For sure, it was quite recently, perhaps even the other day, or even today. Most likely, you were asked to come up with some kind of complex password, in order to protect your personal data from intruders.
Well, if you are registered on one or two sites, invented there some sophisticated combinations, remembered them, or even recorded somewhere. That's only the majority of modern people who are actively surfing the Internet, almost constantly, daily registered on various Internet resources.
How to be in this case and how each time to come up with a new complex password? You say, you can come up with one and use it on all sites. All would be fine, but if your account is hacked on one of them by tricky password selection, which prevents an attacker (machine) from breaking your accounts on other sites in the same way. First of all, he (she, it) will surely try that password, which once already worked. And all, forgive your personal data, accounts, profiles in in social networks, farewell to the whole virtual, and even personal life (who knows what you are storing in the global web).

Password Generators online
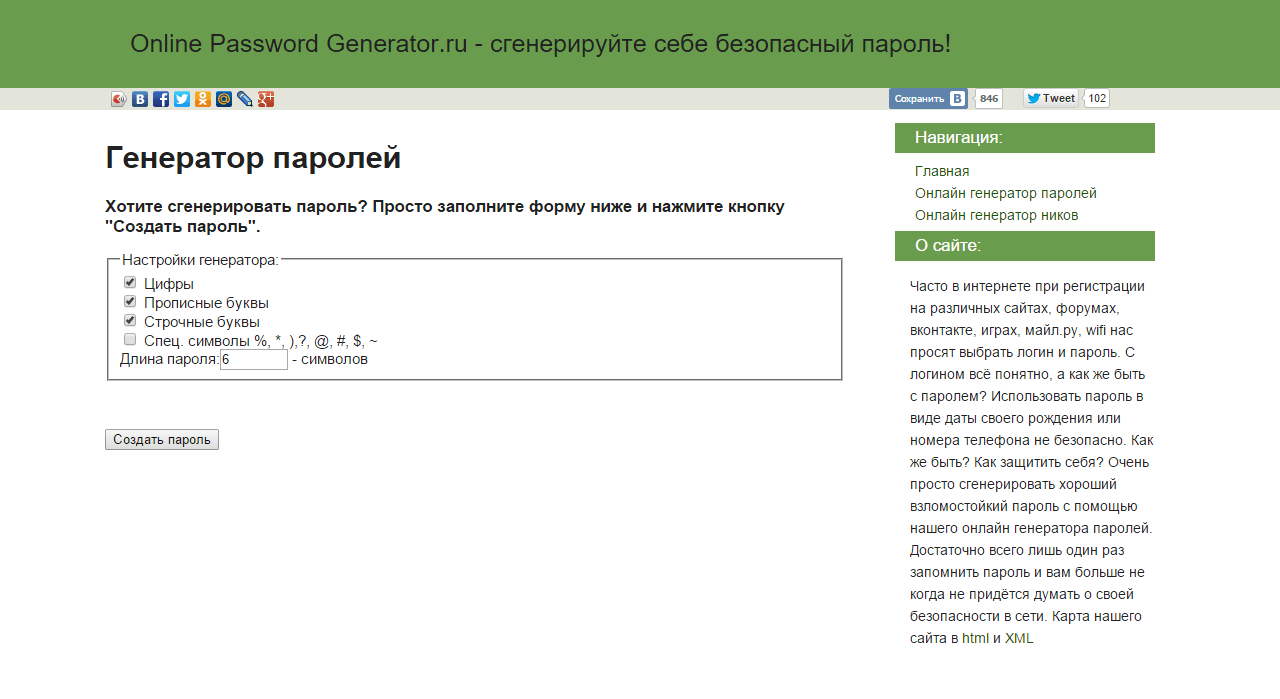
Fortunately, we live in the XXI century and in our time someone (or something) more intelligent can perform many tasks for us. There are many special services called online password generators. They will generate for you the password of any complexity, which you will only have to write down, and it is better to write it somewhere on paper, and not in a note or message.
Before you begin to consider the most popular online services for generating passwords, you should understand the very notion of a "complex password".
So, it's a password that uses lowercase and uppercase letters (for the forest of fidelity you can use two-letter letters), digits and various characters. Therefore, the date of birth, phone number and all the like are eliminated at once, so you need to come up with something more complicated, for example, ! 53YuioPq35Cgs & *%.

Password Generators online will cope with this task for you, and this procedure will take a few seconds. In a few clicks on these services, you can generate really, which certainly will not be able to crack anyone. The main thing is to remember what you will be given as a result of the password. But, as already mentioned, it is better to write down the password.

Below we will consider best password generators online, but first we note that all the passwords generated by such resources are created directly on the user's computer. They can not be intercepted.



Finally, it should be noted that the complex password created by password generators online, which uses 12 characters, among which digits, signs, capital and lowercase english letters and russian alphabets, It has 156 in the 12th degree possible combinations. To test each of them, the most powerful computer will have to spend several years. Actually, during this time you will have time to repeatedly change your password, using for this password generator online.
Most of the modern sites that store client information use the user's authorization (identification) systems. There are several common authorization scenarios:
1. The most common is the authorization of the user on the final site, using a pair of "login-password". In the database, such a pair is usually stored as a login in open access and the password is encrypted with some kind of hashing algorithm (md5, sha *, etc.). The password is almost never stored in the database in clear form.
2. As widespread as the first way of authorization - open APIs third-party services (facebook, vkontakte, openID, etc.). In this case, the login / password is stored on a third-party service, and relieves the user of a headache in the form of registration, and the developer, in turn, from the need to think about most aspects of security.
3. The least common method - cross-domain authorization (currently used on habrahabr). You can see the logic of work in the same place.
If in the first variant the problem of password theft (password hash) is practically excluded, then for the second and third cases this possibility can not be completely excluded. In the event that an attacker can get a hash of your password, it will be more difficult to decrypt it, the harder the password was unencrypted.
Consider the situation with four passwords:
As a hashing algorithm, it was not by chance that md5 was chosen, because there is a variant of pair hashes. Selection was carried out on the bases + iridescent tables + brutom. It is quite evident that the difference in the time for decoding complex and light passwords is visible. All calculations took place on a working computer, in a real situation you can safely reduce the selection time by 100 times. Thus, for your own security, the ideal option is to use authorization through third-party services, passwords must be complex (mandatory). I also advise you not to save passwords in the browser, but use the keepass + dropbox. To obtain strong passwords, the so-called password generator modules are commonly used. Especially for the purposes of our customers, we have developed our own free password generator. Using this tool, you can create in 1 second strong password, which will secure your data. JS code (used by jQuery):
JQuery (). Ready (function () (function getRandomInt (min, max) (// Function to get a random integer in a given interval return Math.floor (Math.random () * (max - min + 1)) + min ;) function getpwd (symb, len) (// Function for generating a password. symb - a string of characters to generate, len - password length var pwd = ""; for (var i = 0; i< len; i++) { pwd = pwd + symb; } return pwd; } function escapeHtml(text) { //Функция для экранирования спецсимволов return text .replace(/&/g, "&") .replace(//g, ">") .replace (/" / g, "" ") .replace (/" / g, "" ");) var chars = [" abcdefghijklmnopqrstuvwxyz "," ABCDEFGHIJKLMNOPQRSTUVWXYZ "," 0123456789 ","! @ # $% ^ & * () _-<>,. ();: No? "]; // Collection of jQuery characters (" # generate "). Click (function () (// Generate passwords for the col- umn if (jQuery (" input.innerVars: checked "). Length\u003e 0 && jQuery ("# countpwd"). Val ()\u003e 0 && jQuery ("# countsymb"). Val ()\u003e 0) (var genspwd = "", symb = "", obj = jQuery ("input.innerVars : checked "); for (var j = 0; j< obj.length; j++) { symb = symb + chars.value]; } for (var j = 0; j < (jQuery("#countpwd").val()); j++) { genspwd = genspwd + "
"+ escapeHtml (getpwd (symb, parseFloat (jQuery (" # countsymb "). val ()))) +"
";) jQuery (" # result "). html (genspwd);) else (jQuery (" # result "). html ("
Select values for password generation
"); } }) })
Html code (without styles):
Lowercase Latin lettersCapital Latin lettersFigures (0-9) Special characters (! @ # $% ^ & * () _-<>,.{};:№?) CharactersNumber of passwordsLiked? Repost!
Our passwords on Facebook, ATM, etc. are electronic locks that store our confidential information from unwanted access. There are two types of passwords: conveniently pronounced, which are easy to remember and effective enough, and random, to crack which is much more difficult.
If you checked the level of complexity of your password and want to increase it, but you do not want to install desktop tools to generate passwords, then you came across the necessary article.

In our review, you will learn about 25 online tools with which you can quickly and easily generate conveniently pronounced and random passwords. The best thing about all this is that the online password generators listed in this article are not only free, but also do not require registration and subscription.
Generators of conveniently pronounced passwords
Perhaps conveniently pronounced passwords are not as reliable as random ones, but sometimes it's better not to risk and create a password that can be remembered so that you do not have to restore it later forgotten password, is not it?
A simple and effective password generator. You determine the length of the password and its version - a conveniently spoken or complex random one. To have a random password that best suits your needs, use the 7 options available (you can choose more than one).

Depending on your wishes, APG Online can generate up to 999 passwords per click. The program also allows you to save your settings in case you apply for a new password.

Password Boy is an easy-to-use password generator that quickly and qualitatively performs the tasks assigned to it. Just select the type of password and the set of characters that you would like to include in your password.

Perhaps the most simple to use online tool. It is ideal for those who want to get the password in a short time and without unnecessary fuss. The generator is available in 14 languages. To get the password, just click "Generate new password"!

This two-stage generator will allow you to select the desired password template, and then give out passwords that match the parameter you specify. You can choose uppercase and lowercase letters, numbers and / or symbols. If you need a conveniently pronounced password, then you will get a great option!

Vint.ca makes it possible to choose the "comfort level" of the password. Less conveniently pronounced passwords are harder to crack, and more - easier to remember. For example, how difficult is it for you to remember "maliLulu"?

This generator creates only conveniently pronounced passwords, composed of lowercase letters. All you need to choose is the password length (maximum 64 characters) and the desired number of passwords (maximum 1 000).

The essence of Xkcd's job is to create a password by carefully mixing four simple words. It is believed that even the most obscure words are bad for a password, since passwords consisting of vocabulary words can easily be cracked. If you do not take this into account, it would be interesting to see what the Xkcd Password Generator will offer. For example, I received the phrase "a small old bean story" as the password. Here you can also find an explanation of their way of generating passwords in the form of funny comics.

Well, this generator seems to us quite effective. Consonant sounds remain, and vowels are replaced by numbers or symbols.

Get a simple and memorable password consisting only of lowercase letters and numbers (not very recommended) or a stronger, conveniently pronounced password such as "sc @ ryLeaf92".

Generators of random passwords
Unlike conveniently pronounced passwords that are compiled on the basis of your personal data or simple dictionary words, random passwords are just a collection of meaningless characters that are not for the hacker's teeth, and can be classed as "very complex". Some of these generators also offer an option to eliminate ambiguous characters, which at first glance look almost identical - 'i', 'I', '1? or '0 ?,? O' and 'o'.
LittleLite Password Generator is an extremely simple and consistent program. It is enough to choose the necessary sets of characters, the length of the password, and it's ready.

The purpose of this generator is to create an easy to remember password, using for this purpose some interesting phrase or, better yet, the name of the song. Take the first letter of each word, add a few punctuation marks, and replace some letters with similar numbers. To use the generator or not is up to you, but it seems to us, it was interesting to make such a password yourself, how do you think?

A fast generator that avoids ambiguous characters. It will be an excellent choice for you if you are tired of the fact that your Wi-Fi is constantly hacked, and friends complain that they often incorrectly enter your password because of the presence of symbols like '0? and 'O'. And this is not all that Random Password Generator offers, you can also set such parameters so that your password can be pronounced.

Password Bird creates passwords by combining parts of words and numbers that are close to you for certain reasons. Thus, you get your unique memorable random password.

Here you decide whether you want to completely eliminate ambiguous characters (i I l, etc.) or vice versa, some specific include in your password. If the output password is too difficult to remember, you can switch the pronunciation settings to "Normal" and get something more easily remembered.

If you need an easy-to-remember password, then all you have to do is select letters or numbers and determine their number. Or you can diversify your password with symbols and capital letters.

Can not decide which options to use? Read the recommendations for using this convenient generator. It is best if your password consists of more than 14 characters. And, of course, do not forget to include in it figures, symbols and letters, which are often confused.

Norton not only protects users' devices from viruses and hacker programs, but also ensures that their password is not hacked. In addition to the standard feature set, you can also exclude any similar characters in your password.

Password Chart is a fun way to generate secret codes, very similar to the one we used in high school. To begin with, think up and enter a phrase (preferably something funny and easy to remember). Then either print the table and do it yourself, or save time and re-convert it using the generator. As a result, get the full gibberish, which only you are destined to remember.

The program not only generates passwords, but also subsequently assesses how strong they are.

Free Password Builder allows you to completely eliminate some characters or increase the probability of their appearance in the password.

A generator can create as many passwords as you want. You will also be prompted how best to memorize the received code.

The generator combines all the basic functions plus some additional features, such as limiting ambiguous characters and demonstrating phonetic pronunciation.

Random Password helps indecisive users to choose the format of the password, offering them to decide on two points-length and symbols.

If you want to instantly get a complex password, the Secure Password Generator will suit you for this as well as possible.
Other Password Generators
So, we have briefly reviewed the 25 best online password generators. The following is a list of 9 useful tools that you can get acquainted with:
1. - Generator with a neat minimalist design that creates passwords in an instant.
2. - generates a password and immediately determines the degree of its complexity.
3. - Excellent for generating a reliable WEP-key.
4. - Generates passwords without multi-valued characters, which can easily be confused.
5. - A simple and effective program that can generate up to 500 passwords at a time.
6. - will make your password as complex and reliable as possible.
7. - another simple generator; just select the length of the password and their desired number.
8. - it is enough simply to set the length of the password and determine whether it should contain punctuation marks; everything else will do Strong Password Generator.
9. - automatically excludes multi-valued characters.
Thanks to this online generator you have an excellent opportunity to easily create a password of a given length and complexity. The password is the guarantor of the protection of your information. You know who owns the information, he owns the whole world! So it's not superfluous to protect your data (probably extremely important) with a long and catchy password. The online password generator will pick up such a combination of symbols that will allow you not to worry about the safety of your personal data. Try it yourself right now!
- dtino5pk3f
- r34dosheaa
- gxje3dmk6i
- ttvvzebzzy
- oom1syw68y
- dm5qq7u63o
- 3nfr0o2o0s
Please help the service with one click: Tell your friends about the generator!
Password generator program
To find the correct password, let's first find out what it is. A password is a simple set of randomly selected characters, an identification code for recognition. The system will not be able to do this without entering this particular set.
There are cases when passwords are selected, recognized or simply guessed. It is to prevent such incidents that you need to create a good and reliable password with the help of an online password generator.
Generator of random passwords
To create a complex password, follow the brief instructions:
- Choose the characters of different case: big and small letters, numbers or punctuation marks for absolute difficulty;
- It is not recommended to take known data for the password, such as date of birth, name and surname;
- Better: use the random password generator for this purpose online.
How does the password generator work?
Get a complicated password online is quite simple:
- Select the password length (up to 20 characters);
- Check the boxes next to the characters you want in the password. You can choose either one or several options: numbers, uppercase or lowercase letters, punctuation, additional characters;
- And just click the "Generate Password" button.
And now useful information for reflection. If you put 6 Latin characters of one register on your password, the hacker will recognize your password in 31 seconds, if 8, then for 5 hours 50 minutes, if 10 characters - 164 days, if 12, then 303 years.
If you put 6 Latin characters of different registers, numbers and punctuation marks, you can pick up the password in 2 hours 45 minutes, if 8, then it will take 530 days, if 10 - 6700 years, if 12 - 30, 995, 620 years.
Passwords for users
Do you keep the keys to your apartment well? You try not to lose them, right? Do not give into the hands of anyone horrible? Do you choose reliable locks? The password is the key to your information, your mail, your computer. After all, from your account. It is important! And to treat the choice and storage of passwords should be taken seriously.
Everyone agrees that sometimes information is more expensive than the computer in which it is stored. All lock the rooms and will grieve if the computer is stolen. And if you steal information? Of course, the security of information depends not only on passwords. About setting up access rights, firewalls, programming with an eye to the fact that you will be broken I'll write later. And here about the most user part - selection of correct password and reliable conservation of its a secret.
Hacking due to badly chosen or badly kept secret passwords occur much more often than because of incorrect configuration or errors in the software. There are three ways to break the password protection.
- Password Recognition - Social Engineering
- Selection of the dictionary - Dictionaries are different
- Full search of possible combinations - BruteForce - Brute Force method
Choose a password
| Good Password: | Bad password: |
|
|
Counteraction to the third method of hacking requires that the password be as long as possible. The more characters the more options are available - the search of all will take more time. Using Large and Small Letters alternately, as well as numbers increases the number of variants of each symbol - a complete search will be even more difficult.
Any words from the dictionaries are not suitable. Even specific professional terms - there are thematic dictionaries - they will be picked up on them. The speed of brute-force passwords can sometimes reach hundreds of thousands and even millions of options per second (!) On an ordinary PC. The thickest dictionary hardly contains a million words. So this password will be picked up in a second!
Dialing Russian the words in the Latin layout is also a bad idea. Between the layouts there is a one-to-one correspondence - the thickest Russian dictionary can be translated into "Latin-Tabar" and such a password will be selected from this dictionary. Another thing is typing mixture Russian words in the Latin layout - 90soka is typed 90. When the dictionary word is unpredictably mixed with delirium, the attack on the dictionary will be greatly hampered. Only this password should not be used! He is already certainly included in the crackers, as published by Yandex, and certainly there are "clever and clever" who took it "to themselves." Do not trust the advice to write a word where a number of letters are replaced by the numbers MO5KVA (S is replaced by 5). The point is that there are few such replacements: S-5, ch-ch-for-4, to-2, l-L-1, з-З-3, b-б-6, and perhaps all. The cracker will have a chance to build from a conventional dictionary, a dictionary with such replacements in different versions. Yes it will increase the number of words, but not on orders. So attacking such passwords using a modified dictionary can be successful.
Not suitable as a password: your name, surname, nicknames of pets, the name of the wife, children, friends. In general, names, names of cities. Numbers of telephones, cars, passports, rights, houses, apartments. Date of birth. Another similar. Any information related to you can be guessed. Its relatively not much.
Well of course do not use such combinations as 1, 123, 12345, qwerty, asdfgh, zxcvbn, xxxxxxa. Password can not be your login. You can not use words like god, sex, password, ok, yes - very popular passwords in the very distant past.
Use different passwords for access to different systems. Even following all the tips of this document does not give 100% guarantee that your password will not be recognized. 100% guarantees do not happen in nature at all! And if a black day comes, the problems will only be with one of the systems.
There are different opinions whether passwords use punctuation elements (not alphanumeric characters). On the one hand, this increases the alphabet, and hence the number of options. On the other hand, these symbols carry problems. I advise you to manage without them. Follow the rules a good password - It's enough.
Password storage
The perfect place to store the password is your head. You can steal a briefcase, a cell phone, a notebook, a piece of paper / a floppy / flash drive with a password, but your memory is much more difficult to steal. So if possible, passwords should be remembered and stored in your memory.
From the rule of memorability there is an exception. To access the sites, you can generate very reliable, but completely unremarkable passwords (for example, qmPHuwBgseb8Cw37) and store them in the password manager. You do not have to type this password easily through the clipboard. However, remember that you will have to take care of the security of the password database.
Never tell anyone your password. Even a charming girl! Is there really nothing to talk about with her? Another user must work under his account and naturally with his password. Administrator your password is not needed. The admin always has enough rights in the system and without knowing your password.
Do not say the password out loud or by phone. Do not mutter it to yourself while you are typing. This may seem ridiculous, but I've seen too many users who have done this. And once in his life he himself uttered the password aloud to the whole corridor. :)
You should be able to quickly type your password. Often happens so that it is necessary to type at strangers. If an outsider is experienced, and you are slowly typing, he will remember your password at a glance at the keyboard.
Passwords for professionals
This article is an attempt to collect on one page the most important thing about password features, their application, choice, storage. About a lot here you can paint more details, but hardly worth it. Experience everyone still gets himself, and landmarks "where to dig" here just and marked.
Things that everyone knows, but do not always remember
The password is just a set of characters. More often than not, the system has no other way of knowing you, except by password. So anyone can enter correct password and get the appropriate authority.
The password can be recognized, guessed or matched. Add opportunity in some cases get around protection system due to the weakness of the applied algorithm, errors in implementation, backdoors, and get a complete list of what should be feared.
For example, passwords for otsharenye resources in Windows-9x could pick character-by-character! Do I need to explain how it simplified their selection by the attacker?
From the weaknesses of the algorithm and software error protection options only two. If there is a patch that corrects the situation, put it; if it does not, do not use a weak system. There is a very rare third option, when the source is open and you are able to write such a patch yourself. Those who can do this usually do not need a reminder to contact the authors so that corrections are made to the development repository.
Over time, there is a clear tendency to the fact that the hole is getting smaller. Today, burglaries due to badly chosen or badly kept secret passwords occur much more often than because of incorrect configuration or software errors.
Learning password social engineering, spying on typing, keyloggers, slovenliness (a piece of paper with a password in a prominent place). Guessing - brute force dictionary dictionaries are different (modified by syllables, rules) Selection - full search of possible combinations. BruteForce - Brute Force Method
Here are three ways to break a password protection when it cannot be bypassed using the imperfections of the system. It is in these three areas that you need to think when choosing and storing a password. And also reading further this article. It all depends not on distant developers, but on the user. From US. From you.
Length matters
The two main characteristics of a password are the number of characters (length) and the number of variants of a character in each position (alphabet).
As is known from combinatorics, the total number of possible passwords for a given length (L) and alphabet (A) is calculated as (A ** L). A to the power of L. The time (T) for which the password of a given length will be guaranteed by the Brute force method is less than or equal to (A ** L) / V, where V is the brute force. So, we can write T<=(A**L)/V. Эту формулу обычно называют формулой Андерсона. Следующая таблица вычислена по этой формуле и наглядно демонстрирует зависимости указанных величин.
|
6 characters |
8 characters |
10 characters |
12 characters |
|
|---|---|---|---|---|
|
26 (Latin all small or all large) |
5 hours 50 minutes |
163.5 days |
||
|
52 (Latin alphabet with variable case) |
1,239,463 years |
|||
|
62 (Latin alphabet of different register plus numbers) |
252 days 17 hours |
10,230,425 years |
||
|
68 (Latin different case plus numbers plus punctuation.,;:!?) |
2 hours 45 minutes |
30,995,621 years old |
80 (Latin for different case plus numbers plus punctuation.,;:?? Plus brackets and the alphabet 80 (all symbols plus not alphanumeric) will be searched for 5 years and 4 months .At the same time, all variants of the 10-character password on the alphabet “only letters,” will go over almost a hundred times longer - 458 years. If you add numbers, it will be 2,661 years.
It can be concluded that, as expected from a power-fast, fast-growing function, increasing the password length by only 2 characters gives 500 times (2661 / 5.32) more options than increasing the alphabet by 18 characters (from 62 to 80).
If you carefully read the brief table of the commandments for choosing a password, you will notice that it does not have a usual recommendation to use symbols other than large and small Latin letters and numbers. I advise you to create longer passwords than to include special characters in them. Such as.,:; () () # $%
Indeed, "as a rule" special characters in the password do not cause trouble. At least the programmer. The password is probably the only user-entered information that web services programmers may not filter for unwanted characters. All other user input is required to be filtered. This has been said so many times that I want to apologize for the repetition.
I prefer to make the password a little longer, and at the same time on the "normal" password alphabet - 62 characters. Why? Passwords should not be pronounced, but pronouncing affects memorability. And special characters reduce the pronunciation.
In addition, it happens that we in life get on non-standard keyboards. How long will it take the user to find where the dot on the French keyboard is? Consider that everyone who sees this will immediately notice in what position he has a point. In this case, the actual password length will be reduced by one character! And as calculations show, it is better to “lose” a piece of the alphabet than to reduce the length of the password.
Very important note that the mark’s usual place is equal in the formula less or is equal. Suppose an attacker has somehow learned that your password is 9 characters long, and is going to consistently go through all the combinations: aaaaaaaaa, aaaaaaaab, aaaaaaaac and so on to zzzzzzzzz. What happens if your password is really aaaaaaaaa? He will be right there! Do not think that in this case the most profitable zzzzzzzzz password, since it will be tried last. Algorithm selection is easy to change and perhaps the attacker will just start from the end.
He can start from the middle. There can be a lot of starting points if the calculation is performed on a multiprocessor system or a cluster in several threads. Therefore, each character of the password should be chosen at random and hope that it will be far enough from the starting point of the search algorithm. Remember, time in a given formula is usually always less calculated on the right side. Time calculated guaranteed finding a password. During this time, will be enumerated all possible combinations.
Enumeration speed
The search speed can vary greatly for different cases. This will be discussed in more detail later in the section on password usage. I will not give similar tables for other speeds. Since the dependence is linear, everyone can easily recalculate the indicated times at their own speed.
For example, if the brute force speed of 1,000 passwords per second times in the table must be multiplied by 10,000. If the search speed is 15 million passwords per second, these times should be divided by 1.5. Fortunately, brute-force speeds of 100 million passwords per second are not found on today's equipment. So, reducing the maximum time for finding a password by an order of magnitude specified in the table is already impossible.
"Fortunately" because after all the password systems are designed to protect. Such big hacking times will not be very fortunate for you if you forget your own password.
If an attacker can not guess the length of your password and will have to go through all the password options with a length of say from 5 to 8 characters, then the time for such a complete search can obviously be estimated as the sum of the times of sorting out 5, 6, 7, and 8 -m character passwords. From the table of times it can be seen that the main component in this series is the time for searching passwords of the maximum selected length. The remaining terms are sometimes negligible.
If you yourself are in the role of an intruder, for example forgetting a strong password for your own archive, then spending 252 days and 17 hours to sort through all 8 character passwords, you can easily spend 95 more minutes to go through all 6 symbolic passwords. By the way, the situation is very real. On the Zip archives of the latest versions there is no possibility to bypass encryption, and the speed of a complete search is just 10 - 15 million passwords per second. 250 days to restore the forgotten password ... Do not let you God forget the strong password. And not resistant you should not use.
Password Generators, Memorized and No
You should not expect memorized passwords to be also pronounced and familiar as ordinary words. However, if we compare them with the fact that the generators are given in random, non-remembered passwords, then of course they are more pleasant to remember.
Do not forget about the main password generator - your own head. Thing indispensable in the economy, but sometimes buggy. Once in my life, my friend and I had already come up with a password, looking at things in the room, mixing names. It seemed to us that we will never forget. As luck would have it, we encrypted a rar-archive with this password. When in a couple of months we needed to decrypt it ... The password was remembered only by a miracle and by incredible brainstorming.
Generally, mixing words is a good idea. If you do it thoughtfully, slowly, adjusting to yourself, you can get a really easy to remember, but hard-to-find password. Just for frequent use as a password to the local system or password manager. That is, these passwords must not be forgotten.
You need to mix words to get a password not by syllables, or not always by syllables. Otherwise, such a password can be selected using the modified dictionary obtained by iterating over the combinations of syllables of dictionary words. Such a dictionary, although it will be more than usual, but the number of words in it will be relatively small.
Since the passwords must be typed quickly so that no one peeps, you can require the optimization of the password generator for speed dialing. However, in the listed generators, I did not come across this option. In addition, it is not always convenient to simply alternate characters from different sides of the keyboard in the password.
I believe that manual optimization can best help here. Take the password, even if it's generated by the machine. Try to pick it up. See how memorable it is for you. Optimize - change a few characters. In the end, not many passwords require this optimization. Only according to the "Scheme" are the most frequently used, most important.