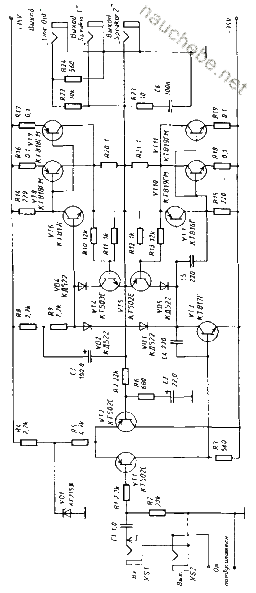
- Tutorial
Good day to all. I would like to talk about installing and configuring Windows Server 2012 R2 Essentials. This article is not a call for a ubiquitous installation of Windows or the promotion of Microsoft products. I would just like to talk about an interesting product and maybe someone will be interested in and useful in this product. I tried to write an article for an unprepared reader, so a minimum of terminology and a maximum of generalization of some concepts.
A little bit about the editions of Essentials
Windows Server 2012 R2 Essentials is one of the editions of the server operating system from Microsoft. However, it has many differences from Standard and Datacenter editions. What Essentials can do:- Authorization and authentication of users of your network (domain controller Active Directory)
- File storage (file server role)
- Remote access to the corporate network (VPN and DirectAccess server)
- Remote access to file storage via the Web interface (configured for this IIS)
- Remote access to desktops of client machines (Remote Desktop Gateway)
- Backing up client machines (windows backup)
- Backing up the server itself (windows backup)
- Integration with Microsoft cloud technologies (Office 365, Azure backup, etc.)
- Essentials Unified Configuration Console, which allows you to configure the features described above to even an unprepared system administrator.
Thus, Essentials is very suitable for small organizations that would like to use most of the modern solutions for securing the corporate network, document storage, remote access, possibly mail systems. For those organizations that would not like to spend a lot of money both on the IT infrastructure itself and on the work of highly qualified system administrators.
Installation and initial setup
Installing this OS is a fairly standard procedure. If you have ever installed Windows Vista /7/8/8.1, then you can install Essentials without any problems. However, if you have not installed either of the above OSs or any of the latest server OS versions, then I recommend either trusting a professional or at least a sophomore student.The only thing I would recommend at the time of installation, if you have one hard drive, split it into two partitions. Those. make sure that after installation the system has a second already formatted hard drive. Of course, this is only a recommendation, you can prepare a second disk in the future, however, you will have to transfer some folders.
After the first login to the freshly installed OS, the “Configure Windows Server Essentials” wizard will start, which will help you to perform the initial setup.
In the first step, you need to set the date and time settings.

In the second step, you need to fill in the company name in English. In this case, the domain name and server name will be generated automatically, although of course you can change them.

In the next step, you need to fill in the administrator name and set his password.

At the last step, you need to specify how to update the operating system and click configure

After that, a process will start that will make all the necessary initial settings. It takes about 30 minutes and will require several reboots. During this time, the OS will in particular be able to install the necessary roles and configure the server as a controller domain for the new domain.

Customization
The product is very large and extensive, I would like to talk about the most basic configuration options, such as creating users, setting up remote access, creating folders, connecting clients.All configuration takes place in the dashboard, access to it is from the desktop, quick launch panel and start screen.

User Creation
When you start this panel for the first time, the installation tab opens, on which you can perform a number of server configuration tasks.I will start by adding users. Click the link to add accounts.


Choose the level of access to the shared folders that were created. At the initial stage, there is only one - the Organization. In the future, you can change access permissions from both user properties and folder properties.


The account has been created. Click close.

Similarly, you can create many accounts. Of course, you can use the familiar and familiar interface of Active Directory Users and Computers, but in this case you will have to issue access permissions with pens.
Adding Server Folders
To add folders, there is another wizard that will help you create a folder on the disk, set up shared access for it, and issue permissions. To start it, click the corresponding link in the dashboard.
In the wizard that opens, enter a name. You can change the location and add a description. Click on.

On the next page we indicate the necessary permissions. If necessary, make it inaccessible with remote access.

From the last step of this wizard, you can start the backup configuration wizard. Click close.

Configure Remote Access
One of the most difficult stages of configuring Windows Server 2012R2 Essentials. Setup also happens using the wizard. The wizard traditionally starts from the dashboard.
The first thing you need to configure is your router - the wizard informs you about this. In fact, you need to configure port forwarding on the router. To do this, the router must have a “white” IP address. And on the server itself it is better to configure a static IP address. You need to forward the following ports 80, 443, 1723, 987 to the IP address of your server. In general, the wizard itself can also perform the configuration procedure if your router supports UPnP. I did the tuning with pens, so I skipped this step.

After that, a new domain name setup wizard opens. Click on.

The wizard prompts you to enter the name of an external domain or create a new one. For your own domain, you will need a certificate, so here we will consider the configuration option using the Microsoft domain. Select a different domain name and click on.

Consider the Microsoft domain option.



Enter the domain name and check the availability, click configure.

Well, that sorted out the domain name. We continue - further.

We choose which features will be available.

Choose whether remote access will be available for current users.

Well, that’s all you can try to go to wiseguy.remoteweaccess.com.

From this web site there is the ability to access shared folders and access to users' desktops.
Workstation connection
If this time we open the dashboard and go to the computer connection page, we’ll only see instructions for action there
Following the instructions on the client in the browser, open the page http: //<Имя сервера>/ connect. Click the download link.

We choose to execute.
We accept the license and wait.

Enter the username and password of the user of this computer or administrator. I entered the user account.

Reboot the server.

We choose who will use the computer.

Enter a description of the computer.

Archiving Options.

Hooray! Done.

We go to the computer under the user account.

You can work. The desktop already has all the necessary shortcuts.

Post scriptum
Of course, Windows Server 2012R2 Essentials is not a panacea. Automated a lot, but not all. However, for small organizations, this is a very interesting solution and needs to be considered. In this article, I talked only about the most basic Essentials settings. If you want to get a little closer acquainted with the product, you can see my video reports on Techdays.ru.Windows Server 2012 R2 Essentials first look: www.techdays.ru/videos/7351.html - here you can carefully study the installation process of Essentials.
Windows Server 2012 R2 Essentials setup: www.techdays.ru/videos/7370.html - configuration of all features is considered, the configuration of remote access for your domain is shown.
Windows Server 2012 R2 Essentials Office 365 Integration: www.techdays.ru/videos/7380.html - Microsoft Cloud Office Integration.
Our company is professionally engaged in setting up servers and server systems. The specialists of our company have vast experience in this field, as well as all the necessary certificates, they will help you choose the equipment, as well as hold a consultation on software.
We configure a wide variety of servers, among the main ones we can distinguish:
Installation and configuration of the server is based on Windows Server. Using a domain controller in a computer system will allow:
- provide centralized management of user stations and other resources;
- differentiate user rights;
- delimit access to information;
- provide the ability to interact with remote systems;
- use centralized anti-virus protection systems;
- implement centralized backup configuration.
- server Tuning
Internet server setup
The Internet server includes many services such as www, ftp server, ssh access, firewall, netbios, samba, databases, vpn server and vpn access, mail and much more. In the first place, we put a safe and uninterrupted mode of operation of services, which ensures round-the-clock access to services.
 Configuring a proxy server (proxy)
Configuring a proxy server (proxy)
Proxy server is a service in computer networks that allows clients to perform indirect requests to other network services. First, the client connects to the proxy and requests a resource (for example, a file) located on another server. Then the proxy either connects to the specified computer and receives the resource from it, or returns the resource from its own cache (in cases where the proxy has its own cache). In some cases, a client request or server response may be modified by the proxy server for certain purposes.
Direct access to FTP sites allows the user to work with files and folders stored on the FTP server in the same way as with files and folders on his computer. Files and folders can be viewed, downloaded, transferred, renamed, deleted. If permission is required to complete all of these operations, a user name and password request will appear.
Each administrator understands the importance of timely updates, especially when it comes to critical security updates. However, with the growth of the network and the increase in the number of software products, this becomes a very difficult task. So it's time to deploy WSUS (Windows Server Update Services) - a local update server on your local network.
Setting up a mail server (mail)
Own mail server allows our customers not to depend on the company that provides mail hosting, and significantly save Internet traffic. When using your own mail server, it becomes possible to completely control the flow of letters, to ensure uninterrupted and reliable management of mail resources.
VPN server setup
For remote users, you can configure remote access to private network resources on the server through a dial-up connection or a vpn connection. This is a vpn server setup. VPN provides the ability to translate network addresses (NAT). For computers, you can open Internet access through a shared Internet connection using NAT. Using a virtual private network and NAT, VPN clients can determine the IP addresses of computers on a private network, but not on the Internet.
Traffic accounting and control system
The traffic accounting and control package allows you to add and delete users, set users a traffic limit, and view traffic statistics in real time and for specified periods. The installed software reduces Internet costs due to system control over the traffic consumption, and also does not allow an infected computer to significantly increase Internet costs due to the triggering of traffic limits.
 Backup system
Backup system
Acronis True Image software is configured on all servers to back up system partitions of servers and all important data storages. Copying occurs once a day. In the event of a software or hardware failure, the system allows you to restore the servers and restore the loss of important data in the shortest time (5-30 minutes). Data can be restored on any day in the past week.
Setting up a Linux server, Windows server
The Internet and LAN (local area networks) have for many years been a mandatory attribute of any medium and large, and sometimes even small business. This is explained primarily by the unique capabilities of its coordination between the individual subjects of its components. So, there is no faster way to send / receive information than to resort to using the Internet or, in some cases, private networks with limited access rights.
 Antivirus complex
Antivirus complex
Antivirus complex - a set of antiviruses that use the same antivirus kernel or kernels, designed to solve practical problems of ensuring the antivirus security of computer systems. The anti-virus complex also includes mandatory tools for updating anti-virus databases.
Every local network, as a rule, contains two types of computers - workstations, which people are directly sitting at, and network servers used for business purposes. In accordance with the nature of the functions performed by the server are divided into:
— Networkthat provide a centralized storage of information: file servers, application servers and others
— Postagerunning a program that serves to transfer electronic messages from one computer to another
— Gatewaysresponsible for transferring information from one network to another. For example, a gateway is needed to connect a local network to the Internet. Therefore, there are four types of anti-virus systems - to protect workstations, file servers, mail systems and gateways.
Workstations - These are computers on the local network for which users directly work. The main task of the complex for protecting workstations is to ensure safe operation on the computer in question - this requires real-time verification, on-demand verification and local email verification.
Network server - These are computers specially designated for storing or processing information. They are usually not used to work directly behind them, and therefore, unlike workstations, checking e-mail for viruses is not needed here. Therefore, the anti-virus complex for file servers must perform real-time and on-demand scans.
File Server Deployment
Installation setting up a file server allows you to organize ordered storage and work with data, as well as to differentiate access rights for users. Due to this, it becomes possible to configure a centralized backup of important data.
 Our company provides technical support and server maintenance.
Our company provides technical support and server maintenance.
Need to install and configure your operating system and software?
Or maybe your project can’t cope with the load and you want to optimize the system?
We install Linux, FreeBSD, OpenBSD, OpenSolaris, Windows operating systems. We configure and optimize the MySQL, PostgreSQL, MSSQL DBMSs and the Nginx, Apache, Tomcat, Mongrel web applications. We know how to do it right.
If the computer is equipped with an Ethernet network card, then after setting it up (see section 2.4.3.3), a special system folder appears on the desktop network. By opening it with a double click, we get the window shown in Fig. 12. Trying to open the icon Whole networkin this window, we get the result shown in Fig. 13. This suggests that there is no access to the local network and the reason for this is most likely that the workstation is not configured to work on the network.
The network setup procedure is as follows.
· Right-click on the folder networkcall the context menu and select a command The properties Another way: Start - Programs - Settings - Control Panel - Network.;
 |
· In the window that opens Network(fig. 14) on the tab Configuration Check which devices and protocols are installed on this workstation. If the computer from network devices has only a network card. If the computer is equipped with a modem, the window may contain additional lines for remote access, but it is preferable to configure remote access in a different way (see below)., Then the tab should contain one line corresponding to this device , one line corresponding to the TCP / IP protocol, and one line corresponding to the client program for working on a Microsoft network. In addition, the line may be contained here: Microsoft Network File and Printer Sharing Service. If this line is not present, then press the button Access to files and printers and in the window that opens (Fig. 15), checkboxes are set to ensure that the files and printers of this workstation are accessible to other computers on the network;
· To configure network addresses allocated network administrator highlight the line TCP / IPand press the button The properties. In the window that opens TCP / IP Properties (Fig. 16) there are several tabs. If this network does not have a DHCP server that automatically assigns addresses to workstations, then on the tab IP address (Fig. 16) fill in the IP address and subnet mask fields. If the addresses in the network are allocated automatically, you must install the appropriate selector;
 |
 |
· On the tab Gateway(Fig. 17) fill in the address field of the server acting as a gateway and press the button Add There can be several gateways .;
· On the tab DNS configuration (fig. 18) include a selector Enable DNS, record the names of the workstation and domain recognized by the DNS server, as well as the IP address of the DNS server DNS servers can also be more than one. and close the window TCP / IP Properties;
· On the tab Identificationwindow Network(fig. 19) fill in the fields Computer name, Working group and Description of the computer. Computer name - This is the network name of the computer, that is, the name under which this workstation will be visible on the network. Working group - This is an association of workstations belonging to one unit of the organization. Computer description - This is a comment that will allow you to determine the affiliation of the workstation if the network name is not sufficiently informative;
Workstation setup
In order to join workstations to the domain, you must do the following:
We go into the properties of the computer on the tab "Computer Name" and click the "Change" button. In this window, specify the new computer name (if necessary) and the visan.local domain.
After that, you will need to specify the name and password of an account with rights to join the domain.
And if everything is specified correctly, then we will see the next window in which there will be an inscription “Welcome to the visan.local domain”. Then you will need to restart the computer.
After restarting the computer, when you enter Windows, you will need to specify the username and password of the user that we created earlier in Active Directory. This completes the configuration of connecting the workstation to the domain. The same thing needs to be done with the rest of the workstations.
Internet access setup
After the modem is physically connected to the central hub of our LAN via Ethernet and to the telephone line according to the ADSL standard, it is necessary to configure it.
To do this, follow these steps:
1. Launch a web browser and in the address bar type the IP address of the modem (default is 192.168.1.1), after which we should see a window with a prompt to enter a password.
2. After entering the password, we will be taken to the main page of the modem web configurator.
3. After going to the Network - LAN page, on the IP, DHCP Setup, Client List tabs, configure the modem IP address and subnet mask; install a DHCP server (the initial IP address for the DHCP server and the number of IP addresses to be distributed); add a list of clients (indicating the IP and MAC addresses of the network card).
5. Then we configure the firewall on the page Security - Firewall - General. Allow (permit), prohibit (drop), or do reject (reject) to transmit packets. In this case, the reject property allows you to configure the rules for transmitting packets over TCP / IP protocols for each user individually.
At this stage, the modem setup is completed. Now, in order to make sure that the modem is configured correctly and its firewall is working, we ask the provider to attack our IP address. Our modem successfully reflects the attack (port scan), and we can assume that the LAN is secured from intrusions from outside.
LAN Internet access through a proxy server
Proxy server (from the English proxy - “representative, authorized”) - a service on computer networks that allows clients to perform indirect requests to other network services. First, the client connects to the proxy server and requests a resource (for example, a file) located on another server. Then the proxy server either connects to the specified server and receives the resource from it, or returns the resource from its own cache. In some cases, a client request or server response may be modified by the proxy server for certain purposes. Also, the proxy server allows you to protect the client computer from powerful network attacks.
Proxy servers are used for the following purposes:
· Providing access from computers on the local network to the Internet.
· Data caching: if access to the same external resources is often done, you can keep a copy of it on the proxy server and issue it on request, thereby reducing the load on the channel to the external network and speeding up the client receiving the requested information.
· Data compression: the proxy server downloads information from the Internet and transfers the information to the end user in a compressed form. Such proxies are mainly used to save external traffic.
· Protection of the local network from external access: for example, you can configure the proxy server so that local computers will access external resources only through it, and external computers will not be able to access local resources at all (they only see the proxy server).
· Restricting access from the local network to the external: for example, you can restrict access to certain websites, restrict the use of the Internet to some local users, set quotas for traffic or bandwidth, and filter ads and viruses.
· Anonymization of access to various resources.
So, you have successfully installed the Windows Server 2003 operating system on your computer (you can read about the installation process). There is an exciting setup process ahead that you can easily complete with this illustrated guide. Of course, you are free to choose the order of the indicated procedures yourself, but here they are given in the optimal sequence that allows you to achieve your goal in the shortest possible way. Let's get started.
First of all, turn off the password request when logging in. In the "Start" menu, select "Run" and enter the control userpasswords2 command:

The "User Accounts" dialog will appear, in which you need to uncheck "Require username and password":

After clicking OK, the system will ask for the current (valid) password.
The Windows 2003 security policy provides for control of machine reboots and shutdowns. In everyday life, this is unnecessary, so let's turn off this feature. In the above way, we give the gpedit.msc command:

The MMC console opens, in which you need to find the option, "Display the event tracking dialog" ,. Look at the screenshot where to look for it:

It needs to be given a state of "Disabled."

You will not be able to just use additional drives, such as USB flash drives. They need to force the free letters from ", Disk Management" ,. However, you can enable automatic volume mounting. We type diskpart

a command line will open, in which you should type automount enable:
After pressing Enter, a confirmation message appears.

The automount parameter first appeared in Windows Server 2003. Do not try to set it in Windows XP, nothing will come of it.
For convenience, you can disable driver signature verification. This is done from the "System Properties" dialog, which can be called up using the WIN + Break keyboard shortcut

Deactivation of the check is carried out by selecting the corresponding item and pressing OK.

It should be remembered that this action carries a certain risk, which could entail unstable operation of the equipment.
If you have an expensive or slow Internet connection, it would be wise to opt out of Windows Update services.

Select "Never use Windows Update to search for drivers," and click OK.


After clicking on the "Options" button, we get to "Performance Options", where on the tab "Visual Effects", you can customize the appearance. Experience has shown that engaging the items, “Using typical tasks for folders,”
", Casting shadows of desktop icons", ", Display the contents of the window when dragging", and "Displaying a transparent rectangle when selected" creates additional comfort during work without causing a noticeable decrease in performance.

After clicking on the "Apply" button, go to the "Advanced" tab, where the main parameters for managing performance are located.

In the section "CPU time allocation", a choice should be made in favor of programs. For the section "Using memory", not everything is so simple. Systems with a small amount of RAM are shown to optimize the operation of programs. If the memory is 512 MB or more, it may be worth optimizing the system cache. In this case, switching between applications will be faster.
We’ll go to the tab “Data Execution Prevention” ,. If you are experiencing problems when working with applications that cause the message "Memory cannot be read," select "Enable DEP only for main Windows programs and services,"

Using the "Error Report" function on a home computer running Windows Server 2003, to put it mildly, is doubtful ...

You can disable the function as follows:

A very different user attitude to automatic system updates. Usually, users who do not have unlimited access to the Internet turn off this feature. We also hold this opinion. ", System Properties", tab "Auto Update",

Now let's figure out the desktop and screen settings. Right-click on the desktop to call the context menu in which we select ", Properties" ,. Next, go to the "Screen" tab.

Using the ", Desktop Settings" button, we open a new dialog.

In it, we note those elements whose presence on the desktop we need.
By going to the "Screen Saver" tab, uncheck "Password protection" if you do not want to enter this same password again after several minutes of inactivity.

The "Power" button will open the energy saving settings.

In many cases, they can be skipped to owners of stationary computers, but if you have a laptop, a visit there is required.
On the ", Hibernate" tab, check the box if necessary.

After that, return to the "Advanced" tab, and uncheck the ", Ask for a password when exiting hibernation" item.

On the ", Power Schemes" tab, make the settings to suit your needs. Pressing the OK button will lead us back to the screen properties settings. We’ll go to the “Options” tab and then click on the “Advanced” button.

Attention! This is a very important part of the setup. By skipping it, you will not be able to use the computer's video card to its full potential. Open the tab "Diagnostics" and move the slider "Hardware acceleration" to the maximum.

In addition to the actual hardware acceleration, thanks to this procedure, the video card settings become available to us, you can see them later, after installing the drivers.
By default, Internet Explorer is quite aggressive. On the network server, this is justified, since the risk of virus infection and hacker attacks is reduced, but is unacceptable for everyday use. Therefore, you must remove the enhanced security configuration. From the control panel, open "Add or Remove Programs."

By clicking the "Install Windows Components" button, we get a window for selecting components. Uncheck "Internet Explorer Enhanced Security Configuration",

What's next? For many programs, the presence of some libraries that are absent initially in the system is critical. We recommend that you immediately, in order not to experience difficulties later, install the following components available for download (link):
If you want to install themes from other (not Microsoft) manufacturers, you will need the following file, which should replace the existing one:
(dll files are installed by simply copying to the% SYSTEMROOT% \\ System32 directory)
Today it is also difficult to do without the .NET Framework, so we’ll install it:

The latest version of NET.Framework 3.5 SP1 can be downloaded.
If you need support for the 4th version of NET.Framework, download it.
Now you can install the device drivers. It should be noted that not all equipment officially supports server systems, so if you encounter a message of this kind during the installation of drivers

just click the "Yes" button. As a rule, there are no problems after this.
From the "Start" menu, go to Administration, where select ", Services" ,. The corresponding snap-in opens. You need to start Windows Audio, the Image Download Service (WIA), and also, if you want to use XP themes, the Themes service. How to do this, see below:

In conclusion, you need to enable DirectX acceleration. In the dialog, "Run," type dxdiag, and then "DirectX Diagnostic Tool" opens, in which you need to go to the ", Display" tab,

Press in sequence all available acceleration enable buttons. Go to the "Sound" tab, on which set the full hardware acceleration of the audio.

Now in the Control Panel, find ", Sounds and Audio Devices" ,. Check the box "Display taskbar icon" ,.

Setup completed.
When installing programs that are not intended for server platforms, you may have some difficulties. As one of the possible solutions, you can try the NTSwitch utility, which makes changes to the system that mislead the installer. Most likely, a successful download will follow, then boot the computer in safe mode and install the program. Then put the system back into server mode. Attention! This is a violation of the license agreement! In addition, this action can lead to complete inoperability of the OS! Act at your own risk!
The solution to problems with the transfer of an already installed system to new equipment is described in the article