With the development of technology, social networks are becoming more and more involved in our lives, increasingly drawing us into virtual space. But after all, we so like hours and days hanging on the Internet, talking with friends, sharing some information. Services offered by developers social networks becomes more and more, today we will tell you about one of them.
In addition, the team conducted penetration tests and found vulnerabilities in radar and missile defense systems of the country, as well as in its international telecommunications. The opportunities that he provided for national defense would, in practice, be directed against citizens.
This function has other features
He left the project and returned to the United States. He settled with several good customers, the best of which was the company, 20 miles from home. The attacker would have known that he could not steal the Company's data; for this there could be different reasons. It was important to make him think whether the hack was discovered. The redemption file was a universal ready-made module that did not have much interest or complexity. He arrived only two or three days before he was identified. The question is how he arrived. It was a hacking that really mattered.
Many users of the well-known site "Odnoklassniki.ru" probably know that the site provides a special service, which received the name "Invisible". The service is chargeable, and for different countries it has a different price. You can pay in several ways - terminal, electronic wallet, sms. To become unrecognizable, you can use the "Enable invisibility" button. After clicking it, you can find out how, where and how much you need to pay. The service is connected for 10, 20, 30, 60 or 90 days, the mode can be switched on or off indefinitely.
The scale of this is not yet clear, but the company's network has been secretly "owned" since. The system's compelling evidence that the attackers were the same team of the Chinese government that fell into the Company four years ago. And the capabilities of the Chinese team have improved significantly. The initial violation was a work of art. The Chinese wrote part of the specialized software exclusively for this work.
They knew exactly where they were going. Secondly, and more importantly, the Chinese led the network "assembly" system, part of the network in which software changes were compiled, and then uploaded to the content distribution network to download updates to customers. In this position, they acquired the ability to bind their own software packages and insert them into a regular stream, potentially reaching 70 million personal computers or more. But at the moment they did nothing. Instead, they installed three empty Trojan Trojans on three separate network computers and left them there to wait for future instructions.
How to recognize the invisibility
The most important question that worries users is how to recognize classmates in classmates. Let's find out how everything works. When accessing someone else's account in this mode, the "On Site" light does not blink under your photo, you do not appear as "Friends on the site", and instead of your photo, users can see the standard picture. From the section "Guests" such a picture is deleted after 30 days, it can disappear, if you go to someone else's profile in the usual way. Therefore, if you went to the site anonymously, and then again, but already as common user, in the category "Guests" due to the disappearance of the picture and the appearance of your photo, a person can guess who was unrecognized among visitors, especially if he has few guests. Also need to pay attention to the fact that it is impossible to go anonymously on someone else's closed account (unless, of course, you with this profile are not "Friends"). The regime also does not allow a secret visitor to visit the accounts of people, where he is on the "Black List".
"Bot" in the "botnet" comes from the "robot". Botnets are illegal networks of infected computers known as zombies or nodes that function normally, but are secretly controlled by hackers and can be used in combination to obtain huge computing power. The largest of them consisted of several million computers. They have been around for a long time. No one knows how many are active, but the figures are large. Some of them are self-propagating, but most of them require active loading.
In any case, they are multipliers of the power of the Dark Web. Some of them are commercial and offer services in the black market. At the simplest level, hackers use them to mount denial-of-service attacks, overwhelming websites with huge amounts of traffic. In addition, their goals are almost limitless: identity theft, credit card fraud, bank fraud, intelligence gathering, high-speed code split, corporate espionage, commercial sabotage and attacks on the national infrastructure, including industrial control networks, telephone systems and the Internet itself .

So, does reliable way find out who is hiding under this status? If you closed your account, and someone came to visit you anonymously, then this someone from your "Friends" list. If the account is open, you can not find out the visitor. An exception may be a situation where a person in invisible mode appeared again in your "Guest", but in the usual way. In this case, in place of the standard picture of a secret visitor, a real photograph of the "Guest" appears.
How to use invisibility in Classmates?
Botnets are so valuable and, perhaps, so short-lived that their creators usually rush to use them as soon as they are built. It was a strange part about attacking the Company. The Chinese made every effort to insert their Trojan, but stopped, not taking further measures.
What does the expression of the invisible mean?
Botnet, which he could create, would be huge. If the Chinese violated other major Internet companies through the same payment center route, and it looks like it was similar to the fact that they were merged - that would be perhaps the biggest botnet that ever saw the Internet A robot consisting of 200 million computers, all controlled by a small Chinese team of hackers. And its lack of use was key. The only possible goal, concluded by Opsek, was that the sleeping chamber, lying on hold, as a pre-deployed asset, which would be used as a last resort, as a nuclear weapon, in the case of total cyberwar.
Hello everybody! How does invisibility work in classmates? In this I will try to understand the current article. To begin with, I guess that we need to figure out what the "Invisible" is in general. Ignoramus in Odnoklassniki is a special regime. As a rule, it is needed for those who wish to visit a variety of profiles, while being incognito.
Of course, the world is moving in this direction. Already, cyber attacks are an active component of almost all conventional military battles. Some say that the global cyber war has already begun, because everyone is being hacked. But many states - China, Russia, Germany, France, Pakistan, Israel and the United States - are actively preparing for something much greater. A sleeping cell would never have been found if not for a redeemed technique that could not be deployed. When it is identified, if it has not already been, a member of the renegade team in China will face a very unhappy future.
Odnoklassniki has a system so that when viewing a certain person's account, the person who visited his page appears in the "Guests" section. If you want to be invisible, but continue to collect people and classes, then the function "Invisible" is just the way. By connecting the function, you get the ability to view absolutely any pages of accounts and, while in the "Guests" section, this person will not appear your page. You can connect it as much as you want.
Of course, the US government was informed. Yes, and they will not remove it. They watched it, conducted reconnaissance and monitoring so that they could follow them, and they would probably spend some time developing an opportunity to destroy or capture the botnet if necessary.
What is an invisible?
Right ?, he said. "Let the Chinese build their cyber weapons and think that it has it, and when we need it, we simply block it or turn it over." As Opsek himself answers, another question. Turning to a friend of equal reputation, he said: "We write a very invasive software". He said: We will find their command-control structure, the control brain for the malware that they use. We, at least, destroy their network. And, maybe, he continued, as a gift, you could give them the identity of the guy whose ransom led to hacking.
Pay attention, if you connected "Invisible" and went to the person, then you will not appear in the list of guests, but if you after a while turned off the function and went to him on a new one, the information will be declassified.
This function has other features:
- You will be offline;
- You will immediately become visible, if you perform any actions on his page - they have jumped the photo, left a record;
- Visiting pages with a closed profile is impossible;
- The service is provided for a fee and for a certain period of validity;
- If you have exceeded the limit of the service, and it was disabled, then on the pages that you visited earlier with the active service, you will also remain hidden;
- "Invisible" connects quickly.
How does invisibility work in classmates? - Turn on the "Invisible"
So, here is the following instruction:
How does the invisible man work?
They all came out of nowhere and killed many people. Nobody saw them. Their affairs give rise to many questions, few answers. In any case, the society perceives terrorist individual criminals. Even in the name of solitary wolves, the fear accompanying their killing resonates: unpredictable brutal attacks that can not be prevented, which can suddenly and unexpectedly become a victim of a victim. Three times this happened during the week, in Orlando, in the murderous attack of an Islamist on a policeman and his wife near Paris, and more recently with the murder of British parliamentary deputies in the village of Birstall near Leeds.
- First, open your profile;
- Under your main photo, find and select the "Enable Invisibility" option;
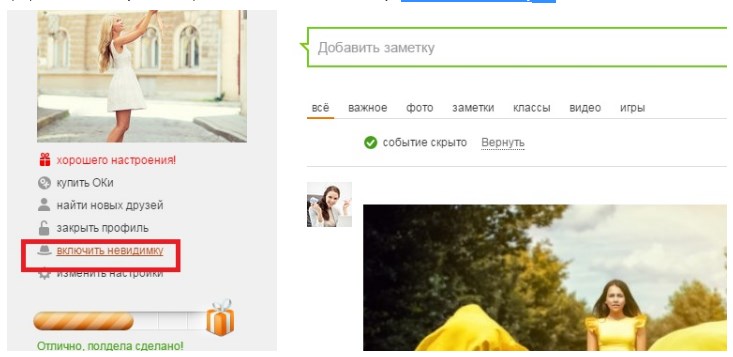
- A window for connecting the "Invisible" is displayed. The default time is 50 days. You can change it at your discretion;
- Go to payment and pay in any convenient way.
We recognize guests with the service "Invisible"
The service is provided for a fee - which means that the administration is in full control. Therefore, only with the help of logical thinking can you find out who visited the page.
It's a nightmare for all security agencies. But those who watch carefully, can also find patterns in which they can be recognized. On the surface there is no clear profile of a lone wolf. Some, like Omar Matein in Orlando, are seeking religious excuses for their murders. Others use ideological justifications and refer to terrorist groups from left to right. Some, like Anders Breivik, record their beliefs in long complex pamphlets. Others leave no words or few references to their thinking buildings.
Some of them are mentally ill and noticeable, others live unnoticed before their deeds. Some of them are in schools, shopping centers or in their workplaces, others are looking for celebrities, government buildings. Nevertheless, there are signs that are found in all criminals who plan and commit the murder of many people alone. And there are characteristics that separate individuals from those terrorists who are part of a group or organization.
If you are in the " Closed profile"And you still have an invisible guest, it means that this guest is your friend. It is not possible to recognize the invisibility when the profile is open. The hidden guest will disappear in a month.
If you are unhappy with one of your friends, and you suspect him, then, most likely, it is he. In this case, you can add it to the Black List. If a person is on the Black List, he will not be able to visit the page, even through invisibility.
Lonely, but not isolated
The most obvious common point is that these violators act alone. They are more or less pronounced singles, during their deeds as well as in the rest of their lives. Kaczynski lived alone in a homemade, remote hut without electricity and running water in Montana. But so far not everything is isolated, but not at all spatially.
How the "Invisible" option works
It is among the Islamists that social isolation does not seem very pronounced. They have friends, partners, acquaintances, colleagues. In addition, not everyone is silent about their ideas. Looking back, people from their environment often recall expressions and events that they did not take seriously before, but who after this act appear in a new light. Matein, as former classmates say, expressed, for example, his sympathy for the killers.