Let's create a vivek user and add it to the developers group. Log in as root user:
For example, add a user vivek:
useradd -g users -G admins,ftp,www,developers -s/bin/bash -pxxxx-d/home/ghost -m vivek
- -d home directory
- -s set the start shell (/bin/sh) - after that you can change it in the file /etc/passwd
- -p password
- -g the main group to which the user is assigned (Group must exist)
- -G other groups to which the user belongs
- -m create a home directory for the user
- xxxx character user password
Make sure the developers group exists:
# grep developers /etc/group
If there is no group, use the command groupadd to create a new developers group:
Now with the command usermod add the user vivek to the developers group:
# adduser vivek developers && newgrp developers
Make sure the user is added to the developers group:
# id vivek
output:
uid=1122(vivek) gid=1125(vivek) groups=1125(vivek),1124(developers)
Set/change the password for the vivek user:
Let's play with groups
Indicate the vivek user to participate only in the developers group
usermod-G developers vivek
Instruct the vivek user to only participate in the admins, ftp, www, developers groups by typing:
# usermod -G admins,ftp,www,developers vivek
Remove user vivek from some groups (reassign groups to him):
# usermod -G ftp,www vivek
now vivek is not a member of the admins and developers groups.
Note: team usermod will not change the username if that user is currently logged in.
userdel- delete user
For example, let's delete the user vivek:
- -r delete user along with home directory
Detailed SYNTAX
useradd [-u identifier[-o] [-i]] [-g group][-G group[[,group] . . .]] [-d catalog][-s shell] [-c a comment][-m[-k skel_dir]] [-f inactive] [-e expire][-p passgen][-a event[, . . .]] reg_nameDetailed description
Call useradd usually adds a new user entry to the system data files identification and identity verification(Identification and Authentication - I&A). Users are an exception. network information service(Network Information Service or NIS for short). It also allows you to set membership in additional groups for the user (option -G) and create an initial directory for it (option -m). The new login is blocked until the command is executed. passwd.
Immediately after installation, the default values for various parameters are specified in the file /etc/default/useradd. The default values for those of the options listed below that require default values can be changed with the command defadm.
System file entries created with this command have a length limit of 512 characters per line. If multiple options are given long arguments, this restriction may be violated.
The following options are supported:
| -u identifier | User identification number (UID). This number must be a non-negative integer not greater than MAXUID defined in sys/param.h. The default is the next available (unique) non-legacy UID greater than 99. This option is ignored if the new login will be administered by the Network Information Service (NIS). See the "Network Information Service Registration Names" section below for more details. |
| -o | This option allows you to duplicate the UID (make it non-unique). Since the protection of the system as a whole, as well as the integrity audit trail(audit trail) and accounting information(accounting information) in particular depends on the one-to-one correspondence of each UID to a certain person, it is not recommended to use this option (to ensure that user actions are accounted for). |
| -i | Allows the use of a legacy UID. |
| -g group | Integer identifier or symbolic name of an existing group. This option sets main group(primary group) for the new user. By default, the standard group specified in the file is used. /etc/default/useradd |
| -G group[[,group] . . .] | One or more elements in a comma-separated list, each of which is an integer identifier or symbolic name of an existing group. This list defines belonging to additional groups(supplementary group membership) for the user. Repetitions are ignored. The number of elements in the list must not exceed NGROUPS_MAX-1, because the total number of additional groups for a user plus the main group must not exceed NGROUPS_MAX. This option is ignored if the new login will be administered by the Network Information Service (NIS). See "Network Information Service Registration Names" below. |
| -d directory | Home directory(home directory) of the new user. The length of this field must not exceed 256 characters. The default is HOMEDIR/register_name, Where HOMEDIR is the base directory for new users' home directories, and reg_name- the login name of the new user. |
| -s shell | The full path to the program used as the initial shell for the user immediately after login. The length of this field must not exceed 256 characters. By default, this field is empty, which forces the system to use the standard shell /usr/bin/sh. As a value shell an existing executable must be specified. |
| -c comment | Any text string. Usually, this is a short description of the login name and is now used to indicate the last name and first name of the real user. This information is stored in a user record in a file /etc/passwd. The length of this field must not exceed 128 characters. |
| -m | Creates the new user's home directory if it does not already exist. If the directory already exists, the user you add must have permissions to the specified directory. |
| -k skel_dir | Copies the contents of a directory skel_dir to the new user's home directory, instead of the contents of the standard "skeleton" directory, /etc/skel. Catalog skel_dir must exist. The standard "skeleton" directory contains standard files that define the user's work environment. Administrator-defined directory skel_dir may contain similar files and directories created for a specific purpose. |
| -f inactive | The maximum number of days allowed between uses of a login before the login is declared invalid. Typically, positive integers are used as values. |
| -e expire | The date from which the login can no longer be used; after this date, no user will be able to access under this login. (This option is useful when creating temporary logins.) Enter the value of the argument expire(representing a date) can be in any format (except Julian date). For example, you could enter 10/6/99 or October 6, 1999 . |
| -p passgen | Indicates that the FLAG field in the file /etc/shadow must be set to the specified value. This field is accessed by the command passwd to determine if the password generator is valid for the given user. If option -p not explicitly set, the record is checked FORCED_PASS in file /etc/default/useradd to determine the value for the corresponding field in /etc/shadow. If records FORCED_PASS no in /etc/default/useradd, in the corresponding entry field in /etc/shadow there will be no value. If the value FORCED_PASS equals 1, write to /etc/shadow gets the value 1. If the value passgen is not empty and is not an ASCII printable character, a diagnostic message is issued. |
| -a event | List of types or classes of events, separated by commas, forming audit mask(audit mask) for the user. Immediately after the system is installed, there is no standard audit mask for the user, but it can be set in the file /etc/default/useradd using the command defadm. This option can only be used if the Auditing Utilities are installed. (To see which packages are installed on your system, run the command pkginfo.) |
| reg_name | A printable string that specifies the login name for the new user. It should not contain colons ( : ) and newline characters ( \n). It also must not start with an uppercase letter. |
Note that many of the default values for the options discussed above can be changed with the command defadm, designed to work with a file /etc/default/useradd. These default values apply only to local users. For NIS users, the default values are set in the Network Information Service database. To change the default NIS values, you must specify options on the command line.
Network Information Service Registration Names
If the login starts with a character + , (For example, +chris), the user definition will be managed by the Network Information Service (NIS). The default values will be determined based on the NIS database, not the file /etc/defaults/useradd. Option Argument Values -u, -g And -G will be silently ignored if these options are given. Instead, the user ID and group ID values will be taken from the NIS database. See the man page for details passwd. Note that when adding a NIS user, the login must already exist in the NIS database. For example, to add a login Chris as NIS username, Chris must already exist in the NIS database. Then you need to call useradd with login +chris to indicate that a user needs to be added Chris as a NIS user, not as a local user.
FILES
/etc/default/useradd/etc/group
/etc/passwd
/etc/security/ia/ageduid
/etc/security/ia/audit(if auditing utilities are installed)
/etc/security/ia/index
/etc/security/ia/master
/etc/shadow
/etc/skel
DIAGNOSTICS
Team useradd exits with a return code of 0 if successful. When errors occur, the following messages may be issued:
Invalid command line syntax.
The command line syntax was invalid.
An invalid argument was specified in the option.
An invalid argument was provided with an option.
The identifier specified in the -u option is already in use, and the -o option is not specified.
The uid specified with the -u option is already in use and the -o option was not specified.
The group specified with the -g option does not exist.
The group specified with the -g option does not exist.
The login name specified is not unique.
The specified login is not unique.
Failed to modify /etc/group. The login is added to the /etc/passwd file, but not to the /etc/group file.
Cannot update /etc/group. The login was added to the /etc/passwd file but not to the /etc/group file.
Failed to create home directory (in -m option) or failed to copy skel_dir to home directory.
Unable to create the home directory (with the -m option) or unable to complete the copy of skel_dir to the home directory.
The identifier is not old enough. Choose another.
uid not aged sufficiently. Choose another.
An invalid -a option was specified; system service is not installed.
An invalid option -a was specified; system service not installed.
An invalid audit event type or class was specified.
An invalid audit event type or class event was specified.
The basis of the distribution of access rights in the Linux operating system lies on the concept of a user. The user who owns the file is given certain permissions to work with it, namely to read, write and execute. Read, write, and execute permissions for all other users are also set separately. Since in Linux everything is a file, such a system allows you to control access to any action in this operating system by setting file permissions. But even when creating Linux, the developers realized that this was clearly not enough.
That's why user groups were invented. Users can be combined into groups so that groups can already be given the necessary permissions to access certain files, and, accordingly, actions. In this article, we will look at user groups in Linux, consider why they are needed, how to add a user to a group and manage groups.
As I said, groups in Linux appeared at the very beginning of the development of this operating system. They were designed to enhance rights management. Let's analyze a small example, let's take an organization in which there is only one computer, we have administrators and users. Each person has their own account on our computer. Administrators can configure the system, but it is better for users not to give free rein so that something is not broken. Therefore, administrators are united in the admin group, and it is given access to all equipment, in fact, to all the files in the dev directory, and users, united in the users group, and this group is given the opportunity to read and write files to a common directory, with which they can share the results of your work. We could assign rights for each user separately, allowing him access to a particular file, but this is too inconvenient. That's why groups were invented. Say, yes, nothing, you can appoint? Well, now imagine that our users are processes. This is where the beauty of groups comes to the fore, groups are used not so much to provide access for users, but to control the rights of programs, especially their access to equipment. For services, separate groups are created and the user on whose behalf it is launched, the service can be in several groups, which provides it with access to certain resources.
Now let's look at how to view linux groups.
Groups in Linux
All groups created on the system are located in the /etc/group file. By looking at the contents of this file, you can find out the list of linux groups that are already on your system. And you will be surprised.
In addition to the standard root and users, there are a couple dozen more groups here. These are groups created by programs to control the access of these programs to shared resources. Each group allows reading or writing of a specific file or directory on the system, thereby regulating the permissions of the user, and hence the process running under that user. Here we can consider that the user is the same as the process, because the process has all the rights of the user from which it is launched.
Let's take a closer look at each of the groups in order to better understand why they are needed:
- daemon- on behalf of this group and the daemon user, services are launched that need the ability to write files to disk.
- sys- group provides access to kernel sources and include files saved in the system
- sync- allows you to execute the /bin/sync command
- games- allows games to write their settings files and history to a specific folder
- man- allows you to add pages to the /var/cache/man directory
- lp- Allows the use of parallel port devices
- mail- allows you to write data to mailboxes /var/mail/
- proxy- used by proxy servers, no access to write files to disk
- www-data- with this group the web server is started, it gives write access to /var/www, where the web document files are located
- list- allows you to view messages in /var/mail
- group- used for processes that cannot create files on the hard disk, but only read, usually used with the nobody user.
- adm- allows you to read logs from the /var/log directory
- tty- all /dev/vca devices allow read and write access to users from this group
- disk- opens access to hard drives /dev/sd* /dev/hd*, we can say that this is an analogue of root access.
- dialout- full access to the serial port
- cdrom- access to CD-ROM
- wheel- allows you to run the sudo utility to elevate privileges
- audio- audio driver control
- src- full access to sources in the /usr/src/ directory
- shadow- allows reading the /etc/shadow file
- utmp- allows writing to files /var/log/utmp /var/log/wtmp
- video- allows you to work with the video driver
- plugdev- allows you to mount external USB devices, CDs, etc.
- staff- allows writing to the /usr/local folder
Now that you know why Linux groups are used and what they are by default, let's take a look at managing Linux groups.
Linux group management
You can also manage groups using the graphical interface. KDE has a Kuser program specifically designed for this, while Gnome does it through system settings. In addition, popular distributions have separate tools such as YaST in OpenSUSE or Ubuntu Settings. But with a graphical interface, I think you'll figure it out. And we will look at managing linux groups through the terminal. First, let's deal with files, and only then with users.
When a file is created, it is assigned the primary group of the user who created it. It's just for example:

Here you can see that the owner of all folders is sergiy and the group is also sergiy. That's right, since these users were created by me. But let's go further:

Here we see that the sd * disk devices are assigned to the disk group, which means that the user in this group can access them. Or another example:

All as we considered in the previous paragraph. But these groups can not only be set by the system, but you yourself can manually change file groups for this there is the chgrp command:
chgrp groupname filename
For example, let's create a test file:
And change the group for it:

If you want to create a linux group, you can do so with the newgrp command:
sudo groupadd test
With users, the situation is a bit more complicated. The user has a main group, it is specified during creation, as well as several additional ones. The main group differs from the usual ones in that all files in the user's home directory have this group, and when it is changed, the group of these directories will also change. Also, this group is received by all files created by the user. Additional groups are needed so that we can allow users to access different resources by adding it to these groups in linux.
Managing Linux groups for a user is done using the usermod command. Consider its syntax and options:
$usermod options Username
- -G- additional groups to add the user to
- -g change primary group for user
- -R remove a user from a group.
You can add a user to a group with the usermod command:
sudo usermod -G -a groupname username
You can add a user to the linux group temporarily with the newgrp command. A new shell will open, and the user will have the necessary permissions in it, but after closing everything will return as it was:
sudo newgrp groupname
For example, let's add our user to the disk group in order to have direct access to hard drives without the sudo command:
sudo usermod -G -a disk sergiy
You can now mount drives without the sudo command:
mount /dev/sda1 /mnt
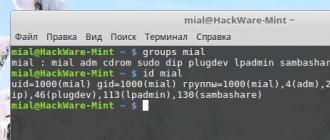
You can view the linux groups in which the user is a member with the command:

You can also use the id command. In the first case, we simply see a list of linux groups, in the second, the group and user id are additionally specified. To include a user in a Linux group, the -g option is used for the primary group.
Original: Linux Fundamentals
Author: Paul Cobbaut
Publication date: October 16, 2014
Translation: A.Panin
Date of transfer: December 23, 2014
Chapter 29 User Groups
System user accounts can be grouped together. The concept of user groups allows you to set access rights at the level of user groups instead of setting similar access rights for each individual user.
Every Unix or Linux distribution has a GUI tool for managing user groups. Users who do not have experience with these systems are advised to use these tools. More advanced users can use CLI tools to manage user accounts with caution: some distributions do not allow both GUI and CLI user group management tools to work at the same time (an example is the YaST tool from the Novell distribution). Suse). Experienced system administrators can directly edit the relevant files using the vi text editor or the vigr utility.
groupadd utility
User groups can be created using the groupadd utility. The example below shows how to create five groups (without adding users to them). [email protected]:~# groupadd tennis [email protected]:~# groupadd football [email protected]:~# groupadd snooker [email protected]:~# groupadd formula1 [email protected]:~# groupadd salsa
group file
Users can belong to multiple groups. Membership of users in groups is described in the /etc/group file. [email protected]:~# tail -5 /etc/group tennis:x:1006: football:x:1007: snooker:x:1008: formula1:x:1009: salsa:x:1010: [email protected]:~#
The first field on the user group description line is the group name. The second field contains the (encrypted) password of the group (this field can be empty). The third field contains the group ID or GID value. The fourth field is the list of group members, which in this case is empty because there are no users in the groups.
groups command
The user can issue the groups command to see the list of groups he is a member of. $ groups harry sports $
usermod utility
A user's group membership can be changed using the useradd or usermod utility. [email protected]:~# usermod -a -G tennis inge [email protected]:~# usermod -a -G tennis katrien [email protected]:~# usermod -a -G salsa katrien [email protected]:~# usermod -a -G snooker sandra [email protected]:~# usermod -a -G formula1 annelies [email protected]:~# tail -5 /etc/group tennis:x:1006:inge,katrien football:x:1007: snooker:x:1008:sandra formula1:x:1009:annelies salsa:x:1010:katrien [email protected]:~#
Exercise caution when using the usermod utility to add users to groups. By default, the usermod utility will remove the user from all groups in which he was a member, if the names of these groups were not passed as part of the command! Using the -a (append) option avoids this behavior.
groupmod utility
You can change the user group name using the groupmod utility. [email protected]:~# groupmod -n darts snooker [email protected]:~# tail -5 /etc/group tennis:x:1006:inge,katrien football:x:1007: formula1:x:1009:annelies salsa:x:1010:katrien darts:x:1008:sandra
groupdel utility
You can permanently delete a user group using the groupdel utility. [email protected]:~# groupel tennis [email protected]:~#
gpasswd utility
You can also delegate control over membership in a specific user group to another user using the gpasswd utility. In the example below, we delegate the rights to add users to the sports group and remove them from it to the user serena. We then use the su command to add the user harry to the sports group on behalf of the user serena. # gpasswd -A serena sports # su - serena $ id harry uid=516(harry) gid=520(harry) groups=520(harry) $ gpasswd -a harry sports Add user harry to the sports group $ id harry uid=516( harry) gid=520(harry) groups=520(harry),522(sports) $ tail -1 /etc/group sports:x:522:serena,venus,harry $
User group administrators are not required to be members of these groups. They can remove their accounts from the user groups they administer without affecting their ability to add users to or remove users from those groups. $ gpasswd -d serena sports Remove the user serena from the sports group $ exit
Information about user group administrators is stored in the /etc/gshadow file. # tail -1 /etc/gshadow sports:!:serena:venus,harry #
To remove all administrator accounts from a user group, use the gpasswd utility with options to specify an empty list of administrators. # gpasswd -A "" sports
newgrp utility
You can start a child shell with the user's new temporary primary group using the newgrp command. [email protected]:~# mkdir prigroup [email protected]:~# cd prigroup/ [email protected]:~/prigroup# touch standard.txt [email protected]:~/prigroup# ls -l total 0 -rw-r--r--. 1 root root 0 Apr 13 17:49 standard.txt [email protected]:~/prigroup# echo $SHLVL 1 [email protected]:~/prigroup# newgrp tennis [email protected]:~/prigroup# echo $SHLVL 2 [email protected]:~/prigroup# touch newgrp.txt [email protected]:~/prigroup# ls -l total 0 -rw-r--r--. 1 root tennis 0 Apr 13 17:49 newgrp.txt -rw-r--r--. 1 root root 0 Apr 13 17:49 standard.txt [email protected]:~/prigroup# exit exit [email protected]:~/prigroup#
vigr utility
Similar to the vipw utility, the vigr utility can be used to manually edit the /etc/group file, as it locks the file gracefully during editing. The vi text editor or the vigr utility can only be used by experienced system administrators to manage user groups.
Practice Activity: User Groups
Correct Practice Procedure: User Groups
1. Create the tennis, football, and sports user groups.
groupadd tennis ; groupadd football ; groupadd sports
2. With a single command, make the user venus a member of the tennis and sports groups.
Usermod -a -G tennis,sports venus
3. Rename the user group fotball to foot.
Groupmod -n foot football
4. Use the vi text editor to add the user serena to the tennis user group.
5. Use the id command to verify that the user serena is a member of the tennis user group.
Id (after logging out and logging in, the user serena must be a member of the group)
6. Make a user responsible for managing user memberships in the foot and sports groups. Check the functionality of the mechanism used.
gpasswd -A (to make a user responsible for managing user group membership) gpasswd -a (to make a user a member of a user group)
I touched on the issues of user membership in a group, as well as the fact that users and groups have their own UID And GID. The topic of about was also raised. Today I would like to systematize knowledge about local user base in Linux, how manage users and about files responsible for user management.
Linux is a multi-user operating system. Every user in linux belongs to one core group and one or more additional groups. In Linux, as in most other operating systems, working with users consists of a set of the following manipulations: adding user/group, deleting user/group, modifying user/group settings. These manipulations are performed using the commands: useradd, groupadd, userdel, groupdel, usermod, groupmod, and passwd gpasswd id. In more detail: There are also graphical user administration tools, usually located in the X shell under Administration - Users and Groups.
Features of user management in Linux
An example of adding a user using a shell:
User-add-server:~# groupadd test user-add-server:~# useradd -c "Test Test" -g test -m test user-add-server:~# passwd test Enter new UNIX password: Retype new password UNIX: passwd: password updated successfully user-add-server:~# id test uid=1001(test) gid=1001(test) groups=1001(test) user-add-server:~# ls -ld /home/test / drwxr-xr-x 2 test test 4096 Dec 16 10:24 /home/test/ user-add-server:~#
In the example, we add a group for the new user (groupadd), then we create a new user with the full name Test Test, which has the main group test and the login test, then we set a password for the user test (passwd test) and check the parameters of the created user (id and created directory user /home/test/). The listing shows that UID and GID are more than 1000. This feature is a sign ordinary user. Values below (less than) 1000 (or less than 500 on some distributions) indicate that the user is system user.
According to the agreement, system users usually have an id less than 100, and root user has id equal to 0. Automatic numbering of ordinary users starts from values UID_MIN set in the file /etc/login.defs, this value is usually set to 500 or 1000.
Apart from regular user accounts and user account root, usually there are several special purpose accounts for daemons like FTP, SSH, mail, news, etc. These accounts often manage files, but they cannot be accessed through regular login. Therefore, they usually have login shell defined as /sbin/nologin or /bin/false so that login attempts fail.
On some systems, the add user command(s) has extended functionality. That is, for example, the useradd command in Fedora and Red Hat distributions by default creates a new group for a new user, and to cancel this function, you must use the -n option. For clarification of such issues, please refer to the documentation of the distribution.
When a user is deleted, their directory is not deleted. As a result, you can get an interesting situation:
User-add-server:~# userdel test user-add-server:~# groupdel test user-add-server:~# ls -ld /home/test/ drwxr-xr-x 2 1001 1001 4096 Dec 16 10:24 /home/test/ user-add-server:~# groupadd test123 user-add-server:~# useradd -c "Test Test" -g test123 -m test123 user-add-server:~# ls -ldn /home/ test* drwxr-xr-x 2 1001 1001 4096 Dec 16 2:30 pm /home/test drwxr-xr-x 2 1001 1001 4096 Dec 16 2:29 pm /home/test123 user-add-server:~# ls -ld / home/test* user-add-server:~# ls -ld /home/test* drwxr-xr-x 2 test123 test123 4096 Dec 16 10:24 /home/test drwxr-xr-x 2 test123 test123 4096 Dec 16 14 :25 /home/test123 user-add-server:~# passwd test123 Enter new UNIX password: Retype new UNIX password: passwd: password updated successfully user-add-server:~# su -l test123 [email protected]:~$ pwd /home/test123 [email protected]:/home/mc-sim$ ls /home/ mc-sim test test123 [email protected]:~$ cd /home/mc-sim/ [email protected]:/home/mc-sim$ ls -la total 24 drwxr-xr-x 2 mc-sim mc-sim 4096 Nov 15 12:31 pm . drwxr-xr-x 6 root root 4096 Dec 16 14:25 .. -rw------- 1 mc-sim mc-sim 99 Nov 15 13:45 .bash_history -rw-r--r-- 1 mc-sim mc-sim 220 Oct 1 17:42 .bash_logout -rw-r--r-- 1 mc-sim mc-sim 3116 Oct 1 17:42 .bashrc -rw-r--r-- 1 mc- sim mc-sim 675 Oct 1 17:42 .profile [email protected]:/home/mc-sim$ rm /home/mc-sim/.bash_logout rm: delete write-protected regular file `/home/mc-sim/.bash_logout"? y rm: cannot delete `/home/mc-sim /.bash_logout": Permission denied [email protected]:/home/mc-sim$ rm /home/test/.bashrc [email protected]:/home/mc-sim$
In the given example, we delete user and group test created earlier. At the same time, the directory of this user remained untouched. As you can see from the listing, the rights of the directory remained for id 1001. Next we create a new user and group, but with a different name - test123. This user is assigned UID And GID- previously existing user test. Looking at the list of directories starting with /home/test* with key -n and without it, we see what happened - the user directory test became owned by the user test123 what permissions tell us -rw-r--r-- test123 test123. Login as user test123 and to check permissions, in the directory /home/test try to delete the file, and also try to delete the file from the directory of the third user - mc-sim. This example illustrates well that in Linux everything is tied to identifiers.
Managing user and group databases in Linux
The main files containing user and group information are the four files in the directory /etc.
/etc/passwd
password file containing basic information about users
/etc/shadow
shadow encrypted password file containing encrypted passwords
/etc/group
groups file containing basic information about groups and users belonging to these groups
/etc/gshadow
shadow group file containing encrypted group passwords
It is not recommended to edit these files with a regular text editor. They (files) are updated when the above commands are executed, and when they change, they are blocked and synchronized.
If, nevertheless, there is an urgent need to edit the specified files, then using the command vipw it is safe to edit the file /etc/passwd, and using the vigr command it is safe to edit the file /etc/group. These commands will lock the required files while the changes are made with the help. If you make changes to a file /etc/passwd, team vipw prompts you to check if you need to update the file /etc/shadow. Likewise, if you update the file /etc/group using the vigr command, you will be prompted to update and the file /etc/gshadow. If you need to remove group administrators, you must use the command vigr because the command gpasswd only allows you to add administrators.
Please note that in modern systems, passwd and group files do not store passwords in clear text. This is done for security reasons. themselves passwd and group files must be readable by everyone, and encrypted passwords must be unreadable by everyone. That's why encrypted passwords are stored in shadow files, and these files are only readable by the root user. The necessary access to change authentication data is provided by the suid program, which has root user authority but can be run by any user.
FILE /etc/passwd
user-add-server:~# cat /etc/passwd root:x:0:0:root:/root:/bin/bash lp:x:7:7:lp:/var/spool/lpd:/bin/ sh sshd:x:101:65534::/var/run/sshd:/usr/sbin/nologin test123:x:1001:1001:Test Test:/home/test123:/bin/shThe /etc/passwd file contains one line for each user on the system. Each line contains seven fields separated by colons (:), describing the fields using the root user as an example:
| field | meaning | description |
| Username | root | the name used to log in to the system (login) |
| Password | x | user password (if encrypted, character -x is used) |
| user id (UID) | 0 | User ID |
| group id (GID) | 0 | Group ID |
UNIX-like operating systems are multi-user. Users and the groups they belong to are used to control access to system files, directories, and peripherals. By default, linux offers relatively simple access control mechanisms. You can extend them with LDAP and ACL, but in this topic we'll look at the standard access controls.
Users and Groups in Linux
Users:
Business - Internet Access #1.
User is anyone who uses a computer. The user is assigned a name, the name must be unique on the system (linux has reserved names such as "root", "hal", and "adm"). The name can consist of letters of the English alphabet, Arabic numbers and symbols "_" (lower space) «.» (dot).
root(from English root- root; read "root"), a superuser is an account in UNIX-like operating systems with an identifier (UID) of 0, the owner of this account has the right to perform any operation. For security reasons, run as superuser root Not recommended.In addition to the system name, the full name (for example, full name) of a real user can be entered and stored in the system. For example, the real-life user newuser might be a person named John Smith. This information will allow a system administrator to better control and identify users, especially if there are hundreds or even thousands of users in the system.
For each user, a separate directory (home directory) is created. The user enters this directory after he has logged in and the user's personal files and folders are stored in it. All user directories are collected in one place, usually /home.
Also, the user is assigned a command shell (command interpreter used in operating systems of the UNIX family). For example: /bin/bash, /bin/zsh, /bin/sh etc. Many linux distributions have a bash shell by default for users.
Each user is assigned an identification number (User ID). The number is abbreviated as UID, which is a unique user identifier. The operating system keeps track of the user by UID, not by their name.
Also, each user is assigned a password to log into the system. The password is stored in encrypted form (encripted). The passwd command is used to create and change a password. The system administrator can assign a password himself or allow the user to enter his own password at the first authorization.
Each user belongs to at least one or more groups. (users and groups in linux)
Groups:
To differentiate rights in linux, in addition to users, there are groups. Just like a user, a group has access rights to certain directories, files, peripherals (there are reserved groups in the system). For each file, not only the user is defined, but also the group. Groups group users to provide the same permissions for any action.
Each group is assigned an identification number ( group ID). GID is short for a group's unique identifier. A user's membership in a group is set by the administrator.
View Users
(users and groups on linux) All of the above information is stored in the /etc/passwd file. To view the list of users, you need to enter the command:
# cat /etc/passwd
Each account occupies one line. The output might be:
Root:xD928Jhs7sH32:0:0:root:/root:/bin/bash newuser:Xv8Q981g71oKK:1000:100:John Smith:/home/newuser:/bin/bash
This line has the following format:
Account:password:UID:GID:GECOS:directory:shell
account- Username password- encrypted user password UID- user identification number GID- identification number of the user's primary group GECOS- an optional field used to specify additional information about the user (for example, the user's full name) directory- user's home directory ($HOME) shell- user shell (usually /bin/sh)
To view a list of users who are currently in the system, there is the who command.
The output might be:
Newuser pts/0 2013-11-13 14:19 (:0)
Creating, managing and deleting users
(users and groups in linux) When creating new users, a sequence of certain actions is performed. First, an entry is made in the /etc/passwd file, where the user is assigned a unique name, UID, GID, and other information. UID must be greater than 1000 and GID greater than 100, this is due to the fact that the system reserves small values for its own needs. Also, a directory is created, permissions are set, shell initialization files are placed, and configuration files are modified.
In order not to enter this information manually, there is a useradd (or adduser) program. The settings for this program are stored in the /etc/default/useradd file.
# cat /etc/default/useradd
The output is the following:
GROUP=100 HOME=/home INACTIVE=-1 EXPIRE= SHELL=/bin/bash SKEL=/etc/skel CREATE_MAIL_SPOOL=no
It allows you to change the default settings. For example, a directory for users from /home to /home/user or an interpreter from /bin/bash to /bin/sh.
To create a new user, use the useradd command:
# useradd -m -g users -G audio,lp,optical,storage,video,wheel,games,power,scanner -s /bin/bash newuser
Decryption:
# useradd -m -g [primary group] -G [list additional groups] -s [shell] [username]
- -m- creates a home directory, like /home/[username].
- -g- name or number of the user's primary group.
- -G- list of additional groups the user belongs to.
- -s- defines the user's shell.
For more detailed information, use the manual:
#manuseradd
With the chfn command, you can enter or change user account information (name, work phone, work coordinates, etc.) (username - username).
# chfn [-f fullname][-o office][-p workphone][-h homephone][-u][-v]
The passwd command is used to set the password:
If we want to force the user to change the password to his own at the first login, we need to use the command:
# chage -d 0
You can read more about the chage command in the manual, enter:
# man change
There is a userdel command to delete a user.
# userdel -r
The -r option tells the user to delete the home directory and mailbox along with the user.
Group management
To view all groups systems and how user they belong you need to enter the following:
# cat /etc/group
The /etc/group file defines the groups in the system. To see which groups a user belongs to, type:
# groups
The id command shows more detailed information.
# id
To create a new group:
#groupadd
To add a user to a group:
# gpasswd -a
Removing a user from a group:
# gpasswd -d
And in order to delete a group, enter the following:
#groupdel
(users and groups in linux) That's all, in principle, the most basic is stated.