MPort magazine will offer some simple but effective ways to create and remember passwords for your accounts.
depositphotos.com
For a reliable password, one or even a few words are frankly small. Use whole phrases that are difficult to pick up intruders, but it's easy to remember you.
This can be "MportEtoSamiyKrutoyJurnal777", for example. It is also important to use both uppercase and lowercase letters - this will complicate hacking. Do not hesitate to use passwords of about 20 characters in length. If the site is limited by the number of characters - use the maximum.
A good password contains letters and numbers, so boldly add them to any part of the phrase. The main thing is that it's not the year of your birth, the number of the car, phone or apartment.

depositphotos.com
It will also complicate the hacking of the use of special characters, which on the computer is plentiful:!?;?;%:? * (_ @ # | $ & And this is not all.
The phrase-password can be something of your interests or vice versa. Do you like cars and do not know what password to come up with? The password "SubaruImprezaWRXsti" will work. The main thing is that you do not have Impreza, and on pages in social networks there were no pictures of her, or you give a hint to intruders.
You can also switch the layout while writing the password. So, turn on the keyboard Russian language, and type the password in English letters or vice versa.
It is not necessary to use one password for different mailboxes, social networks, online banking and a working computer. It's better to take your ready-made phrase and use thematic prefixes - add letters or numbers, or special symbols.
Check the password at https://howsecureismypassword.net/. By the way, to crack the password "SubaruImprezaWRXsti" hackers will need 3 quadrillion years (on an ordinary computer without special hardware and software).
And a little more on how to come up with an intelligent password and check its reliability:

How to come up with a strong password
MirSovetov found that Internet users, when they come up with passwords for their accounts, often make the same mistakes. Let us consider in more detail what kind of protection for hackers will be easier to crack:
- A direct or reverse sequence of digits is considered the most common variants of the password. The first thing that comes to mind is a person who wants to get to personal data - this is to enter into the desired field a combination of "123456 ..." or the same numbers, but in the reverse order.
- The second most popular password is the word "rassword", not inferior to it in the prevalence and the combination of the letters "qwerty".
- Often, Internet users enter the name of the service as the password, in the account of which they create protection.
- Many people like to use their name or surname, date of birth or address as a password email. These data can be used in a variety of combinations, written in uppercase letters or supplemented with combinations of numbers, but experienced hackers can easily crack such protection if necessary.
- Instead of their data, Internet users often use data from their relatives: a husband, children, parents. In this case, the key word may be the name or date of birth of the child, mother's maiden name, etc. Popular passwords are also considered the nickname of a pet, the brand or number of the car, the name of the native city.
- The sequence of letters on the keyboard can also be attributed to simple and unreliable types of protection. Such sequences are very easy to calculate with the help of special programs, which in just a few minutes from a variety of options will choose the right one.
- Simple words like "money", "love", "friendship", "happiness" can also be classified as dubious types of personal data protection.
- Modern programs for hacking have a special function for recognizing modifications, so replacing letters in simple words with similar symbols will not help. This utility can easily recognize in the figure 4 the letter "A" or "H", and in the figure "0" the letter "O".
- Simple passwords include simple sentences like "I love you".
- A common mistake many people make is using the same passwords in different services. Any hacker, hacking one password, is not too lazy to check it on other accounts.
What should be a strong password

- The main rule is to use different passwords for all Internet accounts.
- A security word or phrase should not be associated with a user's personal data. Avoid including passwords in names, surnames, birth dates, nicknames of pets, etc.
- It is desirable that for an unauthorized person the password looks like an illogical sequence of words, letters or numbers. In this case, the protective combination must be logical for the user himself, otherwise he will simply forget it.
- The phone number must also not become a password.
- Password can not be communicated to anyone, especially to unauthorized persons. Remember that even a call from a bank or other organization with the request to provide such information in many cases is the work of scammers.
- Some services after registration of the account send a temporary password to the email. This combination should be changed immediately after you enter the site.
- Do not store passwords in a browser or desktop computer.
- The security word should be long enough and contain not only letters, but also numbers and other valid symbols.
- To create a password, you can use a special generator. There are a lot of similar programs, among the popular services, you can identify such: onlinepasswordgenerator.ru, securrity.ru, sadesign.pro, genpas.net. With the help of programs it is possible not only to create unique passwords, but also to check independently invented combinations for the degree of reliability. For this purpose, use one of the following services: blog.kaspersky.com, parolemanager.com or earninguide.biz.
- Try not to log into your accounts from other people's computers, especially in Internet cafes or in game clubs. In such places, you can most likely stumble upon a spyware program that reads the sequence of keystrokes on the keyboard.
- Passwords should be changed periodically. The more reliable the protection, the less it is necessary to do it, but even a long 12-digit combination of letters and numbers must be changed at least once in 2 years.
Ideas for creating a password

To come up with an original password, hack which will be difficult, use a well-known you otnalochku or short poem. Take the first letter from each word of such a rhyme, replace some of them with similar symbols, for example, change the letters "o" to "0", "h", replace with "3", and the letter "h" with the number "4". In the password, you can use punctuation marks, if they are in the poem. For additional protection, Cyrillic letters can be written in the Latin keyboard.
Instead of a quatrain or counting, some favorite saying is also quite appropriate. This may be a favorite philosophical quote, a well-known phrase of a movie hero, etc. The principle of creating a password in this case is the same as when using a count. By the way, for a greater complexity, some letters can be replaced not by similar figures, but by some other. For example, instead of "h" you can write not "4", but "8", "5" or any other symbol.
As a protective word, you can apply a specific term, known to a narrow circle of specialists in a particular field. Technical or medical definitions may be useful here, for example, complex names of medicines.
The password is not recommended to prescribe the date of birth of yourself or someone from your loved ones, but this does not mean that you can not use other memorable dates. Such a number can, for example, denote the day of the first kiss. The main thing is that the date was known only to you or a very limited circle of people. Instead of points dividing the day, month and year, it is better to enter any character or letter.
To create a password, a so-called visual key can be used. Visually draw on the computer keyboard some simple drawing, for example, a funny face. Click on the keys through which your drawing passes.
How to save the password

After inventing a complex and original password, the most important thing is that it is not forgotten afterwards. To not rely solely on your memory, a combination of symbols can be written and saved in various ways:
- The simplest way is to rewrite the protective word on a sheet of paper and hide it in your favorite book or put it on the shelf of the cabinet. It is not recommended to write the password to the notepad, since the attackers can steal the organizer.
- The combination of symbols can be fixed in notes mobile phone, only the note itself can not be signed with the word "passwords" or with any similar definitions.
- The password can also be saved on the computer, only for this it will be necessary to disguise the file well. For this, you can text extension Change to graphic and hide the file in the folder with pictures. To open the document, you need to right-click on it and select a text editor from the list of programs.
In general, this is good advice, but the realities of the Internet are much more complicated than this. If we could remember all the lines of encrypted text for every site we visit, our online life would probably be much more secure. But we, as people, are prone to errors and, as a result, we forget, we use labels and we inadvertently create ourselves serious security problems.
The truth is that most of the hacking that takes place on blogs and other personal pages are not caused by any vulnerability software, but occur as a result of selection or phishing. Thus, maximum security can be ensured if you try to come up with a password that will be very reliable. But here the protection of the blog is described in more detail.
But much easier said than done. Here are some practical tips.
When we start an account somewhere, the question immediately arises: what password can you come up with?
And so, start with the word that you know, and then modify it. For example, start with the word "orange":
1. Basic word: orange
2. Add the numbers: o7ran3ge
3. Add capital letters: O7ran3Ge
4. Add the following conventions: O7r + n3G =
The above password is according to Microsoft's Password Checker is "strong", but it can easily be made "best" by adding six additional letters and numbers, possibly adding another word. However, since not all sites allow the use of more than 8-10 characters for the password, it is important to first create a short one, and then expand it if necessary.
Create different passwords
As soon as you come up with complex password, it is necessary to create its variations. There are two reasons for this. First, using the same secret word on several sites poses a security risk. Secondly, even if you feel comfortable using the passphrase in several places, not all sites will allow you to use symbols or capital letters, in effect, forcing you to choose weak variations.
For example, for bank accounts you have to come up with a word that will be beyond the complex. On forums it is better to use less reliable ones, such as "O7ran3Ge".
Variations on the theme
An even more reliable way would be to use the site that you visit as the base for the password. For example, you can use the first letters of the domain.
1. Basic word: alex
2. Move one key to the left on the keyboard: akwz
3. Add the numbers: 1akwz3
4. Add capital letters: 1AkWz3
5. Add the symbols: 1Ak + Wz3%
The problem with such a system is that it can slow down your work, especially on sites that you do not visit often.
Conclusion
However, there is no magic wand for absolutely reliable protection. You just have to use trusted, easy-to-remember, but complex passwords and not tell anyone. And to strengthen the security of the site can be and with the help of plug-ins.
Lastly, using a strong password is the first rule of security on your computer, and you are most likely to be all right.
Passwords are everywhere: on social networks, payment systems, on the computer and on the phone. To keep in mind so much information is unrealistic, so many users go along the path of least resistance - come up with one key that is easy to remember, and then enter it at all sites on which they register.
This approach to security can end badly. If the access code for VKontakte or Classmates can be lost without serious financial consequences, and therefore it is not necessary to make it complicated, then you need to come up with a password to register in the payment system or create an Apple ID so that no one but the owner can access the data.
Rules for creating passwords
Practically on all sites at registration there is a list of requirements to passwords. However, these requirements are usually minimal: at least 8 characters, can not consist only of numbers or letters, etc. To create a really complex password, you need to remember a few more restrictions.
- The login and password must not be the same.
- It is not recommended to use any personal information, especially if it can be learned from social networks or other sources.
- It is not recommended to use words.
To understand the logic of these prohibitions, it is enough to see how passwords are cracked. For example, a key of 5 digits is just 100,000 combinations. The program for hacking through a simple search of all options will find a suitable combination of minutes for 2, if not less. It will not do for the access code and a rare word. The cracker can analyze different dictionaries in different languages and find a match. The only question is how long this will take - a few minutes or a couple of hours.
Advanced PDF Password Recovery for hacking passwords installed on a PDF document. Uses bruteforce, allows you to fine-tune the selection, noting the symbols used in the password.
The combination of a rare word and numbers also does not work. Bruteforce technology allows you to search for combinations of numbers and words, so if necessary, such a key will fall. It will last, of course, a little longer than 123456789, but if you suffer losses due to a break, then this time difference is unlikely to be significant. To understand which password is reliable and which one is not very, let's look at specific examples. Approximate time of hacking is calculated with the help of password verification services, which are described below.
- Date of birth (05041992) - will be hacked for 3 milliseconds.
- The name with a small or capital letter (Segey, sergey) - will last 300-500 milliseconds, that is less than half a second.
- Combinations of numbers and lowercase letters (1k2k3d4a9v) - about 1 day.
- The hacking of a password like HDA5-MHJDa takes about 6 years.
- The combination of AhRn & Mkbl363NYp will be decoded after 16 million years.
No 16 million years or even 6 years the burglar will not work - this value only demonstrates that it is impossible to crack the password in an acceptable time.
Password Generation
It's one thing to know the rules, it's another thing to follow them. Most users are aware that an access code consisting of a date of birth or a name can not be used for registration, but few people stop it. There are two problems:
- It's hard to come up with a complicated password.
- Even if you create a password containing a random character set, it's hard (sometimes impossible) to remember it.
The online password generator will help you with the first problem. On the Internet, you can find a large number of services offering to quickly create a complex password of letters, numbers, special characters.
Online generators work on one principle: you specify which symbols to use, select the required number of characters and click "Generate". The services differ only in particular moments. 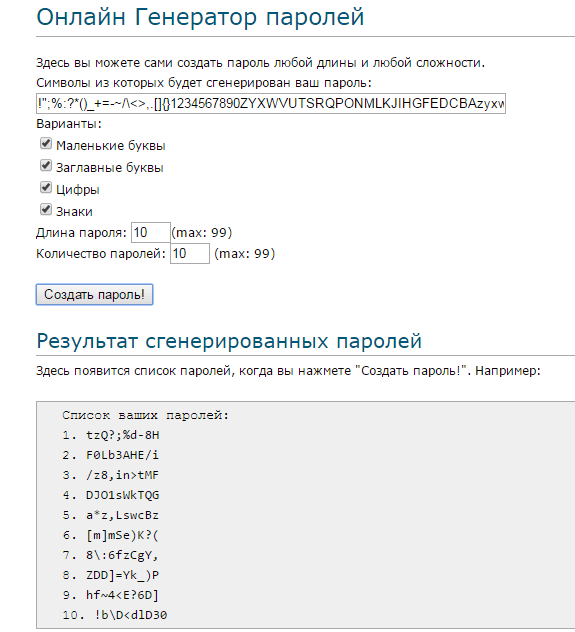
For example, on Pasw.ru you can generate several dozens of passwords at once (up to 99 combinations). PassGen allows you to set the option to automatically remove duplicate characters from the security key, that is, all the characters in it will be in the singular.
Key storage
If you can generate the password online, then you need to store the keys on the computer. Write a password on a piece of paper, in a separate document on the computer, on a sticker glued to the screen - the path to unauthorized access to data. So here comes the second problem: how to remember the generated key.
You do not have to hope for memory, but you can rely on the password manager. Many users choose KeePass. This program is distributed free of charge and runs on Windows 7, Windows 10 and other modern versions of the operating system from Microsoft. In addition, KeePass has a built-in password generator, so you do not have to search for online services every time. 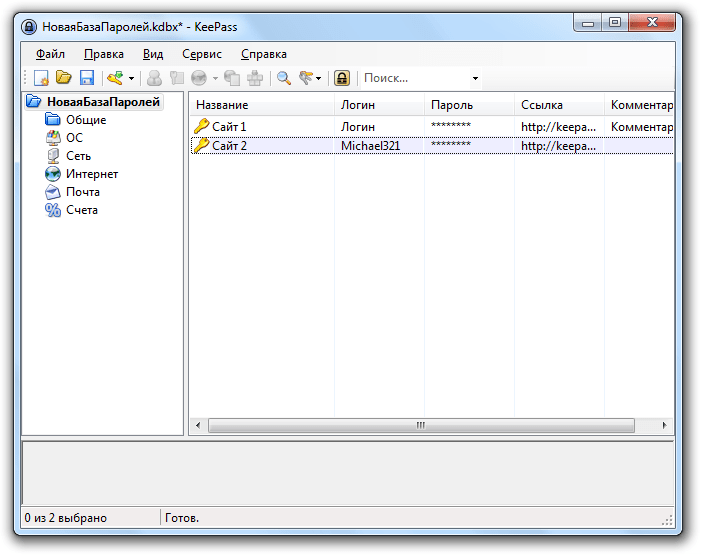
The minus of the password manager is only that it also needs an access code, which is called the master password. But remembering one master password is much easier than keeping dozens of complex combinations in mind. In addition, when you create it, you can use the trick - to take as a basis verses, counters or any other memorable lines and turn them into a combination of letters, numbers and signs. 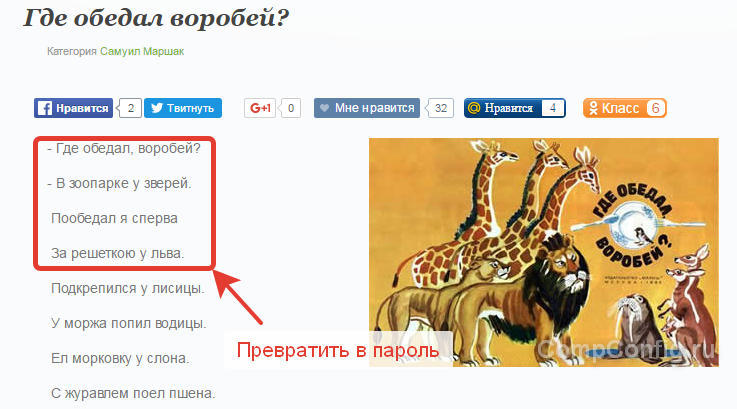
For example, you can take a quatrain, highlight the first letters and punctuation marks, and then write them on the Latin keyboard. Some letters can be replaced by numbers - "z" to "3", "o" to "0", "h" to "4". As a result of this manipulation of the four lines of the children's poem, which never flies out of your head, you get the password U0d? D3ep.Gzc3hek, which will take 3 trillion years to break.
Checking the complexity
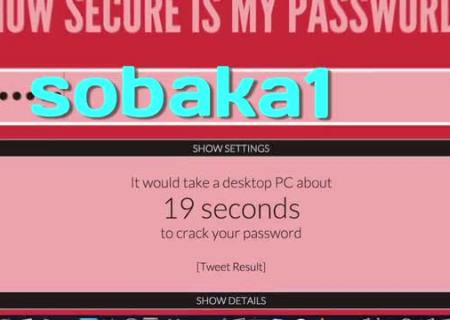
On many sites, when registering, the user is shown if he has a good password. Make sure that the generated code is complex, and it can not be hacked quickly, it is possible and independently using the service? In the "Enter Password" field, insert the generated password. In response, you get an approximate time, which will be spent on hacking the key on an ordinary computer. If several million or even thousands of years, then the code turned out to be unambiguously reliable. 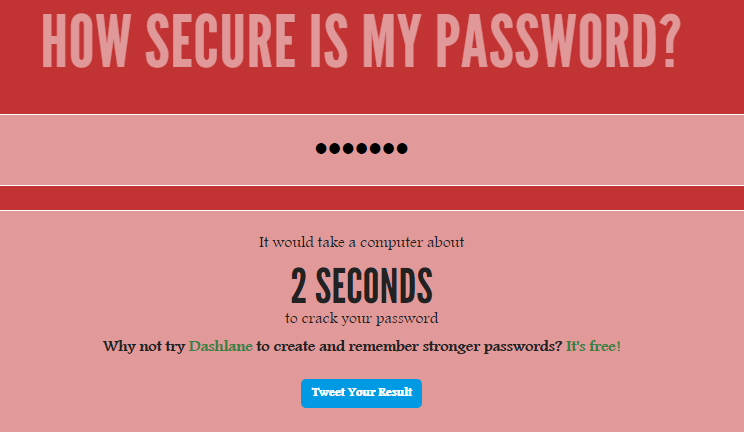
You can use other services to verify reliability: for example, from Kaspersky Lab. It also shows the time needed to crack the password, at the same time telling what can be done for the specified interval. ![]()
Another interesting way to check is the "Password Strength" service on the site 2ip.ru. Here the result is categorical: the key is either reliable or unreliable. 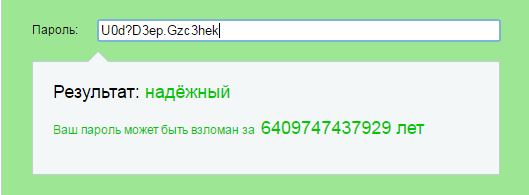
We need to understand that the time of hacking that these services show is quite arbitrary and is calculated in case the cracker uses a regular computer. A supercomputer with fantastic performance will cope with the task faster, like special machines for hacking passwords, which can test up to 90 billion keys per second. But it's unlikely that people who own such a technique will need your password from e-mail, Skype or Wi-Fi.