Only at first glance, impenetrable passwords do not contain a logical structure and look like an abracadabra. Complex passwords are such only for those who do not know the recipe for their creation. You do not need to memorize case of letters, numbers, special characters and their order. Simply select a memorable base and follow the simple tips for creating strong passwords.
Children counters
For the basis of the password we take any children's rhyme or counting. It is desirable that it was found only in your area and was not well known. And better than your own essay! Although any children's rhymes will do, the main thing is to keep the lines firmly in your head from a young age.
The password will consist of the first letters of each word. And the letter will be written in upper case, if it is the first in the sentence. Replace some letters with numbers similar in spelling (for example, “ch” to “4”, “o” to “0”, “z” to “3”). If you do not want to get confused with replacing letters with numbers, look for the count that already contains numbers. Do not forget about punctuation marks that separate words and sentences - they will be useful.
Example:
Turtle tail pursed
And ran for the hare.
It was ahead
Who does not believe - come out!
Replace the letters "h", "s" and "o" with similar numbers. The second, third and fourth lines begin with capital letters, and therefore are written in upper case. Include four punctuation marks. Of course, we write in Russian letters, but on the English keyboard layout.
17-character password ready! It may not be perfect, as it contains repeated characters, consecutive lowercase letters and numbers. But to call it a simple language certainly will not turn.
Favorite sayings
The scheme is similar to the children's counting. Only as a basis you take the phrases of thinkers, celebrities or film characters that you like and remember very much. You can somewhat complicate your life by replacing the letter “ch” not with “4”, but with “5”, for example. Confusing maneuvers do not happen much!

Example:
I learned that from me
There is a huge family:
River, field and forest,
In the field - each spikelet ...
Replace the letter "h" with "8", do not forget about upper case and punctuation.
Ze, 8evTjc ^ H, g, bk, Dg-rr ...
Slang and terminology
This implies the use of professional jargon, understandable to a very narrow number of people. These words are far more distant from an ordinary person than criminal sayings, which are widely covered on television and the streets of any city.
For example, you can use an extract from a hospital or an intricate medical definition.
Example:
Cyclopentanperhydrophenanthrene is a 28 letter term. It turns out a bit long, therefore I propose to throw out the vowels and dilute the remaining consonants with the upper register.
Memorable dates
Of course, your birthday or the day you began your family life is not the most successful basis for a password. The event must be of exceptional importance, and only you should be aware of it. For example, it could be the day when you first ate gum, fled from a lesson or broke a heel. Since the basis of the password will be the numbers, not superfluous seems to be mixing them with letters.
Example:
10.22.1983 and 06.16.2011
Replace the dots separating the day, month and year with any letter, for example, the small English “l”, which is very similar to the often used separator “/”. Between the dates, put the underscore "_". Zeros replace the letters "o".
Visual key
Use the unlock technique of your smartphone and on your keyboard. Invent any shape and “swipe” your finger along its contours.

Do not forget to go through the numbers, change the horizontal and vertical direction of motion. And show, unlike me, fantasy!
Conclusion
The proposed ways to create a memorable, but at the same time quite complex for perception from the password can be changed and combined at your discretion. It is enough to ponder your superparol once, and you can use it without fear in the presence of an outsider.
How do you choose your password?
Many do not realize how important it is. In my practice, there were many cases among my friends who, for various reasons, neglected the complexity of the password in favor of its simplicity and memorization. They came and complained to me - “Sasha, I was hacked !!!”.
Let's first decide what the password should be? From the point of view of professionals the password must contain an arbitrary set of letters, numbers and symbols that does not have any regularity. With this you can not argue, such passwords are really resistant to cracking. But agree that in everyday life normal user it does not fit, because it will be rather difficult to remember it, there are a lot of opportunities to make a mistake.
Often people choose passwords on the basis of their name, surname, patronymic, date of birth, etc. Some use the terminology of the area of life that is close to them. For example, a person working with cars may come up with a password h4 halogen lamps. You may find that this password is good. However, it is not! Modern password cracking techniques they work according to the dictionary masks and the base of words, in which the most likely terms are encountered: halogen lamps and / or halogen lamps. A similar situation with the names - they are also in the databases.
Now we know that passwords should not use dates, names, and various common terms . And here we return to where we started - passwords, consisting of a set of letters, numbers and symbols.
I will give a simple password creation algorithm.
1 step - Let's say your name is Vladimir and your family has a father, mother and little brother, their names are Andrey, Marina and Sergey, respectively. Arrange the first letters of the names in order of seniority, typing them in Latin (many Internet sites prohibit the use of Russian characters):
AMVS
2 step - let's say you were born in 1989, Andrew - in 1958, Marina - in 1961, and Sergey - in 1995. Add after each letter of their name the year of birth:
A58M61V89S95
3 step - we will bring one more parameter - work or study. Parents and you are already working, and my brother is still studying. Let us denote work by $, and study - *. We will get the following password:
A58 $ M61 $ V89 $ S95 *
4 step - use different passwords on different sites! This will prevent hacking of other services where you are registered: mail, blog, social. network, etc. To do this, simply add the first letter of the address of the site where you register. So, passwords will look like:
For the site VKontakte (vk.com) - A58 $ M61 $ V89 $ S95 * v
For Odnoklassniki site (odnoklassniki.ru) - A58 $ M61 $ V89 $ S95 * o
By following this algorithm, you will get easy to remember and at the same time really good password. You can add or change it, make extra optionsby defining characters for them.
Keep in mind only the algorithm, and you will never forget the set of characters!
MirSovetov found out that Internet users, inventing passwords for their accounts, often make the same mistakes. Let us consider in more detail what kind of protection it will be easiest for hackers to hack:
- Forward or backward sequence of numbers are considered the most common password options. The first thing that comes to mind is a person who wants to get to his personal data - is to enter in the desired field a combination of "123456 ..." or the same numbers, but in the reverse order.
- The second most popular password is the word "password", not inferior to him in prevalence and the combination of the letters "qwerty".
- Often, Internet users enter as the password the name of the service in whose account they create protection.
- Many people like to use their first name or surname, date of birth or address as a password. email. These data can be used in various combinations, to be spelled with upper case letters or supplemented with combinations of numbers, but experienced hackers can easily crack such protection if necessary.
- Instead of their data, Internet users often use the data of their relatives: husband, children, parents. In this case, the key word may be the name or date of birth of the child, the mother's maiden name, etc. Popular variants of passwords are also considered the nickname of a pet, brand or car number, the name of the hometown.
- The sequence of letters on the keyboard can also be attributed to simple and unreliable types of protection. Such sequences are very easily calculated with the help of special programs, which in just a few minutes from a variety of options will choose the right one.
- Simple words like “money”, “love”, “friendship”, “happiness” can also be considered as questionable types of personal data protection.
- Modern hacking programs have a special feature for recognizing modifications, so replacing letters in simple words with similar symbols will not help. Such a utility can easily recognize in the number 4 the letter “A” or “H”, and in the number “0” the letter “O”.
- TO simple passwords You can also include simple sentences like "I love you."
- A very common mistake of many people is to use the same passwords in different services. Any hacker, hacking one password, is not too lazy to check it on other accounts.
What should be a strong password

- The main rule is to use different passwords for all Internet accounts.
- The security word or phrase should not be associated with the user's personal data. Avoid including names, surnames, dates of birth, pet names, etc. in the password.
- It is desirable that for a stranger password looked illogical sequence of words, letters or numbers. In this case, the security combination must be logical for the user himself, otherwise he will simply forget it.
- Phone number also should not become a password.
- No one can share the password, especially to unauthorized persons. Remember that even a call from a bank or other organization with a request to provide such information in many cases is a job of fraudsters.
- Some services after registering an account send a temporary password to the email. This combination should be changed immediately after you enter the site.
- Do not store passwords in the browser or on the desktop computer.
- The security word must be long enough and contain not only letters, but also numbers and other valid characters.
- To create a password, you can use a special generator. There are quite a lot of similar programs; among popular services one can highlight such: onlinepasswordgenerator.ru, securrity.ru, sadesign.pro, genpas.net. With the help of programs, you can not only create unique passwords, but also check your own invented combinations for reliability. For this purpose, use one of the following services: blog.kaspersky.ru, parolemanager.com or earninguide.biz.
- Try not to log into your accounts with other people's computers, especially in Internet cafes or gaming clubs. In such places, you can with high probability stumble upon a spyware program that reads the sequence of keystrokes on the keyboard.
- Passwords should be changed periodically. Than more reliable protection, the less will have to do it, but even a long 12-digit combination of letters and numbers must be changed at least once every 2 years.
Ideas for creating a password

In order to come up with an original password, which will be difficult to crack, use a well-known to you counter or a short rhyme. Take the first letter of each word of such a rhyme, replace some of them with similar symbols, for example, change the letters “o” to “0”, “z” replace “3” and the letter “h” with “4”. In the password, you can use punctuation marks, if they are in the poem. For additional protection, Cyrillic letters can be written in the Latin layout.
Instead of the quatrain or the counting, any favorite adage is quite appropriate. This may be a beloved philosophical quotation, a famous movie character phrase, etc. The principle of creating a password in this case is the same as when using the counting. By the way, for greater complexity, some letters can be replaced with different numbers, but with some others. For example, instead of “h” you can write not “4”, but “8”, “5” or any other character.
As a protective word, you can use a specific term known to a narrow circle of specialists in a particular area. Technical or medical definitions, such as complex drug names, can be useful here.
The password is not recommended to register the date of birth of yourself or someone from your loved ones, but this does not mean that you can not use other memorable dates. Such a number may, for example, denote the day of the first kiss. The main thing is that the date was known only to you or to a very limited circle of people. Instead of the points separating the day, month and year, it is better to enter a symbol or letter.
To create a password can be used so-called visual key. Visually draw on the computer keyboard some simple drawing, for example, a funny face. Click on the keys that your drawing passes through.
How to save a password

Having come up with a complex and original password, the most important thing is not to forget it later. In order not to rely solely on your memory, a combination of characters can be recorded and saved in various ways:
- The easiest way is to rewrite the security word on a piece of paper and hide it in your favorite book or put it on the shelf of the closet. It is not recommended to write the password in a notebook, since attackers can steal the organizer.
- The combination of characters can be fixed in the notes. mobile phone, only the note itself cannot be signed with the word “passwords” or any similar definitions.
- The password can also be saved on the computer, only for this you will need to disguise the file well. For this you can text extension change to graphic and hide the file in the folder with pictures. To open a document, you will need to right-click on it and select a text editor from the list of programs.
Hello, dear readers of my blog!
Today I would like to tell you about how to come up with a password.
By registering on many sites, I saw that there are different requirements for passwords everywhere. Based on this, I came up with the ideal formula for creating a password. It will be almost on all sites different, but at the same time, you will remember it and will not forget! 🙂
Why is it important to use different passwords?
Before I start creating a password, I would like to say a few words about the importance of having different passwords.
One password to all sites is certainly convenient, but dangerous. After all, it can be stolen not only by administrators of sites on which you are registered, but also by hackers.
Knowing the password, they can find out some personal information, get some secret data and documents.
Having access to your mailbox, you can change or restore passwords from other sites. May correspond on your behalf. Therefore, I recommend that you take this issue seriously. In addition to creating a complex password, I advise you to change it periodically or, if possible, to connect an sms login confirmation to account. For example, as implemented vkontakte. Moreover, it is free
The list of requirements for an ideal password, which is suitable for many sites:
- Your password should consist of at least 8 characters, as I noticed that on some sites they require just such a length;
- Your password must contain at least one number;
- At least one letter of your password must be capitalized;
- Use the first 2 letters of the site name in the password (this is necessary so that the password is always different);
- Use any punctuation mark. It is not necessary, but if it is, then it is good.
Perfect password example
Suppose we need to come up with a password for the site Mail.ru.
Choose a punctuation mark, let it be - “!”.
Take the first 2 letters of the site, the first letter we make uppercase - "Ma".
There are 5 more characters left. I can advise you to use the last 2 digits of your year of birth. Suppose - "90".
3 characters left. This is your choice. You can enter your name. Suppose - "baa".
Total, we get the password - ! Ma90baa
For yandex.ru, it will be - ! Ya90baa
For rambler.ru - ! Ra90baa
For vk.com - ! Vk90baa
For skype - ! Sk90baa
It is not necessary to write in the same manner as mine. You can change the characters in places as you like, as you find it easier to remember. For example: Sk90baa !, Skbaa90 !, 90Skbaa !, 90baaSk! etc.
The number of digits in the password you can choose any, at least 5, it is up to you. Or you can add numbers to the end, and 3 letters in front of them.
Well, that's all 🙂 Now you will passwords from all your accounts and never forget them. 😎
Good luck, I hope the article was useful for you. I would be glad if you share it with friends! 🙂
Passwords everywhere: in social networks, payment systems, on your computer and phone. It’s impossible to keep so much information in your head, so many users follow the path of least resistance - they come up with one key, which is easy to remember, and then enter it at all sites where they are registered.
Such an approach to security can end badly. If the access code for VKontakte or Odnoklassniki can be lost without serious financial consequences, and therefore it is not necessary to make it difficult, then you need a password to register with the payment system or create an Apple ID so that no one except the owner has access to the data.
Password Creation Rules
Almost all sites at registration have a list of password requirements. However, these requirements are usually minimal: no less than 8 characters, cannot consist only of numbers or letters, etc. To create a truly complex password, you need to remember a few more restrictions.
- Login and password should not be the same.
- It is not recommended to use any personal information, especially if it can be obtained from social networks or other sources.
- Do not use words.
To understand the logic of these prohibitions, just look at how passwords are cracked. For example, a 5-digit key is just 100,000 combinations. Program for hacking by simply going through all the options will find a suitable combination of minutes for 2, if not less. Not a rare word for the access code. A cracker can analyze different dictionaries in different languages and find a match. The only question is how long this will take - a few minutes or a couple of hours.
Advanced PDF Password Recovery program for hacking passwords installed on a PDF document. Uses brute force, allows you to fine-tune the selection, noting the characters used in the password.
The combination of a rare word and numbers is also not suitable. The bruteforce technology allows you to search for combinations of numbers and words, so that if necessary, such a key will fall. It will last, of course, a little longer than 123456789, but if you suffer losses due to hacking, this time difference is unlikely to seem significant. To understand which password is strong and which is not very good, let's look at specific examples. Estimated hacking time is calculated using password check services, which are described below.
- Date of birth (05041992) - will be hacked in 3 milliseconds.
- Name with a little or capital letter (Segey, sergey) - will last 300-500 milliseconds, that is, less than half a second.
- Combinations of numbers and lowercase letters (1k2k3d4a9v) - about 1 day.
- Hacking a password like HDA5-MHJDa will take about 6 years.
- The combination AhRn & Mkbl363NYp will be decrypted in 16 million years.
A hacker will not work for 16 million years or even 6 years - this value only demonstrates that it is impossible to crack a password in a reasonable time.
Password generation
One thing is to know the rules, another thing is to follow them. Most users are aware that it is impossible to use an access code consisting of a date of birth or name for registration, but few people stop it. There are two problems:
- Hard to come up complex password.
- Even if you create a password containing a random set of characters, it is difficult (sometimes impossible) to remember it.
The first problem will help to handle online password generator. On the Internet you can find a large number of services offering to quickly create a complex password from letters, numbers, special characters.
Online generators work by the same principle: you specify which symbols to use, select the required number of characters and click "Generate". Services differ only in private moments. 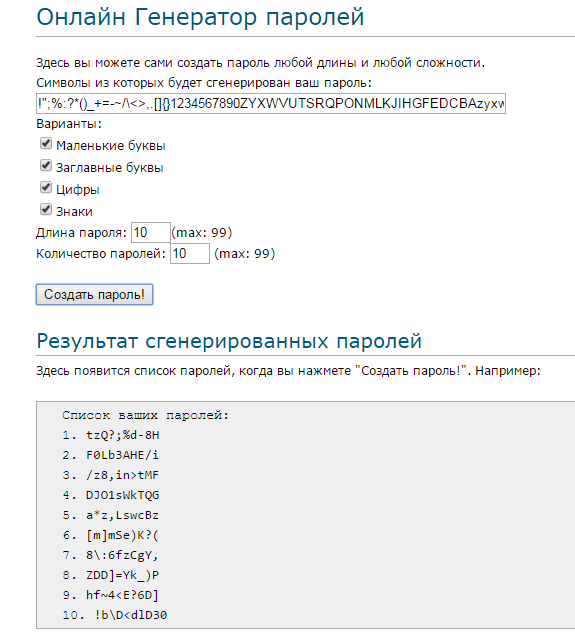
For example, on Pasw.ru you can generate several dozen passwords (up to 99 combinations) at once. PassGen allows you to set the option to automatically exclude duplicate characters from the security key, that is, all the characters in it will be in the singular.
Key storage
If you can generate a password online, then you need to store the keys on your computer. Writing a password on a piece of paper, in a separate document on a computer, on a sticker pasted on the screen is the path to unauthorized access to data. So here comes the second problem: how to remember the generated key.
You shouldn't hope for memory, but you can rely on the password manager. Many users choose KeePass. This program is free and works on Windows 7, Windows 10 and other modern versions of the OS from Microsoft. In addition, KeePass has a built-in password generator, so you don’t have to search for online services every time. 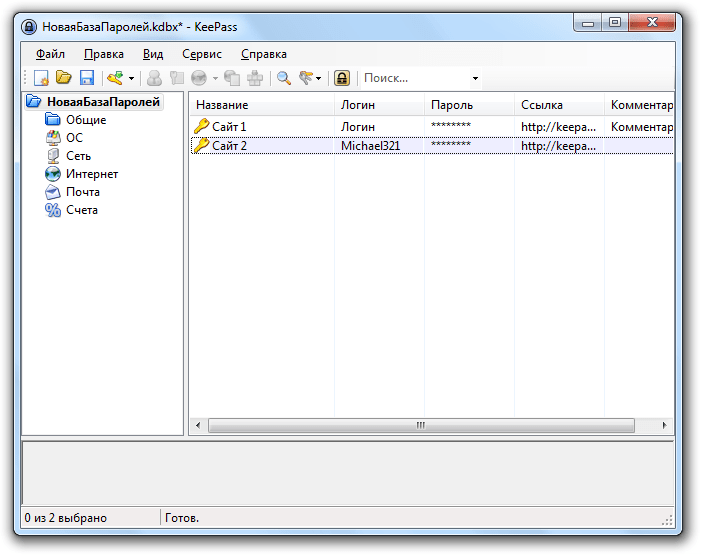
The only problem with the password manager is that it also needs an access code called the master password. But remembering one master password is much easier than keeping in mind several dozen complex combinations. In addition, when creating it, you can use cunning - take verses, notes or any other memorable lines as a basis and turn them into a combination of letters, numbers and signs. 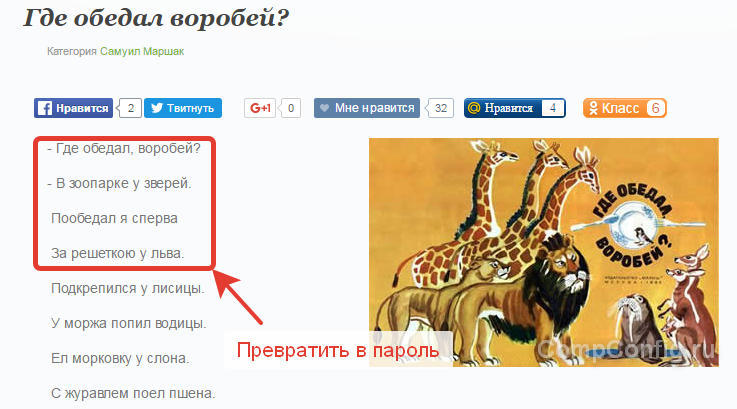
For example, you can take a quatrain, select the first letters and punctuation marks, and then write them in the Latin layout. Some letters can be replaced by numbers - “h” for “3”, “o” for “0”, “h” for “4”. As a result of this manipulation of the four lines of the children's poem, which never gets out of my head, you get the password U0d? D3ep.Gzc3hek, which takes 3 trillion years to break into.
Difficulty check
On many sites, when registering, the user is shown whether his password is good. Make sure that the generated code is complex, and hacking it quickly will not work, can you do it yourself using the service? In the field “Enter Password” insert the generated password. In response, you will receive an estimated time that will be spent on hacking the key on a regular computer. If several million or even thousands of years, the code turned out to be definitely reliable. 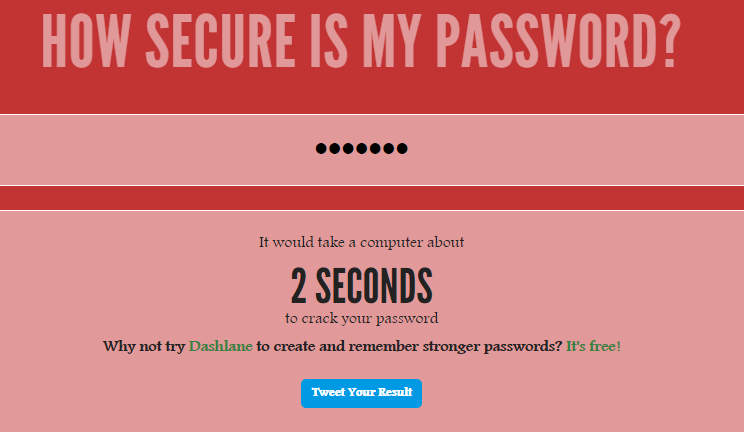
You can use other services to check the reliability: for example, from Kaspersky Lab. He also shows the time required to crack a password, at the same time telling what can be done in the specified period. ![]()
Another interesting way to check is the Password Strength service on 2ip.ru. Here the result is issued categorical: the key is either reliable or unreliable. 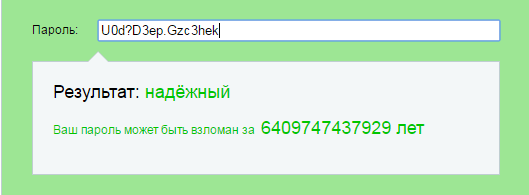
It is necessary to understand that the hacking time, which is shown by these services, is rather arbitrary and is calculated in case the hacker uses ordinary computer. A supercomputer with fantastic performance will do the job faster, just like special password cracking machines that can test up to 90 billion keys per second. But it is unlikely that people owning such a technique will need your password from email, skype or Wi-Fi.