Computer ports by the principle of their work are very similar to ordinary ports, the same ones that can be found in any city with a developed water transport infrastructure.
No wonder these two words are homonyms.
From this point of view, a computer seems to be nothing more than a city, or even better a country with many ports, and programs that have access to the Internet are ships with useful or dangerous cargo (anything can happen here).
A computer port and a port as a place on the seashore, in addition to its explicit purpose, also lies in the fact that ships, if their size allows it, can enter different ports, but programs only connect to certain ports.
Many browsers, for example, use port 80, while they can use two ports, namely 25 for sending mail and 110 for receiving.
So, sometimes users have a need to find out which port which program is using. And it's very easy to find out. For these purposes, you can use special utilities like TCPView or the most ordinary command line. Start the console as administrator and run the following command:
netstat /?
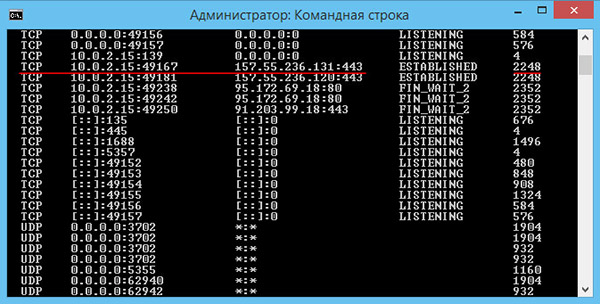
This will open short description commands and a list of available parameters. For example, using netstat with the key -and will list all connections and listening ports, key –O will open access to the ID of each process, and the –b switch will show the executable file involved in creating the connection, which is what we actually need. You can also use the key to view addresses and port numbers –N.
So, we execute the command netstat –a –n –oand see what happened. We got a list of active connections with the protocol, local and external addresses, status and ID. How to find out, for example, which file ID 2248 belongs to? You can expand the command by adding a key to it –B or immediately execute another command tasklist | find "2248"... It's that simple.
Uses program (or what program uses ports), usually occurs in case of suspicion of a computer infection trojan horse... If you notice something suspicious, open a command prompt: "Start" - "All Programs" - "Accessories" - "Command Prompt".
Enter in command line the tasklist command and press Enter. You will receive data on all processes running in the system. Pay attention to the PID - process identifier. He will help determine which program uses this or that port.
Type netstat –aon at a command prompt and press Enter. You will see a list of current connections. The “Local address” column at the end of each line contains the port number. The PID column contains process identifiers. After looking at the port number and the corresponding PID, go to the list of processes and use the identifier number to determine which process is using this port.
If you cannot understand by the name of the process which program it belongs to, use one of the programs that are suitable in this case. For instance, everest program, aka Aida64. Run the program, open the tab " operating system", Select" Processes ". In the list of processes, find the one you need and look at the line for starting it. This will help determine which program the process belongs to.
Use AnVir Task Manager for the same purpose. It allows you to track all suspicious processes, including the processes of programs that connect to the Internet. All suspicious processes are highlighted in red in the program list.
If you see that the port is being used by an unknown program, then if there is a current connection in the "External address" column (netstat –aon command), you will see the ip-address of the computer with which the connection is established. The “Status” column will contain the ESTABLISHED value - if the connection is present at the current moment; CLOSE_WAIT if the connection is closed; LISTENING if program waiting for a connection. The latter is typical for backdoors, a type of Trojan horse.
The software port is a conditional number from 1 to 65535 that indicates which application the data packet is addressed to. The port that works with the program is called open. It should be borne in mind that at the moment any port can only work with one program.
If the port is open, this means that some program (for example, a service) uses it to communicate with another program via the Internet or local system... To see which ports are open in your linux system you can use the netstat command. The output will show all services and the ports and ip addresses they are listening to.
sudo netstat -ntulp Active Internet connections (only servers)
Proto Recv-Q Send-Q Local Address Foreign Address State PID / Program name
tcp 0 0 0.0.0.0:139 0.0.0.0:* LISTEN 2392 / smbd
tcp 0 0 0.0.0.0:9518 0.0.0.0:* LISTEN 2894 / skype
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN 2896 / vlc
tcp 0 0 127.0.0.1:3493 0.0.0.0:* LISTEN 2467 / upsd
...
- -l or -listening - show only listening ports
- -p or -program - show the name of the program and its PID
- -t or -tcp show tcp ports
- -u or -udp show udp ports
- -n or -numeric show ip addresses in numeric form
Method 2 lsof
The lsof utility allows you to see all open connections in the system, including network connections, for this you need to use the i option.
dhcpcd 2136 root 6u IPv4 4986 0t0 UDP *: bootpc
hamachid 2323 root 8u IPv4 5587 0t0 TCP 192.168.1.2:35445-\u003e212.118.234.65:https (ESTABLISHED)
smbd 2392 root 27u IPv6 5624 0t0 TCP *: microsoft-ds (LISTEN)
sshd 2421 root 3u IPv4 6196 0t0 TCP *: ssh (LISTEN)
upsd 2467 nut 4u IPv4 6235 0t0 TCP comm-app.local: nut (LISTEN)
Another example, we look at what processes are running on port 80:
sudo lsof -i | grep 80
ntpd 2213 root 23u IPv6 5422 0t0 UDP: ntp
ntpd 2213 root 27u IPv6 5598 0t0 UDP: ntp
skype 2894 serigy 87u IPv4 7080 0t0 TCP *: 9518 (LISTEN)
chrome 3114 sergiy 122u IPv4 31904 0t0 TCP 192.168.1.2:47804-\u003esrv118-131-240-87.vk.com:https (ESTABLISHED)
Method 3.nap
Nmap is a powerful network scanner designed to scan and penetrate remote hosts, but nothing prevents it from being directed to the local machine:
Starting Nmap 6.47 (http://nmap.org) at 2015-08-02 17:27 EEST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.00036s latency).
Other addresses for localhost (not scanned): 127.0.0.1 127.0.0.1 127.0.0.1 127.0.0.1 127.0.0.1 127.0.0.1
rDNS record for 127.0.0.1: comm-app.local
Not shown: 995 closed ports
PORT STATE SERVICE
22 / tcp open ssh
139 / tcp open netbios-ssn
445 / tcp open microsoft-ds
3493 / tcp open nut
8080 / tcp open http-proxy
Nmap done: 1 IP address (1 host up) scanned in 0.10 seconds
If you want to see what ports on the computer are accessible from the outside, Nmap comes in handy here too. If the computer is a public server, then the result most likely will not differ from the local scan, but on home computer everything is a little different. The first option - a router is used and only the ports of the router will be visible to the network, another protection threshold can be the provider's NAT server. NAT technology allows multiple users to share one external IP address. And so, to view the open external ports, we first find out the external ip address, for reliability, we will use the online service:
nmap 178.93.149.50
As a result, we can get open port 80 web servers, or even 21 - file server, which we did not install, these ports are open by the router, 80 for the web interface, and 21 for can be used to update the firmware. Also, you may not get any results at all, this will mean that all ports are closed, or the server has IDS intrusion protection system installed.