The development of computer technology is taking place at an ever more rapid pace. A few years after the beginning of its operation, the computer passes into the category of obsolete technology, but this does not mean its uselessness. There are a number of tasks with which such equipment, in this case computers, can quite cope. All you have to do is make them Terminal Services thin clients.
Terminal Service allows multiple applications to run concurrently on a server. The client, on the other hand, acts as a terminal - it only transmits data about the keys pressed and the position of the mouse cursor to the server. The server performs the necessary calculations and returns to the terminal the image displayed on the monitor. For the user sitting at the terminal, the whole process looks exactly the same as if the application was running on his computer. The advantage of this technology is that almost no load falls on the "hardware shoulders" of the client, because the entire computing process takes place on the server side. Thus, having a sufficiently powerful server at your disposal, you can use existing low-performance computers to perform tasks that they are no longer able to cope with in other configurations. The greatest effect from the use of terminals is achieved in conditions of ensuring the work of a large number of users performing the same type of tasks, for example, classrooms or office work places.
The thin client only transmits data about keyboard and mouse events to the terminal server, receiving graphic data from the server to display on the monitor.
The performance of such a system will depend only on the capacity of the resources of the terminal server. When using a terminal server based on Windows 2008 Terminal Server, communication between computers is carried out via the RDP (Remote Desktop Protocol) protocol, and it is also possible to connect via the web interface via the secure SSL protocol (port 443), with the ability restricting access to applications.
In addition to the low requirements for the hardware resources of the terminal clients, such solutions have a number of other advantages. In the case of using applications that need constant communication between the client and the server, the load on the network is significantly reduced. In this case, both the client software and the server are physically located on the same computer, the bulk of the data is located on the server itself. Only the result ready for display is sent to the terminal client. The data used by the clients of the terminal of the application software as such is not transmitted over the network at all, excluding their interception. The modernization of the computers of the terminal clients no longer needs to be done every time when the new software becomes more and more demanding on the hardware resources of the computer equipment - it is enough to increase the resources of the terminal server.
Storing data on a server greatly simplifies backing up data. Saving on sources uninterruptible power supplysince disconnection of the terminal client or its complete failure will not lead to information loss. Administration tasks are greatly simplified. Applications must be installed and updated only on the server - changes to the terminal server affect all workstations simultaneously. The absence of removable media on the terminal clients, increases security and allows you to save on antivirus software, will remove the need to control the installation of unauthorized software by users and the possibility of leakage of confidential information. Customization software the terminal requires significantly less time and effort than deploying local copies of the OS.
Of course, terminal technologies also have a number of application restrictions. The use of terminals is extremely inefficient and sometimes even impossible to ensure the operation of "heavy" applications that require a lot of complex calculations, for example, programs like AutoCAD. Intensive load on the server processor will cause a decrease in service to other clients. Also, do not use terminals when running programs that create streaming video and 3D, or connecting to a terminal server remotely. In this case, the network may not be able to handle the transfer of information to the terminal. That is, it will not be possible to play modern 3D games and watch movies on the terminals. For such cases, you can use a mixed architecture, installing full-fledged PCs on the necessary workstations. The main attention should be paid to ensuring uninterrupted operation of the server - if it fails, no terminal client will be able to continue working.
Terminal servers are not new and have been around since the days of the huge mainframes. Previously, terminal servers were used due to the limited system resources of clients. Now they are used for greater ease of administration - you set up a terminal server, install an application (for example, 1C) and provide all users who need access to this application. The advantage is that users can be located in different cities and even countries and they are not limited to just the corporate LAN.
Nowadays, the entire IT infrastructure is gradually "moving" to the clouds, because it is easier, more convenient and even cheaper. This article contains instructions for setting up a virtual terminal server based on the xelent.cloud platform.
Why move to the cloud?
After all, you can take a physical server, "raise" a terminal server on it and provide access to the same 1C to everyone who needs it. We have already written about the advantages of a virtual server earlier and I really don't want to repeat myself. In short, the virtual server does not need physical maintenance (for example, replacing failed components, the same cleaning from dust, etc.), it is easier to back up and restore the server (after all, there are snapshots), no need to buy expensive UPS, organize a backup Internet channel. The xelent.cloud platform takes care of all this.
As it was already calculated in the article "Physical or virtual", the maintenance of a virtual server is inexpensive, and sometimes even cheaper than a physical server, given the huge costs of purchasing it.
The only thing that will have to be spent additionally is for terminal access licenses. But you would buy them anyway, no matter what kind of server you have - local physical, virtual or dedicated.
Creating a virtual server
The first step is to create a virtual server. Since we will be creating a terminal server, we need to order the appropriate configuration. Two cores are no longer enough, at least four cores, 12 GB of "RAM" and a 120 GB SAS disk. You do not need to order a disk that is too large - you can always increase its volume. Operating system - Windows Server 2012 R2. In principle, you can choose a different version (2008 or 2016), but below all illustrations will be shown using Windows Server 2012 R2 as an example.
Figure: 1. Created (minimal) server configuration
It should be noted that such a configuration will cost only 4,820 rubles per month - not much money for an enterprise. This configuration will be enough for 5 users to work simultaneously. If you need more, it is recommended to increase the number of cores to 8 and the volume random access memory up to 16 GB. This configuration is sufficient for comfortable work 10-15 users (simultaneously). But it will also cost 6520 rubles a month.
So, our server is created (Fig. 2). By the way, it took only 2 minutes and 57 seconds to create it. Wondering how long it will take to deliver the physical server and set it up for the first time?

Figure: 2. The virtual server is created
Connect to the server using the information provided in the control panel.

Figure: 3. Remote connection to the server. Server Manager launched
Installing Remote Desktop Services
Open Server Manager if you closed it. To do this, launch it from the shortcut on the taskbar or run the servermanager.exe command - whichever you prefer (Fig. 3).
From the Manage menu, select Add Roles and Features (Figure 4). The Add Roles and Features Wizard will open (Figure 5).

Figure: 4. Menu Control

Figure: 5. Wizard for adding roles and components
Then follow these steps:
- Click the button Further.
- Leave the switch in position Installing roles or componentsin(fig. 6) and press the button again Further.
- Select a server from the pool where you want to install Terminal Services. In our case, there will be one server (Fig. 7). Click the button Further.
- Check the role Remote Desktop Services and press the button Further.

Figure: 6. Leave the switch in the Install Roles or Features

Figure: 7. Select server

Figure: 8. Select Remote Desktop Services
- Leave the components unchanged, that is, on the next screen Add Roles and Features Wizards just click Further.
- The wizard will display a description of the Remote Desktop Services role (Figure 9). Click the button Further.
- Select the role services to install. Install Remote Desktop Licensing... Immediately after choosing this service, you must agree to the installation of additional components by clicking Add components, see fig. ten.
We also need a service Remote Desktop Session Host (fig. 11). As in the previous case, you need to agree to add additional components.


Figure: 10. Select Remote Desktop Licensing and then click the Add Features button

Figure: 11. Installing the Remote Desktop Session Host service
We have defined all the parameters for installing the role. On last page wizard enable the parameter Automatically restarting the destination serverif required and press the button Install(fig. 12).

Figure: 12. Click the Install button
If clouds are for you
not just theory
Wide range of services
by selected north
and multicloud solutions
It remains to wait for the role to be installed. If everything goes well, you will see a message after the restart. successful installation all selected services and components. Just press the button Closeto complete the wizard.

Figure: 13. Installation complete
Configuring a License Server for Remote Desktop
Now you need to start. To do this, select the appropriate command from the menu Facilities, Terminal Services Server manager.

Figure: 14. Run the Remote Desktop Licensing Diagnostic Tool
The diagnostic tool will report that there are no licenses available yet because the licensing mode for the RD Session Host server is not set (Figure 15). The diagnostic will also report that the grace period (120 days by default) has not yet expired, but this server is not yet configured to use at least one license server.

Figure: 15. No licenses available
You need to know the following about the grace period:
- There is a grace period during which the license server is not required, but after the grace period, clients must use a valid RDS CAL issued by the license server to connect to the server.
- Remote Desktop supports two simultaneous connections for remote computer administration. No licensing server is required for these connections.
In other words, while you have not yet purchased licenses for terminal access, you can take advantage of the grace period. Why not use a terminal server for free for 4 months? Then, if you only need two remote connections, for example, you have two remote offices, then the licensing server is not required at all, and the configuration of the virtual server can be simplified - 8 GB of "RAM" is enough.
In Windows Server 2012, the licensing server is listed in local group policies, so run gpedit.msc to open the local group policy editor.
Go to Computer Configuration, Administrative Templates. Windows components, Remote Desktop Services, Remote Desktop Session Host, Licensing (Figure 16).

Figure: 16. Local Group Policy Editor
Open the options Use Specified Remote Desktop Licensing Servers - just double click on the parameter name. In the window that appears, set the switch to Includedand specify which license server to use. We will be using the same server (Figure 17). Specify the server name or its IP address and click the button OK.

Figure: 17. Licensing server parameters
Next open the options Set the Remote Desktop Licensing Mode... Set the switch to position Includedand specify the license mode for the RD Session Host server. There are two options - "Per device" or "Per user". Let's say you have 10 licenses. In Per Device mode, you can create an unlimited number of users on the server that can connect via Remote Desktop from only 10 computers with these licenses installed. If you select the "Per user" mode, then only 10 selected users will be able to access the server, but from any device. Often the "Per user" mode is more preferable, so we choose it.

Figure: 18. Selecting a licensing mode
As a result, you should have the parameters set as shown in Fig. 19. Close the Local Group Policy Editor window.

Figure: 19. Result of parameter setting
Return to the Remote Desktop Licensing Diagnostic Tool window and click Refresh... You will see new error, which tells us that the license server is not enabled (Figure 20).

Figure: 20. New error
To start the licensing server, go to - it can be called in the menu Facilities, Terminal Services... Find our server in the list, click on it right click mouse and select command Activate server (fig. 21).

Figure: 21. Remote Desktop Licensing Manager
A window will open Server Activation Wizardswhere you need to press the button Further- on the first page of the wizard (fig. 22). Select a connection method. It is recommended to leave everything as it is - Auto(fig. 23).

Figure: 22. Server Activation Wizard

Figure: 23. Choosing a connection method
Enter your organization information and click Next. additional information It is not recommended to fill in about the organization, just click Next.

Figure: 24. Entering information about the organization

Figure: 25. Additional information about the organization
The license server has been activated successfully. Now you need to start the license installation wizard. Leave the checkbox on and click Further(fig. 26).

Figure: 26. The license server is activated
Installing Remote Desktop Services Licenses
So in the previous section, you pressed the button Furtherwith active checkbox Run the license installation wizard... In the window that appears, just click the button Further.

Figure: 27. The License Installation Wizard is running
Select the licensing program you need. Here you must select your specific licensing program. In the article, for reasons of demonstrating server configuration, we will use the program Enterprise Agreement (fig. 28).

Figure: 28. Select a licensing program
Enter the agreement number. It usually consists of seven digits. Click the button Further(fig. 29).

Figure: 29. Entering the agreement number
Next, you need to select the product version (select Windows Server 2012), the type of license and the number of licenses. Previously we selected the Per User licensing type, so here we have to select Remote Desktop Services User CAL... Enter the number of licenses available on this server licensing.

Figure: 30. Product version and license type

Open up. You need to make sure that the server is running and also view the total available number of installed licenses (Figure 32).

Figure: 32. Remote Desktop Licensing Manager
Return to Remote Desktop Licensing Diagnostic Tool and make sure there are no errors. At the same time, you will see information about installed licenses (fig. 33).

Figure: 33. Remote Desktop Licensing Diagnostic Tool. No mistakes
This completes the terminal server configuration. You just have to add users who are allowed remote access to the server to the group Remote Desktop Users (Remote Desktop Users). Indeed, by default, only server administrators have RDP access to the server desktop, and making all users administrators is a bad idea. We will talk about how to do this in the next article.
Connecting to a terminal server
An application is used to connect to a terminal server (Fig. 34). There is nothing difficult in using it - you need to specify the server IP address, username and password. When correct setting the server will be connected. However, even this simple application, as Remote Desktop Connection, there are secrets that will be discussed in the next article.

Figure: 34. Remote Desktop Connection (note the username is den, not CloudAdmin)
Actually, that's all. The task at hand, namely the configuration of the virtual terminal server, is completed, and you can use it in full. In the next article, we will talk about cloud accounting.
Implementation of terminal access facilities in recent times arouses considerable interest among the heads of many companies - after all, this category of products, if properly applied, can provide a significant reduction in both the costs of maintaining corporate software and the costs of regular hardware updates. In this article, we'll talk about what this product category can do for small businesses.
What is terminal access
once upon a time, when personal computers were not yet known to mankind, the typical architecture of any corporate application was one that used a mainframe (or, in the case of a poorer company, a minicomputer) and a number of controlled by the same mainframe (or minicomputer) non-intelligent external terminal devices. This approach, based on the complete centralization of resources, data and applications, had certain advantages - with all its shortcomings and the high cost of computing equipment of those years, it, firstly, allowed to solve problems that users of the first personal computers never dreamed of, and secondly , was distinguished by the relative (of course, for that time) ease of operation - after all, all computer equipment was physically located in one place, and users jointly exploited a common processor, memory, external devices, multitasking operating system and a set of applications.
Modern means of terminal access, used on personal computers, specialized terminal workstations and handheld devices, are based on a similar principle of centralization of computation and collectivization of resources. The user in this case runs on workstation the client part of the terminal access tool and with its help addresses the remote server computer containing the corresponding server part this tool... Upon successful authentication, the server part of the terminal access facility creates its own session for the user, in which either he himself manually or automatically (it depends on the session settings and access rights) in the address space of the server launches the applications he needs. The user interface of the applications launched in this way is available to the user of the workstation in the window of the client part of the terminal access tool, and he can use the keyboard and mouse of the workstation to control this application - information about the keys pressed and mouse movement (and often the contents of the clipboard) are transmitted to the session given user on the server, and changes are sent back to user interface applications. When the user session ends, all applications running in it are closed.
Terminal access and IT infrastructure costs
the advantages of using terminal access become obvious when there are a large number of workstations or with increased requirements for security and centralization of data storage. If applications are accessed using a terminal access tool, then only the operating system and the client part of this tool are installed on the workstations, and the applications themselves, with which users work, are installed on the terminal server. In this case, the costs of maintaining workstations turn out to be much lower than when they are fully equipped with client parts of corporate applications, office suites, mail clients and other products used in the company, and the requirements for the hardware of such workstations are very moderate. In addition, there are special workstations for windows management CE designed to work in this particular mode. True, the requirements for the terminal server hardware can be very high - they depend on the number of concurrent users. But modern means of terminal access, as a rule, are able to work with server clusters and balance the load.
While the cost savings in purchasing, upgrading, and maintaining workstations can be calculated fairly easily, the savings associated with provisioning additional security access to corporate data is not immediately apparent. As long as the applications are executed on a remote server, on the end user's workstation there is neither the client side of the server DBMS used in the company, much less access to the files of the desktop DBMS, and this significantly reduces the risk of unauthorized access to corporate data - otherwise than by regular means using the corporate application) you will not be able to access them.
Leading providers of terminal access facilities
Microsoft
The simplest means of terminal access, called terminal services, are part of the server windows versions... Terminal Services is available for Windows NT Server 4.0, Terminal Server Edition (the first version of Terminal Access tools co-created with Citrix), Windows 2000 Server, Windows 2000 Advanced Server, Windows 2000 Datacenter Server, Windows Server 2003 (all editions).
Control tools for terminal operation parameters windows services relatively simple. When windows application Server 2003, Enterprise Edition, you can balance server load; dynamic control of session parameters is possible; client sessions can have screen resolutions up to 1600Ѕ1200 and True Color, and Windows Server 2003 Terminal Services clients can access their local resources (external devices, disks, etc.) from within a terminal session. Here, in fact, are all the capabilities of Windows terminal services available today. However, these services are often used by network administrators to implement remote control servers, as well as in development companies and in software development departments to access applications installed on other computers.
Access licensing through terminal services is carried out as follows. All devices using Terminal Services access must have a Windows Server 2003 Terminal Server Device (CAL) license that grants Windows Server 2003 access for the device, or their user must have a Windows Server 2003 Terminal Server User CAL. In addition there is windows license Server 2003 Terminal Server External Connector License for anonymous concurrent connections to Terminal Services over the Internet for application providers.
Citrix
Citrix is \u200b\u200brightfully considered the leader of the terminal access market today. This company produces terminal access tools for Windows and UNIX; at the same time, the specified set of tools differs from the Windows terminal services (licensed at one time from the same Citrix) in a very wide range of both the possibilities for configuring client sessions and tools for managing terminal servers and other network resources, involved in the use of terminal access, as well as a comprehensive set of integrated related tools and technologies, such as password management, secure access, roaming terminal connections when moving a client from one place to another. So, using the tools included in the Citrix Access Suite running on top of Windows Terminal Services, you can set a very wide range of session parameters (window size, screen resolution, number of colors, rules for working with audio data), up to creating sessions that start in a window mode, only one specific application and terminated at the end of its work, carry out detailed monitoring of the entire distributed system and analyze the use of resources in user sessions, implement optimal control so-called server farms - clusters of servers containing applications of the same type, by balancing their load.
Note that when Citrix technologies are used (in particular, the ICA - Independent Computing Architecture), only information about mouse manipulations and keyboard input, as well as changes in the image on the screen, is transmitted over the network, which limits the bandwidth required for a session to less than 20 Kbps.
Citrix Access Suite supports access to terminal servers from DOS, Windows, Mac OS, UNIX, Linux, OS / 2, Java workstations from browsers using Netscape plug-ins or Active X controls for Internet Exploreras well as from a wide range of mobile devices.
Accompanying products
having started to use terminal access, companies often face other tasks, such as managing access to applications, multiple user passwords, protecting transmitted data, providing access that does not depend on the infrastructure and the type of device, interaction between users and effective maintenance of their IT- service. For this purpose, they may need tools for password management, conferencing, remote control of workstations and their interface. All of these products are available as part of the Citrix Access Suite, the release of which will provide a fully integrated solution that provides a unified infrastructure for user access to applications.
Terminal access for small businesses
traditionally, it was believed that terminal access tools should be implemented at large enterprises with a large number of workstations of the same type, and reports on the most famous projects for the introduction of such tools often refer to tens of thousands of jobs and huge budgets. However, there are products in this category that make sense to implement in small and medium-sized enterprises.
Among the novelties in this area, we first of all note the Citrix Access Essentials product focused on this market segment. This product can serve companies using the platform Microsoft Windows with the number of terminal jobs not exceeding 75 (including portable and mobile devices) and meets the requirements of small companies - its acquisition and implementation will be relatively cheap due to inexpensive licenses (less than $ 250 per one workplace, which already includes a license for the use of Windows Terminal Services - Windows Terminal Server Client Access License) and ease of deployment and administration.
Citrix Access Essentials Technical Features
Citrix Access Essentials is server applicationthat runs under Windows Server 2003 and provides access to applications installed on this server through a Web interface. This product requires one server with an operating microsoft system Windows Server 2003 Standard or Enterprise Edition, network connection between user devices and the server; and a Web browser on each connected device.
Citrix Access Essentials supports two operational options: running on a single server (Figure 1) and operating with Citrix Access Gateway hardware (Figure 2). In the first case, remote users can access the terminal server through a firewall, in the second, through a virtual private network Access Gateway VPN (in this case, the terminal server is installed in the DMZ, which provides increased security of access to applications).


To help secure server access, Citrix Access Essentials supports several methods for authenticating users, including using encryption.
Deployment of the Citrix Access Essentials server is simplified as much as possible - for this purpose, the product package includes the Quick Start utility, which is a wizard for installing and configuring the server, registering licenses, generating client distributions, and publishing applications on the server. Client parts are available for all versions of Windows, Windows CE, Pocket PC 2003, Mac OS X, Linux, Solaris, as well as for devices that support Java.
The tools for server management, configuration changes, and user access control included in Citrix Access Essentials are also as simple as possible: their mastering, in my opinion, should not cause any difficulties for specialists involved in administering networks of small companies (Fig. 3). They allow you to perform almost any operation, up to customizing the appearance of the interface of the client part of this product (Fig. 4). In addition, the product is supplied with highly detailed documentation describing every administrator's action, from installing the server to optimizing its performance, setting security settings and accessing external devices.


In other words, this product was really created taking into account the peculiarities of small companies, including the limited funds for the use of the services of highly qualified (and, accordingly, expensive) IT specialists.
Licensing
Citrix Access Essentials is licensed as follows. The product is available as named licenses, purchased for each user who will use the software. This product does not support concurrent use or device or server licensing. The product can be purchased with or without Subscription Advantage.
When using Citrix Access Essentials (like any other means of terminal access), you should also follow the licensing rules for software that will be accessed in terminal mode - licensing agreements for modern software usually provide for certain rules for using products in such a mode. In particular, when operating in this mode, the number of purchased licenses must be equal to the number of connected workstations, despite the fact that only one copy of the application is actually installed on the server.
Citrix Access Essentials and Cost Savings
How much will small and midsize businesses avoid by implementing Citrix Access Essentials? The standard advantages of using terminal access means, such as reducing the cost of maintaining the same type of workstations, their hardware, in the case of small enterprises at first do not seem so obvious. But after all, the budget of such enterprises is not large, so the possibility of avoiding unnecessary maintenance costs, even if not as significant as in large enterprises, is even more relevant for small companies. And providing additional security for access to corporate data for small businesses can be vital - if leaked, the consequences for small companies can be much more severe than for large enterprises.
Among the costs that small companies that have implemented Citrix Access Essentials will be able to avoid, first of all, we should highlight the costs of transforming the existing IT infrastructure and implementing new solutions when expanding the business, for example, when opening new offices and branches. In this case, the implementation of terminal access to the corporate information systems available in the central office (such as enterprise management systems, warehouse, accounting or personnel records) is usually much simpler and cheaper than deploying an independent infrastructure in a branch and organizing data synchronization with the central office... In addition, a relatively large part of modern small and medium-sized businesses have so-called mobile employees on their staff, ensuring for whom communication with offices, security of access to corporate applications and data, as well as control of these processes is a very difficult task, which will also help Citrix Access Essentials. Given the potential reduction in the aforementioned costs, IT leaders in small companies should take a closer look at this product - perhaps it will be able to solve the problems facing some of them.
The introduction of terminal access facilities has recently attracted considerable interest among the heads of many companies - after all, this category of products, if properly applied, can provide a significant reduction in both the costs of maintaining corporate software and the costs of regular hardware updates. In this article, we'll talk about what this product category can do for small businesses.
What is terminal access
once upon a time, when personal computers were not yet known to mankind, the typical architecture of any corporate application was one that used a mainframe (or, in the case of a poorer company, a minicomputer) and a number of controlled by the same mainframe (or minicomputer) non-intelligent external terminal devices. This approach, based on the complete centralization of resources, data and applications, had certain advantages - with all its shortcomings and the high cost of computing equipment of those years, it, firstly, allowed to solve problems that users of the first personal computers never dreamed of, and secondly , was distinguished by the relative (of course, for that time) ease of operation - after all, all computer equipment was physically located in one place, and users jointly exploited a common processor, memory, external devices, a multitasking operating system and a set of applications.
Modern means of terminal access, used on personal computers, specialized terminal workstations and handheld devices, are based on a similar principle of centralization of computing and collectivization of resources. In this case, the user launches the client part of the terminal access tool on the workstation and uses it to access the remote server computer containing the corresponding server part of this tool. Upon successful authentication, the server part of the terminal access facility creates its own session for the user, in which either he himself manually or automatically (this depends on the session settings and access rights) in the server address space, the applications he needs are launched. The user interface of applications launched in this way is available to the user of the workstation in the window of the client part of the terminal access tool, and he can use the keyboard and mouse of the workstation to control this application - information about the keys pressed and mouse movement (and often the contents of the clipboard) are transmitted to the session of this user on the server, and changes are sent back to the application user interface. When the user session ends, all applications running in it are closed.
Terminal access and IT infrastructure costs
the advantages of using terminal access become obvious when there are a large number of workstations or with increased requirements for security and centralization of data storage. If applications are accessed using a terminal access tool, then only the operating system and the client part of this tool are installed on workstations, and the applications themselves, with which users work, are installed on the terminal server. In this case, the costs of maintaining workstations turn out to be much lower than when they are fully equipped with client parts of corporate applications, office suites, mail clients and other products used in the company, and the requirements for the hardware of such workstations are very moderate. In addition, there are special workstations running Windows CE designed to work in this mode. True, the requirements for the terminal server hardware can be very high - they depend on the number of concurrent users. But modern means of terminal access, as a rule, are capable of working with server clusters and balancing the load.
While the cost savings in purchasing, upgrading and maintaining workstations can be calculated fairly easily, the savings associated with providing additional security for accessing corporate data are not immediately apparent. As long as the applications are executed on a remote server, on the end user's workstation there is neither the client side of the server DBMS used in the company, much less access to the files of the desktop DBMS, and this significantly reduces the risk of unauthorized access to corporate data - otherwise than by standard means (i.e. using the corporate application) you will not be able to access them.
Leading providers of terminal access facilities
Microsoft
The simplest terminal access tools, called terminal services, are included with server versions of Windows. Terminal Services is available for Windows NT Server 4.0, Terminal Server Edition (the first version of Terminal Access tools co-created with Citrix), Windows 2000 Server, Windows 2000 Advanced Server, Windows 2000 Datacenter Server, Windows Server 2003 (all editions).
The controls for Windows Terminal Services are relatively simple. When using Windows Server 2003, Enterprise Edition, you can balance server load; dynamic control of session parameters is possible; client sessions have screen resolutions up to 1600Ѕ1200 and True Color, and Windows Server 2003 Terminal Services clients can access their local resources (external devices, disks, etc.) from within a terminal session. Here, in fact, are all the capabilities of Windows Terminal Services available today. However, these services are often used by network administrators to remotely manage servers, as well as by development companies and software development departments to access applications installed on other computers.
Access licensing through terminal services is carried out as follows. All devices using Terminal Services access must have a Windows Server 2003 Terminal Server Device (CAL) license that grants Windows Server 2003 access for the device, or their user must have a Windows Server 2003 Terminal Server User CAL. In addition, there is a Windows Server 2003 Terminal Server External Connector License that allows anonymous concurrent connections to Terminal Services over the Internet for application providers.
Citrix
Citrix is \u200b\u200brightfully considered the leader of the terminal access market today. This company produces terminal access tools for Windows and UNIX; at the same time, the specified set of tools differs from the Windows terminal services (licensed at one time from the same Citrix) in a very wide range of both the possibilities for configuring client sessions and tools for managing terminal servers and other network resources used when using terminal access, as well as an exhaustive set integrated with each other related tools and technologies, such as password management, secure access, roaming terminal connections when moving a client from one place to another. So, using the tools included in the Citrix Access Suite running on top of Windows Terminal Services, you can set a very wide range of session parameters (window size, screen resolution, number of colors, rules for working with audio data), up to creating sessions that start in the window mode, only one specific application and terminated at the end of its work, carry out detailed monitoring of the entire distributed system and analysis of resource use in user sessions, implement optimal management of so-called server farms - server clusters containing applications of the same type, by balancing their load.
Note that when Citrix technologies are used (in particular, the ICA - Independent Computing Architecture), only information about mouse manipulations and keyboard input, as well as changes in the image on the screen, is transmitted over the network, which limits the bandwidth required for a session to less than 20 Kbps.
Citrix Access Suite supports access to terminal servers from DOS, Windows, Mac OS, UNIX, Linux, OS / 2, Java workstations from browsers using Netscape plug-ins or Active X controls for Internet Explorer, as well as from a wide range mobile devices.
Accompanying products
having started to use terminal access, companies often face other tasks, such as managing access to applications, multiple user passwords, protecting transmitted data, providing access that does not depend on the infrastructure and the type of device, interaction between users and effective maintenance of their IT- service. For this purpose, they may need tools for password management, conferencing, remote control of workstations and their interface. All of these products are available as part of the Citrix Access Suite, the release of which will provide a fully integrated solution that provides a unified infrastructure for user access to applications.
Terminal access for small businesses
traditionally, it was believed that terminal access tools should be implemented at large enterprises with a large number of workstations of the same type, and reports on the most famous projects for the introduction of such tools often refer to tens of thousands of jobs and huge budgets. However, there are products in this category that make sense to implement in small and medium-sized enterprises.
Of the novelties in this area, first of all, we note the Citrix Access Essentials product oriented to this market segment. This product can serve companies using microsoft platform Windows with no more than 75 terminal workplaces (including portable and mobile devices) and meets the requirements of small companies - its acquisition and implementation will cost relatively cheap due to inexpensive licenses (less than $ 250 per seat, where already Windows Terminal Server Client Access License included) and ease of deployment and administration.
Citrix Access Essentials Technical Features
Citrix Access Essentials is a server application that runs on Windows Server 2003 and provides Web-based access to applications installed on that server. This product requires one server running Microsoft Windows Server 2003 Standard or Enterprise Edition, a network connection between user devices and the server, and a Web browser on each connected device.
Citrix Access Essentials supports two operational options: running on a single server (Figure 1) and operating with Citrix Access Gateway hardware (Figure 2). In the first case, remote users can access the terminal server through a firewall, in the second, through the Access Gateway VPN server (the terminal server is installed in a DMZ, which provides increased security for access to applications).


To help secure server access, Citrix Access Essentials supports several methods for authenticating users, including using encryption.
Deployment of the Citrix Access Essentials server is simplified as much as possible - for this purpose, the product package includes the Quick Start utility, which is a wizard for installing and configuring the server, registering licenses, generating client distributions, and publishing applications on the server. Client parts are available for all versions of Windows, Windows CE, Pocket PC 2003, Mac OS X, Linux, Solaris, as well as for devices that support Java.
The tools for server management, configuration changes, and user access control included in Citrix Access Essentials are also as simple as possible: their mastering, in my opinion, should not cause any difficulties for specialists involved in administering networks of small companies (Fig. 3). They allow you to perform almost any operation, up to customizing the appearance of the interface of the client part of this product (Fig. 4). In addition, the product is supplied with highly detailed documentation describing every administrator's action, from installing the server to optimizing its performance, setting security settings and accessing external devices.


In other words, this product was really created taking into account the peculiarities of small companies, including the limited funds for the use of the services of highly qualified (and, accordingly, expensive) IT specialists.
Licensing
Citrix Access Essentials is licensed as follows. The product is available as named licenses, purchased for each user who will use the software. This product does not support concurrent use or device or server licensing. The product can be purchased with or without Subscription Advantage.
When using Citrix Access Essentials (like any other means of terminal access), you should also follow the licensing rules for software that will be accessed in terminal mode - licensing agreements for modern software usually provide for certain rules for using products in such a mode. In particular, when operating in this mode, the number of purchased licenses must be equal to the number of connected workstations, despite the fact that only one copy of the application is actually installed on the server.
Citrix Access Essentials and Cost Savings
How much will small and midsize businesses avoid by implementing Citrix Access Essentials? The standard advantages of using terminal access means, such as reducing the cost of maintaining the same type of workstations, their hardware, in the case of small enterprises at first do not seem so obvious. But after all, the budget of such enterprises is not large, so the possibility of avoiding unnecessary maintenance costs, even if not as significant as in large enterprises, is even more relevant for small companies. And providing additional security for access to corporate data for small businesses can be vital - if leaked, the consequences for small companies can be much more severe than for large enterprises.
Among the costs that small companies that have implemented Citrix Access Essentials will be able to avoid, first of all, we should highlight the costs of transforming the existing IT infrastructure and implementing new solutions when expanding the business, for example, when opening new offices and branches. In this case, the introduction of terminal access to corporate information systems available in the central office (such as enterprise management systems, warehouse, accounting or personnel records) is usually much simpler and cheaper than deploying an independent infrastructure in a branch and organizing data synchronization with the central office. ... In addition, a relatively large part of modern small and medium-sized businesses have so-called mobile employees on their staff, ensuring for whom communication with offices, security of access to corporate applications and data, as well as control of these processes is a very difficult task, which will also help Citrix Access Essentials. Given the potential reduction in the aforementioned costs, IT leaders in small companies should take a closer look at this product - perhaps it will be able to solve the problems facing some of them.
Thin client (English thin client) in computer technology - a computer or client program in networks with a client-server or terminal architecture, which transfers all or most of the information processing tasks to the server. An example of a thin client is a computer with a browser that is used to run web applications.
In addition to the general case, a hardware thin client (for example, Windows and Linux terminals) should be distinguished - a specialized device that is fundamentally different from a personal computer (PC). The hardware thin client does not have a hard disk, uses a specialized local operating system (OS, one of the tasks of which is to organize a session with a terminal server for the user to work), does not include moving parts, and is executed in specialized cases with completely passive cooling.
To expand the functionality of a thin client, they resort to its "thickening", for example, they add the capabilities of autonomous work, while maintaining the main difference - working in a session with a terminal server. When moving parts appear in the client ( hard drives), there are opportunities autonomous work, it ceases to be a pure thin client, but becomes a universal client.
In most cases, a thin client has a minimal hardware configuration; instead of a hard disk, a DOM is used to load a local specialized OS (DiskOnModule - a module with an IDE connector, flash memory and a microcircuit that implements the logic of a conventional hard disk - is defined in the BIOS as a normal hDD, only its size is usually 2-3 times smaller). In some system configurations, the thin client boots the operating system over the network from the server using PXE, BOOTP, DHCP, TFTP and Remote Installation Servic.
Terminal Access - Access to information system (IS), organized so that the local terminal machine does not perform computing work, but only redirects the input of information (from the mouse and keyboard) to the central machine (terminal server) and displays graphic information on the monitor. Moreover, all the computing work in the terminal system is performed on the central machine.
As shown above, historically, terminal access was first organized on computers capable of simultaneously serving several computing processes. This made it possible to more efficiently distribute computing resources among the users of the first very expensive computers. With the advent of cheap personal computers, the role of terminal access began to decrease somewhat, since it was believed that sufficient performance of the IP could be obtained on the desktop of each PC user.
However, later it became obvious that the low cost of PCs is not able to compensate for the daily costs of maintaining a large number of user workstations, which supposedly have advantages due to the possibility of personalizing settings for operating systems and software (software). In reality (in large organizations), the presence of a large number of "motley" equipment instead of advantages creates additional difficulties for users and system administrators. Issues of ensuring IP security also required a revision of views and a return to terminal access as more unified and economically viable.
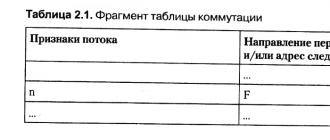
User workstations are equipped with "thin client" terminals - inexpensive and simple specialized devices that take up a minimum of space, are silent and require virtually no maintenance. They can be computers without an installed operating system and programs (everything is loaded from the server), which are only a device for entering and displaying information. Almost any computer with a Celeron 300MHz processor, 64MB RAM or more can be used as a terminal, and there is no need for a hard disk. All applications run on the server, only screen refresh data is transmitted to the client over the network, and keystrokes and mouse movements from the client to the server. Appearance personal computer and thin client is shown in Fig. 2.1.
Figure 2.1 - Appearance of a thin client (right) in comparison with a traditional desktop PC
Terminal network - This is the principle of building a computer network and working in it, which is characterized by speed, reliability and efficiency in comparison with a "regular" office network.
Terminal Server – a computer with a specially configured server operating system Windows 2003 Server and installed 1C programs: Enterprise, Word, Excel, and others.
For the user of the terminal, everything looks as if a computer, equal in power to the server, was on his desk. You can connect dozens of terminals to one server and none of the users notices that the server is being used by someone else. In the terminal network 1C: Enterprise and other databases work much faster.
From the user's point of view, working with a thin client from working with a traditional PC has only one difference. The difference is silence. There is no source of noise in the thin client because there is no moving part.
A variant of the structural diagram of a network built on these principles is shown in Fig. 2.2.

Figure 2.2 - Block diagram of the terminal network
2.2 Local network facilities based on "thin clients"
A wide variety of thin clients are currently available, with varying features and costs.
Number of users in local network depends on the operating system loaded on the server. For instance:
Windows XP - allows you to serve 10 thin clients;
Windows 2003 Server - allows servicing 70 thin clients;
Windows 2008R2 - allows you to serve up to 100 thin clients.
The distance between the clients and the server is usually up to 100m. Clients' connection to the server is cable or wireless, for example, using Wi-Fi technology.
For example, Russian-made OPTION Wi-Fi thin client devices have the following characteristics. Power supply unit power: 5V1A consumed 4-5W.
Minimum requirements: P4 2.0 or above 512M memory; overall dimensions: 14.5 * 14.5 * 3.2 (cm); weight: 220 gr.
Interface: PS / 2 VGA LAN DC SPk USB.
OS Support: Windows 2000 Windows XP Windows 2000/2003/2008 Server, Windows 7.
The server in the terminal network performs a triple function:
First of all, it is a file server providing centralized storage of station configuration files and all user files. It also suggests itself to launch an http-server on it, software that organizes the exchange of e-mail messages, and an SQL server (in case the process of using the network reaches the proper height);
In addition, the server acts as a kind of "application server", because it is on it, in fact, that most of the tasks launched by users are executed. From which it follows that he must have user accounts corresponding to station users. Moreover, the home directories of these users must contain configuration files that determine the execution of the necessary applications;
Finally, the server is used as the only workstation in the network where all installed applications can be launched. In fact, the algorithm for "expanding" the functionality of the network is as follows: the administrator, if necessary, installs an application on the server.
Servers are different and they perform completely different tasks. The range of tasks, and, accordingly, the requirements for a specific server, depend on the role that the server has to play in the information and telecommunications (IT) infrastructure of the organization. Below we will consider two types of servers: file server and terminal server. The first is required when using desktop PCs in workplaces, the second - when using thin clients in workplaces.
The file server solves a fairly simple task - it provides users with access to their work information.
The terminal server solves a more complex problem - it provides users, in addition to access to their information, a full-fledged working environment in which user applications are executed.
The requirements for a file server are not high - a sufficient level of information storage reliability at a reasonable price (achieved by using RAID 1 and inexpensive Serial ATA hard drives in the disk subsystem) and normal server availability, which is achieved by using entry-level server components.
The requirements for the terminal server are much higher. He must:
Provide access to information 24 hours a day, 365 days a year (which is achieved by using server hard drives and using a level 5 RAID array);
Provide a comfortable working environment for every user.
The last point is the most interesting for us, because it is he who determines the requirements for server performance. The starting point in this case is the number of jobs.
Processors. To service 50 thin clients, a 2-processor configuration based on Intel Xeon class processors with 800 MHz bus is required and sufficient.
RAM. 256 MB of memory is required for the operation of Windows 2003 Server, 64 MB is required for each session.
Thus, the first 1 GB of memory allows servicing 12 thin clients, each subsequent 1 GB - 16 thin clients. 4 GB of RAM, respectively, allows us to provide comfortable work for 50 or more thin clients.
HDD. 25 GB disk space required for OS and applications. It is enough for each user to allocate 100 MB.
2.3 Advantages and disadvantages of using "thin clients" in the network
No moving parts. The more moving parts, the more likely one of them will break. Thin clients do not have any moving parts, so each device has a normal lifespan of 8 years.
Ease of service. Thin clients require a minimum of administrative attention. There is practically nothing to tune in them, and there is nothing to break, even physically. All settings are made on the server. You only need to visit the premises in which the thin clients are manufactured in order to check the condition of mice, keyboards and peripherals.
High administration efficiency. The system administrator, without leaving his workplace, can configure all the necessary security policies, clearly and unambiguously differentiate the rights of various user groups. You don't have to go through all computers, setting up something on each of them. Thin clients allow you to centrally solve security problems and differentiate access rights for various categories of users. This significantly increases the efficiency of administration.
100% safety of information during work. The thin client only displays information and processes user actions. All information is on the server. And if, for some reason, the terminal client session is suddenly terminated, the information will remain in its place. At the next connection, the user will see the document with which he worked before the accident, and in the form in which the document was at the time of the accident. Not a single byte will be lost. Moreover, it does not matter where the accident occurs - in the cable, at the level of network switching equipment or the thinnest client. The information will be saved on the server. By the way, another consequence is that thin clients do not need an uninterruptible power supply. Power outages for thin clients do not result in the loss of information or the failure of the devices themselves. Centralized data storage simplifies backup procedures and guarantees data recovery.
Ultra-low power consumption. A "cold" processor, no fans and other motors, hard drives and drives, flash memory with negligible power consumption - all this, a thin client consumes extremely little power compared to a conventional PC. The difference can be tenfold. In other words, 1 regular, traditional PC consumes as much power as a hundred thin clients.
All the functionality you need. Thin clients are equipped with USB ports, which allows you to connect the necessary peripherals to them. And the "network" nature of thin clients makes it easy to use the network printers present on the network. And, of course, any storage medium (or device for working with them) can be easily connected to the thin client via the USB interface. It should also be noted the possibility remote access to the "workplace".
Ease of expanding the information system. Thin clients make it easy, with minimal effort and time, to expand the information system, increasing the number of jobs. For a thin client to start fully functioning, two sockets are required: an electrical outlet and a local network. No need to install OS, no need to install drivers, no need to install and configure software. You just need to connect the thin client to two outlets. And the growth of the thin client network itself is limited only by the capabilities of the server subsystem, which is easily expandable.
Low ownership risks. An ordinary computer can be stolen - the system unit can be easily taken out, especially since standard cases are not equipped with any anti-theft protection elements. Stealing thin clients is stupid and pointless.
High economic efficiency. Statistics are stubborn things. She says that up to 77% of the cost of ownership of a product are those costs that enterprises incur after purchasing the product. This includes costs for: maintenance, repairs, spare parts, product downtime, management, etc. And only 23% of the cost of ownership of a product is the cost of purchasing it. At the same time, thin clients are cheaper than PCs and provide the lowest cost of ownership. They do not require the purchase of an operating system license, its cost is already included in the price of the device, and the cost of TC CAL (client license for access to a terminal server) is almost 2 times lower than the cost of Windows XP Pro OEM OS for PCs. Thin clients will last 2 - 4 times longer, require a minimum of attention from service personnel, and greatly facilitate the administration and maintenance of the information system. Finally, thin clients minimize the risks of information loss due to various accidents, minimize power consumption, their use significantly reduces the noise level in the room, and the risk of theft of such devices tends to zero.
High-speed performance. When working in a "normal" office network with the 1C: Enterprise program and other databases, a large amount of information is transmitted over the network, which causes a slowdown in the execution of programs in proportion to the number of jobs. In a terminal network, all programs are executed on the server, and only the screen view is transmitted over the network. The network traffic will be minimal, there will be no slowdown in program execution even with a large number of workstations.
Disadvantages of building a network based on thin clients. One of the main ones is the increased requirements for the performance and reliability of the terminal server, since its failure leads to the inoperability of the entire network.
This problem is solved by using multiple servers and load balancing between them. Also in the technology "thin client" resource-intensive applications for working with graphics and three-dimensional modeling, such as Photoshop, AutoCAD, 3D Studio Max, are not applicable. For these tasks, you will have to use specialized powerful workstations. Videoconferencing is becoming very problematic, but latest version Citrix MetaFrame Presentation Server has special tools to overcome this problem, although this technology is very expensive
2.4 Comparative characteristics of network design options
The results of comparing some factors of building networks based on thin clients with a traditional solution based on standard PCs are presented in Table. 2.1. This table summarizes the benefits of using thin client technology to build a corporate infrastructure compared to standard personal PCs.
Table 2.1 - Benefits of using thin client technology
|
Factor description |
Thin clients |
Personal computers |
|
Administration |
Centralized with free bundled software; easy problem diagnosis |
Decentralized, requires additional management tools, takes more time and resources; complex diagnostics of failures due to a more complex design |
|
Data and computer security |
Very high because applications are executed on the server, the inability to change them by users, theft of the device does not lead to data loss; simple backup (on the server) |
Low due to the abundance additional programs, the complexity of their interaction and mutual influence |
|
User errors |
Restricted to the applications that users work with |
The high level is due to the multitude and complexity installed applications |
|
Fleet renewal cycle (budget) | ||
|
Reliability and maintainability |
Higher due to the absence of rotating parts, as well as more comfortable thermal operation of the components; there is no need to maintain a spare parts warehouse |
Less high (most often fans, HDD, power supplies fail). It grows with increasing temperature. A warehouse of spare parts is required for repair. |
|
Noise level |
About 20 dB |
|
|
Power consumption (savings in electricity bills and the need to use UPS) | ||
|
Dimensions |
1/4 PC area<1/15 объема ПК | |
|
The need and cost of upgrading as the software grows |
Low, because upgrade is performed on the server |
High, requires upgrade of the entire PC fleet |
|
Ease of implementation |
Installation and connection: 10 minutes |
30 minutes to 2-3 hours |
|
Total cost of ownership during the operation of the TCO (5 years) |
60-70% less than a PC (in some cases up to 80% reduction in total costs) |
The cost of maintaining and operating an information system is 77% of the total cost of ownership of a product such as an information system. Naturally, this is an average and can be significantly reduced. By what means?
First of all, let's pay attention to the service life of the equipment. Since there are no moving parts in thin clients, the probability of failure tends to zero, and the estimated service life is considered to be a time period of 8-10 years. After this period, thin clients do not break at all, by the way, they simply become obsolete. The service life of ordinary personal computers is much shorter, and the problem of their obsolescence arises after 3 years. In addition, it must be understood that the life of a PC depends greatly on the quality of the components used and the quality of preventive maintenance. Moreover, the lack of such maintenance significantly increases the likelihood of early failure of computers. And its presence in full can significantly extend the life of a PC. However, the cost of such service is quite high and significantly increases the total cost of ownership of an organization's information system. Note that the cost of annual support of an information system using thin clients is 80% less than the cost of supporting an IT infrastructure built using standard PCs.
Let's analyze the cost of maintaining an information system. Serving thin clients is reduced to replacing external power supplies, keyboards and mice in case of failure. Everything. You don't need to do anything else in the workplace. When servicing a PC fleet, everything is much more complicated. Firstly, it is necessary to carry out regular maintenance of each system unit, removing accumulated dust and dirt, lubricating the fan on the processor. Secondly, after three years of operation, the cost of replacing parts that have failed, that is, the cost of repair, increases significantly. Third, the larger the PC fleet, the more qualified technicians are needed for maintenance. Of course, the staff need not be increased, but then the IT department at some point in time will have to concentrate exclusively on PC maintenance and will cease to fulfill its main role. The key function of IT specialists in any organization is to optimize work processes by introducing information technologies and, in the future, to increase the efficiency of work processes by improving the information system of an enterprise or organization. Setting before IT specialists exclusively the task of maintaining the existing information system of the organization is an extremely dangerous decision, since without the development of the information system today it is impossible to develop an organization or improve its work processes.
An important place in the network is the cost of administration. In the case of using personal computers at workplaces, the cost of administration is quite high. Why? IT infrastructure is usually built gradually. As a result, different workplaces have PCs with different configurations. As a result, each PC requires some attention from the system administrator. And when it comes to a computer park exceeding at least 50 units, the organization starts to experience problems. A sysadmin who is able to effectively set up a large number of PCs is expensive. Of course, in some places where information technology is not a core subject, there are examples of courageous and effective struggle of IT departments with the problems that a regular PC brings them. However, in commercial organizations, courageous and effective struggle against problems is possible only if there is sufficient motivation (usually financial), which means that you will have to pay significant money to each system administrator. Or - to lose thousands of dollars every day due to downtime, failures, breakdowns and "glitches", as happens in companies that save on normal system administrators, preferring "enikeys" to them. Tonic clients enable significantly fewer system administrators to be deployed by deploying a turnkey management solution - Altiris deployment solution. Yes, these administrators should be experts in their field, but the information system will perfectly perform its tasks, and they will have enough resources to work on improving its efficiency.
And the last one is power consumption. The power consumption of an average modern computer is over 150 watts. Power is consumed by a powerful processor and a cooling fan. The hard disk, optical drive, memory, modern chipsets, fans in the power supply unit, on the north bridge and in the case actively consume energy. The video subsystem consumes noticeably energy, even if it is built into the chipset. At the same time, the power consumption of the thin client averages 15 W * h. There are slightly more "gluttonous" models, there are less "gluttonous" models, however, in general, the difference in power consumption is very, very noticeable. It is easy to calculate that when using thin clients, energy savings will amount to about 135 W * h per 1 workplace. If the organization has 100 workplaces, then the transfer of the information system to thin clients will provide savings of 13.5 kWh per hour. It is enough to multiply this figure by the number of working hours per day to get the amount of daily savings. For example, if the computer park is 300 PCs, then the transfer of the information system to thin clients will save 40.5 kWh of electricity per hour. With an 8 hour working day, the savings in just one day will be 324 kWh.
All of the above allows us to conclude that the introduction of networks based on thin client technology is essential.