What today can be more important than protecting your home Wi-Fi network 🙂 This is a very popular topic on which more than one article has already been written on this site. I decided to collect all the necessary information on this topic on one page. Now we will examine in detail the issue of protecting Wi-Fi networks. I’ll tell and show how to protect Wi-Fi with a password, how to do it correctly on routers of different manufacturers, which encryption method to choose, how to choose a password, and what you need to know if you plan to change the wireless password.
In this article we will talk specifically on securing your home wireless network. And about password protection only. If we consider the security of some large networks in offices, then it’s better to approach security a little differently (at least another authentication mode). If you think that one password is not enough to protect Wi-Fi networks, then I would advise you not to bother. Set a good, complex password according to this instruction, and don’t worry. It is unlikely that someone will spend time and effort to break into your network. Yes, you can, for example, hide the network name (SSID), and set up filtering by MAC address, but these are unnecessary troubles that in reality will only bring inconvenience when connecting and using a wireless network.
If you are thinking about protecting your Wi-Fi, or leaving the network open, then the only solution here is to protect. Yes, the Internet is unlimited, but almost every home has its own router, but over time, exactly someone will connect to your network. And why do we need this, because extra customers, this is an extra load on the router. And if it’s not expensive with you, then it simply cannot withstand this load. And if someone connects to your network, he will be able to access your files (if LAN is configured), and access to the settings of your router (After all, the standard password admin, which protects the control panel, you most likely did not change).
Be sure to protect your Wi-Fi network with a good password with the correct (modern) encryption method. I advise you to set up protection immediately when configuring the router. And also, it would be nice to change the password from time to time.
If you are worried that someone is hacking your network, or has already done so, just change the password and live in peace. By the way, since you will all be logged into the control panel of your router, I would also advise which one is used to enter the router settings.
Proper protection of your home Wi-Fi network: which encryption method to choose?
In the process of setting a password, you will need to choose a method for encrypting Wi-Fi networks (authentication method). I recommend installing only WPA2 - Personal, with encryption according to the algorithm AES. For a home network, this is the best solution, at the moment the newest and most reliable. This is the kind of protection that router manufacturers recommend installing.
Only under the condition that you do not have old devices that you want to connect to Wi-Fi. If after setting up some old devices you refuse to connect to the wireless network, you can set the protocol WPA (with TKIP encryption algorithm). I do not recommend installing the WEP protocol, as it is already outdated, not secure, and can be easily cracked. Yes, and there may be problems connecting new devices.
Protocol combination WPA2 - Personal with AES Encryption, this is the best option for a home network. The key itself (password) must be at least 8 characters. Password must consist of English letters, numbers and symbols. Password is case sensitive. That is, “111AA111” and “111aa111” are different passwords.
I don’t know which router you have, therefore, I’ll prepare small instructions for the most popular manufacturers.
If after changing or setting a password you have problems connecting devices to a wireless network, then see the recommendations at the end of this article.
I advise you to immediately write down the password that you will set. If you forget it, you will have to install a new one, or.
We protect Wi-Fi with a password on Tp-Link routers
We are connected to a router (via cable or Wi-Fi), launch any browser and open the address 192.168.1.1, or 192.168.0.1 (the address for your router, as well as the standard username and password are indicated on the sticker on the bottom of the device). Enter your username and password. By default, these are admin and admin. In, I described in more detail the entrance to the settings.
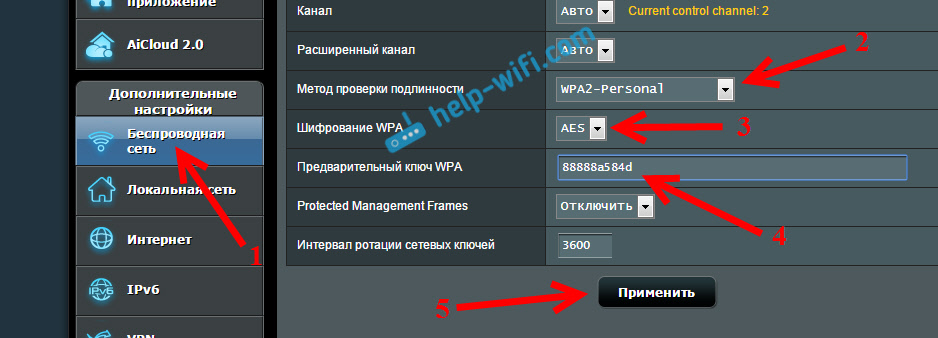
In the settings, go to the tab Wireless (Wireless) - Wireless security (Wireless Security). Place a checkmark next to the protection method WPA / WPA2 - Personal (Recommended). In the drop down menu Version (version) select WPA2-PSK. On the menu Encryption (encryption) install AES. In field Wireless password (PSK password) provide a password to protect your network.
In the settings we need to open the tab Wireless network, and make the following settings:
- In the "Authentication Method" drop-down menu, select WPA2 - Personal.
- "WPA Encryption" - install AES.
- In the field "Preliminary key WPA" write the password for our network.
To save the settings, click on the button To apply.

Connect your devices to the network already with a new password.
Protecting the wireless network of the D-Link router
Go to the settings of your D-Link router at 192.168.0.1. You can watch detailed instructions. In the settings, open the tab Wifi - Security Settings. Set the security type and password as in the screenshot below.

Setting a password on other routers
We have more detailed instructions for ZyXEL and Tenda routers. Look at the links:
If you did not find instructions for your router, then you can configure Wi-Fi network protection in the control panel of your router, in the settings section, which is called: security settings, wireless network, Wi-Fi, Wireless, etc. I think I’ll find it will not be difficult. And what settings to install, I think you already know: WPA2 - Personal and AES encryption. Well, the key.
If you can’t figure it out, ask in the comments.
What to do if devices do not connect after installation, password change?
Very often, after setting, and especially changing the password, devices that were previously connected to your network do not want to connect to it. On computers, this is usually an error "Network settings stored on this computer do not meet the requirements of this network" and "Windows could not connect to ...". On tablets and smartphones (Android, iOS), errors like “Failed to connect to the network”, “Connected, protected”, etc. may also appear.
These problems are solved by simply removing the wireless network, and reconnecting, already with a new password. How to remove a network in Windows 7, I wrote. If you have Windows 10, then you need to "forget the network" by. On mobile devices, click on your network, hold, and select Delete.
If connection problems are observed on older devices, then set the WPA protection protocol and TKIP encryption in the router settings.
Not necessarily the neighbors steal wi-fi, but someone does it unscrupulously. And it seems that the connection speed allows you to share with your neighbors, but sometimes it drops. What needs to be done to load the network like this? At the very least, lose conscience and use someone else’s Internet without permission. But closer to the point.
The situation - you are sitting on the Internet through your wi-fi router. And suddenly the speed drops so that the pages hardly open. And this is not the first time. It is a reasonable idea that someone is stealing wi-fi. How to find out if someone is connected to my file and how to disconnect strangers.
Important! All router descriptions are not universal - we are talking about a specific TP-LINK model and may vary for other devices. If you are not confident in your actions - do not continue.
Find out if anyone is connected to wi-fi
The first way. Program. SoftPerfect WiFi Guard
This method is for those who do not want to bother too much and who will conduct diagnostics through a personal computer. To determine who connected to the router, you need SoftPerfect WiFi Guard. We find it, for example, through Google and install. The program is in Russian, it installs quickly. Minimum settings required.
In the “basic” tab of the “settings” item of the program, we find the column - “network adapter”. We select the item, in my case it is Qualcomm Atheros. Click OK. After that, in the program window, click “scan”.
The program will show all the devices that are connected to our wi-fi. If only you are connected, you will see two devices (column “Info”), which will be designated as “This computer” and “Internet gateway”. That is, your computer and the router itself.
If there are strangers, the program will show them - the devices of neighbors will be displayed in red circles. These are either neighbors or your other devices.
The second way. Router admin
This method does not require additional software. We go to the admin panel of the router. After connecting to the file network, we type the IP address of the router. As a rule, this is 192.168.1.1. On different models, the address may be different - you can specify it on the device’s case. After we enter the username / password. As a rule, this is admin / admin (you can specify on the device case).
This is where the difficulty begins. On different models of routers, the menu may be different. On my device, in the “Status” tab, we find the item “Wireless”. There is a plate with the MAC addresses of the connected devices. If you are connected one, then in this table there is only one MAC. There are other addresses - neighbors steal Wi-Fi. But it’s important - at this point you can get information about devices that are connected right now.
More information can be seen in the “Interface Setup” tab, “DHCP” item.
How to disconnect neighbors from wi-fi
We offer the easiest and most effective way to protect your Internet. Namely, we set the password. The neighbors connected to our Internet either by hacking your password, or you did not set it at all.
The algorithm may be different on different devices. In my case, in the admin panel of the router, go to the “Interface Setup” tab, the “Wireless” item. In the column “WPS Settings” we find the item “Authenticatio n Ty pe. " If it is “Disabled”, then change it to “WPA-PSK”. Then in the same tab appears the column "WPA-PSK" below. In the “Pre-Shared Key” field, enter the password - at least 8 characters. It remains only to click "save". We are reconnecting to our Wi-Fi, now we are required to enter a password.
As a rule, the password on each device (laptop, tablet, smartphone) needs to be entered only once. The device will remember it and enter it automatically.
If you forgot your wi-fi password
If you forgot the password from wi-fi, then it is impossible to restore it - it is stored in the device itself. It can only be reset. To do this, hold down the reset button for a few seconds. The settings of the router will be deleted and it will need to be configured again.
I’ll tell you a story that still continues with one Internet provider in my city. Once, going to a friend, I asked him for access to Wi-Fi. The network was saved on the smartphone. While in a different area of \u200b\u200bthe city, I suddenly discovered that I was again connected to my friend’s Wi-Fi. How is this possible? It turns out that the Internet provider set the same network name and password for all routers that were issued to subscribers when they connected. More than one year has passed, and I still have free Wi-Fi in almost every yard. The login and password for accessing the routers, by the way, are also the same. :)
Naturally, I informed a friend about a funny discovery and reconfigured his router. Are you sure that you are not in a similar situation?
The danger of unauthorized access to your Wi-Fi and router
Imagine that an attacker connected to your Wi-Fi, downloaded several gigabytes of child pornography and posted a couple of hundred extremist and other “incendiary” messages. The contract for the provision of Internet services is drawn up for you, and, accordingly, they will also ask you for a violation of the law.
Even if the connected person does not commit unlawful actions, it can download and distribute large files for days (including illegal content from torrent trackers), which will affect the speed and stability of your Internet connection. The network is full of stories with free neighborly Wi-Fi. Perhaps you, too, are that good neighbor?
The situation when an outsider knows the username and password for the router itself includes all the risks listed above, and also adds a few new ones.
For example, a joker simply changes the password to Wi-Fi and you lose access to the Internet. He can change the password for the router, and you will have to reset to the factory settings and re-configure everything (or call a specialist if there are no relevant skills) to regain control of your equipment. Also, the joker himself can perform a reset.
There is no absolute protection, but you do not need it
There are many ways to hack into networks. The probability of hacking is directly proportional to the motivation and professionalism of the hacker. If you have not made enemies and do not possess any super-valuable information, then it is unlikely that you will be deliberately and diligently cracked.
In order not to provoke casual passers-by and neighbors who are eager for a freebie, it’s enough to close elementary security holes. Having encountered the slightest resistance on the way to your router or Wi-Fi, such a person will abandon his plan or choose a less secure victim.
We bring to your attention the minimum sufficient set of actions with a Wi-Fi router, which will allow you not to become the object of evil jokes or someone’s free access point.
1. Access your Wi-Fi router
The first step is to take control of your own router. You must know:
- Router IP address
- login and password to access the settings of the router.
To find out the IP address of the router, turn the device over and look at the sticker below. There, among other information, IP will be indicated. Usually it is either 192.168.1.1 or 192.168.0.1.
Also, the address of the router is indicated in the user manual. If the box with the instructions from the router is not preserved, then Google will help to find the user manual in electronic form.
You can independently find out the address of the router from the computer.
- On Windows, press Windows + R.
- In the window that appears, type cmd and press Enter.
- In the window that appears, type ipconfig and press Enter.
- Find the line "Main Gateway". This is the address of your router.
Enter the received IP address of the router in the browser. You will see the page for entering the settings of the router.
Here you must enter the username and password that you must know. In most cases, the default username is admin, and the password is either an empty field or admin as well (the default username and password are also shown at the bottom of the router). If the router came from an Internet service provider, then call him and find out.
Without the ability to change the settings, you actually lose control of your own equipment. Even if you have to reset the router and configure everything again, it's worth it. To avoid problems with access to the router in the future, write down your username and password and store them in a safe place without access for outsiders.
2. Create a strong password to access the router
Having gained access to the router, the first thing you need to do is change the password. The interfaces of the routers vary depending on the manufacturer, the specific model and firmware version. In this matter, as well as in the following steps to improve protection, the user guide for your router will help you.
3. Create a unique name (SSID) for your Wi-Fi network
If your neighbors don’t understand anything at all in technology, then a network name like fsbwifi or virus.exe might scare them away. In fact, a unique name will help you better navigate among other access points and uniquely identify your network.
4. Create a strong password for your Wi-Fi network
By creating an access point without a password, you will actually make it public. A strong password will prevent outsiders from connecting to your wireless network.
5. Make your Wi-Fi network invisible
You will reduce the likelihood of an attack on your network if it cannot be detected without special software. Hiding the name of the access point enhances security.
6. Enable encryption
Modern routers support various methods of encrypting data transmitted over a wireless network, including WEP, WPA and WPA2. WEP is inferior in reliability, but is supported by old equipment. WPA2 is optimal in terms of reliability.
7. Disable WPS
WPS was created as a simplified way to create wireless networks, but in fact it turned out to be extremely unstable to hacking. Disable WPS in the settings of the router.
8. Enable MAC Filtering
Router settings allow you to filter access to the network by unique identifiers called MAC addresses. Each device that has a network card or network interface has its own MAC address.
You can create a list of MAC addresses of trusted devices, or block devices with specific MAC addresses from connecting.
If desired, an attacker can fake the MAC address of the device from which he is trying to connect to your network, but for an ordinary household wireless access point, this scenario is extremely unlikely.
9. Reduce the radius of the Wi-Fi signal
Routers allow you to change the signal strength, thus increasing and decreasing the range of the wireless network. Obviously, you only use Wi-Fi inside an apartment or office. By lowering the transmission power to a value when the network signal is confidently received only within the premises, on the one hand, you will make your network less noticeable to others, and on the other hand, reduce the amount of interference for neighboring Wi-Fi.
10. Update the firmware of the router
There is no perfect technology. Craftsmen find new vulnerabilities, manufacturers close them and issue "patches" for existing devices. By periodically updating the firmware of your router, you reduce the likelihood that an attacker will take advantage of flaws in old versions of software to bypass protection and access to your router and network.
11. Block remote access to the router
Even if you protect your wireless network and password entry, attackers can still access the router via the Internet. To protect the device from such outside interference, find the remote access function in the settings and disable it.
12. Firewall
Some routers have a built-in firewall - a means of protection against various network attacks. Look in the router’s security settings for a function with a name like Firewall, “Firewall” or “Firewall” and turn it on if it is present. If you see additional firewall settings, read the official instructions on how to configure them.
13. VPN
They create something like an encrypted tunnel for secure data transfer between the device and the server. This technology reduces the likelihood of identity theft and makes it difficult to find the user's location.
To use a VPN, you need to install a special client program on the gadget. Such software exists for mobile devices and computers. But some routers can also be connected to VPN services. This feature allows you to protect all gadgets in the local Wi-Fi network at once, even if they do not have special programs.
Whether your router supports VPN, you can find out in the instructions or on the manufacturer’s website. The same applies to the necessary settings.
Today, when in most homes you can catch a wireless Internet network, the question of how to put a password on wifi takes on the role of an important aspect of data security. Creating a reliable “defense line” of the home network is quite a responsible business, and has its own subtleties. Given this, it will be useful for you to adopt the knowledge and advice proposed in this article.
The topic familiarization plan will be as follows:
- First, we will reveal the main existing types of encryption in wifi networks;
- Then we will consider using a generalized example how to password protect a network.
WIFI Network Encryption
Personal information stored in the files of a computer connected to a wireless network may be available to unauthorized people. In other words, with bad intent or not, for entertainment or profit, through the network without a password, unauthorized access to all the contents of a PC can be obtained. To prevent this, various encryption methods have been developed that can protect users. Further about what they exist.
WEP
This technology (802.11 standard) was one of the first systems providing wifi network security. It provided poor protection, which is why it was often hacked by hackers in order to steal important information. The result of this was a significant slowdown in the introduction of wifi networks in companies and business organizations. The leaders did not have the slightest confidence in the confidentiality of the data transmitted via wireless communication. In addition, the system did not provide the ability to set a password.
The IEEE Institute, which organized 802.11i, a working group that began creating a new data encryption model that can protect wifi networks, took up the solution to this problem.
The result was the introduction in 2004 of WPA (Wifi Protected Access or Secure Access). The new system corrected the shortcomings of the old thanks to a combination of several technologies that could solve the problem of its vulnerability and put an end to the history of easy network hacks.
WPA
The 802.1x standard, as mentioned above, replaced 802.11. The main difference was mutual authentication and the constant encapsulation of data transmitted between the server and client access points. The authentication protocol (EAP) has also been expanded.
We suggest that you familiarize yourself with the schematic representation of the work of WAP and many other security systems (see figure)
In addition, the Temporary Key Integrity Protocol (TKIP) method and MIC, a message checksum that prevents any change in data packets during transmission, were integrated into the WAP. Working together, these technologies can guarantee the protection of the network, giving the right to connect to it only users who have a password.
WPA2
The next jerk towards network security was the release of WPA2 (802.11i). Only with its appearance, wireless networks began to actively introduce enterprises and companies that give privacy a special role.
The most important innovation was the emergence of AES - a 128-bit advanced data encryption algorithm. It allows you to put an end to the work of the “blocker” of the cipher, which makes it possible to use one code for authentication and encryption. Now it has become mandatory to use different ciphers for each of these operations. We also added key caching and pre-authentication of users (for ordering them by access points).
There are modifications to the 802.11i standard:
- 802.11r is a technology specializing in the fast and reliable transfer of key hierarchies based on the Handoff algorithm. This wifi standard is fully compatible with 802.11a / b / g / n modifications.
- 802.11w - Designed to improve the security mechanism through increased focus on protecting 802.11i-based management packets. Both of these standards belong to the 802.11n group.
Thus, the use of the latter (WPA2) standard in organizing wireless network security is obvious.
Enough theory. The next step should be the organization of wifi password protection, which we will now consider.
Password for wifi - installation nuances
A wireless network makes it possible to connect various devices to the Internet in a radius far beyond the boundaries of the apartment. Therefore, if your wifi is not password protected, neighbors will be able to take advantage of it. And it’s one thing if such an unauthorized “visit” is made just for the sake of getting free Internet, and it’s quite another if it is to get personal information for fraudulent activities.
Therefore, setting a password on wifi is a priority after creating and configuring a network.
This procedure may have slight differences when working with different models of routers. But, despite this, there is one general tuning algorithm that is applicable in all cases.
Step 1

The first operation necessary to password-protect the network is to enter the settings of the router.
Included with it is a CD, designed to facilitate equipment setup. But if you find it difficult to find it, you can use the web interface of the router. In this case, you will need to launch a web browser and enter a special code in the address bar (construction consisting of “http: //” and “IP router”). The standard addresses for most routers start with “192.168.”, And then follow: “1.1”, “0.1”, “2.1” (for example, 192.168.1.1). Which one is right for you? You can find this out by looking at the back cover of the router (for 99% of cases), or by browsing the Internet.
Consider the following:
- It’s better to go into the settings of the router from a computer connected to it using an Ethenet cable. When using wifi, you will have to repeat the login procedure every time, after any change.
- The name and password of the router is almost always “admin”. If it doesn’t work, look through the instructions for the right option, or look at the back cover of the device.
- If you find it difficult to remember the password that you managed to set earlier, reboot the router with the Reset button. This will reset all user settings of the device, returning them to the factory settings.
Step 2

Now you need to find a tab with a name similar to "Network Security Properties." It is most often found in the "Wifi settings" or in the "Security" section. Having trouble finding a tab? You can enter the model name of your router in the search and set its location.
Step 3

Next, you need to select the type of data encryption. Modern models provide for the use of various network protection methods. We talked about the features of each at the beginning of the article. And, as discussed there, it is most advisable today to use WPA2 because of its highest reliability.
- Important! On older router models, you may not be able to use WPA2. Therefore, you need to install either WPA, or change the device to a more modern one.
STEP 4
After choosing an encryption method, you must install its algorithm. For WPA2-Personal, you need to install AES. The other - TKIP - is much inferior to the first in reliability, and it is not advisable to use it.
Important! In some models of routers, TKIP is no longer even provided, since it is outdated and cannot provide the desired level of protection.
Step 5
So we have reached the most important stage of the whole procedure. You need to determine the SSID (name of the access point) and put the password on wifi (in other words, specify a code word or password protect the network).
When choosing a secret phrase, consider:
- A combination of both numbers and symbols should be the password, and it is very good if they are mixed. By complicating the secret code in this way, you can set a difficult task for ill-wishers who want to pick it up.
- The Internet is littered with many simple password generators with which they crack in a matter of seconds.
Step 6. Last

It remains only to save the new settings and reboot the router. Click on “Apply” (“save”, “save”, “apply” ...), and all changes will be ready to take effect. This will happen only after rebooting the router. In most cases, the router will start an independent reboot, and all connected devices will necessarily disconnect from wifi. In order to notify them of changes in the network, you will have to re-establish the connection and enter the new password specified in the step earlier.
Important to remember:
- If automatic reboot did not start after saving, you will need to do it manually. It is necessary to disconnect the router from the power supply, count to 10, and then turn it on again. It will be possible to get to work after it performs the initial boot. Its completion will be reported by light indicators, ceasing to flash randomly.
- Such a reboot is different from that obtained by pressing the RESET button! The latter will erase all your settings, resetting them to the initial (factory).
- To prevent network intrusions, it is recommended that you change your password at least twice a year.
Remember, you have everything you need to ensure that your personal data is not compromised. The main thing is to learn how to use wireless security methods.
Protection in Wi-Fi networks has been constantly improved since the advent of this wireless technology. Recently, it has developed so much that almost all modern routers are protected from possible attacks by strong passwords, sophisticated encryption methods, built-in firewalls and many other means of protection against intruders. But what happens if the encryption algorithms that still make Wi-Fi one of the most secure protocols turn out to be hacked?
This is exactly what happened in the fall of 2017, when Belgian researchers from Leuven University found several critical vulnerabilities in the WPA2 protocol and published a detailed report on this. The WPA2 protocol is used to protect most Wi-Fi networks in the world and is considered the most reliable security tool available for mass use.
Content
How to protect your data if Wi-Fi no longer guarantees security?
The fact that the WPA was hacked is troubling news that affects many electronic devices, but there is no reason for alarm.
In fact, the researchers found a vulnerability in the Wi-Fi protocol, which makes wireless traffic potentially accessible to attack by cybercriminals. In other words, anyone can use this flaw in network security to spy on other people's actions on the Internet, steal credit card numbers, passwords, intercept messages in instant messengers, etc.
Fortunately, manufacturers of many gadgets have already managed to improve and modify their devices, eliminating the vulnerability found. And besides, WPA2 is far from the only wall of protection between the hacker and the personal data of users.
To hack someone else’s Wi-Fi, an attacker, first, needs to position his receiving antenna within the range of the radio channel, and secondly, most of the information on the Internet is transmitted in an encrypted form, and in any case, the hacker will not be able to read it. 
The https protocol, which most web servers run on, adds an extra layer of protection to the connection, as well as the use of VPN services.
That is why you always need to remember the lock icon in the address bar of the browser. If a small padlock is not displayed there, this means that the site does not use the https protocol, and all information entered into the forms, including passwords, may be available to third parties.
That is why, before sending somewhere your home address or payment data, you always need to make sure that there is a lock in the address bar.
All the leading software developers almost immediately after the news about the vulnerability of the Wi-Fi protocol released the corresponding patches for their products. For example, Microsoft released an update for Windows in October 2017. Apple also fixed its macOS and iOS operating systems at about the same time.
Google released an update for Android in November, so each owner of devices with this platform needs to read the About section in the phone or tablet settings to find out when the last security update was. If it was running before November, and Android 6 or an earlier version of the OS is installed on the phone, then an update is necessary.
Which wireless security standard should I prefer?
Wireless routers can use a wide range of different protocols to encrypt data. Here are three basic standards that most home and office routers work with:
1. Wired Equivalent Privacy (WEP): this protocol was introduced in 1997 immediately after the development of the 802.11 Wi-Fi standard; WEP is currently considered unsafe and already since 2003 it has been replaced by WPA information security technology with the TKIP encryption method.
2. Integrity Key Temporal Key Protocol (TKIP). This standard is also obsolete and is phasing out. But unlike WEP, it can still be found in the firmware of many models of modern equipment.
3. Advanced Encryption Standard (AES). This standard was introduced immediately after TKIP in 2004, along with an updated and improved WPA2 connection certification system. Routers working with this technology should be preferred when choosing new network equipment. Wireless gadgets must also support AES in order to communicate properly with such routers. Despite the vulnerability mentioned above, WPA2 is still considered the best Wi-Fi protection method. Currently, router manufacturers and Internet service providers typically use WPA2 as a standard; some of them use a combination of WPA2 and WPA to make it possible to work with the widest range of wireless gadgets.
In the technical documentation for routers, you can also sometimes see letters PSK, which mean Pre-Shared-Key or Personal Shared Key. When there is a choice, it is always better to give preference to models with WPA2-PSK (AES) instead of WPA2-PSK (TKIP), but if some old gadgets cannot connect to the router, then you can stop at WPA2-PSK (TKIP). TKIP technology uses the advanced WPA2 encryption method, leaving older TKIP-dependent devices able to connect to wireless routers.
How to secure your Wi-Fi
Disabling WPS
WPS stands for Wi-Fi Protected Setup, a standard and protocol that was created to make wireless setup easier. Despite its practicality and functionality, this solution contains a serious flaw: an eight-digit PIN code consisting of only numbers is easy to break by primitive selection, and this creates a convenient starting point for hackers who want to take over someone else's Wi-Fi.
To find out if a wireless router uses WPS or not, you need to take a closer look at the box in which it is delivered: WPS support is indicated by the presence of a special logo on the package and a separate physical button on the device’s body. From the point of view of protection against hacking, it is better to disable this protocol and never use it.