Man is a social being. This definition implies first of all communication between different people. With all at once or separately it does not matter. Our distant ancestors were able to realize the opportunities for communication that were laid down by nature. The air exhaled in a special way began to take shape into words, which later received a graphic representation in the form of writing.
However, communication with sound remained and remains the most preferable. For a long time, we used natural ways of transmitting sound waves: shouting as far as possible while gesticulating with all possible limbs, showing that we want something from someone who is far away now; or it was just possible to transfer what was necessary through an intermediary.
In the second half of the XIX century, the voice began to be transmitted by wire. The speed increased by several orders of magnitude - now it was enough to pick up the phone and in a few seconds you could hear a person on another continent 20,000 kilometers away. Technologies of the last century made communication even more accessible and convenient. She became wireless. Today you can "catch" almost anyone wherever he is. Another thing is that not everyone is happy about such “freedom”, especially those for whom it has become another way to control, but the story is not about that.
Computers allowed to transmit not only sound (in particular voice) over distances, but also text, and recently video transmission has become an increasingly popular service. And if you observe the latest trends, then computer networks become: a) wireless; and b) global. It is in all the diversity of wireless digital network standards that we will try to understand this article.
Cellular communications, the latest generations of which are persistently becoming "native" not only for phones, but also for computers, we will not touch. This is done in our other article: "". Here we will touch on those networks that are created at a less "global" level, but at the same time are quite common.
Many modern wireless standards support work with almost any PC, but some of them are designed for somewhat less universal, but at the same time very popular devices. For example, cell phones. Indeed, many of them today can transmit and receive data not only from GSM networks (NMT, CDMA and others), but also conduct data exchange with local devices. It is with short-range wireless networks that we begin.
Bluetooth
The Bluetooth standard (or as it is popularly called “blue tooth”) is one of the most famous and popular today. It was developed in 1994 by two specialists from Ericsson, Sweden, Jaap Haartsen and Sven Mattisson. The main purpose of Bluetooth is to provide data exchange without wires between two or more devices.

Since the origin of the "tooth" was a company engaged in the production of mobile phones, this technology was created for these devices. Is it any wonder that the Ericsson R520 was one of the first phones equipped with the Bluetooth module? By today's standards, it is a very weighty and functionally deprived "brick", which in its time was unclaimed.
Why? Yes, because 6-7 years ago, Bluetooth was literally equipped with a couple of devices. Exactly the same was the situation with Wi-Fi. What was the point of letting Apple get an iBook with an optional wireless network card if there were only a couple of access points for a fabulous price? But Wi-Fi could easily be paired with a conventional wired network, which is not possible with Bluetooth. After all, for data exchange, not all the standardized TCP / IP protocol is used at all, but its own. But more about that later.
For now let's touch the history of the issue. On May 20, 1998, the creation of the Bluetooth Special Interest Group (SIG) was officially announced, which began to develop and adopt standards for this technology. Initially, it included Ericsson (now Sony Ericsson), IBM, Intel, Toshiba and Nokia). Later they were joined by others. To date, the group has adopted six Bluetooth standards:
Bluetooth 1.0 and 1.0B
The very first versions of the standard had many errors and flaws. When pairing devices, there were various problems, the connection was unstable.
Bluetooth 1.1
The new version of the standard eliminated many errors 1.0B, and was also adopted as the IEEE 802.15.1-2002 standard. This added support for working through channels without data encryption, as well as support for the Signal Strength Indicator (RSSI).
Bluetooth 1.2
Version 1.2 was the peak of the development of the first generation of "blue tooth". Until now, you can find in the sale of the device with its support (for example, laptops or phones of three or four years ago). Among its changes are the following:
faster search for devices and connection to them;
increased stability of the compound, especially when driving;
higher data exchange rate (in practice, up to 721 Kbps;);
improved quality of communication with the sound transmitting headset;
added support for HCI (Host Controller Interface).
This version was adopted as the IEEE 802.15.1-2005 standard. But, pretty soon it was replaced by the second generation of Bluetooth.
Bluetooth 2.0
Bluetooth 2.0 has become quite a significant event in the digital industry. The new “teeth” could now “chew on” much more data, which is clearly indicated by the post-fix "EDR", added to the updated standard name: Bluetooth 2.0 + EDR. EDR means Enhanced Data Rate, which freely can be translated as "Teeth in three rows." Joke. In fact, the translation sounds like "Extended bandwidth". The speed in some cases increased by 10 times, but did not really exceed 2.1 Mbit / s, and the peak value is 3.0 Mbit / s.
Interestingly, Bluetooth 2.0 without EDR is Bluetooth 1.2 with bug fixes. Some devices support exactly this version of it, although most manufacturers have provided increased speed data transmission. In addition, power consumption has been reduced.
Bluetooth 2.1
Most recently, Bluetooth 2.1 has been adopted. This happened already during the stay of our project, about which we even wrote the appropriate one. Innovations have been made slightly. Among them - an even greater reduction in power consumption, accelerated pairing, better immunity and others. Until now, the support of this version is not attended to by many. So modern laptops (for which the data transfer rate is much more important than for mobile phones) are still equipped with Bluetooth 2.0 + EDR controllers.
Bluetooth 3.0
Of course, the development of Bluetooth has not stopped. Although today there are quite a few alternatives to this standard, which will be discussed later, the development of the Bluetooth 3.0 standard, known under the code name "Seattle", is already underway. That he will be even faster, you can guess so. The Bluetooth SIG organization wants to adapt the UWB technology (somewhat lower about it), capable of providing speeds of up to 480 Mbps (here, without undue modesty, we can talk about several hundred “rows of teeth”).
If this concept is implemented, Bluetooth will become a serious competitor to the actively developed and already implemented Wireless USB standard, which, oddly enough, is based on the same UWB specification. But more about that later.
Of course, in addition to significantly increased bandwidth, new features will be added. So it is planned to introduce support for special information points that will contain any information (advertising, weather data, stock prices, currencies, etc.), and it will be possible to read it from them. It is also expected to simplify the pairing of devices, thanks to automated management of topologies. An alternative to MAC and PHY profiles will be introduced for data transmission, which will reduce energy consumption with low data flow, as well as increase the speed if you need to transfer a large amount of information.
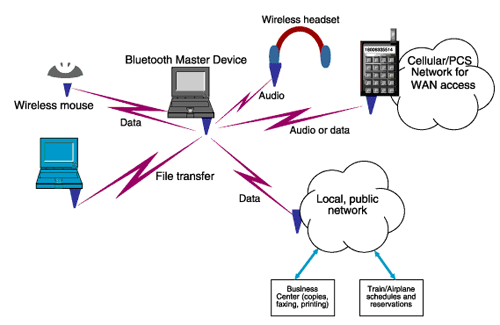
Now consider the principle of operation of Bluetooth. This standard does not work with access points like Wi-Fi — any device equipped with an appropriate controller can act as an access point. Conventionally, it is called a "master" and forms around it a "piconet" (piconet), into which up to seven other devices can enter. More precisely, seven devices can be active at a given time, while another 255 pieces may be in an inactive state, which is reversed if necessary.
The piconet can be interconnected. Then several devices will act as a bridge for data exchange. But while full support for this functionality has not appeared. However, it is she who should be implemented in future versions of the standard.
At one point in time, data can be exchanged with one device. If you need to give the data to another, then the switch quickly. Parallel transmission is also possible, but it is rarely used. At the same time in the piconet any of the slave devices, if necessary, easily take on the role of master.

Provide Bluetooth support modern computers Special USB adapters are designed. Many modern laptops of the average price range (from $ 1000) usually have a built-in controller. Controllers come in three classes:
Class 3. Power is 1 mW. The range of about 1 meter;
Class 2.Power 2.5 mW. The range of about 10 meters;
Class 1.Power 100 mW. The range of about 100 meters.
Today Class 1 and 2 are most common. It is not surprising - despite the very low power consumption of the Class 3, its scope is extremely limited. Even for a headset, it fits very poorly. It is not necessary to keep the phone in a breast pocket - it can easily be in jeans, where the pocket is sewn just above the knee, or even on the table, and the owner will be observed within a radius of 5-7 meters from the device.
But Class 1 and 2 are sold quite actively. If you choose your own external USB Bluetooth adapter, it is better to take care of its long range. After all, even with a Class 1 adapter, a weaker Class 2 device will be able to work at a greater distance.
Well, a little about the scope. As it has already become clear, these are primarily mobile “gadgets”: the exchange of data between cellular phones (pocket computers, cellular phones and laptops, etc.), the connection of a wireless headset for talking. Recently, Bluetooth has become actively used in computer mice and keyboards. Many GPS navigators "speak" with the help of "blue teeth". Even the joysticks of modern consoles Nintendo Wii and PlayStation 3 work via Bluetooth.

However, not all devices need a high data transfer rate, as well as a large radius of action. This was clearly demonstrated by Apple on its phone communicator. Who does not know, we inform that his Bluetooth-controller can work only with a headset. Data exchange is not available to him.
And really, why should a cell phone (especially an entry level) have the ability to transfer more information? "Teeth" in them are most often used for a headset. And in this case, you need a stable data stream, normally transmitted over a distance of 5-10 meters with a fixed speed, consuming a minimum of energy. This is what prompted some companies to create branched standards.
Wibree
In mid-June 2007, Nokia issued an official press release, which was informed about the development of the standard. Wibree is based on Bluetooth technology and is designed to complement it, but not compete. Most importantly, it differs from the "original" - a much lower power consumption. It is assumed that Wibree modules will be used in devices like biometric sensors that monitor human parameters, in a wireless headset, keyboards, and various remote control devices. So do not be surprised if soon a person standing next to you on the bus suddenly presses something in the area of his navel and starts talking to himself.

Wibree will work in the same range as Bluetooth: 2.4 GHz. Maximum bandwidth is up to 1 Mbps. The range is 5-10 meters. Generally reminiscent of Bluetooth 1.2 Class 2 with ultra low power consumption.
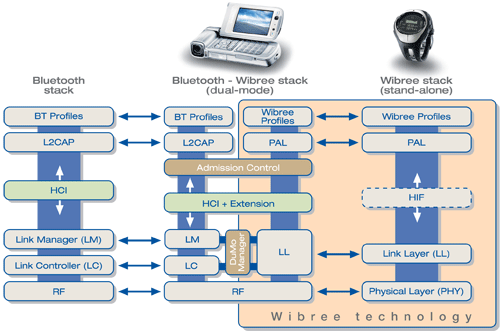
Although Wibree is based on blue teeth, there is still no full backward compatibility. Although nothing prevents you from integrating it into modern Bluetooth controllers, you only have to modify them a bit. But in any case, all modern devices will not be able to exchange data with your tennis racket, a bio sensor, stuck to your body or a smart kettle, reporting boiling not with a banal whistle, but through your mobile phone via SMS.
But Wibree is not the only "low-power" standard. There are its analogues, and already ready, and in places even not the first generation. The final specifications of Wibree will be ready in the first half of this year, while ZigBee already exists in its third version.
Zigbee
ZigBee is another "ultra mega super maxi low-power" wireless standard with two "ee" at the end. It was first conceived back in 1998, when it became clear that Wi-Fi and Bluetooth are not suitable for all occasions. Like the last ZigBee created to pair devices, but its principle of operation is somewhat different.

There are three types of ZigBee devices: the coordinator (ZigBee Coordinator - ZC), the router (ZigBee Router - ZR) and the "end device" (ZigBee End Device - ZED). The first is the main one in the created wireless network and can serve as both a router and a bridge for data exchange and with other networks. The router receives data from the end device, and can also exchange information with other routers and coordinators. The end device itself can only transfer data.
Thus, ZigBee is excluded as a technology for exchanging data between digital devices like music players, cameras, printers, PDAs, laptops, and so on. But the use of this technology in production or as a security system is much more important. It is in this direction that it is used.
On the official page of the project, you can read successful projects related to the automation of production (at the factory, during construction, etc.), ensuring the safety of the premises, the automation of modern buildings, the integration of home appliances into a single network, and so on. Bluetooth (and Wibree) is more focused on the transfer of "computer" data, while the ZigBee channels mainly circulate bits and bytes from technical information from sensors, remote controls, etc.
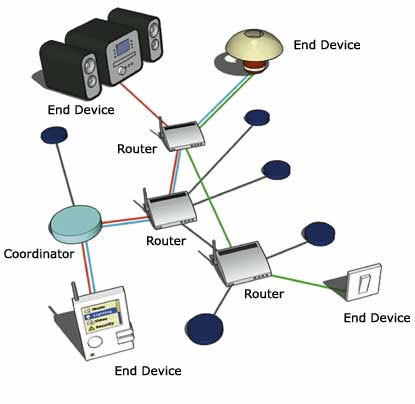
Now a little about the principles of building ZigBee-networks. There are two of them: without and with constant ZED polling. In the first case, the router or coordinator is in the mode of constant waiting for a signal from the end device (ZED). Good example Such a network can serve as a wireless light switch. The lamp acts as a router, usually equipped with a constant power source. ZED is the switch itself. He is in an inactive state. But as soon as you click on it, it will be activated and send a signal to the router. The latter will react and give a command to turn on the light. In this case, the energy is not sending data will be spent at the very least. Batteries in the switch will last for a year, or even a few years. Of course, if you do not constantly make "light music".
The second option assumes that the router will poll the ZED at regular intervals. At the same time it will consume less energy, so there is no need for a constant power source. But more electricity will be needed for the ZED. We believe that this type of network is more suitable for security systems, or for various sensors. By doing a ZED survey, you can check the status of a particular object, and, if necessary, quickly respond to changes in the situation.
ZigBee devices must comply with the IEEE 802.15.4-2003 standard, which allows operation at 2.4 GHz, 915 and 868 MHz. In the first case, up to 16 channels can be used for data transmission (at frequencies of 2405-2480 MHz in 5 MHz increments). In this case, the speed of information exchange can reach 250 Kbps. At frequencies of 915 and 868 MHz, the speed is 40 and 20 Kbit / s, respectively. The choice of these three frequency ranges is dictated by both technological reasons and geographic ones. So the frequency of 868 MHz is allowed in Europe, 915 in Australia and the USA, and 2.4 GHz almost everywhere. It is worth noting that ZigBee supports 128-bit encryption.

So, ZigBee is a great example of the implementation of an industrial wireless standard that expands and simplifies our life and work. Bluetooth and Wibree would be really bad for this purpose, which is why such specialized technology was created. Today it is supported by a large number of manufacturers. Entering the ZigBee Alliance and starting to use standard specifications for commercial purposes costs only $ 3,500 per year. And if not commercial, it is generally free.
There are several more such developments, for example, MiWi, JenNet, EnOcean, Z-Wave. They compete with both ZigBee and Wibree, and their implementation at some points coincides. We will not dwell on them - although they are digital, they are still used to exchange data between relatively simple and highly specialized devices. And in this material we are primarily interested in what provides for the interaction of computers, cell phones, PDAs and multimedia. household appliances. ZigBee was described only as an example of an alternative use of wireless networks. In the meantime, we are moving on to the next subclass of standards operating at a relatively small radius, but already with huge speeds compared to Bluetooth.
Uwb
The volume of information transmitted grows with every second. So 7-8 years ago, the MP3 format seemed to be a panacea for the ubiquitous distribution of music over the Internet. Thousands of compressed tracks with an average bit rate of 128 Kbps appeared on the Web, which made the average size of one song equal to 3-6 MB. At that time, the sites were optimized both in terms of code and graphics, and no one even thought about downloading movies.
Let's see what happens now. Songs are also distributed in MP3, only the average bitrate has grown to 160-320 Kbps. And earlier, if we could look for a smaller version of a song, now it's the other way around - we are looking for a better quality, especially if we like the track very much. Movies in MPEG4 format, which perfectly suited one DVD to a single CD, now often take up 1400 MB instead of the more usual 700 MB. But modern speeds allow you to download a full DVD from a P2P network (for example, BitTorrent) in a few hours, which are gradually beginning to be replaced by HDTV. In the latter case, we are talking about tens of gigabytes.
Modern hard drives easily transfer data at speeds up to 100 MB / s, and the capacity of optical disks has increased to 50 GB, and in two or three years it can double. Do you think modern Bluetooth speed is enough for such volumes? How long does it take to transfer 20 GB through a 3 Mbit / s channel? Even a fairly fast Wi-Fi standard is not good here. It is created rather for wireless internetrather than watching an HDTV movie from a nearby computer. In this case, we need a technology that can provide high speed data transfer, and not necessarily at a great distance. This is the main concept of UWB.
UWB is an abbreviation of Ultra-WideBand, which in our free translation sounds like "awesome fast connection". Joke? Nearly. The connection is really very fast, which is ensured by the broadband data transmission. As noted above, this is not really a technology, but rather a concept. This is the basis for different standards, two of which are described below.
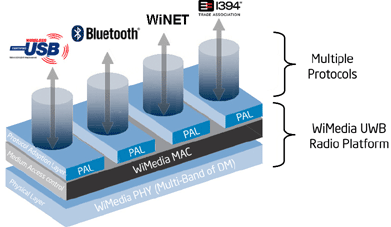
At the heart of UWB is still the draft IEEE 802.15.4a standard. Unlike conventional radio transmissions, UWB transmits data using waves generated at specific points in time. It uses a wide frequency range, thus causing time modulation.
For data transmission, frequencies of 500 MHz and higher can be used. But on February 14, 2002, the Federal Communications Commission (FCC - Federal Communications Commission) of the United States recommended a range of 3.1-10.6 GHz for UWB. It is assumed that data transmission will be carried out within the same room, although with increasing transmitter and receiver power, the range of the network will also increase. However, it is prohibited.
Now about the appointment. It is not difficult to guess that UWB will be used to transfer large amounts of data between digital devices. Among the latter, first of all, you can include computers, cell phones (especially top models with large amounts of memory), printers, digital photo and video cameras, audio and video players, and so on. The maximum speed of UWB is unknown to us, but it can reach tens of gigabits. Very impressive value not only by modern standards, but also by the standards of the near future. So there is a stock.
Now directly about the standards based on UWB. First of all, this is a new generation of Bluetooth. It is not yet clear whether this concept will be used in Bluetooth 3.0 or not, but there is definitely something in the plans. There are rumors of an increase in speed up to 480 Mbps. We believe that they are not far from the truth, only here such opportunities will be available mainly for transferring large amounts of data and after fifty warnings about high power consumption. Yet such speeds will not be available for nothing.
But when the light will see the specifications of Bluetooth 3.0 is still unknown. But now Wireless USB controllers are ready for mass production, and most recently we announced the release of the first version of the standard. Let us dwell on these two technologies in more detail.
Wireless usb
Wireless USB (abbreviated as WUSB) is not entirely new. Intel first spoke about it at its spring 2004 IDF session. The devices themselves then did not provide, as well as not announced the availability of specifications. They simply announced that such a technology exists. There is so there, thought the people who heard it, and continued to live on as they lived before.
In 2005, during the IDF autumn session, Intel already showed the first prototypes. Prototype i must say inspired. True, it is not clear what exactly: respect or amazement. It was a massive PCI-card into which the PCMCIA-controller was integrated, and an antenna stuck behind the mount. A strange solution, which in the future should have been integrated into motherboards and laptops. However, as it turned out, it was rather the first working sample, rather than the prototype of the series.

To date, it seems that both normal Wireless USB modules and the first devices with its support are already available. What are these devices? Yes, exactly the same ones that we connect through a regular USB connector: printers, scanners, cameras, mice, external hard drives, PDA, etc. WUSB allows you to transfer the capabilities of such a popular wired serial bus to wireless rails.
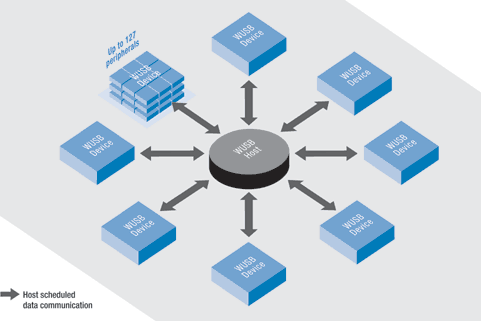
Let's see how it works. Let's start with the topology. For the exchange of data between devices is a special host controller. Each device that is in range, is allocated a separate communication channel. The latter is especially important if you have to transfer data at high speed - channel separation like Wi-Fi can lead to sad consequences (for example, optical disk when recording, if the data will be too slow). One "normal" WUSB host supports connecting up to 127 devices.
There are also not quite "normal" host controllers - these are the devices themselves. They have a limited list of capabilities, but can also receive and transmit data from other sources. In this way, a kind of cellular network is obtained, when information from a fairly remote source can pass through several devices, and then get to the main host, which will transmit it directly to the computer that made the request.
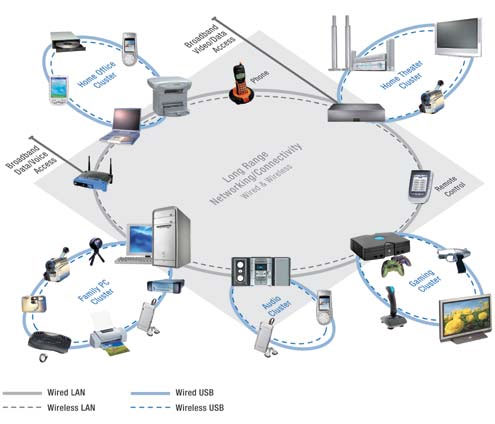
How can this be used in the same apartment or house? Somewhere not very far from the main computer you install a WUSB controller, or connect it directly to motherboard. After that you can use any devices within the room that can work with Wireless USB directly or through a hub. Yes, it is the hub - host controller that can be equipped with the most common USB ports to which the most ordinary devices like a mouse, keyboard, printer can be connected.
At the same time to communicate with other rooms can be used as other host controllers or Wireless USB devices both themselves and more convenient Wi-Fi access points, or even ordinary LAN switches.
The huge advantage of Wireless USB is its full compatibility with the original wired standard. An analogy with LAN and WLAN is appropriate: point wi-Fi access connects to wired local network with the help of the most common twisted pair, after which all devices within its range can safely use the resources of the entire network, not just wireless.
Since WUSB is USB compatible, this wireless standard should work just as fast. Actually, the way it is: in a radius of 3 meters, the speed will be 480 Mbit / s, and in a radius of 10 meters - 110 Mbit / s. In subsequent versions of the standard promise to raise the speed to 1 Gbit / s. For data transmission, frequencies from the range of 3.1-10.6 GHz are used, which clearly indicates the origin of this standard from UWB.
As for energy consumption, it should not be very significant. So, modern mobile phones and PDAs with a WUSB controller enabled will work about as much as before (of course, if you don’t constantly transfer gigabytes of information), and WUSB-based remotes will be able to last for several months on one charge. Although in the latter case it is much more relevant to use technologies like Wibree or ZigBee - it’s more economical, and the range is larger.
Does Wireless USB have any future prospects? Judging by the data the agency iSuppli has. So in 2007, the market for compatible devices amounted to only $ 15 million, but by 2011 it will increase to $ 2.6 billion. The number of devices sold will increase from 1 million to 500 million in the same 2011. Well, let's hope that everything will be .
Wirelesshd
Connect wirelessly to computers and peripheralsworking with them is far from the limit for modern technology. Yes, and put up with a short USB cable from the printer to system block big work will not be. But if you have an expensive home theater system installed, from which and to which a cloud of wires stretches, then it may be thought to get rid of them and her. Nevertheless, it is not always so easy to hide such "charms of life", even if there are only a few of them.

If we consider that modern home theaters are original semi-computers, then equipping them with the support of wireless communications is not so difficult. Is it any wonder that Sony LocationFree-like consoles began to appear capable of transmitting video and audio from a computer to LCD TVs and phonics? However, they work via Wi-Fi, and this type of network bandwidth will not always be enough, especially if you transmit video in 1080i / p format.
So the WirelessHD standard was invented. Most recently, we are on the adoption of the first version of its specifications. This is a special wireless standard designed to combine consumer electronics. Its frequency range goes far beyond the UWB and operates at a frequency of 60 GHz (± 5 GHz depending on the country). Its radius of action is small - only 10 meters. This is quite enough to customize the interaction of home theater devices.
The use of such frequencies is necessary to achieve high data transfer rates. It is about 2-5 Gbit / s in the first versions of the standard. But the theoretical limit is 20-25 Gbit / s. For comparison, the peak for HDMI 1.3 is 10.2 Gbps. So there is a reserve for the future, and very good one at that.
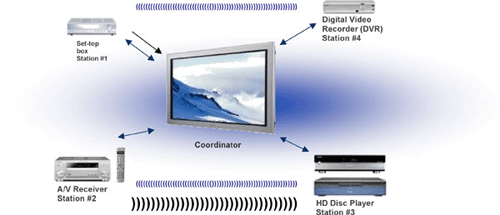
At the head of the WirelessHD network is the coordinator - a device that controls the transmission of audio and video streams, as well as sets their priorities. All other devices are stations that can be both a source and a receiver of data, as well as the coordinator himself.
Whether the support for WirelessHD will be provided for the computer is still unknown, but we believe it will. This is just like the HDMI outputs on many modern video cards and laptops. Thus, video and audio can be played with ordinary computerthat will significantly expand the functionality. After all, domestic players do not always support the latest codecs, not to mention the formats of disks. I must say that the implementation of this technology is really very useful and relevant. It is much more convenient than what is used now. And now, as we said, Wi-Fi is used. We proceed to the description of this standard.
Wi-Fi
Of all the Wi-Fi standards discussed in this article, paired with Bluetooth is the most famous and popular. Wi-Fi gained its popularity thanks to laptops. Today, even the cheapest models are equipped with a wireless network card. But, as always, this technology did not become popular at once as it was presented.

The first work on Wi-Fi began in the 80s of the last century. However, the final specifications were ready only in 1997. The IEEE organization assigned them the label 802.11 (or rather 802.11-1997). In 1999 they were accepted as a standard. New and promising technology immediately picked up Apple. As an option to the new iBook laptops, a Wi-Fi network card was offered. But Apple even now does not occupy a dominant position in the market, and then it only began to emerge from a protracted crisis. So the "fruit company" was not able to walk around the planet as a pioneer, sowing Wi-Fi grain everywhere. This honor was reserved for Intel.
We believe many have heard about the mobile platform Intel Centrino. Her first generation was introduced in 2003. The laptop, to get a new and trendy logo, must be based on the Intel processor (now Core Duo or Core 2 Duo, and then on the Pentium M), the Intel chipset, and also inside it must be installed Wi-Fi network Intel production card. This was the impetus for the ubiquity of wireless local area networks.
However, it cannot be said that this is the sole merit of Intel alone. Just the market was already ready for this technology. Apple's initiative at the time was too innovative, that it was accepted by no means all. Four years later, Wi-Fi equipment was also quite expensive, but not so much. Yes, and the range has expanded significantly. Intel just gave everyone the most convenient form for adopting the next technology, designed to bring a bright future closer.

Now let's see how the Wi-Fi works. As it became clear, the corresponding network card should be installed in the computer. It can be either a PCI (or PCI Express) expansion card, or a relatively small USB stick. There are PCMCIA (PC Card) and ExpressCard versions for laptops.
Using wireless network card You can establish a connection with another one the same. That is, it is not difficult to establish a network connection between two laptops or between a laptop and a desktop PC. Only here, despite the apparent freedom to connect to them another participant will not succeed. The third, as they say, is superfluous. To get around this restriction, one has to resort to access points.

A Wi-Fi access point is an analogue of a regular local area network router. Only connections to it are made via radio transmission, and not by wire. Theoretically, their number is unlimited, although for greater speed and stability it is better to distribute the connected computers between several points. In this case the analogy with cellular communication is relevant. One base station can serve several subscribers at the same time, but if there are a lot of them it is overloaded and someone can not get through, and someone will break the connection.
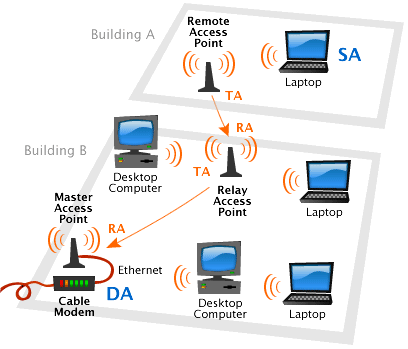
In general, the principle of deployment of Wi-Fi is quite similar to a cellular network. In the role of base stations are access points. If they are configured accordingly, they will communicate with each other, making it possible to exchange information between computers connected to any of them. If you do not do this, the Wi-Fi card management program will provide the ability to connect to one of the available networks.
But to connect to Wi-Fi network sometimes you need to know the password or the key to access it. Still, very important data can be transmitted through the network, such as passwords for accessing money accounts of various services, and it is much easier to intercept a radio program than the usual information exchange over wires. To this end, several encryption standards have been implemented.
The first of these, WEP (Wired Equivalent Privacy), adopted in 2001, did not last long. It is considered to be a rather weak protection against unauthorized entry. Today, you can easily find a program that can crack a key in a short time, after which it will be possible to track all packets on the network.
In mid-2003, WEP was proposed to replace new algorithm WPA encryption (Wi-Fi Protected Access). It was based on the 802.11i draft standard. The latter was later adopted in June 2004. At the same time, as the main method of protection, he proposed a more advanced WPA2 algorithm. Hacking it is much more difficult, so its use is strongly recommended. Of course, progress does not stand still, and even more advanced protection features have been proposed that will be adopted as standards in the future. One of these is 802.11w.
A little about the need to protect data. Today quite often access point installed in the apartment to network all local computers (Yes, and PDAs with cell phones, if they support Wi-Fi). Moreover, if you exchange only movies, music and similar information, then your network is of no great value. However, nothing will prevent a neighbor behind the wall from connecting his laptop to your network, especially if it is not protected. In addition, in such a network there is no need to fear everyone and everything, so you can open certain sections in full free access. hard drives. Of course, nothing but the latest comedy and action movie may not lie there, but there will always be those who want to spoil it. It's still not nice if the movie just copied is deleted before viewing.
But the situation is different. At your home, the Internet is connected via an ADSL modem. If you have several computers, or one laptop for convenience, the modem can be equipped Wi-Fi point access. Agree to sit comfortably from anywhere in the apartment on the web. If Wi-Fi is not properly secured, then anyone can access your Internet. Theoretically, even from the street, you can sit on the bench under the window. Well, if you have an unlimited channel - you just feel a decrease in speed. And if the traffic? You can fly into the entire amount that lies on the account. So protection of a local wireless network is of paramount importance. And it is not necessary to be limited to WPA (2) encryption. If computers are always a static number, each can create a separate account, and at the same time make identification by the MAC address of the network card.
Well, about the standards of Wi-Fi. In total, we managed to learn about 28 standards. But only six of them directly describe the speed of data exchange, the range of action and the operating frequency:
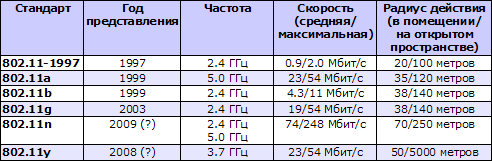
The very first version of Wi-Fi to put it mildly is not impressive. Although it was adopted before Bluetooth, it does not even reach modern Bluetooth 2.0 + EDR. But the standard was originally developed as a wireless analogue of wired LANs where huge amounts of data can be transmitted. 802.11a / b provided far better options, especially 802.11a. But the frequency of 5.0 GHz is not allowed everywhere, so it was not widespread. That is why 802.11g was developed, which provides the same speed as well as the ability to work at 2.4 GHz.
Since last year, access points and network cards with 802.11n support began to appear on the market. As can be seen from the table, it works several times faster than 802.11g. However, this standard is still designated as draft. Judging by the available data, it will be adopted no earlier than next year. But most likely all modern devices based on 802.11n draft will be compatible with the final specification after updating the firmware.
The 802.11y standard is an analogue of 802.11g capable of operating at a much greater distance (up to 5 km in open space). It was for this purpose that he was created. To achieve such indicators, it was necessary to use higher-frequency waves from the 3.7 GHz range.
Now we will list all other standards from the 802.11 family. All Latin characters were reserved for it:
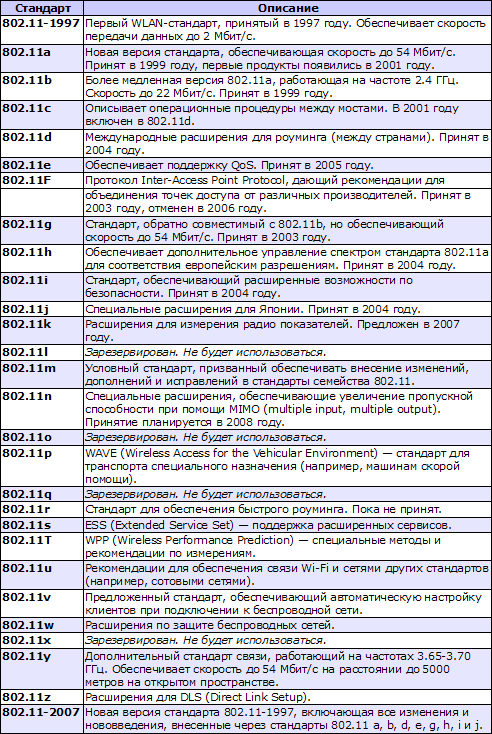
As you can see, Wi-Fi is still growing. It is possible that the speed of this technology will increase even more in the future. In addition, today not a small attention is paid to the implementation of support for this standard in all devices. Communicators and mobile phones with Wi-Fi are not rare. It is not surprising, there are access points in many modern cities. And the Internet through them can be much faster than through the WWAN (EDGE / GPRS, UMTS / WCDMA, HSDPA). However, another very promising technology was invented for the Internet: WiMAX.
WiMAX
Completes our list of standard WiMAX. Its main difference from all previous ones is in the range. Depending on the transmitters used, the signal can be received at a distance of up to 50 km from the source. Here we are talking about an analogue of cellular communication, and not just about "another wireless LAN".

WiMAX is not entirely designed for deploying a network within an apartment, house, or neighborhood, although it can also be used for this. One of its main goals is to provide high-speed access to the Internet both for particularly remote communities, and for individual areas of the city.
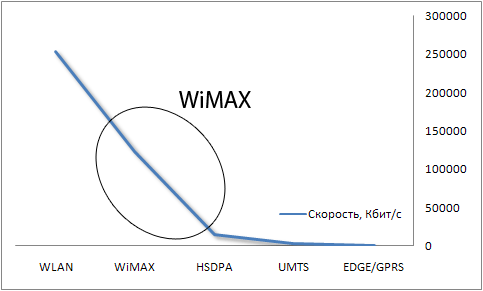
This is not exactly an alternative to cellular communication, since it provides several other possibilities and it is no longer computer oriented. Rather, it is an intermediate option between cellular standards. last generations (UMTS, HSDPA) and wireless local area networks. WiMAX provides a larger radius than Wi-Fi, but the average data transfer rate will be lower. At the same time, cellular communication is deployed for much greater distance and is more noise-resistant, but the data transfer rate in it is lower.
However, WiMAX is called a competitor to fourth-generation cellular networks. We tend to believe that this is not far from the truth, but only in part. Yet WiMAX is designed primarily for computers, and only then for communicators and mobile phones. But we are starting to delve into the specifics of the work of this standard. First, a little history.
The WiMAX Forum organization, formed in 2001, is responsible for the development of WiMAX specifications. The WiMAX name itself is an abbreviation of Worldwide Interoperability for Microwave Access or "Worldwide Networking for Microwave Access." In December 2001, the final WiMAX specifications, ratified as the 802.16-2001 standard, were presented. In 2004, the 802.16-2004 standard, also known as 802.16d, was adopted, describing the possibility of organizing WiMAX indoors. Finally the latest version The standard was adopted in 2005 and received the 802.16-2005 index, but also informally referred to as 802.16e.
Now about the principles of work. Inside WiMAX, IP is implemented, allowing it to simply integrate with modern networks. So this technology can be a great addition to Wi-Fi. But unlike the latest WiMAX provides a more stable connection. For example, a connection to a Wi-Fi access point with a significant distance may be unstable if there is another point nearby. In the case of WiMAX, a single slot is allocated to one connection, which no one else can use. And when you move, various WiMAX base stations will be responsible for its activity.
Yes, WiMAX is also based on base stations. Depending on the tasks, they can be quite small (for example, for premises), or installed on separate towers in order to transmit data over a long distance. Initially, WiMAX was assigned a frequency range of 10-66 GHz, but later added support for lower frequencies 2-11 GHz.
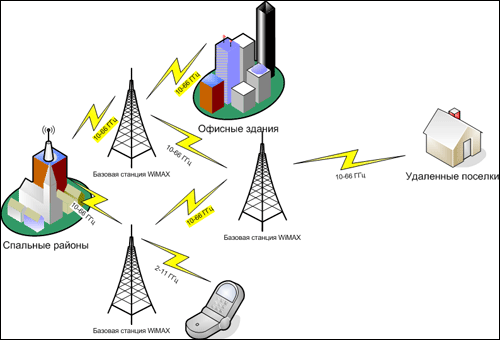
Why does everyone need this? The range of 10-66 GHz is good for constant transmission at high speeds. So the peak transfer rate can reach 120 Mbps and this is at a distance of tens of kilometers. A great option to connect a small settlement. But since ultra-high frequencies require direct visibility for an ordinary city, they are not as good. So from a laptop or mobile phone to connect to the network will be somewhat problematic. For them, the range of 2-11 GHz is much better suited.
In this regard, there are four modes of WiMAX operation:
Fixed WiMAX.Uses the high-frequency range of 10-66 GHz, designed to combine distant objects that are within the line of sight;
Nomadic WiMAX. Essentially the same Fixed WiMAX, but with session support. So having connected to one tower session is created. If you go beyond her reach, but you find yourself in a different area, your session can be transferred. In this case, the connection will not suffer;
Portable WiMAX.Allows you to automatically switch sessions from one base station to another. Uses a lower frequency range, allowing you to move at speeds of up to 40 km / h;
Mobile WiMAX.This version of the standard was adopted as the latest version of the 802.16-2005 supplement. Allows you to receive a signal at speeds up to 120 km / h. Great for mobile devices.
As you can see, all categories are covered: from the sleeping areas of large cities, as well as their offices, to remote settlements and people moving between them with laptops, PDAs, mobile phones. If it is widely distributed, it can really become a serious competitor to fourth-generation cellular networks being developed today. Of course, the latter meanwhile promise speeds of up to several gigabits, but the second version of WiMAX standards will also raise the bar to 100 Mbps in the case of the mobile mode and to 1 Gbps in the fixed mode.
However, WiMAX has not really been introduced anywhere. Dozens of test networks are deployed worldwide, including Russia and Ukraine. And in the majority while it is Fixed WiMAX. However, South Korea in a test mode deployed a WiBro network, which is essentially renamed Mobile WiMAX. It provides a connection at speeds up to 30-50 Mbit / s in a radius of up to 5 km. The speed of movement can be up to 120 km / h. For comparison - the usual cellular communication operates at speeds up to 250 km / h.
Also for the time being there are few devices on sale both for deployment and for using WiMAX. The latter should be presented with the fifth generation of the mobile platform Intel Centrino in mid-2008. We hope that this can serve as a similar impetus for the market, which at one time was the first Intel Centrino for Wi-Fi.
Finish
Total what we see? Wireless networks surround the entire world with their invisible "threads". They do not interfere with any boundaries, without drying water, or buildings, and even better there would be more energy and more open space. And the more of all this will be, the closer our bright future is with you. The future, where everything will be united into a single network between not only all possible phones, computers, coffee makers, kettles, stoves, refrigerators and irons, but also all the planets of the solar system, the galaxy, and the small planet K-PAX.
Seriously, the future prospects are clear. Miniature devices will gradually gain the ability to exchange data using the Bluetooth standard (or its similar replacement). The range of the wireless headset will expand with the help of Wibree, and the ZigBee will turn on the light in the room from the remote.
Unite the periphery within the room called Wireless USB. By the way, not so long ago he was called to help him. It provides the same speeds, except that the distance from the source can be no more than a few centimeters. Freedom of placing devices is not much, but there is no need for wires. For home theater is designed WirelessHD. An interesting and promising technology that can eventually push out the modern wired connection.
At the apartment level or even a few apartments, or for the connection of wired LANs between the houses, Wi-Fi will be used. It is for this purpose created and it is more convenient. It is much cheaper to install a small access point for $ 50-70 in an apartment or in a cafe (for visitors) than expensive WiMAX equipment. But it will also have to be installed and configured correctly.
As for WiMAX, this standard is well suited primarily for Internet providers. With it, they will be able to bring the light beam of the world wide web into the darkest backwaters of our planet. However, it is not yet known what the fourth generation of cellular communication will offer us. In any case, we will win - the ordinary inhabitants of a small planet Earth, already girdled with wires, from which everyone is now rapidly getting rid.
The material used information from the following resources:
The absence of wires and, as a result, binding to a particular place has always been significant for mobile users, who need constant access to information constantly, regardless of their location.
Today, there are several wireless access options: mobile cellular and wireless network data transmission standard 802.11b. cellular It has a more global reach, but in terms of speed, it absolutely does not meet modern requirements for working with corporate applications. And in the world, wireless Radio-Ethernet networks, which are considered by some analysts as competitors of third-generation mobile networks, are beginning to play an increasingly prominent role. Today, the development of RadioEthernet technology has reached another milestone in the field of data transfer speed, frequency resource and services provided. The IEEE 802.11b wireless networking standard provides data rates of up to 11 Mbps, which is quite enough to connect to the corporate network and navigate the Internet. In addition, the current situation in the global market, which is characterized by lower prices for wireless kits (PCMCIA-cards, access points), is contributing to their increasing distribution. Now, for example, in the Moscow market (according to http://www.price.ru/) you can buy a PCMCIA wireless access card for as low as $ 130.
Initially, wireless access technologies were used as a supplement to traditional wired, as well as in places where it was impossible to reach with a cable or it was impractical. Based on this, a narrow circle of areas was formed in which wireless local area networks were the most preferable solution. It is about connecting users in warehouses, creating temporary communication lines, local networks in museums, hospitals and shopping centers. Indeed, in some cases it is impossible to lay wired communications. for example, in shopping centers where space is leased and each vendor organizes a pavilion in accordance with their own design, the fixed-line wired communications outlet becomes inconvenient (the need to configure the room based on the location of the outlets). Another example: the creation of networks in historic buildings, where the violation of architecture and design is unacceptable. But still, the most popular applications are storage and production facilities, where it often happens that there is access to corporate network data, but there is no wired connection or it is inaccessible. In such cases, a radio access point is installed in the room to which the subscriber device is connected, for example, a laptop with an installed radio card. However, today there is a rapid growth of user interest in wireless access not only in the workplace or within the corporation, but also on the road, in another city, in waiting rooms, in hotels, etc. And if true mobility (access to the network in motion) is so far achieved only through the use of cellular networks, albeit slower, but with a wider coverage, such as, for example, CDPD (Cellular Digital Packet Data) networks popular in the USA, then fixed mobile Access is easily realized using the IEEE 802.11b wireless standard. Than operators didn’t fail to take advantage - wireless access networks were deployed in airports, waiting rooms of railway stations and other public places. Today, white-collar businessmen working on the road have access to several public wireless ones. access networksto which they can connect, for example, while waiting for a flight, with their equipment or rent a wireless access card. According to the WECA (Wireless Ethernet Compatibility Alliance), public wireless LANs are now being deployed at airports, conference centers and other public places, which in the future can form a kind of global wireless network consisting of hot spots for access to a wireless data medium. . Today, through these points, mobile users can connect to Internet services and corporate networks at 11 Mbps using personal computers (laptops or PDAs) that support the 802.11b standard.
There are similar examples in our country - in mid-September, at the ADE conference “Results and Prospects for the Development of the Internet in Russia” in the “Vatutinki” boarding house ”CompTek organized a wireless local area network, and conference participants received PCMCIA cards through which the laptop connected to WLAN. The result is obvious - fast, convenient and no wires.
Move without problems, or roaming in wireless networks
From the user's point of view, everything is quite simple (although it’s not quite convenient at the moment) - connected, worked, paid for services and that's it. But from the point of view of operators, things are not so prosaic - now wireless network providers are very seriously concerned with refining the technical and economic details of inter-network roaming, the implementation of which will allow users of wireless local networks to connect to the systems of almost any wireless access providers, by analogy with cellular roaming. The problem lies in charging, invoicing and authorizing guest users on wireless networks. Indeed, in the absence of roaming agreements between operators, each time a user arrives at a new place, it will be necessary for the user to enter into a service contract, authorize and pay for services. As a result, a lot of time is spent on “official events”, which could be used “on business”. It is also inconvenient for the user to receive bills from a dozen providers for using wireless access services at the end of the month. That is why the WECA association, which includes 3Com, Cisco Systems, IBM, Intel, Microsoft, is developing the network-wide standards needed to support roaming. This initiative aims to provide shared access to data on subscriber connections and billing information, so no matter how many Internet providers the subscriber uses while wandering around on business trips, as a result he will receive an account from only one “home” provider. And besides, there is no need for complex authorization of mobile users in the new network - it will be enough just to enter your credentials, and the system will independently determine which provider user is in the “guest” network.
This summer, a preliminary version of internetwork roaming, developed by the WISPR (Wireless Internet Service Provider Roaming) group, which is part of WECA, has already been presented. The main task of this group is to develop a solution that allows the subscriber to use a single identifier and password to access the Internet through the network of any operator. The group is also working on the addition of the RADIUS protocol with special attributes, such as user name, time on the Web, received or transmitted bytes, etc. Information about the user's location will be included there, which will allow the client to provide additional information services.
Despite the seemingly simple task of roaming, there are a number of pitfalls, for example, it is quite difficult to determine the method of conducting transactions between providers when processing Internet user sessions. The WISPR team does not have an exact schedule of work, so now it’s hard to say when 802.11b roaming will become a reality. However, according to some participating firms, WISPR will prepare a final document by the end of this year. Users will be able to count on the mass introduction of roaming in the next two years. Although we can expect a shorter time frame for establishing roaming relations. Firstly, the pace of implementation should grow as all new telecommunication companies-operators and equipment manufacturers join the project. Secondly, according to the Cahners In-Stat report, the 802.11b market will continue to grow at a rapid pace. And in 2005, according to these estimates, about $ 6.4 billion will be spent on the equipment of wireless local area networks. And according to a report by Allied Business Intelligence, Inc. (ABI), the market of wireless local area networks will grow from 969 million dollars in 2000 to 4,5 billion dollars in 2006. According to this source, the greatest growth of WLAN (Wireless Local Area Network) is expected in common areas, cafes, health facilities, academic campuses and home systems. And the number of installed wireless access points will increase from 4.9 million in 2000 to 55.9 million in 2006. According to ABI analysts, the 802.11b standard (or, as it is also called Wi-Fi) is currently dominant in the wireless data transmission sector, but in the near future it will be pressed a new version - 802.11a. Products based on the 802.111a standard, which will appear in 2002, by 2005 will win 50% of the market from their “younger brother” - 802.11b. In this regard, the majority of market participants are very much counting on the imminent emergence of devices operating in the 802.11a standard, which provides data transmission at speeds up to 54 Mbps. A kind of FastEthernet for radio. Firstly, these devices are not only faster, they operate in the new 5.5 GHz band, which is completely free for BSPD operation. In addition, in the new range it will be possible to make frequency diversity for Indoor- and Outdoor-systems.
Russia goes its own way
Global trends in the development of public wireless access networks may well inspire optimism, but for our country the picture is not so rosy. The specificity of Russia is in the use of the 802.11b wireless standard for building wireless data networks (BSPD) at a city or district scale. According to Peter Kochegarov, CompTek technical director and head of the ADE working group on wireless networks, in Russia 95% of the networks built are urban. The main task that wireless networks solve is the organization of the “last mile” in the conditions of a complex topographic situation, the complete absence of installed cable channels. in other words, RadioEthernet is the only way to organize communication when it is impossible to use cable systems. And in our country there are quite a few similar tasks.
As for local wireless networks, the situation here is somewhat more complicated than the western one. And it's not just about the high price of adapters for wireless communication, the cost of which is almost an order of magnitude higher than popular network adapters, but also about compulsory licensing of the frequency range. It does not make a difference where the buyer will use wireless equipment - indoors (in his office, in a warehouse, in a shopping center) or on the street (the “last mile” organization), licensing is necessary.
On the one hand, today there is practically no problem of obtaining frequency and resolution, and almost all operators constantly “stew in this mess”, and on the other hand, there is an absolutely understandable desire to significantly simplify the procedure. And for local use (indoor solutions), to cancel licensing altogether.
In this regard, there are already shifts - at the 6th conference BESEDA (Wireless Data Networks), organized by Moscow company CompTek, held in early June, it became clear that the state has an understanding of the current situation and the imperfection of the procedure for obtaining permits. And soon we can expect significant simplifications in obtaining permits for the use of wireless data transmission systems, and for internal solutions (local wireless networks without access to the streets) it will even be possible to use wireless equipment in the notification procedure (bought and used, just inform the relevant authorities).
To date, many manufacturers (see, for example, the article “LG Network Equipment. Part 2” in this issue) have added kits for organizing local wireless networks to their network equipment. The main feature of these solutions in addition to the relatively low price was the reduction of the signal power from 100 to 30 mW, which is quite enough for internal use, but does not interfere with street systems. So, perhaps, by the end of this year, the distribution will be carried out in a licensing notification procedure - of course, with certain restrictions on the use (for example, signal strength). This forecast is absolutely realistic, because today there are already precedents for abolishing the need for licensing equipment (for example, DECT phones, cell phones and some others).
"Wireless" are becoming more accessible
In conclusion, our review, we note that wireless systems are becoming more accessible not only thanks to network vendors who expand their lines with wireless access equipment. And most of this equipment is made up of devices for the organization of local wireless networks. In addition, the emergence of low-cost wireless kits from D-Link, Compex LynkSys and LG on the market lowered the bar of entry into the “wireless fraternity” below $ 150 per card, and if recalculated in the minimum configuration (2 cards and an access point), then According to http://www.price.ru/, as of September 20, 2001, the minimum cost of connecting one port is only $ 180 (using a Compex Waveport WP11 access point and two COMPEX WL11-E PCMCIA cards).
It is worth noting the movement in this direction and the manufacturers of portable computers. For example, Dell last year launched the Latitude model with a built-in antenna and integrated wireless access card. The antenna in this model is connected to the MiniPCI compartment, which makes it possible to organize wireless access to the local network according to the 802.11b standard.
Compaq, in turn, launched the Compaq Evo series, some models of which (for example, the Evo N400c) are equipped with the new MultiPort interface. A module that connects to this interface, located on the outside of the on-screen panel, provides all the same wireless standard 802.11b functionality.
As you can see, there are many examples. And it gives hope for a bright wireless future.
ComputerPress 10 "2001
Wireless lan (Wireless LAN) supports high-speed data transfer within a small space (for example, a university town or a small building) when users are moving from place to place. Wireless devices that have access to this LAN are usually fixed or moving at pedestrian speed. All wireless LAN standards in the United States operate in the unlicensed frequency range. The main unlicensed frequency bands are the ISM bands at 900 MHz, 2.4 GHz and 5.8 GHz, as well as the range of the unlicensed national information infrastructure (U-NII) at 5 GHz. In the ISM bands, unlicensed users are secondary users and therefore have to cope with interference created by primary users while they are active. There are no primary users in the U-NII range. To work in ISM or U-NII bands, the FCC license is not required. However, this advantage is a double-edged sword, since other unlicensed systems also operate in these ranges for the same reason, which can cause very strong interference between systems. The problem of interference is reduced when setting for unlicensed systems power limitations per unit frequency range. Wireless LANs can either have a star connection with wireless access points or concentrators. located within the coverage area, or peer-to-peer LAN network architecture, where wireless terminals are automatically configured into a network.
In the early 1990s, dozens of companies appeared - suppliers of wireless LAN equipment and services, seeking to capitalize on the unsatisfied demand for high-speed wireless data transfer. These first-generation wireless LANs were based on incompatible user protocols. Most of them operated in the 26 MHz frequency band of the ISM 900 MHz frequency range using direct sequence spread spectrum with data transfer rates of the order of 1-2 Mbit / s. Used as a star connection and peer-to-peer network architecture. The lack of standardization in this area has led to high development costs, small-scale production and small markets for each individual product. Of all these original products, only a small amount was more or less successful. Only one of the first-generation wireless LANs, Altair from Motorola, worked outside the 900 MHz frequency band. This system, which operated in the 18 GHz licensed band, had a data transfer rate of about 6 Mbps. However, the use of "Altair" was difficult because of the high cost of components and large losses in the transmission path at 18 GHz, and "Altair" was discontinued several years after its release.
Wireless lan second generation in the United States, they operate in the 83.5 MHz wide band in the 2.4 GHz ISM band (WiFi). The IEEE 802.11b standard for wireless LANs in this frequency range has been designed to avoid some problems with patented first-generation systems. The standard defines the expansion of the spectrum by the direct sequence method at a data transfer rate of about 1.6 Mbit / s (the maximum physical data transfer rate is 11 Mbit / s) and a coverage area of about 100 m. The network can be in the form of star connections or ad hoc network architecture, although the latter is rarely used. Many companies began to develop their products based on the 802.11b standard. After a slow initial growth, the popularity of 802.11b wireless LANs has increased significantly. Many small portable computers with built-in 802.11b wireless LAN cards have appeared. Companies and universities have installed 802.11b base stations on their territories, and many cafes, airports and hotels offer wireless access, often free, to increase their attractiveness.
To provide higher data rates than the 802.11b standard, two additional standards for the 802.11 family were developed. Wireless LAN standard IEEE 802.11a takes polo su 300 MHz wide in rangeU-NII 5 GHz. The 802.11a standard is based on multi-carrier modulation and provides data rates of 54Mbit / s in an area of approximately 30 m. Since the 802.11a system has a much wider bandwidth and, therefore, much more channels than 802.11b, it can support a larger number of users at a higher data transfer rate. At first, there was a consensus about whether 802.11a systems would be significantly more expensive than 802.11b systems, but in reality they quickly became competitively priced. The other standard, 802.llg, has the same scheme and data rate as 802.11a, but it operates in the 2.4 GHz band with an area of about 50 m. To avoid incompatibility, many wireless LAN cards and wireless transceivers networks support all three standards.
In Europe, the development of wireless LANs revolves around HIPERLAN standards. The HIPERLAN / 2 standard is similar to the IEEE 802.11a wireless LAN standard. In particular, it has a similar data link layer scheme, it also operates in the 5 GHz frequency band, like U-NII. Consequently, HIPERLAN / 2 has the same maximum data transfer rate of about 54 Mbps, and the same coverage area is about 30 m as 802.11a. The HIPERLAN / 2 standard differs from 802.11a in the access protocol and the built-in support for "Quality of Service Guaranteed" (QoS).
Wireless technologies - classification of wireless networks
First of all, let's define the names and standards so that we can speak the same language.So, the interaction of wireless devices is regulated by a number of standards. They indicate the spectrum of the radio frequency range, data transfer rate, method of data transmission and other information. The main developer of technical standards for wireless communications is the IEEE organization.
The IEEE 802.11 standard regulates the operation of wireless devices in WLAN networks (Wireless LAN). Today, the following amendments are in effect - 802.11a, 802.11b, 802.11g and 802.11n. All of these technologies are categorized as Wi-Fi (Wireless Fidelity).
The Wi-Fi Alliance is responsible for testing devices for wireless LANs manufactured by different manufacturers. The Wi-Fi logo on the device means that this equipment can interact with other devices of the same standard.
For those who are curious, I provide some technical data from existing IEEE 802.11 revisions:
802.11a:
- uses 5 GHz radio spectrum;
- incompatible with the 2.4 GHz spectrum, i.e. 802.11 b / g / n devices;
- range is approximately 33% of 802.11 b / g;
- relatively expensive to implement compared to other technologies;
- 802.11a compliant hardware is becoming increasingly rare.
- the first technology 2.4 GHz;
- maximum data transfer rate of 11 Mbit / s;
- the range is approximately 46 meters indoors and 96 meters outdoors.
- 2.4 GHz technology family;
- maximum data transfer rate increased to 54 Mbps;
- the range is the same as the 802.11b;
- backward compatible with 802.11b.
- newest standard;
- 2.4 GHz technology (the draft standard provides support for 5 GHz);
- increased range and throughput;
- backward compatibility with existing 802.11g and 802.11b hardware.
Each wireless access point has its own service set identifier (SSID) - for us, users, this identifier is represented as a network name:
The SSID tells wireless devices what wireless network they belong to and what devices they communicate with. Accordingly, if several wireless devices (computers) are connected to one access point - they form a local wireless network.
The SSID is an alphanumeric string, case-sensitive, of up to 32 characters. This identifier is sent in the header of all data packets transmitted over the local wireless network.
There are two types of wireless networks: ad-hoc and infrastructure network.
As mentioned, the access point has a limited coverage area. To increase coverage, you can set up multiple access points with a common SSID. In this case, it should be remembered that in order for the transition between cells to be possible without losing the signal, the coverage areas of neighboring access points must intersect each other by about 10%. This allows the client to connect to the second access point before disconnecting from the first access point.
Basic access point setup
Let's try setting up an access point. I will give an example of setting up an integrated router (this is the name of the box that combines the router, switch and wireless access point) D-Link DGL-4500. Since the web interface for interacting with the router is very similar for different models from different manufacturers, you can easily perform the same operations with your device.In my case, the wireless settings are as follows:
Let us examine the most significant points:
- Enable Wireless - turns the access point on and off. Of course, we are interested in the “on” state.
- Wireless Network Name (Also called SSID) - ID of the wireless network, or in other words, its name. The SSID is the hallmark of each wireless LAN, and all devices participating in the same network must use a single SSID.
- 802.11 band - this setting is not present in most routers and corresponds to the frequency of the used radio frequency spectrum. Leave the default value - 2.4 GHz.
- 802.11 mode - It is worth to focus attention. Most home access points support different standards. These are mainly 802.11b, 802.11g and 802.11n standards. Although they all use the 2.4 GHz frequency band, each of them uses its own technology to achieve maximum throughput. Therefore, the choice of 802.11 Mode at the access point depends on the type of connected wireless device. If only one type of device is connected to the access point, select the 802.11 Mode that supports this device. If several types of wireless devices are connected, you should select mixed mode, but remember that network performance will decrease due to the increased load on support for several 802.11 Mode. The type of wireless standard in each device can be found in the user manual.
- Wireless channel - if all access points worked on a single frequency, they would be in a single coverage area, they would become a serious obstacle to each other, just as I interfere with two radio stations on neighboring frequencies. To solve this problem, 11 wireless communication channels were created - each channel has its own frequency (all of them are close to 2.4 GHz or 5 GHz, depending on the type of connection used). The channel for the access point is selected taking into account the adjacent wireless networks. In order to achieve optimal operation of neighboring access points, bandwidth should be chosen in each of them with channels with a difference of at least 6 channels (for example, in one 1st channel, in the second 7th and above). All access points provide the ability to manually configure the channel. My access point also provides the ability to automatically search for the least loaded channels (setting Enable Auto Channel Scan).
- Transmission Rate and Channel width - these settings are also not present in most routers and are responsible for the speed of data transfer. Leave them as default values.
- Visibility Status - for quick detection of the wireless network by clients, the access point broadcasts an SSID every few seconds. The SSID distribution feature can be disabled by setting the Visibility Status to “invisible”. In this case, the SSID will not be broadcast, it will need to be manually configured on wireless clients, so network invisibility can be an additional security measure to prevent unwanted connections. This can be useful if you need to hide the network (it simply will not appear in the search results of available networks on client devices).
Securing Wireless LAN
One of the main advantages of wireless networks is the convenience of connecting devices. The flip side of the coin is a network vulnerability to intercept information and attacks from malicious users — a hacker does not need to physically connect to your computer or any other device to gain access to your network; it can tune into your wireless, network signals just like a radio station wave.A hacker can access your network from anywhere within the wireless range. Having access to your network, attackers will be able to use your Internet services for free, as well as gain access to computers on the network and damage files, or steal personal or confidential information. Of course, this does not apply to cafes, airports and other establishments, where an access point devoid of any protection is specifically set up so that everyone can use it.
To protect against these wireless vulnerabilities, special security features and methods to protect against external attacks are needed. To do this, it is enough to perform several simple operations during the initial setup of the access point.
As mentioned, one of the easiest ways to restrict access to a wireless network is to disable the SSID distribution.
As an additional security measure, it is strongly recommended to change the default settings, as the integrated routers come with pre-configured SSIDs, passwords and IP addresses. Using the default settings, an attacker can easily identify the network and gain access.
Even if the SSID broadcast is disabled, there is a possibility of network penetration if the attacker becomes aware of the default SSID. If you do not change other default settings, namely passwords and IP addresses, hackers can penetrate the access point and make changes to its configuration. The default settings should be changed to more secure and unique.
These changes alone do not guarantee the security of your network. For example, the SSID is transmitted in clear text, without data encryption. But today there are devices for intercepting wireless signals and reading messages in plain text. Even if the SSID broadcast function is disabled and defaults are changed, hackers can find out the name of the wireless network using such devices, since the identifier is sent in the header of all data packets transmitted over the local wireless network. Using this information, they will be able to connect to the network. To ensure wireless LAN security, a combination of several security methods should be used.
One way to restrict access to a wireless network is to filter by MAC address:
When using filtering by MAC address, the decision on the admission of a specific device to a wireless network is made based on the MAC address. Every time a wireless client attempts to establish a connection or associates with an access point, it must transmit its MAC address. If the filtering function is enabled by MAC address, the access point will search for the MAC address of this device according to its predefined list. Connection to the network will be allowed only to those devices whose MAC addresses are entered into the database of the router. If the MAC address is not in the database, the device will be refused to connect or exchange data over the wireless network.
You can find out the MAC address of the computer network card by running the getmac command in command line. MAC addresses of other network devices are available in the settings of the devices themselves or in the user manual.
This security method has some drawbacks. For example, he assumes that the MAC addresses of all devices that need to be granted access to the network are included in the database before the connection attempt is made. A device not recognized by the database cannot complete the connection. In addition, an attacker can create a clone of the MAC address of a device that has access to the network.
Another way to administer access is authentication. Authentication is the granting of permission to enter the network based on the results of authentication of a set of credentials (password and in some cases a user name).
There are three groups of authentication methods in wireless networks: open authentication, PSK and EAP.
- Open authentication - This is the default authentication setting, in which all devices are allowed to establish connections regardless of their type and membership. Open authentication should only be used in publicly available wireless networks, such as schools and Internet cafes (restaurants).
- Pre-shared Key (PSK) - in this mode, the access point and the client must use a common key or a code word. The access point sends a random byte string to the client. The client accepts this string, encrypts it using the key, and sends it back to the access point. The access point receives an encrypted string and uses its key to decrypt it. If the decoded string received from the client matches the source string sent to the client, the client is given permission to establish a connection. As you can see, one-way authentication is performed in this technology, i.e. access point checks the details of the connected node. PSK does not imply that the device authenticates the access point, nor does it authenticate the user connecting to the access point.
- Extensible Authentication Protocol (EAP)- provides mutual or two-way authentication, as well as authentication of each specific user. If EAP software is installed on the client, the client interacts with an internal authentication server, such as the Remote Authentication Dial-In User Service (RADIUS). This internal server operates independently of the access point and maintains a database of users who have permission to access the network. When using EAP, the user must present the name and password, which are then checked against the RADIUS server database. If the presented credentials are valid, the user is considered authenticated.
Authentication and filtering by MAC address can block a hacker from accessing a wireless network, but cannot prevent interception of transmitted data. Since there are no clear boundaries of wireless networks and all traffic is transmitted without wires, an attacker can easily intercept or read data frames of a wireless network. Encryption is the process of transforming data in such a way that even intercepting information is useless. There are several ways to encrypt data in wireless networks:
- Wired Network (WEP) Compatible Privacy Protocol - This is an advanced security mechanism that allows you to encrypt network traffic during transmission. WEP uses pre-configured keys to encrypt and decrypt data. The WEP key is entered as a string of numbers and letters 64 or 128 bits long (in some cases, WEP also supports 256-bit keys). To simplify the creation and entry of these keys, many devices use passphrases. A passphrase is a simple means of memorizing a word or phrase used in automatic key generation.
- For effective operation of the WEP protocol, the access point, as well as each wireless device that has permission to access the network, must use a common WEP key. Without this key, devices will not be able to recognize data transmitted over the wireless network.
- WEP is an effective means of protecting data from interception. However, WEP also has its weak points, one of which is the use of a static key for all devices with WEP support. There are programs that allow a hacker to determine the WEP key. These programs can be found on the Internet. After the burglar gets the key, he gets full access to all information transmitted.
- One of the means of protecting against such a vulnerability is frequent key changes. There is an advanced and secure encryption tool - Wi-Fi Protected Access Protocol (WPA).
- Wi-Fi Protected Access Protocol (WPA) - this protocol uses encryption keys of length from 64 to 256 bits. At the same time, WPA, in contrast to WEP, generates new dynamic keys each time a client attempts to establish a connection with an access point. For this reason, WPA is considered to be more secure than WEP, since it is much harder to crack.
With this connection, all users wishing to connect to the network will have to enter a single password pre-set in the settings of the access point (Pre-Shared Key), and the data sent will be encrypted with WPA protocol.
In a large-scale wireless network, it may be worth switching to using WPA-Enterprise, where access control to the network will be controlled by the RADIUS authentication server, and the data sent will be encrypted with WPA.
Customize clients
In the case of the included SSID mailing, setting up clients with modern softwareIt boils down to a simple password entry (in the case of non-open network authentication):In the case of disabled SSID distribution, the network will have to be manually determined once. In Windows 7, to do this, go to the Network and Sharing Center, select Manage Wireless Networks and click the Add button. In the window that appears, select Manually create a network profile and in the window that appears, enter all the network data:
After saving the settings, you can connect to this hidden network at any time by selecting it from the list of available.
Tags: wlan, wireless networks, authentication
Wireless LAN (Wireless LAN - WLAN) Ensures that all functions are performed and all the benefits of traditional LAN LAN technologies, such as Ethernet, are preserved, without restrictions on the length of the wire or cable. Typical wireless LAN devices are wireless. network adapters NICs, wireless access points and wireless bridges.
In this example, we use device connections, both using Ethernet technologies and the IEEE 802.11 standards group, a basic standard for WLAN, known to users more by the name of Wi-Fi.
Access Point (AP)also called base station, is a wireless transceiver of a local LAN, which acts as a hub, i.e. The central point of a particular wireless network, or the bridge function, is a wired and wireless network connection point. The use of multiple AP points allows roaming functions to be performed, which provides wireless users with free access within a certain area,
while maintaining continuous communication with the network.
Wireless bridge - provides high-speed (11 Mbit / s) long-range wireless connections within sight (up to 25 miles), implies visibility in the radio sense, - antenna coverage area, between Ethernet networks. In a wireless network, any access point can be used as a repeater (extension point).
Benefits from dedicated LAN:
Materials and tools: An important condition for quality wi-Fi operation network is right choice antenna, connecting cable, as well as the correct selection of active network wireless equipment. The experience of installing and using Wi-Fi equipment shows that the quality of communication is affected by all network components: the output power and sensitivity of the transmitter, the quality of antennas, connecting cables and connectors. In the real world, the quality of any receiving device is determined by its ability to determine the useful signal against the background of interference from neighboring access points, atmospheric and industrial noise.
Sequence when installing a wireless LAN.
Paving a twisted pair. Which cable to choose.
Twisted pair is divided into categories depending on the range of operating frequencies and, accordingly, throughput. The majority of local networks currently organized as a transmission channel use UTP category 5e. This cable fully provides enough bandwidth for home and office up to 100 Mbps. However, for an office with serious internal information traffic, a twisted pair category 6 or 6a is more suitable, on which Fast Ethernet and Gigabit Ethernet networks are built.
What should be twisted pair cable, advantages and disadvantages.
* The main difference between the categories of twisted pair is the frequency of the transmitted signal, which, in turn, determines the quality and speed of data transmission. Categories 5 and 5e operate in the frequency band up to 100 MHz. With the use of cable category 5e, the data transfer rate can be up to 1 Gbit / s, therefore the Cable of this category is currently the most common for laying computer networks.Router, - the brain of the whole network! The main control node of the local network. Also, it is used to make settings for the distribution of access to certain network resources. Plus everything else, for stable job the channel is answered only by it, - the router (well, sometimes another provider). First thing