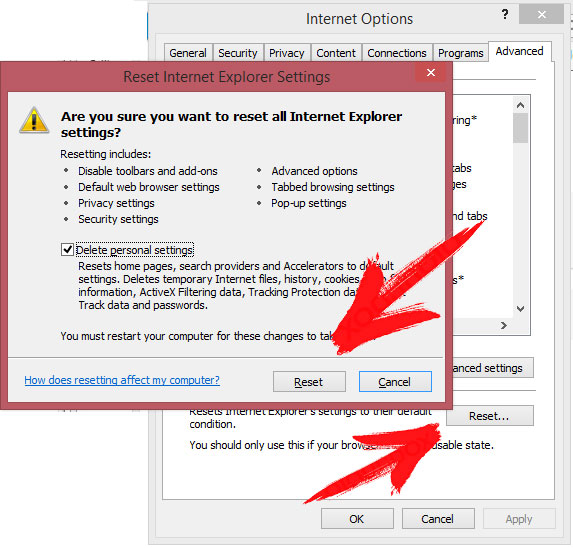
svchost.exe Removal from Internet Explorer
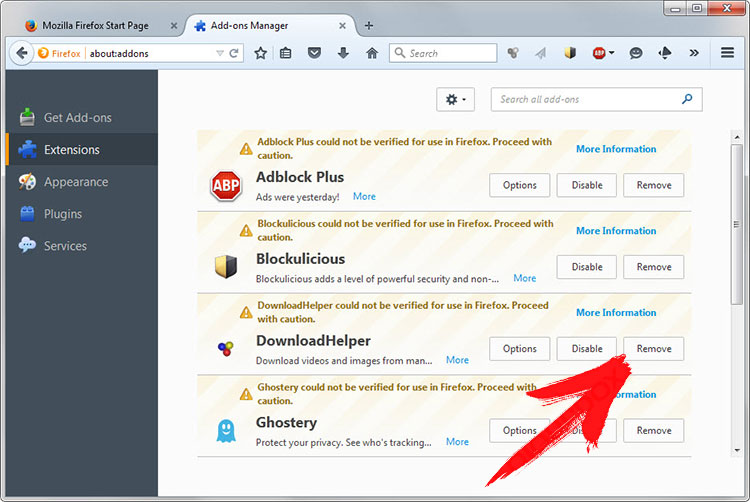
Erase svchost.exe from Mozilla Firefox
Stop svchost.exe from Chrome