12345 - we need to change the password. How to create a complex password and remember it forever
Internet scammers steal millions of passwords daily from mailboxes and user accounts. But do not despair - we will give some very simple but effective advice that will protect you from losing control over your resources.
1. Use the complex passwords
You guessed it, did not you? Forgive for the banality, but this is the main advice - which until now most users are neglected. Not without reason, passwords such as qwerty remain in the top most popular to this day.
Do not use the names of your favorite heroes, the name of a football club or the pet's nickname as a password, as this information is easy to find in your social networks. A complex password must consist of an arbitrary combination of different characters and symbols.
2. Use uppercase and lowercase letters, numbers and symbols
, users do not like long passwords - they are easy to forget and laziness to recruit. A password of 8 characters was considered reliable only at the dawn of computer development; Today the eight-digit combination is mechanically selected in a couple of hours.
However, even a short password (up to 8 characters) can be made relatively reliable if you use numbers and letters in different registers. The selection of such a password will take 2-3 days.
Maximum reliability is achieved by simply increasing the length of the password and using different characters ($,%, &, '', #), in those services where possible.
3. Use the acronyms
Choose a phrase that you do not forget, and use the combination of the first letters of each word as a password. For example, the poem of 1828 "At Lukomorye oak is a green, golden chain on an oak tree ..." turns into ULdzzcndt1828.
4. Use with a keyword
Select a keyword and mix it with the name of each site on which you have account. For example, for the keyword "antivirus" the password on the site will look like this: c al nu tb ie vs ie rt un sod32. The advantage of this trick is that you will have strong password for each site.
As suggested in the comments, this method may fail in case of changing the site address - however in this case it is enough to use auto-recovery of the password.
5. Do not use the same password for different accounts
As a real artist, be original. Remember that different sites have different levels of security. For example, most services send passwords via e-mail through the password recovery procedure. Having received a password from an unsafe service, hackers can try to use it for your mail or social networks - the same password will be the key to all your resources.
Reduce risks can only be using unique complex passwords for all accounts.
6. Change passwords more often
In the case of the theft of Mail.ru passwords, 99.982% of all passwords were irrelevant. This was largely due to the fact that most of the database of stolen accounts was compiled from a number of other databases.
However, in the case of 57 million addresses (that's the number of records in the leaked database), this is not enough - you can guarantee that your Mail.Ru mailbox is not compromised by intruders? And this is just one example of the leaked base - how many millions of current addresses are walking today on the hands of hackers we do not know.
But we know for sure that they would have been much less if users regularly changed their passwords.
7. Use the password manager
How not to forget the password from the VKontakte account, mailbox and Internet banking? Few can remember dozens of complex passwords. This is normal.
Fortunately, the developers software came up with a solution. Today, there are many tools that help users securely store an unlimited number of the most complex passwords. For example, you can use the most popular - LastPass or 1Password.
However, password managers have their weak points. The most important accounts through which you can access your bank information, do not trust even the most reliable programs.
8. Do not forget about the "secret question"
In the council number 1, we recommended not to use as a password data that can be easily learned about you from social networks. The same goes for "secret issues", which many for some reason forget or do not attach importance to them. In addition, attackers can easily pick up the answer from the database of popular options.
Try to use the tactic of absurdity, when the answer has nothing to do with the secret question. Mother's maiden name? Aspirin! A pet's name? 1989!
9. Use two-factor authentication
To minimize the risk of credential leakage, use two-factor authentication wherever possible.
Most social networks, postal and banking services allow you to enable authorization confirmation via SMS. Thus, scammers will not be able to access your account if they do not have your mobile phone in their hands.
So, if you have an account on Yandex, we recommend using the two-factor authentication function Yandeks.Klyuch:
- Download the Android or iOS app
- Enter password or QR code
- Sign in to Yandex
- Profit!

10. Antivirus is our all
Passwords do not just get to hackers, do not swim to them by air (except for the usual fraud, when users themselves tell criminals passwords from their services).
Personal data collects and sends hackers very specific malware, which all by hook or by crook tend to get on your PC, laptop or smartphone.
Therefore, putting a reliable antivirus with protection of online payments (and regularly updating the database) is one of the main ways to save your money, nerves and privacy.
On the Internet, passwords are required everywhere: for email, online stores, social networks, payment systems and other services. For security reasons, it is recommended to come up with a complex combined password consisting of uppercase and uppercase letters, digits, special characters. Of course, this significantly reduces the risk of unauthorized third-party access. But often the user himself forgets what password he came up with. How can I remember my passwords?
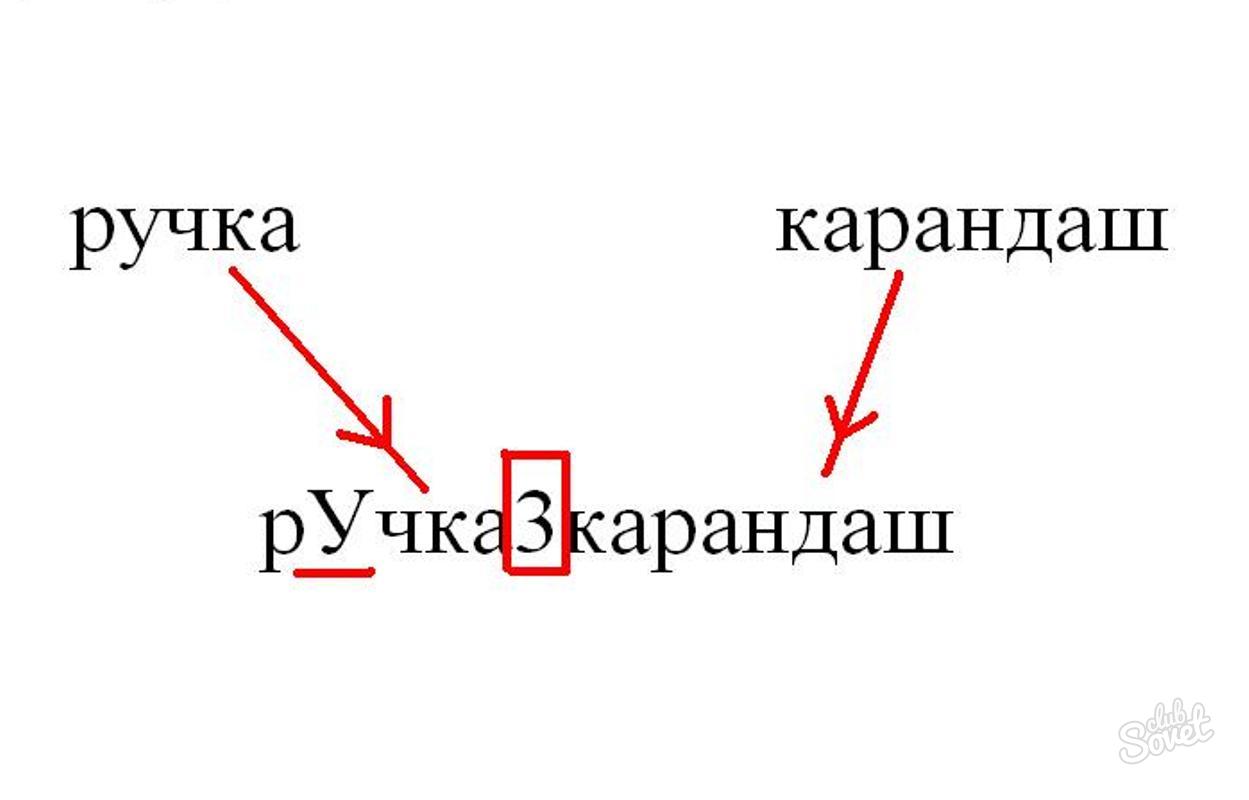
First, do not create the same password for all programs (although, of course, it's much easier and more convenient). There are a few simple ways, which will help you quickly remember your passwords. They do not even have to be recorded. First, how you can create a reliable and memorable password is to combine two words. Between them you can put a symbol, a digit. In addition, you can determine in advance that in any password the second (or any other) letter will be capitalized. For example, "rukka3krandash", "Lampa% table". At input it is necessary to establish English keyboard layout, and to enter symbols, being guided by Russian. Also an interesting way is to insert one word inside the other. You can choose different combinations for mail, e-wallet and shops. For example, take as a rule that first the first two letters of the first word will be written, then the symbol (digit), then the second word (the second letter capital) and the end of the first word. For example:- for webmoney - "maedEngishina";
- for mail - "ma2tExts";
- for soc. network - "madrugshina";
- for the store - "ma% pokupkashina".
- cis4m - strong will win one, knowing - one thousand;
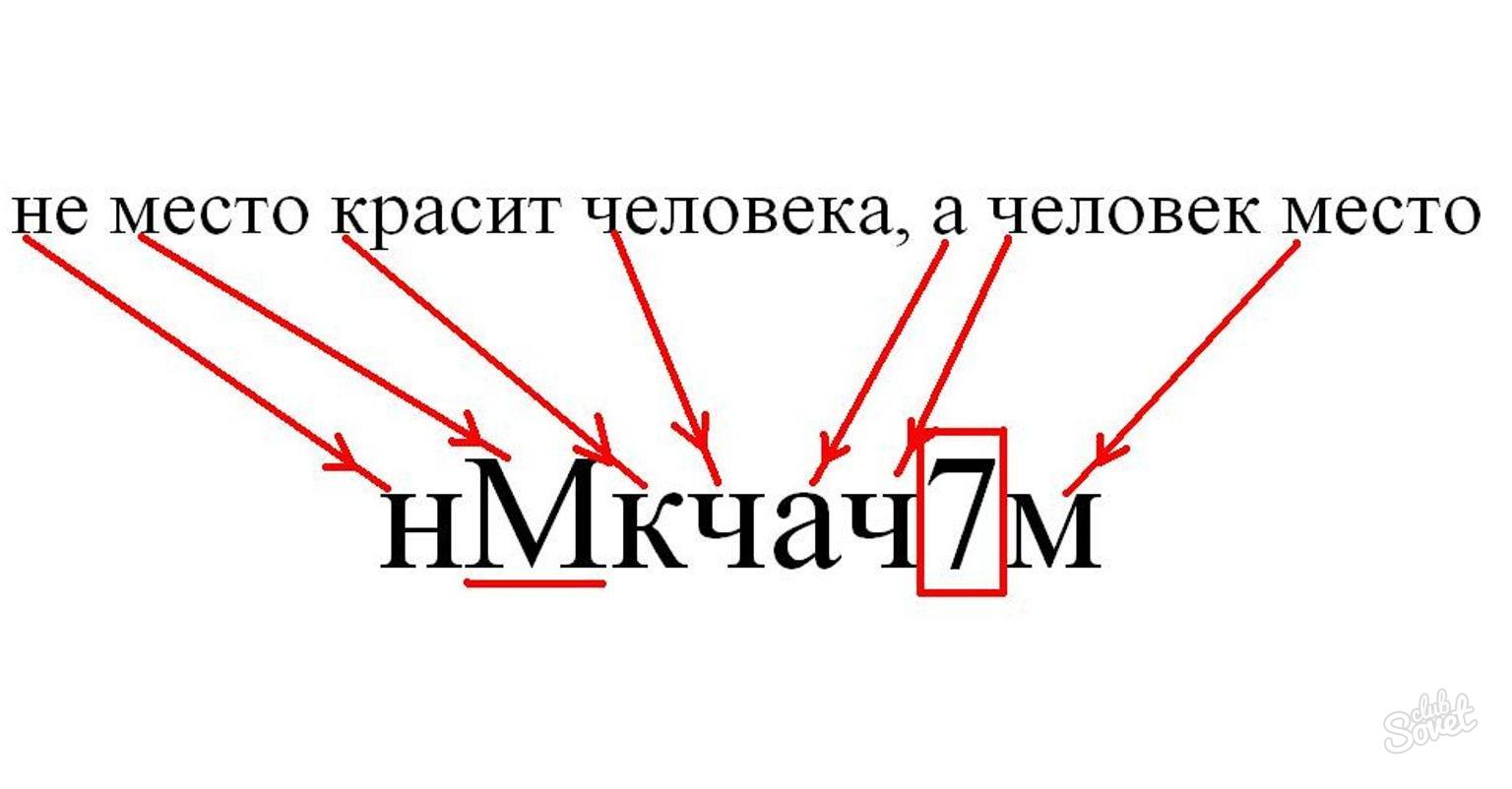
- nMkchach7m - not a place that colors a person, but a person a place;
- dUchm5l - a fool to teach - that the dead be treated.
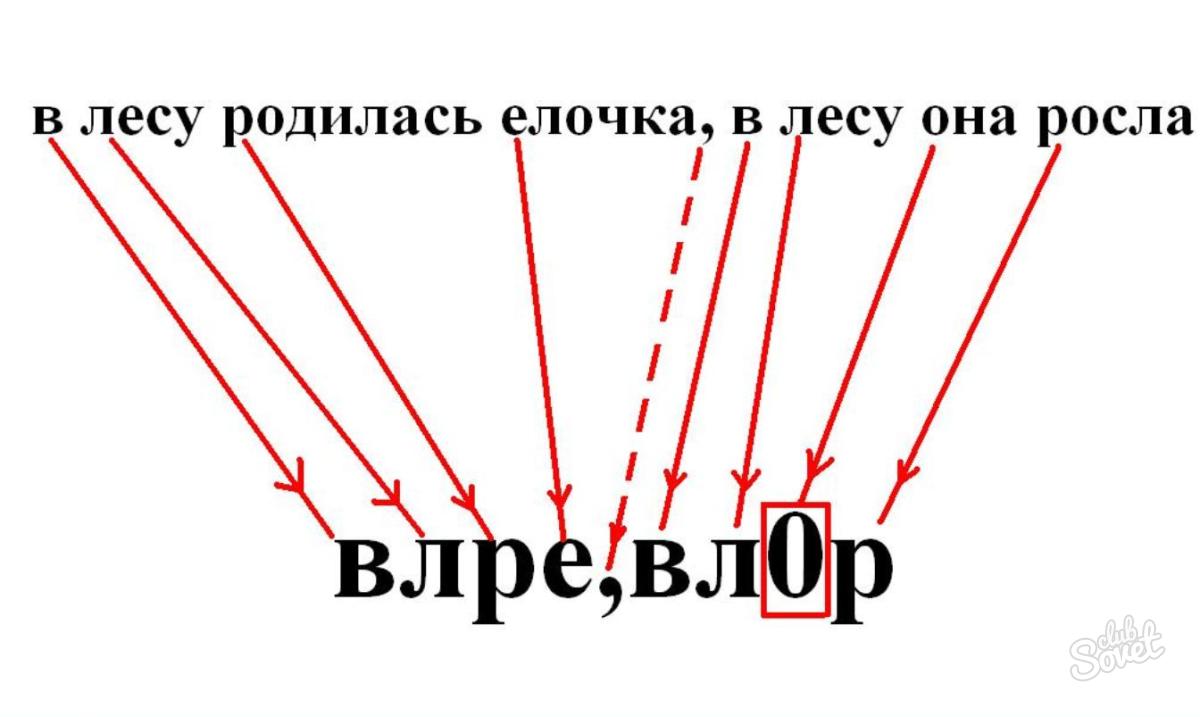
- vlre, ovor - a tree was born in the forest, it grew in the forest;
- umnp, 0ml, vrenb, p40x - dropped the bear on the floor, tore off the teddy bear, still I will not give it up, because it's good.
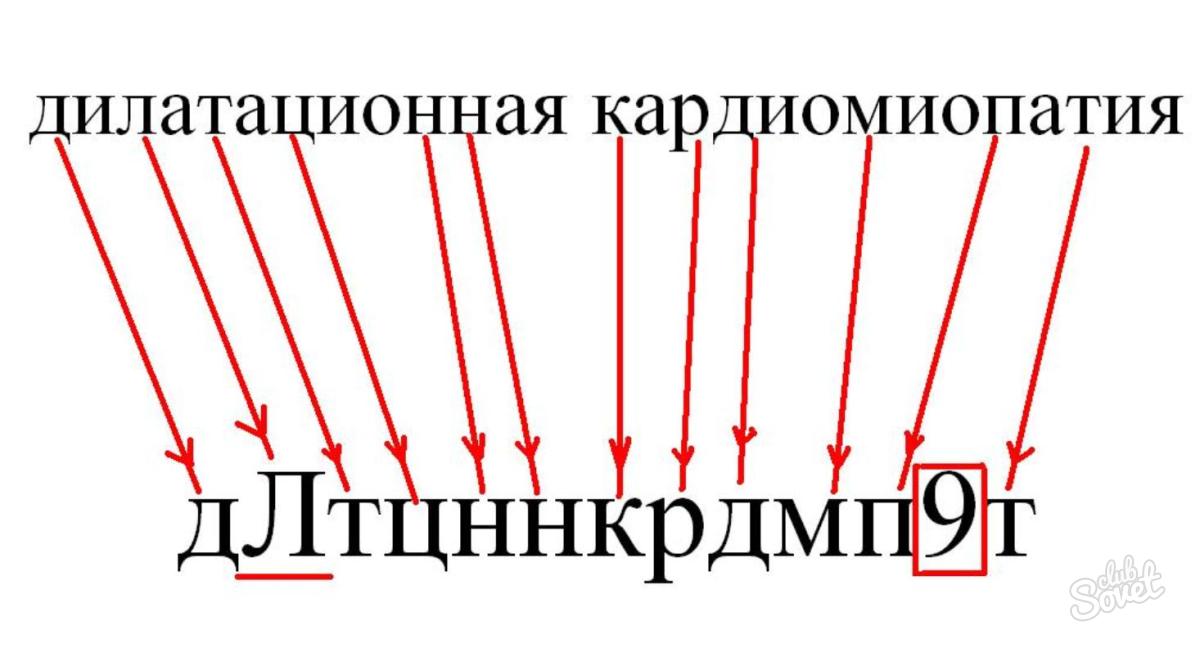
- dLtcnnkrdmp9t - dilated cardiomyopathy;
- dScpktrtrnntfflp8t -discirculatory encephalopathy.
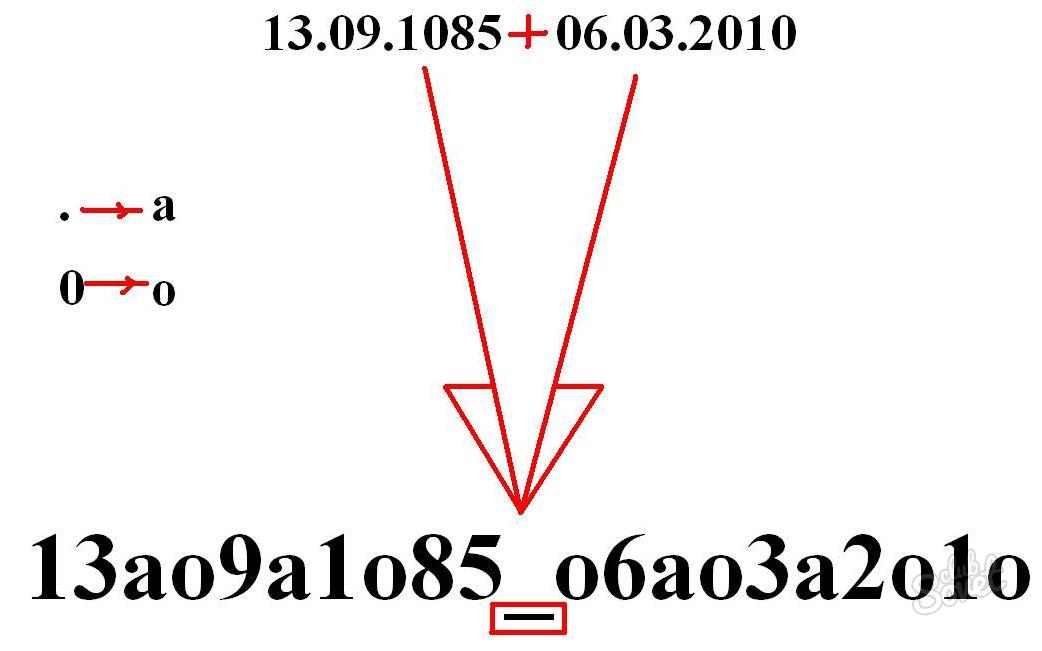

Do not create passwords only from the date of birth, names of close people, nicknames of pets. Of course, they are fairly easy to remember, but such detractors can quickly crack open the password. Be creative - and you will come up with an interesting, reliable and clear only you password, which you will never forget.
Instructions
First, we'll look at the process of hacking passwords. Most people use very simple passwords, such as a set of numbers. Such passwords have the lowest degree of protection against hacking. For cracking passwords, special programs are used. Modern hacking programs run at a speed of 500,000 passwords per second. For example, if your password consists of six digits, then such a password will be cracked in two seconds. How to protect against this type of attack, when all sorts of passwords are being moved at such huge speeds. In fact, it's easy.
First, you need to use long passwords. They must contain at least 15 characters. Such a password will be hacked for tens of years, given the state of the art. This is quite acceptable for us.
Secondly, the password should contain not only numbers, but also letters, spaces, different signs. Take the word "attraction" as an example. This word contains 21 letters. The hacking program will work on such a password for trillions of years.
However, crackers have special dictionaries containing all the words of the Russian language. Let's say 200000 words in the Russian dictionary. The hacking program runs at a speed of 500,000 words per second. It's not hard to count, after how many seconds your password is cracked, it's less than a second. Therefore, do not use the words of the Russian language, and not only Russian, as a password.
The quality of the password depends on two values, this is the length of the password and the variety of characters. Under the symbols understand, capital and capital letters, numbers, spaces or special signs. The richer the variety of characters in the password, the harder it is to crack. But such passwords are harder to remember. Therefore, it is better to create easily remembered passwords. For example, take a word or better a few words and intentionally make a few mistakes. Such a password will have a greater degree of protection.
Hacking your password is very difficult for a number of reasons, such as speed limits, limiting the number of acceptable errors when entering a password, and a number of others. But if an intruder gets access directly to your computer and downloads his programs for hacking, then you will need the password, which we mentioned above.
The procedure for setting a password is very simple. When the computer boots, press and hold the Delete button, this is the BIOS input. In the menu, find Password and enter the password, then press F10, and in the opened window, Yes. The password is set. Be sure to memorize it or write it down, since when you lose it, you do not start the computer. This is the most reliable protection of your computer to date.
Everyone who actively works on the Internet, is constantly forced to register on various services, in in social networks, on some sites. Everywhere you need to enter passwords, so you need to create them as reliable as possible. That's just how it should be? How to create such a password , which will be long.
Rules for creating a strong password
The best option is to use a special random password generator program. To this software can be attributed and Keepass. The disadvantage of this program is that it is very difficult to remember the generated password, it must be constantly recorded. And many users just do not want to mess with it. So, you need to create passwords that are easy to remember, but very difficult to crack. Software products that store passwords will definitely not save everything, some will have to be remembered.
What you need to remember when creating a password
- Use classical combinations of words can not. First of all, the program will check the dictionary and digital combinations
- Any personal information, such as a birthday, car license plates, names of relatives or friends, is strictly prohibited.
- Do not use standard phrases, words, or their combinations to create a password.
- When creating a password, you must use at least 10 characters, optimally 18 or 24.
- When creating a password, you need to use big and small letters, numbers, special characters, for example: u # kcG8Z4 * s when using a combination of Latin and Russian layouts
- When creating a password, you should include fantasy. Never a computer will not pick up a password that is created simply from nowhere. Such passwords are very difficult to crack even for special programs, and password selection can last for months.
How to come up with a strong password
The first step in creating any password is to create a key phrase. The best option is to use fantasy and create a completely meaningless phrase. After you need this phrase, while creating a very strong password. There are many methods that are worth exploring in more detail:
- Using a combination of Latin and Russian layouts at the same time or writing a phrase in Russian using a Latin layout
- Twist the phrase by writing it the other way round. It's pretty hard to do, but hacking such a password is much more difficult
- Replace letters with their similar symbols: a - @, o - ()
- In the password, insert a few letters from each phrase, and do it better in trivial form
- It is possible with a phrase to delete specific symbols, consonants or pairs, there are a lot of options
- Use special characters.
You can simultaneously use several of these combinations at once, completely changing the phrase into a meaningless set of letters. I recommend every person who often uses passwords to come up with their own encryption, which can be used in different services.
If there is a desire, you can create your own password, which is created from various encryption models. For example, cosmic ants - kosmtara - rjcvnfhf - Rjcvnfhf @ 955. And now the attentive user will notice the feature of this password: the first 4 characters of each word are selected, written together and on the English keyboard. We add special characters and any number. And as a result we get a fairly reliable and original password , which is easy to remember and restore.
To check the reliability of the password, you can use the service passwordmeter.com, through which you can check the reliability of the password.
When creating a password, you absolutely must abandon the standard thinking, work in an original way and not standard. This is the only way to create such a password, for breaking it you will have to sweat a special software for a long time.
Computer security experts from Cambridge University have analyzed the structure of more than 70 million passwords. And found out that the most complex passwords in the world are users from Germany and Korea. And they do it naturally and naturally, without special training. And the secret of the stability of combinations lies in the specificity of their language. They apply the same Latin symbols, the same numbers, but take as their basis their native "difficult" words - names, place names, terms, etc. For example, Annaberg-Buchholz # 122. To think up, remember these options is easy, but to pick up an order of magnitude more difficult compared to the vocabulary words of other languages.
If you, the dear reader, do not know Korean or German, this of course does not mean that you should ignore complex passwords. They are the guarantee of the security of your data on the Internet (in online payment systems, on sites, forums). This article will tell you how to meet the requirements for the key to access the account (what it should be) and how to create it.
Definition of complexity
The complexity of the key is a measure of resistance to selection at the symbolic level through manual and automated methods (logical computation, dictionary selection). It is determined by the number of cracker attempts, that is, how much time it takes to compute the user-generated combination.
The complexity of the password is influenced by the following factors:
- The number of characters in the key. The more characters in the sequence, the better. A combination of 5 characters has a high probability of rapid hacking. But the selection of a sequence of 20 characters can take years, decades and even centuries.
- Alternation of uppercase and lowercase letters. Examples: the dfS123UYt key using the capitalization register is an order of magnitude more complex than the same combination, but only with small letters - dfs123uyt.
- Character sets. A variety of types of characters enhances stability. If you make a key of small and large letters, numbers and special characters of 15-20 characters in length, there is practically no chance to find it.
How to make stable combinations?
The following methods will help you come up with a very complex character key that is easy to remember.
1. Create visually contours of a geometric figure or an object on the keyboard of your computer. And then type the symbols on which the lines pass.

Attention! Avoid simple "designs" - lines, squares or diagonals. They are easy to predict.
2. Compose a complex sentence that does not lend itself to logic. In other words, some pun:
For example: Cat Vaska on Jupiter caught a pike.
Then take the first 2-3 letters of each word from the proposed sentence:
Cat + Ba + Na + Yup + ul + pike
Type syllables in Latin letters:
Rjn + Df + Yf +\u003e g + ek + oer
After transliteration, insert between the syllables some familiar numbers: date of birth, height, weight, age, last or first digit of the phone number.
Rjn066Df 45Yf 178\u003e g 115ek1202oer
That's all! As you can see, it turned out to be a fairly "strong" combination. To remember it quickly, you only need the key (sentence-pun) and the numbers used.
3. Take as a basis 2 memorable dates. For example, two birthdays (yours and your loved one).
12.08.1983 05.01.1977
Divide the number, month and year by any special characters:
12|08/1983|05\01|1977
Now replace the zeros in the dates with a small letter "o".
12 | o8 / 1983 | o5 | o1 | 1977
It turns out quite an intricate key.
4. Make a special table: vertically and horizontally, place the letters and numbers in the matrix, and in the rows and columns - the symbols in a chaotic order.
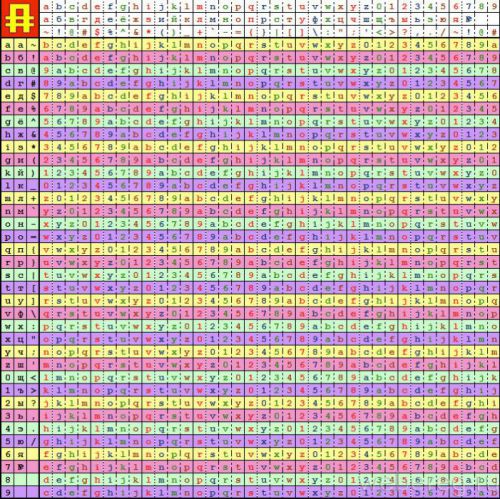
To generate the key, take a few simple words written in English letters, for example, my password very strong
Take the first pair of letters. In our case this is "my". In the vertical list, find "m", in the horizontal "y". At the intersection of the lines you get the first character of the password.
In the same way, through the following pairs, find the rest of the key symbols.
If you forget the password, use a simple keyword and a table to restore it.
How can I check the password strength?
The stability of the symbolic combination to selection can be learned on special web-services. Consider the most popular:
Online service from the Kaspersky Lab anti-virus lab. Defines by the character set and the length of the key, how much time it takes to hack it on different computers. After analyzing the sequence, statistics are displayed for search time on the ZX-Spectrum (the legendary 8-bit 80s machine), the Mac Book Pro (2012 models), the Tianhe-2 supercomputer and the Conficker botnet network.

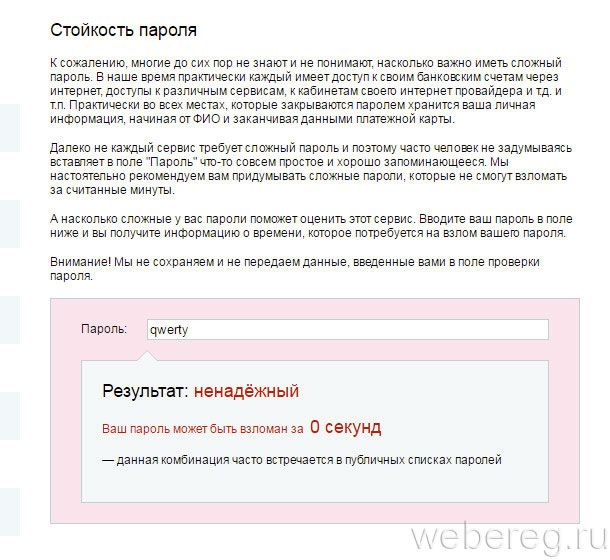
Online utility on the huge service portal 2IP.ru. After sending the key to the server, it gives out its status (reliable, unreliable) and the time it takes to break it.
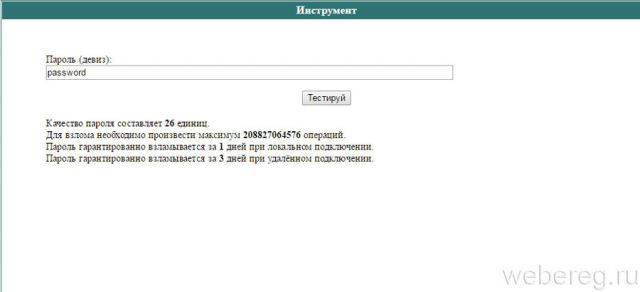
Parolemanager.com/russian/password-tester.html
Gives a detailed description of the key:
- the quality of the sequence, expressed numerically in special units;
- the number of operations required to select;
- time required to compute the combination (locally and remotely).
Successful keying and safe use of the Internet!