VPN is a feature available on iPhone, iPad and iPod touch that allows you to change the IP address of your device when you access the Internet. There are several ways to take advantage of it.
What is a VPN for
Using a VPN leads to the fact that when you access the Internet, all sites and other objects that request your IP will not receive your individual number, which contains the location from which you enter the network, but another, tied to another place or another country ...
This function can come in handy in cases where you need to go to a site that is blocked in your country, or enter any resource blocked by the settings of the Wi-Fi network through which the connection is made. VPN provides anonymity, that is, no one will know that it was from your device that a particular Internet resource was entered.
That is, if you are, for example, in Russia, then with the help of a VPN you can set such an IP for your connection, thanks to which it will be displayed everywhere that you are, for example, in Italy.
VPN use is officially prohibited in Russia.
How to use a VPN
On iPhone, iPad, and iPod touch, there are two ways to use VPN services: through the device's built-in settings or a third-party app.
Using VPN through built-in settings
To use this method, you will have to find a website that provides VPN services in advance and create an account on it.
- Expand device settings. Opening the Apple device settings
- Go to the main parameters.
 Opening the main Apple settings
Opening the main Apple settings - Select "Network".
 Go to the "Network" section
Go to the "Network" section - Select the VPN sub-item.
 Select the VPN subsection in the "Network" tab
Select the VPN subsection in the "Network" tab - Start creating a new configuration.
 Click on the button "Add configuration"
Click on the button "Add configuration" - Indicate that you want to issue PPTP protocol. Fill in all the fields: "Server" - the site that you found in advance, "Description" - can be obtained on the site, "Account" - the name of your account, RSA - leave the factory value, "Password" - the code to the account, if any , "Encryption" - absent. After filling in all the cells, save the entered data.
 Fill in empty configuration cells
Fill in empty configuration cells - Make sure the options you created are selected by default.
 Setting the default configuration
Setting the default configuration - Go back to general settings and enable VPN. If you want to interrupt the VPN connection, then click on the slider again to make the function inactive.
 Turn on VPN in device settings
Turn on VPN in device settings
Video: configuring VPN using the system
Using a VPN through a third party app
There are many VPN programs available. One of the best is Betternet, which can be installed for free from the App Store. To connect and disconnect the VPN, you need to press just one button, and the time of using the VPN is not limited. That is, you do not have to manually enter settings, create accounts or use any other additional services. It is enough to install the application, go into it and press the Connect button to connect and Disconnect to disconnect.
 Connecting or disconnecting from VPN via Betternet
Connecting or disconnecting from VPN via Betternet Also, you can independently choose which country the VPN will link you to.
 Choosing a VPN server over Betternet
Choosing a VPN server over Betternet Video: VPN setup with Betternet
What to do if the VPN icon is missing
If the device is connected to the network via VPN, then the icon in the top notification bar will correspond to this. The disappearance of this icon means that you are still connected to the Internet, but forwarding via VPN is over. That is, the VPN connection is interrupted, it can be deactivated on its own due to an unstable Internet connection or problems on the server providing VPN services. In this case, you must manually reconnect to the VPN again using one of the methods described above. The device may need to be rebooted first before reconnecting.
 VPN icon in the notification bar
VPN icon in the notification bar What to do if VPN doesn't work
A VPN connection may not work for two reasons: an unstable Internet connection or a problem with the server providing VPN services. First, check if your mobile internet or Wi-Fi connection is stable. Secondly, check the correctness of the settings entered if you used the first method described above, or install any other application other than the one described above in the second method, if you used it.
The best way to get rid of your VPN connection problem is to choose a different service or app. The main thing is to find the VPN that will work in your area.
VPN allows you to take advantage of services blocked in your area. You can use it through the Apple device settings or a third-party application.
VPN - what is it?
What is a VPN (VPN), what does it give and why is it needed? We tried to figure out how to use it and how to install it on a computer or smartphone on the Android platform.
What is VPN?
VPN is a virtual private network, literally from English, the decryption sounds like Virtual Private Network.
When you connect to the network, between you and the network itself, there is always some third, or even a fourth link.
For example, this could be your ISP, government, public access, or signal taps.

And at this time, the information that you are looking for is in the public domain for all these links, that is, it is not encrypted and not confidential.
And through the VPN server, you can directly establish a connection with the server you need.
It can be located anywhere in the world, it can be normally blocked for your region, and with the help of this server you can get direct access to it.
In the same way, as in the usual mode, your provider will see the information, but will not be able to read it, since it will be transmitted in encrypted form using the created virtual channel between your device and the desired server.
That is, in other words, during the use of VPN, a certain secret tunnel is established, through which information passes in a secret form, hidden from the eyes of the provider.
He simply won't be able to figure out which site you want to go to. The site visit history will be available only to you, and scammers will not be able to intercept your data.
There are both paid and free VPN servers... The choice depends on the nature of the tasks that you plan to perform.
- free servers for the quality of the services provided do not bear any responsibility and have a low data transfer rate. But in order to gain access to closed or restricted sites, they will be enough.
- paid servers are needed for more serious tasks. They provide complete confidentiality of information and have a very high data transfer rate. Server cost ranges from $ 2 to $ 20 per month. Payment for use is made through WebMoney, sites with cryptocurrencies or anonymously, through terminals.

It's easy to connect the server.
You just need to select one of the options, specify the country through which, in theory, the session will be carried out, connect, and disconnect at the end of the session.
VPN access on a smartphone will allow you to use the network in public places, while maintaining anonymity, and in addition, avoid data interception by system hackers.
VPN provides three main types of connection, depending on the purpose:
- from node to node;
- from node to network;
- from network to network.
Implementation levels

VPNs are often not implemented above the average tier, because the application of privacy techniques at these tiers allows the protocols to be used unchanged.
To create such a virtual connection, it is necessary to pack data into one element of the PPP protocol in any other, for example, IP, or Ethernet.
VPNs are used not only to create personal networks, but sometimes to directly access the Internet.
This server can provide the highest level of anonymity and encryption of information with the required level of use of special software, the main thing is only to correctly configure all the components.
VPN structure
A VPN is made up of two elements:
- external networkthrough which the data is packed into a single whole, and the connection occurs;
- internal network, which is controlled by the external. It may not be one, but have several more of the same controlled networks.

The connection is made using a server connected to both structure elements.
During the connection, the server requires an identity check, as well as a comparison check of the elements already in the database.
After the verification is complete, the user is given space to use the network.
Servers can be classified according to five basic criteria.

By the degree of security of the environment used:
By appointment:
By implementation method:
| Intranet VPN | Remote Access VPN | Extranet VPN | Internet VPN | Client / Server VPN |
|---|---|---|---|---|
| It unites several distributed sections of the same complex into one secure network, which can then exchange data through publicly available communication channels. | Creates a secure channel between a part of the corporate network and a private user who connects to corporate resources during home use. | It is necessary when using those networks to which users from the outside can connect, to which the level of trust is not particularly high. Access will be provided only to information that does not have strong value and anonymity. | It is needed to access the network for providers if several users are connected to the same channel at the same time. | Provides information security through site-to-site transmission on a corporate network. This protection is necessary when you need to create several subnets in an entire network, that is, a certain division of the site into sections. |
By protocol type:
There are several options for implementing servers for TCP / IP, IPX, and AppleTalk. But nowadays there is a complete transition to the TCP / IP protocol, which is supported by most VPN servers.
By network protocol level:
The network protocol degree maps to the model system / OSI layer.
What does a VPN do?
→ This server changes the IP address from which the connection is made to a fictitious one, for example Germany.
When using VPN, no one will know who it is you visited a particular site. Administrators will only see that you are from Germany;
→ The connection is encrypted. That is, neither your system administrator nor your provider will be able to find out your history of using the network;

→ Without this server, your provider has access to your entire search history, without any exceptions. And through VPN, nobody but you will know anything.
→ Hackers and crackers will not be able to intercept your data, and even if they can, they will never decrypt it;
→ By encrypting your data, your use will be completely safe and confidential.
When to connect to a VPN

- you use Wi-Fi when visiting public institutions, then when connected, no intruder will be able to intercept data about your bank card, secret codes and passwords to payment systems where your money is stored;
- you are unhappy with the fact that your entire search history is viewed by a provider who can see in which payment system your funds are stored, and you want to have complete anonymity;
- you don't want your boss to look at your search history, which shouldn't be there during business hours;
- you wish to visit sites without the restrictions of services blocking them;
- the legislation of your country restricts access to your favorite servers or if it specifies certain privileges when moving from a specific country.
In such cases, you definitely need this server.
VPN in Google Chrome

It so happens that you want to go to a certain site, but it is blocked by the decision of the legislation of your country. How does the network calculate that you are from a given country?
The thing is that your location can be calculated by the ip-address, and because of this, you get into the list of blocked users and cannot access this site.
But these locks can be bypassed by masking your address and creating a secure connection. This method will increase the degree of privacy and a VPN is required to do this.
Below we will give detailed instructions with which you can make this even easier.
1 So, open the browser Google chrome.

2 To the right of the address bar, we are looking for "Settings" and go to them.

3 We will open the settings menu, in which we need to find and select an item.

4 There we select the tab .

5 In it you will see a list of all that are already installed. To add a new one, click on the item.

6 Then the repository will be opened, in the search line of which you need to enter browsec vpn and start, directly, to the search.

7 From the list of options, select what we need and install it.

8 To combine it with the browser, you must specify "Install extension" .

9 After installing it to the right of the address bar, near "Settings" , the icon of this extension will be visible, to configure which you need to go into it.

10 To start its activity, it is necessary to switch a certain lever to the on mode.

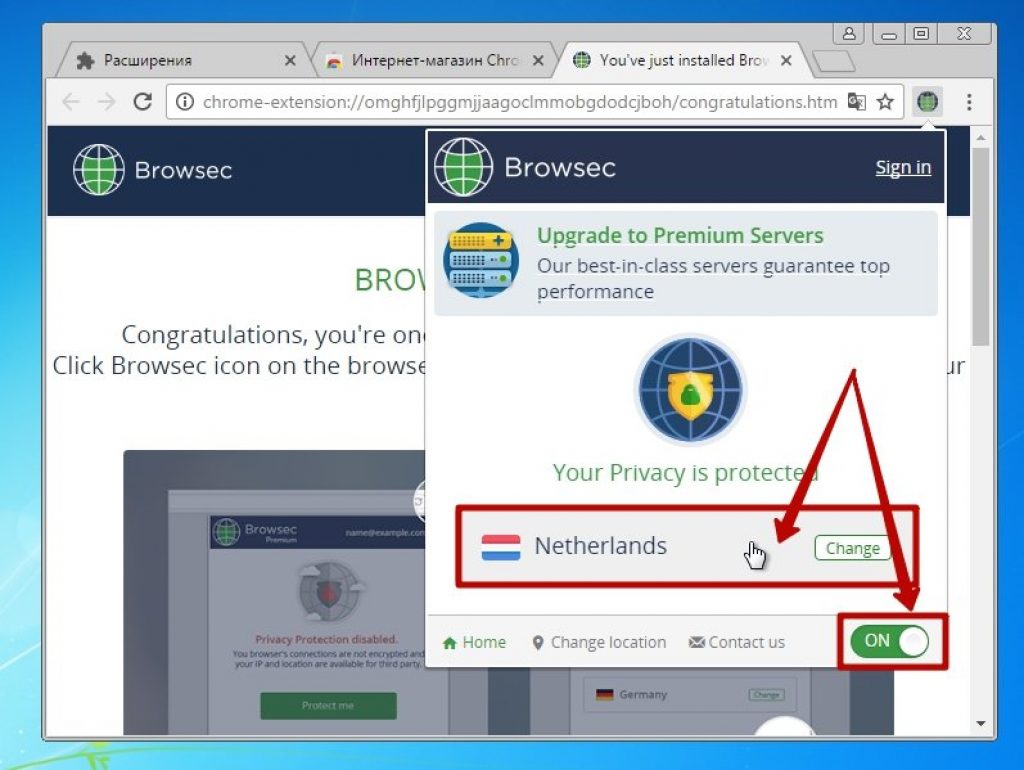
12 To select a country, you need to go to the list of countries and click on its name. The free options available are the Netherlands, the United Kingdom, the United States, and Singapore. To select additional countries, you must subscribe to a paid server.
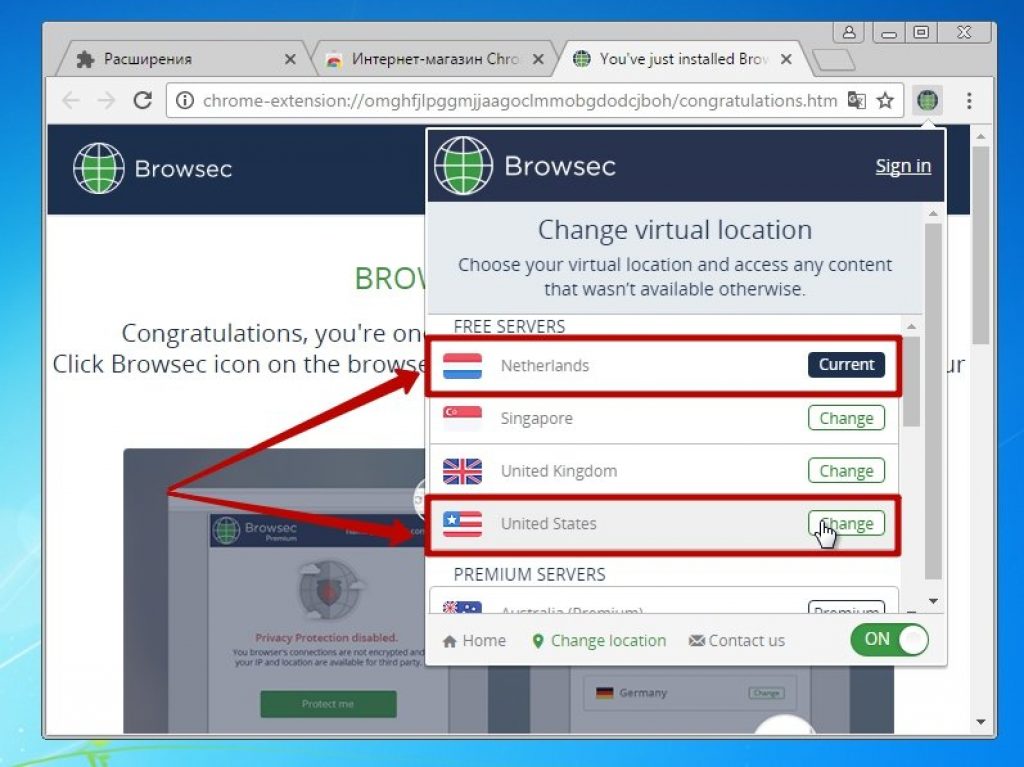
Completing the installation
By installing a VPN in Google Chrome, you will be able to anonymously visit any sites on the Internet.
The extension we reviewed above is completely free, but it also has a premium subscription for advanced features.
The data speed of the 4 countries to choose from is somewhat limited and in order to have more options, you need to purchase the premium version of the extension
This extension will help bypass, both at the private level of use, and at the territorial and global levels. It is also used for security purposes.
VPN for Yandex browser

Here we will provide detailed instructions on how to install the same extension, only in the Yandex browser.
- We find the required browser on the desktop.

- Click on the tab "Settings" .

- We find the item in the list.

- In them we choose .

- In the search, enter Browsec - the addition we need.

- We add it.

- And we install.

- In the same way as in Chrome, an extension icon appeared near the search bar, click on it.

- Switch the slider to enable mode.

- Pressing Change, it will be possible to change the country through which the connection will take place.

- Select from the list the country that you consider preferable for further connection.

- Done!
Completion
In addition to the Browsec extension, there are many more servers, but the considered one is considered one of the more secure and reliable.
In addition, we can recommend the Hola extension for Yandex. It is identical in operation to the one that we gave in the example during installation and is also completely free.
There are countries where it is possible to get jail time for using VPN servers. In countries like Iraq and Iran, these servers are strictly prohibited.
Installing VPN on Android

L2TP / IPsec
Through this method of connection, you can use the resources of the corporate network in a protected access.
Before connecting to the VPN server, you need to ask the network administrator for the access data.
- "Settings" smartphone item "Wireless network" then VPN Settings and further "Add VPN" .

- When creating, you should specify Add L2TP / IPSec VPN , and you will see a window with the settings of the network being created.
You must enter three values:
- in the first field, write any convenient connection name;
- in the second, enter the IP address of the VPN server
- in the third, enter the secret key.

- After that, you will see that the created connection has become available and you need to connect to it.

- During the first launch, you need to specify the username and. And in order not to enter this data with each subsequent connection, you can put a tick on the item "Save information" .

- If all the data is correct, then your successful current state will be displayed in the connection status.

- Installation completed. In case you are unable to connect, try restarting your device and try again.
PPTP protocol
This is one of the most well-known methods of site-to-site connection. It is the standard of use, so connections will not be difficult and will delight you with its speed.
- First you need to find in "Settings" smartphone, as in the previous method, select the item "Yet" then "Virtual network" (VPN).

- And further Add .

On the Internet, you may encounter a situation when you cannot get to the site you need due to the fact that you have limited territorial access to it. I.e. the site is not available to citizens of Russia, for example. But in such a situation, there is a solution, and here the vpn setting will help.
Virtual Private Network is translated as virtual private network. This setting allows you to encrypt your Internet connection, and you can use any opportunity to get online without fear of virus attacks. In this case, you will always be anonymous on the sites you visit.
Initially, such a connection was used by companies to enable personnel to access systems at a distance. For example, while on a business trip or from home. Now such connections are used by individuals to obtain a secure Internet connection at public access points. Or to be able to use the Internet in countries with limited access.
Why VPN on iPhone 6?
How vpn works is pretty simple. Your phone generates a request to connect to a VPN service. After that, he gets off the net. Whereas, all traffic goes through the VPN. Figuratively, it is an imaginary link between your device and the entire Internet that allows you to obtain an IP address. This address masks your actual position.
How to set up vpn on iPhone 6?
There are several ways to enable vpn on your iPhone. The simplest and most popular is the installation through the special TunnelBear application. You can install it for free from the Internet. When the application download is complete, you will be automatically prompted to install the utility profile. Next, you need to select a country from the proposed list, the server that you are going to use and connect to.
If this option did not suit you, you can download a free application in the App Store for IOS - Cloak. The principle of operation is the same here. You download, install and set parameters. The VPN enable will be displayed in the upper corner of your device as corresponding letters. If you often need to use public Wi-Fi networks, then having such applications on your phone comes in handy.
There is also a free application for setting up a VPN on a smartphone - Betternet. Simple and easy-to-use design: two disconnect buttons and connect ... With the first launch, you will need to install a profile. You won't have to do this with the subsequent entry into the application. Actions will be used: connect or disconnect. The application does not have a limit on the volume of traffic, which is a plus in comparison with the programs above.
You can also set up a VPN on the phone itself without installing special applications from the Internet. To do this, you need to go to the main settings of the device and go to the VPN attachment and click "add VPN configuration" here. Next, you need to fill in the "description" column with a lowercase letter in Latin, for example, supermyvpn. Next, fill in the "server" column, for example, us.suprfreevpn.com. In this case, the first pair of letters indicates the country for which your IP address will be replaced.
In the blank field for the account, write a name for the user. After that, select the desired password and additionally duplicate it somewhere so as not to forget. Next, you need to set "auto" in the encryption tab. "For all data" we put on. We click "on" for the "proxy" field. After all these actions, you need to click "save".
VPN (full name - Virtual Private Network) is a way of organizing virtual computer networks over real ones. Why is it needed? They use VPN for a wide variety of tasks. For example, to bypass the blocking of access to certain sites that are prohibited in a particular territory. They use this communication technology to increase confidentiality. VPN makes it easy to encrypt your connection. As a result, the requesting IP will not receive your individual number, which contains the information from where you access the network, but another, tied to a place or a specific country.
So we invite you to work with us to figure out how to set up a VPN on iPhone. At the same time, we promise that the information below will be relevant for almost all models - 4, 4s, 5, 5s, 6, 7, etc.
VPN setup instructions for iOS
You can enable VPN on your iPhone in different ways. Although this is usually done through built-in device settings or using third-party applications.
Let's start by taking a closer look at the first option. That is, we will set up a VPN on the phone itself without installing special software from the Internet.

For reference! VPN is a kind of link between your mobile device and the Internet. Its main function is to give a false IP address to mask the user's real location. Although today many of us use VPNs in order to remove blockages to various prohibited sites.
How to connect VPN on iPhone using the app?
There are many programs out there that provide VPN connections on iPhone. More precisely, every VPN provider has its own app. Therefore, you can simply go to the App Store, download and install it.
Although we recommend paying attention to the program Betternet ... This is one of the most user-friendly of its kind. To connect and disconnect vpn, you need to tap just one button. At the same time, the time for using the VPN is not limited. True, with the first launch, you will have to configure the profile. With the subsequent entry into the application, you no longer have to do this.

Also, you will not need to create accounts or use any other additional services. Just go to Betternet, press "connect" to connect and "disconnect" to disconnect. Also in this application there is no advertising, registration, etc. Even in China it works (there are a lot of restrictions on various resources), where the same popular VPN Master turns out to be useless.
Ask how is this free VPN service doing without any financial backing? It's simple. If desired, each user can become a volunteer and help the project by promoting and installing applications from the App Store. Quite interesting and uncomplicated.
For reference! What other programs for working with vpn can you recommend? These are Tunnel Bear, OpenVPN connect and Cloak. If you have not only an iPhone, but also an Android smartphone, then it is better to use the Turbo VPN program on it.
How to remove VPN on iPhone?
To do this, go to "Settings". Then select the "Basic" section. Then we click on "Profiles". Find your VPN, tap on it and then press the red "Delete" button.

Possible problems
If the iPhone is connected to the network via VPN, then this is indicated by the corresponding icon in the top notification bar (usually it does not blink, but is simply displayed). It also happens that he suddenly suddenly disappears. This means that the VPN connection is not working. As a rule, there are two reasons for the problem:
- unstable internet connection;
- crashes on the server providing vpn services.
Therefore, if there are any problems:
- First, manually reconnect to the VPN using one of the methods described above.
- Then check if your connection to the mobile internet or wifi network is stable.
- Pay attention to the correctness of the specified settings.
- If you used the application, then just install another service. The program you downloaded and downloaded earlier is likely to be blocking the VPN connection in this area.
- You can also try restarting your device and turning off your antivirus software.
Let's sum up
Many people today believe that VPN is an area that only hackers and computer gurus can need. But this is a misconception. Any user, if his favorite Internet resource is blocked, will want to bypass the block and restore access to it. And it will be possible to do this with the help of a VPN. At the same time, we have described in detail how to "crank" all this in this article.
VPN (VPN) - virtual private networks, today on everyone's lips. Many inexperienced users imagine them as a magic key for accessing blocked web resources: they clicked the button and the site was opened. Beauty! Yes, site unblocking is one of the most popular VPN functions, but far from the most important. The main purpose of virtual private networks is to protect data transmitted over the Internet from interception by people for whom this data is not intended.
Let's talk about what virtual private networks are, what functions they perform, where they are used and what are their disadvantages. We'll also explore the capabilities of several popular VPN apps and browser extensions that can be used on both PC and mobile devices.
To better understand the essence of VPN technology, let's imagine the Internet as a network of roads along which post vans with letters and parcels travel. They do not hide at all where they are going and what they are taking. Letters and parcels sometimes get lost on the way and often fall into the wrong hands. Their sender and recipient cannot be 100% sure that the contents of the package will not be read, stolen or tampered with by someone, since they do not control the delivery process. But they know that in terms of security, such a transfer method is not very reliable.
And then a closed tunnel appeared among the roads. The vans that pass through it are hidden from prying eyes. No one knows where the car goes after entering the tunnel, what and to whom it delivers. Only the sender and recipient of the correspondence know about it.
As you may have guessed, our imaginary tunnel is a virtual private network built on top of a larger network - the World Wide Web. The traffic passing through this tunnel is hidden from outsiders, including the provider. The provider, if anyone does not know, under normal conditions (without a VPN) can monitor and control your actions on the Internet, as it sees which resources you visit. And if you dive into a VPN, you can't. In addition, the information sent through such a channel becomes useless for lovers of someone else's good - hackers, since it is encrypted. This is the essence of the technology and the simplified principle of VPN operation.
Where are virtual private networks used?
What is it for, this VPN, I hope it's clear. Now let's see where, how and what it is used for. So, you can't do without a VPN:
- In corporate networks. Here it is necessary for the exchange of confidential data between employees or network resources of the company and customers. An example of the second case is managing accounts through applications such as bank client and mobile bank. VPN is also used to solve technical problems - traffic separation, backup, etc.
- On public Wi-Fi networks, such as a cafe. Such networks are open to everyone and the traffic passing through them is very easy to intercept. The owners of open access points do not provide VPN services. The user himself must take care of the protection of information.
- To hide visited web resources, for example, from the boss or system administrator at work.
- To exchange classified information with other people, if there is no trust in a regular Internet connection.
- To access blocked sites.
- To maintain anonymity on the Internet.
Providing access to the World Wide Web through VPN is also widely used by Russian Internet providers when connecting subscribers.
VPN varieties
As you probably know, the functioning of any computer network is subject to the rules that are reflected in the network protocols. A network protocol is a kind of set of standards and instructions that describes the conditions and procedure for exchanging data between participants in a connection (we are not talking about people, but about devices, operating systems and applications). VPN networks are distinguished by the type of protocols on the basis of which they work and the technology of their construction.
PPTP
PPTP (Point-to-Point Tunneling Protocol) is the oldest virtual private network data transfer protocol, more than 20 years old. Due to the fact that it appeared a long time ago, almost all existing operating systems know and support it. It almost does not load the computing resources of the hardware and can be used even on very old computers. However, in the current environment, the level of its security is very low, that is, data transmitted over the PPTP channel are at risk of hacking. By the way, some ISPs block applications that use this protocol.
L2TP
L2TP (Layer 2 Tunneling Protocol) is also a fairly old protocol based on PPTP and L2F technologies (the latter was specially designed for tunneling PPTP messages). Provides a higher degree of traffic protection than just PPTP, as it allows you to set access priorities.
L2TP is widely used to this day, but usually not in isolation, but in combination with other security technologies such as IPSec.
IPSec
IPSec is a complex technology that uses many different protocols and standards. It is constantly being improved, therefore, when used correctly, it provides a fairly high level of communication security. Can be combined with other network security systems without causing conflicts. These are his strengths.

Disadvantages of IPSec are laboriousness to set up and reckoning on use only by trained specialists (incorrectly configured, it will not provide any acceptable protection). In addition, IPSec is quite demanding on the hardware resources of computing systems and can cause slowdowns on weak devices.
SSL and TLS
SSL and TLS are mainly used for the secure transfer of information on the Internet via web browsers. They protect confidential data of site visitors from interception - logins, passwords, correspondence, payment details entered when ordering goods and services, etc. The addresses of sites that support SSL begin with the HTTPS prefix.
A special case of using SSL / TLS technologies outside of web browsers is the cross-platform OpenVPN software.
OpenVPN
OpenVPN is a free implementation of VPN technology designed to create secure client-server or point-to-point communication channels between Internet users or local area networks. In this case, one of the computers of the connection participants is assigned as a server, the rest are connected as clients. Unlike the first three types of VPN, it requires the installation of special software.
OpenVPN allows you to create secure tunnels without changing the parameters of the main computer connection to the network. Designed for experienced users, as its configuration is not easy to call.
MPLS
MPLS is a technology for multi-protocol data transmission from one node to another using special labels. The label is a part of the service information of the package (if you represent the transmitted data in the form of a train, then the package is one carriage). Tags are used to redirect traffic within the MPLS channel from device to device, while the rest of the packet headers (like the email address) are kept secret.
To strengthen the protection of traffic transmitted over MPLS channels, IPSec is also often used.
These are not all types of virtual private networks that exist today. The Internet and everything that comes into contact with it is in constant development. Accordingly, new VPN technologies are emerging.
Vulnerabilities in virtual private networks
Vulnerabilities are security holes in the VPN channel through which data can leak out to the public network. Unfortunately, absolutely impenetrable protection does not exist. Even a very well-built channel will not give you a 100% guarantee of anonymity. And it's not about hackers who break encryption algorithms, but about much more banal things. For example:
- If the connection to the VPN server is suddenly interrupted (and this happens quite often), but the connection to the Internet remains, some of the traffic will go to the public network. To prevent such leaks, they use VPN Reconnect (automatic reconnection) and Killswitch (disconnect the Internet when the VPN connection is lost). The first is implemented in Windows, starting with the "seven", the second is provided by third-party software, in particular, some paid VPN applications.
- When you try to open a site, your traffic is first directed to the DNS server, which determines the IP of this site from the address you entered. Otherwise, the browser will not be able to download it. Queries to DNS servers (by the way, unencrypted) often go beyond the VPN channel, which breaks the mask of anonymity from the user. In order to avoid this situation, specify the DNS addresses provided by your VPN service in the Internet connection settings.

- Data leaks can be created by web browsers themselves, more precisely, their components, for example, WebRTC. This module is used for voice and video communication directly from the browser, and it does not allow the user to choose the method of network connection himself. Other applications with Internet access can also use unsecured connections.
- VPN works on networks that are based on the IPv4 protocol. In addition to it, there is the IPv6 protocol, which is still at the implementation stage, but in some places it is already being used. Modern operating systems, in particular Windows, Android and iOS, also support IPv6, even more - many of them have it enabled by default. This means that the user, without knowing it, can connect to the public IPv6 network and his traffic will go outside the secure channel. To protect yourself from this, disable IPv6 support on devices.
You can close your eyes to all these flaws if you use VPN only to access blocked web resources. But if you need anonymity or data integrity while transmitting over the network, they can create serious problems for you if you do not take additional protection measures.
Using VPN to Bypass Blocks and Anonymize Traffic
The Russian-speaking audience of the Internet most often uses a VPN precisely in order to freely visit blocked Internet resources and maintain anonymity on the network. Therefore, the bulk of free VPN-applications and services "sharpened" just for this. Let's get to know some of them better.
Opera VPN
The developers of the Opera browser were the first to implement the VPN module directly into the product itself, saving users from the hassle of finding and configuring third-party extensions. The option is enabled in the browser settings - in the "Security" section.
 Once enabled, the VPN icon appears in the Opera address bar. By clicking on it, a settings window opens, including an on-off slider and a choice of a virtual location.
Once enabled, the VPN icon appears in the Opera address bar. By clicking on it, a settings window opens, including an on-off slider and a choice of a virtual location.

The traffic volume through Opera VPN is unlimited, which is a plus. But the service also has a drawback - it protects only the data that is transmitted over the HTTP and HTTPS protocols. Everything else goes through an open channel.
Opera, as well as Yandex browser, has another function with similar capabilities. This is the turbo traffic compression mode. It does not work with VPN, but it opens up access to blocked resources quite well.
The Browsec browser extension and mobile app is one of the most famous VPN services out there. It supports all popular web browsers - Opera, Google Chrome, Firefox, Yandex, Safari, etc., provides a fast and stable connection, does not require configuration, and has no limit. Users of the free version are offered a choice of 4 servers: in the UK, Singapore, the USA and the Netherlands.

A paid Browsec subscription costs about 300 rubles per month. Users of this tariff receive a higher connection speed, technical support and a large selection of servers around the world, including Russia, Ukraine, Latvia, Bulgaria, Germany.
Hola
Hola is Browsec's main competitor in the form of apps and browser extensions. Versions for Android, desktop systems and browsers work on the basis of peer-to-peer technologies (peer-to-peer network), where users themselves provide resources for each other. For personal non-commercial use, access to them is free. The choice of servers is quite large.
 Hola for iOS is designed as a browser with an integrated VPN service. It is paid, it costs about $ 5 per month. The trial period is 7 days.
Hola for iOS is designed as a browser with an integrated VPN service. It is paid, it costs about $ 5 per month. The trial period is 7 days.
Zenmate is the third most popular VPN service, released as an extension for Opera, Google Chrome, Firefox, Maxthon Cloud Browser (Mac OS X only), and several other browsers. And also - in the form of mobile applications for Android and iOS. With free use, the speed limit is noticeable and the choice of servers is very limited. However, all traffic passing through the Zenmate VPN is securely encrypted.

Customers who purchase premium access have a choice of over 30 servers around the world. Plus, connection acceleration is turned on for them. The subscription price starts from 175 to 299 rubles per month.
Like other similar services, Zenmate does not need to be configured - just install and run. Working with it is intuitive, especially since the interface supports Russian.
Tunnelbear is another user-friendly VPN for different devices - PCs running Windows, Linux and OS X, smartphones running Android and iOS. It is released in the form of applications (both mobile and desktop) and browser extensions. Has a very useful function of blocking traffic when the VPN connection is broken, which prevents data leakage into the open network. By default, it selects the optimal communication channel, taking into account the user's location.

The capabilities of the free versions of Tunnelbear are no different from the paid ones, except for one thing - the traffic volume limit is up to 500 Mb per month. In a phone, this is probably enough, if you do not watch movies online, but on a computer it is hardly.
Neither the paid nor free versions of Tunnelbear collect any user data. You just press a single button and you have access.
HideMy.name
HideMy.name is a reliable and relatively inexpensive paid VPN service. Provides a consistently high connection speed even when watching online HD videos and playing games with network toys. It well protects traffic from interception and provides complete anonymity on the network. NideMy.name servers are located in 43 countries and 68 cities around the world.

HideMy.name supports any device that can connect to the Internet: not only phones and computers, but also routers, set-top boxes, SmartTVs, etc. With one subscription, you can use the service simultaneously on all devices.
HideMy.name apps are released for Windows, Mac OS X, Linux, iOS and Android. As said, they all cost money, but you can only pay for the days you use the VPN. The cost of a daily subscription is 49 rubles. License for 1 year - 1690 rubles. The free trial period is 1 day.
Is a long-standing VPN application, one of the few that has always provided services for free and with no traffic restrictions. The limit of 500 Mb per day for "free" use appeared relatively recently. Also, "freemen" have access to only one VPN server, which is located in the United States, so the connection speed through Hotspot Shield is not very high.
 The cost of a paid subscription to VPN Hotspot Shield is $ 6-16 per month.
The cost of a paid subscription to VPN Hotspot Shield is $ 6-16 per month.