Interview with Alexey Berdnik, head of projects of the department for work with strategic clients at Digital Design
The emergence of virtualization has become an urgent reason for the large-scale migration of most systems to virtual machines. However, there is no guarantee that all cloud resources are counted, and there are no unmonitored virtual machines, unnecessary processes running, or mutual configuration of cloud elements is not violated. What are the threats to cloud computing and how can they be prevented?
- This is a high-level type of threat, since it is associated with the manageability of the cloud as a single information system, and the overall protection for it needs to be built individually. To do this, you need to use a risk management model for cloud infrastructures.
In cloud computing, virtualization technology plays a critical platform role. Known threats to cloud computing include the difficulty of moving cloud servers to the compute cloud. In most traditional data centers, engineers' access to servers is controlled at the physical level; in cloud environments, they operate over the Internet. Therefore, the differentiation of access control and ensuring the transparency of changes at the system level are one of the main criteria for protection.
The threat may be related to the dynamism of the virtual machines. Virtual machines are cloned and can be moved between physical servers. This variability influences the design of a holistic security system. At the same time, vulnerabilities of the operating system or applications in a virtual environment spread uncontrollably and often appear after an arbitrary period of time, for example, when restoring from a backup. Therefore, in a cloud computing environment, it is important to reliably record the state of protection of the system, regardless of its location. For cloud and virtual systems, the risk of hacking and malware infection is quite high. Therefore, an intrusion detection and prevention system must be able to detect malicious activity at the level of virtual machines, regardless of their location in the cloud.
A turned off virtual machine is also at risk of infection, since network access is sufficient to access its image storage. At the same time, it is impossible to enable security software on a turned off virtual machine. This is why protection at the hypervisor level must be implemented. It should also be borne in mind that when using cloud computing, the network perimeter is blurred or even disappears, which leads to a completely different definition of the overall level of network security. It corresponds to the least protected part of it. To differentiate segments with different trust levels in the cloud, virtual machines must provide themselves with protection by moving the network perimeter to the virtual machine itself.
What else are the risks of moving to the cloud?
- Vulnerabilities in operating systems, modular components, network protocols are traditional threats, for protection against which it is enough to install a firewall, firewall, antivirus, IPS and other components that solve this problem. At the same time, it is important that these protections work effectively in a virtualization environment.
There are also functional attacks on cloud elements. To protect them, for each part of the cloud it is necessary to use the following protection means: for a proxy - effective protection against DoS attacks, for a web server - control of page integrity, for an application server - an application level screen, for a DBMS - protection against SQL injection, for data storage systems - correct backups (backup), access control. Separately, each of these defense mechanisms have already been created, but they are not collected together for comprehensive protection of the cloud, so the task of integrating them into a single system must be solved during the creation of the cloud.
We can distinguish the so-called attacks on the client. Since most users connect to the cloud using a browser, there is a risk of password hijacking, web session hijacking, and a host of other similar attacks. The only defense against them is correct authentication and the use of an encrypted connection (SSL) with mutual authentication. However, these protections are not very convenient and very wasteful for cloud creators. There are still many unresolved challenges in this information security industry.
One of the key elements of a virtual system is the hypervisor. Its main function is to share resources between virtual machines. An attack on a hypervisor can result in one virtual machine being able to access the memory and resources of another. It will also be able to intercept network traffic, take away physical resources, and even displace a virtual machine from the server. As standard protection methods, it is recommended to use specialized products for virtual environments, integration of host servers with the Active Directory directory service, use of password complexity and expiration policies, as well as standardization of procedures for accessing host server management tools, and use of the built-in firewall of the virtualization host. It is also possible to disable such frequently unused services as, for example, web access to the virtualization server.
The large number of virtual machines used in the cloud requires management systems that can reliably control the creation, migration, and disposal of virtual machines. Intervention in the control system can lead to the emergence of virtual machines - invisible, capable of blocking some virtual machines and substituting others.
Security threats always generate solutions that can prevent them. Which ones are the most effective?
- One of the most effective ways to protect data is encryption. The provider providing access to the data must encrypt the client's information stored in the data center, and, if unnecessary, irrevocably delete it. During transmission, even encrypted data should only be accessible after authentication. In addition, access to data should be carried out only through reliable protocols AES, TLS, IPsec. Also, higher reliability will be achieved by using tokens and certificates for authentication. When authorizing, it is also recommended to use LDAP (Lightweight Directory Access Protocol) and SAML (Security Assertion Markup Language) for transparent communication between the provider and the identity system. In addition, virtual networks must be deployed using technologies such as VPN (Virtual Private Network), VLAN (Virtual Local Area Network) VPLS (Virtual Private LAN Service).
Coursework by discipline
Information security software and hardware
"Information security in cloud computing: vulnerabilities, methods and means of protection, tools for auditing and incident investigation."
Introduction
1. History and key development factors
2. Definition of cloud computing
3. Reference architecture
4. Service Level Agreement
5. Methods and means of protection in cloud computing
6. Security of cloud models
7. Security audit
8. Investigation of incidents and forensics in cloud computing
9. Threat model
10. International and domestic standards
11. Territorial identity of the data
12. State standards
13. Cloud Security Means
14. Practical part
Output
Literature
Introduction
The growing speed of cloud computing is explained by the fact that for little, in general, money, the customer gets access to the most reliable infrastructure with the required performance without the need to purchase, install and maintain expensive computers. The system reaches 99.9%, which also saves on computing resources. ... And what is more important - almost unlimited scalability possibilities. By purchasing regular hosting and trying to jump over your head (with a sharp surge in load), there is a risk of getting a service that has fallen for several hours. In the cloud, additional resources are available on request.
The main problem of cloud computing is the non-guaranteed level of security of the processed information, the degree of protection of resources and, often, a completely absent regulatory framework.
The purpose of the study will be to provide an overview of the existing cloud computing market and the means to ensure security in them.
cloud computing security information
1. History and key development factors
The idea of what we call cloud computing today was first voiced by J. C. R. Licklider in 1970. During these years he was responsible for the creation of ARPANET (Advanced Research Projects Agency Network). His idea was that every person on earth would be connected to a network from which he would receive not only data but also programs. Another scientist John McCarthy put forward the idea that computing power will be provided to users as a service (service). On this, the development of cloud technologies was suspended until the 90s, after which a number of factors contributed to its development.
The expansion of Internet bandwidth in the 90s did not allow for a significant leap in development in cloud technology, since almost no company and technology of that time was ready for this. However, the very fact of the acceleration of the Internet gave impetus to the early development of cloud computing.
2. One of the most significant developments in this area was the emergence of Salesforce.com in 1999. This company became the first company to provide access to its application through the site. In fact, this company became the first company to provide its software on the basis of software as a service (SaaS).
The next step was the development of a cloud web service by Amazon in 2002. This service made it possible to store information and perform calculations.
In 2006, Amazon launched a service called the Elastic Compute cloud (EC2) as a web service that allowed its users to run their own applications. Amazon EC2 and Amazon S3 were the first cloud computing services available.
Another milestone in cloud computing comes with Google's creation of the Google Apps platform for web applications in the business sector.
Virtualization technologies have played a significant role in the development of cloud technologies, in particular, software that allows you to create virtual infrastructure.
The development of hardware has contributed not so much to the rapid growth of cloud technologies as to the availability of this technology for small businesses and individuals. With regard to technical progress, the creation of multi-core processors and an increase in the capacity of information storage devices have played a significant role in this.
2. Definition of cloud computing
As defined by the US National Institute of Standards and Technology:
Cloud computing (Cloud computing) (EnglishCloud - cloud; computing- computing) is a model for providing ubiquitous and convenient network access as needed to a shared pool of configurable computing resources (e.g. networks, servers, storage systems, applications and services) that can be quickly provisioned and released with minimal management effort and need interaction with a service provider (service provider).
The cloud model supports high service availability and is described by five essential characteristics, three service / service models, and four deployment models.
The programs are launched and display the results of work in a standard web browser window on a local PC, while all applications and their data necessary for work are located on a remote server on the Internet. Cloud computing is called the "cloud computing". In this case, the load between computers included in the "computing cloud" is distributed automatically. The simplest example of cloud computing is p2p networks.
To implement cloud computing, middleware products created using special technologies are used. They serve as an intermediate link between the equipment and the user and provide monitoring of the status of equipment and programs, equal load distribution and timely provision of resources from a common pool. One of these technologies is virtualization in computing.
Virtualization in Computing- the process of representing a set of computing resources, or their logical combination, which gives any advantages over the original configuration. This is a new virtual view of the resources of the constituent parts, not limited by implementation, physical configuration or geographic location. Typically, virtualized resources include computing power and data storage. Scientifically, virtualization is the isolation of computing processes and resources from each other.
An example of virtualization is symmetric multiprocessor computer architectures that use more than one processor. Operating systems are usually configured so that multiple processors appear as a single processor unit. This is why software applications can be written for one logical ( virtual) computational module, which is much easier than working with a large number of different processor configurations.
For especially large and resource-intensive calculations, grid calculations are used.
Grid computing (grid - lattice, network) is a form of distributed computing in which a "virtual supercomputer" is represented as clusters of networked, loosely coupled, heterogeneous computers working together to perform a huge number of tasks (operations, jobs).
This technology is used to solve scientific and mathematical problems that require significant computing resources. Grid computing is also used in commercial infrastructure to solve time-consuming tasks such as economic forecasting, seismic analysis, and the development and study of the properties of new drugs.
From the perspective of a networked organization, the grid is a consistent, open and standardized environment that provides flexible, secure, coordinated separation of computing and storage resources that are part of this environment within a single virtual organization.
Paravirtualization Is a virtualization technique that provides virtual machines with a programming interface similar to, but not identical to, the underlying hardware. The goal of this modified interface is to reduce the time spent by the guest operating system to perform operations that are much more difficult to perform in a virtual environment than in a non-virtualized one.
There are special "hooks" that allow the guest and host to request and acknowledge these complex tasks, which could be done in a virtual environment, but at a significantly slower rate.
Hypervisor ( or Virtual Machine Monitor) - in computers, a program or hardware scheme that provides or allows the simultaneous, parallel execution of several or even many operating systems on the same host computer. The hypervisor also provides OS isolation from each other, protection and security, resource sharing between different running OSes, and resource management.
A hypervisor can also (but does not have to) provide the OS running on the same host computer with the means of communication and interaction with each other (for example, through file exchange or network connections) as if these OSs were running on different physical computers.
The hypervisor itself is in some way a minimal operating system (microkernel or nanokernel). It provides the operating systems running under its control with a virtual machine service, virtualizing or emulating the real (physical) hardware of a particular machine, and manages these virtual machines, allocating and freeing resources for them. The hypervisor allows independent "power on", reboot, "shutdown" of any of the virtual machines with a particular OS. However, an operating system running in a virtual machine under the control of a hypervisor may, but does not have to, "know" that it is running in a virtual machine and not on real hardware.
Cloud service models
The options for providing computing power are very different. Everything related to Cloud Computing is usually called aaS - it stands for simply "as a Service", that is, "as a service", or "in the form of a service."
Software as a Service (SaaS) - the provider provides the client with a ready-to-use application. Applications are accessible from a variety of client devices or through thin client interfaces such as a web browser (such as webmail) or program interfaces. At the same time, the consumer does not control the underlying cloud infrastructure, including networks, servers, operating systems, storage systems, and even individual application settings with the exception of some user application configuration settings.
In the SaaS model, customers pay not to own the software as such, but to rent it (that is, use it via a web interface). Thus, in contrast to the classical software licensing scheme, the customer incurs relatively small recurring costs, and he does not need to invest significant funds for the purchase of software and its support. The periodic payment scheme assumes that if the need for software is temporarily absent, the customer can suspend its use and freeze payments to the developer.
From a developer's point of view, the SaaS model allows you to effectively combat unlicensed use of software (piracy), since the software itself does not reach the end customers. In addition, the SaaS concept can often reduce the cost of deploying and implementing information systems.
Rice. 1 Typical SaaS Layout
Platform as a Service (PaaS) - the provider offers the client a software platform and tools for designing, developing, testing and deploying user applications. At the same time, the consumer does not control the underlying cloud infrastructure, including networks, servers, operating systems and storage systems, but has control over the deployed applications and, possibly, some configuration parameters of the hosting environment.

Rice. 2 Typical PaaS Layout
Infrastructure as a Service (IaaS). - the provider offers the client computing resources for rent: servers, storage systems, network equipment, operating systems and system software, virtualization systems, resource management systems. At the same time, the consumer does not control the underlying cloud infrastructure, but has control over operating systems, storage systems, deployed applications and, possibly, limited control over the choice of network components (for example, a host with firewalls).

Rice. 3 Typical IaaS Layout
Additionally distinguish services such as:
Communication as a Service (Com-aaS) - it is understood that communication services are provided as services; usually it is IP telephony, mail and instant communications (chats, IM).
Cloud data storage- the user is provided with a certain amount of space for storing information. Since information is stored distributed and duplicated, such storages provide a much greater degree of data safety than local servers.
Workplace as a Service (WaaS) - the user, having at his disposal an insufficiently powerful computer, can buy computing resources from the supplier and use his PC as a terminal to access the service.
Antivirus cloud- the infrastructure that is used to process information coming from users in order to timely recognize new, previously unknown threats. Cloud antivirus does not require any unnecessary actions from the user - it simply sends a request for a suspicious program or link. When the danger is confirmed, all the necessary actions are performed automatically.
Deployment models
Among the deployment models, there are 4 main types of infrastructure.
Private cloud - infrastructure intended for use by one organization, including several consumers (for example, divisions of one organization), possibly also by the clients and contractors of this organization. A private cloud can be owned, operated and operated by the organization itself or by a third party (or some combination of these), and it can physically exist both inside and outside the owner's jurisdiction.

Rice. 4 Private cloud.
Public cloud - infrastructure intended for free use by the general public. The public cloud can be owned, operated and operated by commercial, academic, and government organizations (or any combination of these). The public cloud physically exists in the jurisdiction of the owner - the service provider.

Rice. 5 Public cloud.
Hybrid cloud - it is a combination of two or more different cloud infrastructures (private, public or public) that remain unique objects, but are interconnected by standardized or private technologies for transferring data and applications (for example, short-term use of public cloud resources to balance the load between clouds).

Rice. 6 Hybrid cloud.
Public cloud (community cloud) - a type of infrastructure intended for use by a specific community of consumers from organizations with common objectives (eg, mission, security requirements, policies, and compliance with various requirements). A public cloud can be co-owned, operated and operated by one or more community organizations or a third party (or some combination of these), and it can physically exist both within and outside the owner's jurisdiction.

Rice. 7 Description of cloud properties
Basic properties
NIST in its document `The NIST Definition of Cloud Computing` defines the following characteristics of clouds:
On-demand self-service. The consumer has the ability to access the provided computing resources unilaterally as needed, automatically, without the need to interact with the employees of each service provider.
Broad network access. The provided computing resources are available over the network through standard mechanisms for various platforms, thin and thick clients (mobile phones, tablets, laptops, workstations, etc.).
Pooling of resources (Resorce pooling). The computing resources of the provider are pooled to serve many consumers in a multi-tenant model. Pools include a variety of physical and virtual resources that can be dynamically assigned and reassigned to meet customer needs. The consumer does not need to know the exact location of the resources, but they can be located at a higher level of abstraction (for example, country, region, or data center). Examples of these types of resources include storage systems, computing power, memory, network bandwidth.
Rapid elasticity. Resources can be elastically allocated and released, in some cases automatically, to quickly scale in line with demand. For the consumer, the possibilities of providing resources are seen as unlimited, that is, they can be assigned in any quantity and at any time.
Measured service. Cloud systems automatically manage and optimize resources using measurement tools implemented at the abstraction level for different kinds of services (for example, managing external memory, processing, bandwidth, or active user sessions) .Used resources can be tracked and controlled, which provides transparency as for the provider and for the consumer using the service.

Rice. 8 Structural diagram of a cloud server
Pros and cons of cloud computing
Dignity
· The requirements for the computing power of the PC are reduced (an indispensable condition is only the availability of Internet access);
· fault tolerance;
· security;
· High speed of data processing;
· Reduced costs for hardware and software, maintenance and electricity;
· Saving disk space (both data and programs are stored on the Internet).
· Live migration - transfer of a virtual machine from one physical server to another without interrupting the virtual machine and stopping services.
· In late 2010, due to DDoS attacks against companies that refused to provide resources to WikiLeaks, another advantage of cloud computing was revealed. All companies that opposed WikiLeaks were attacked, but only Amazon was immune to these influences, as it used cloud computing. ("Anonymous: serious threat or mere annoyance", Network Security, N1, 2011).
disadvantages
· Dependence of the safety of user data on companies providing cloud computing services;
· Permanent connection to the network - to gain access to the services of the "cloud" you need a permanent connection to the Internet. However, in our time, this is not such a big drawback, especially with the advent of 3G and 4G cellular technologies.
· Software and its modification - there are restrictions on software that can be deployed on the "clouds" and provided to the user. The software user has limitations in the software used and sometimes does not have the ability to customize it for his own purposes.
· Confidentiality - the confidentiality of data stored on public "clouds" is currently a matter of much controversy, but in most cases experts agree that it is not recommended to store the documents most valuable for the company on the public "cloud", since currently there is no technology that would guaranteed 100% confidentiality of stored data, which is why the use of encryption in the cloud is a must.
· Reliability - with regard to the reliability of the stored information, we can say with confidence that if you have lost information stored in the "cloud", then you have lost it forever.
· Security - the "cloud" itself is a fairly reliable system, however, when penetrating it, an attacker gains access to a huge data storage. Another disadvantage is the use of virtualization systems, which use standard OS kernels as a hypervisor, such as Linux, Windows and others, which allows the use of viruses.
· High cost of equipment - to build its own cloud, a company needs to allocate significant material resources, which is not beneficial to newly created and small companies.
3. Reference architecture
The NIST Cloud Computing Reference Architecture contains five main actors - the actors. Each actor plays a role and performs actions and functions. The reference architecture is presented as sequential diagrams with increasing levels of detail.

Rice. 9 Conceptual diagram of a reference architecture
Cloud Consumer- a person or organization maintaining a business relationship and using the services of Cloud Providers.
Cloud Consumers are divided into 3 groups:
· SaaS - uses applications to automate business processes.
PaaS - develops, tests, deploys and manages applications deployed in the cloud environment.
· IaaS - creates, manages IT infrastructure services.
Cloud Provider- the person, organization or entity responsible for the availability of the cloud service to Cloud Consumers.
SaaS - Installs, manages, maintains, and delivers software deployed on a cloud infrastructure.
PaaS - Provides and manages cloud infrastructure and middleware. Provides development and administration tools.
· IaaS - provides and maintains servers, databases, computing resources. Provides a cloud structure to the consumer.
The activities of Cloud Providers are divided into 5 main typical actions:
Service Deployment:
o Private cloud - Served by one organization. The infrastructure is managed both by the organization itself and by a third party and can be deployed both by the Provider (off premise) and by the organization (on premise).
o Shared cloud - the infrastructure is shared by several organizations with similar requirements (security, compliance with RD).
o Public cloud - the infrastructure is used by a large number of organizations with different requirements. Off premise only.
o Hybrid cloud - infrastructure combines different infrastructures on the basis of similar technologies.
Service management
o Service level - defines the basic services provided by the Provider.
§ SaaS is an application used by the Consumer by accessing the cloud from special programs.
§ PaaS - containers for consumer applications, development and administration tools.
§ IaaS - computing power, databases, fundamental resources on top of which the Consumer deploys his infrastructure.
o Level of abstraction and resource control
§ Management of the hypervisor and virtual components required to implement the infrastructure.
o Level of physical resources
§ Computer equipment
§ Engineering infrastructure
o Availability
o Confidentiality
o Identification
o Security monitoring and incident handling
o Security policies
Privacy
o Protection of the processing, storage and transfer of personal data.
Cloud Auditor- A contributor who can independently evaluate cloud services, information systems maintenance, performance and security of a cloud implementation.
It can give its own assessment of security, privacy, performance and other things in accordance with the approved documents.

Rice. 10 Provider activities
Cloud Broker- the entity that manages the use, performance and delivery of cloud services, and establishes the relationship between Providers and Consumers.
With the development of cloud computing, the integration of cloud services may be too difficult for the consumer.
o Service mediation - expanding the specified service and providing new opportunities
o Aggregation - combining various services to provide the Consumer
Cloud Communication Operator- an intermediary providing connection services and transport (communication services) delivery of cloud services from Providers to Consumers.
Provides access through communication devices
Provides a level of connection, according to the SLA.
Among the five actors presented, a cloud broker is optional, since cloud consumers can receive services directly from the cloud provider.
The introduction of actors is due to the need to work out the relationships between the subjects.
4. Service Level Agreement
A service level agreement is a document describing the level of service delivery expected by a customer from a supplier, based on the metrics applicable to a given service, and setting out the provider's responsibility if the agreed metrics are not met.
Here are some indicators, in one form or another, found in operator documents:
ASR (Answer Seizure Ratio) - a parameter that determines the quality of a telephone connection in a given direction. ASR is calculated as a percentage of the number of telephone connections established as a result of calls to the total number of calls made in a given direction.
PDD (Post Dial Delay) - parameter defining the period of time (in seconds) elapsed from the moment of the call to the moment of establishing the telephone connection.
Service availability ratio- the ratio of the interruption time in the provision of services to the total time when the service is to be provided.
Packet loss ratio- the ratio of correctly received data packets to the total number of packets that were transmitted over the network for a certain period of time.
Time delays in the transmission of information packets- the time interval required to transfer a packet of information between two network devices.
Reliability of information transfer- the ratio of the number of erroneously transmitted data packets to the total number of transmitted data packets.
Periods of work, time of notification of subscribers and time of restoration of services.
In other words, 99.99% service availability means that the operator guarantees no more than 4.3 minutes of communication downtime per month, 99.9% - that the service may not be provided for 43.2 minutes, and 99% - that the break can last more than 7 hours. In some practices, there is a differentiation of network availability and a lower value of the parameter is assumed - outside working hours. Different values of indicators are also provided for different types of services (traffic classes). For example, the most important thing for voice is the latency rate - it should be minimal. And the speed for it needs low, plus some of the packets can be lost without quality loss (up to about 1%, depending on the codec). For data transmission, speed comes first, and packet loss should tend to zero.
5. Methods and means of protection in cloud computing
Confidentiality must be ensured throughout the chain, including the cloud provider, the consumer, and the communications that link them.
The Provider's task is to ensure both physical and software integrity of data from third parties' attacks. The consumer must put in place appropriate policies and procedures "on their territory" to exclude the transfer of access rights to information to third parties.
The tasks of ensuring the integrity of information in the case of using individual "cloud" applications can be solved - thanks to modern database architectures, backup systems, integrity check algorithms and other industrial solutions. But that's not all. New challenges can arise when it comes to integrating multiple cloud applications from different vendors.
In the near future, for companies looking for a secure virtual environment, the only option is to create a private cloud system. The fact is that private clouds, unlike public or hybrid systems, are most similar to virtualized infrastructures that IT departments of large corporations have already learned to implement and over which they can maintain complete control. Information security flaws in public cloud systems pose a significant challenge. Most burglary incidents occur in public clouds.
6. Security of cloud models
The level of risk in the three cloud models is very different, and the ways to address security issues also differ depending on the level of interaction. The security requirements remain the same, but the level of security control changes across different models, SaaS, PaaS, or IaaS. From a logical point of view, nothing changes, but the possibilities of physical implementation are radically different.

Rice. 11. The most pressing information security threats
in the SaaS model, the application runs on the cloud infrastructure and is accessible through a web browser. The client has no control over the network, servers, operating systems, storage, or even some application capabilities. For this reason, in the SaaS model, the primary responsibility for security falls almost entirely on the vendors.
Problem number 1 is password management. In the SaaS model, applications reside in the cloud, so the main risk is using multiple accounts to access applications. Organizations can solve this problem by unifying accounts for cloud and on-premises systems. With single sign-on, users can access workstations and cloud services using a single account. This approach reduces the likelihood of "stuck" accounts subject to unauthorized use after the termination of employees.
According to CSA's explanation, PaaS assumes that customers build applications using vendor-supported programming languages and tools and then deploy them to the cloud infrastructure. As with the SaaS model, the customer cannot manage or control the infrastructure — networks, servers, operating systems, or storage systems — but has control over application deployment.
In a PaaS model, users must pay attention to application security as well as API management issues such as validation, authorization, and verification.
Problem number 1 is data encryption. The PaaS model is inherently secure, but the risk is inadequate system performance. This is because encryption is recommended when communicating with PaaS providers, and this requires additional processing power. Nevertheless, in any solution, the transmission of confidential user data must be carried out over an encrypted channel.
While customers here have no control over the underlying cloud infrastructure, they have control over operating systems, storage and application deployment, and possibly limited control over the choice of network components.
This model has several built-in security capabilities without protecting the infrastructure itself. This means that users must manage and secure operating systems, applications, and content, usually through APIs.
If this is translated into the language of protection methods, then the provider must provide:
· Reliable control of access to the infrastructure itself;
· Infrastructure resiliency.
At the same time, the cloud consumer takes on much more protection functions:
· Firewalling within the infrastructure;
· Protection against intrusions into the network;
· Protection of operating systems and databases (access control, protection against vulnerabilities, control of security settings);
· Protection of end applications (anti-virus protection, access control).
Thus, most of the protection measures fall on the shoulders of the consumer. The provider can provide standard recommendations for protection or turnkey solutions, which will simplify the task for end users.
Table 1. Delineation of responsibility for security between the client and the service provider. (P - supplier, K - client)
Enterprise Server Application Data Runtime environment Middleware Operating system Virtualization Server Data warehouses network hardware The tasks of the Cloud Auditor are essentially the same as those of the auditor of conventional systems. Cloud security audit is subdivided into Supplier audit and User audit. The User's audit is carried out at the User's request, while the Supplier's audit is one of the most important conditions for doing business. It consists of: · Initiation of the audit procedure; · Collection of audit information; · Analysis of audit data; · Preparation of an audit report. At the stage of initiating the audit procedure, the issues of the powers of the auditor, the timing of the audit must be resolved. The obligatory assistance of employees to the auditor should also be stipulated. In general, the auditor conducts an audit to determine the reliability · Virtualization systems, hypervisor; · Servers; · Data warehouses; · Network equipment. If the Supplier uses the IaaS model on the checked server, then this check will be sufficient to identify vulnerabilities. When using the PaaS model, additional checks should be made. · operating system, Middleware, · Runtime environment. When using the SaaS model, vulnerabilities are also checked Data storage and processing systems, · Applications. Security audits are performed using the same methods and tools as auditing conventional servers. But unlike a conventional server in cloud technologies, the hypervisor is additionally checked for stability. In the cloud, the hypervisor is one of the core technologies and therefore should be given special emphasis on auditing. Information security measures can be divided into preventive (for example, encryption and other access control mechanisms), and reactive (investigations). The proactive aspect of cloud security is an area of active research, while the reactive aspect of cloud security has received much less attention. Investigation of incidents (including investigation of crimes in the information sphere) is a well-known section of information security. The objectives of such investigations are usually: Proof that the crime / incident occurred Recovering the events surrounding the incident Identification of offenders Proof of the involvement and responsibility of offenders Proof of dishonest intentions on the part of the perpetrators. A new discipline - computer and technical expertise (or forensics) appeared, in view of the need for forensic analysis of digital systems. The goals of computer forensics are usually as follows: Recovering data that may have been deleted Recovery of events that occurred inside and outside the digital systems associated with the incident Identification of users of digital systems Detection of the presence of viruses and other malicious software Detection of the presence of illegal materials and programs Cracking passwords, encryption keys and access codes Ideally, computer forensics is a kind of time machine for an investigator, which can travel at any moment into the past of a digital device and provide the investigator with information about: people who used the device at a certain point user actions (for example, opening documents, accessing a website, printing data in a word processor, etc.) data stored, created and processed by the device at a specific time. Cloud services replacing stand-alone digital devices should provide a similar level of forensic preparedness. However, this requires overcoming the challenges associated with resource pooling, multitenancy, and elasticity of cloud computing infrastructure. The main tool in incident investigation is the audit trail. Audit trails — designed to monitor the history of user logins, administrative tasks, and data changes — are an essential part of a security system. In the cloud, the audit trail itself is not only an investigation tool, but also a tool for calculating the cost of using servers. While the audit trail does not address security holes, it allows you to take a critical look at what is happening and formulate suggestions for correcting the situation. Creating archives and backups is important, but it cannot replace a formal audit trail that records who did what, when and. The audit trail is one of the main tools of a security auditor. The service agreement usually mentions which audit logs will be kept and provided to the User. In 2010, CSA conducted an analysis of the top security threats in cloud technologies. The result of their work was the document "Top threats of Cloud Computing v 1.0" in which the threat model and the intruder's model are most fully described at the moment. At the moment, a more complete, second version of this document is being developed. The current document describes the attackers for three service models SaaS, PaaS and IaaS. Seven main attack vectors have been identified. For the most part, all the types of attacks under consideration are attacks inherent in conventional, "non-cloud" servers. Cloud infrastructure imposes certain features on them. So, for example, attacks on the vulnerabilities in the software part of servers are added to attacks on the hypervisor, which is also their software part. Security threat # 1 Inappropriate and dishonest use of cloud technologies. Description: To obtain resources from the cloud IaaS provider, the user only needs to have a credit card. Ease of registration and resource allocation allows spammers, virus authors, etc. use the cloud service for their own criminal purposes. Previously, this kind of attack was observed only in PaaS, but recent studies have shown the possibility of using IaaS for DDOS attacks, placing malicious code, creating botnet networks, and more. Examples of services were used to create a botnet network based on the Zeus Trojan, store the InfoStealer Trojan horse code, and post information about various MS Office and AdobePDF vulnerabilities. In addition, botnet networks use IaaS to manage their peers and send spam. Because of this, some IaaS services were blacklisted, and their users were completely ignored by mail servers. Improvements to user registration procedures Improvement of credit card verification procedures and monitoring of the use of payment means Comprehensive study of the network activity of service users · Tracking the main black sheets for the appearance of a cloud provider network there. Service Models Affected: Security threat # 2 Insecure Programming Interfaces (APIs) Description: Cloud infrastructure providers provide users with a set of programming interfaces for managing resources, virtual machines, or services. The security of the entire system depends on the security of these interfaces. Anonymous access to the interface and the transmission of credentials in clear text are the main hallmarks of insecure APIs. Limited monitoring of API usage, lack of logging systems, as well as unknown relationships between various services only increase the risk of hacking. Analyze the security model of the cloud provider Ensure strong encryption algorithms are used Ensure that strong authentication and authorization methods are used · Understand the whole chain of dependencies between different services. Service models affected: Security threat # 3 Internal offenders Description: The problem of illegal access to information from within is extremely dangerous. Often, on the side of the provider, a system for monitoring the activity of employees is not implemented, which means that an attacker can gain access to the client's information using his official position. Since the provider does not disclose its recruitment policy, the threat can come from both an amateur hacker and from an organized criminal structure that has infiltrated the ranks of the provider's employees. There are currently no examples of this kind of abuse. Implementation of strict rules for the procurement of equipment and the use of appropriate systems for detecting unauthorized access Regulating the rules for hiring employees in public contracts with users Creation of a transparent security system, along with the publication of security audit reports on the provider's internal systems Service models affected: Rice. 12 Example of an insider Security threat # 4 Vulnerabilities in cloud technologies Description: IaaS service providers abstraction of hardware resources using virtualization systems. However, hardware can be designed without considering shared resources. In order to minimize the influence of this factor, the hypervisor controls the virtual machine's access to hardware resources, however, even in hypervisors, serious vulnerabilities can exist, the use of which can lead to privilege escalation or gaining illegal access to physical equipment. In order to protect systems from such problems, it is necessary to implement mechanisms for isolating virtual environments and systems for detecting failures. Virtual machine users should not have access to shared resources. There are examples of potential vulnerabilities, as well as theoretical methods of bypassing isolation in virtual environments. Implementation of the most advanced methods of installation, configuration and protection of virtual environments Use of systems for detection of unauthorized access Applying strong authentication and authorization rules for administrative work Tightening the requirements for the application time of patches and updates · Conducting timely procedures for scanning and detecting vulnerabilities. Security threat # 5 Loss or leakage of data Description: Data loss can happen for a thousand reasons. For example, deliberate destruction of the encryption key will result in the encrypted information being unrecoverable. Deletion of data or a part of data, illegal access to important information, changes in records or failure of the medium are also examples of such situations. In a complex cloud infrastructure, the likelihood of each of the events increases due to the close interaction of components. Incorrect application of authentication, authorization and audit rules, incorrect use of encryption rules and methods, and equipment failure can lead to data loss or leakage. · Using a reliable and secure API Encryption and protection of transmitted data Analysis of the data protection model at all stages of the system functioning Implementation of a reliable encryption key management system Selecting and purchasing only the most reliable media Ensuring timely data backup Service models affected: Security threat # 6 Theft of personal data and illegal access to the service Description: This kind of threat is not new. It is faced by millions of users every day. The main target of the attackers is the username (login) and his password. In the context of cloud systems, stealing the password and username increases the risk of using data stored in the provider's cloud infrastructure. So the attacker has the opportunity to use the victim's reputation for his activities. Ban on the transfer of accounts Using two factor authentication methods Implementation of proactive monitoring of unauthorized access · Description of the security model of the cloud provider. Service models affected: Security threat # 7 Other vulnerabilities Description: The use of cloud technologies for doing business allows the company to focus on its business, leaving the care of the IT infrastructure and services to the cloud provider. By advertising its service, the cloud provider seeks to show all the possibilities, while revealing the implementation details. This can pose a serious threat, as knowledge of the internal infrastructure gives an attacker the ability to find an unpatched vulnerability and launch an attack on the system. In order to avoid such situations, cloud providers may not provide information about the internal structure of the cloud, however, this approach also does not increase trust, since potential users do not have the ability to assess the degree of data security. In addition, such an approach limits the ability to find and eliminate vulnerabilities in a timely manner. Amazon refuses to conduct an EC2 cloud security audit Vulnerability in processing software, leading to a breach of the security system of the Hearthland data center Disclosure of log data Full or partial disclosure of data about the architecture of the system and details about the installed software · Use of vulnerability monitoring systems. Service models affected: 1. Legal base According to experts, 70% of security problems in the cloud can be avoided if you correctly draw up a service agreement. The basis for such an agreement can serve as the "Bill of Rights of the cloud" The Cloud's Bill of Rights was developed back in 2008 by James Urquhart. He published this material on his blog, which caused so much interest and controversy that the author periodically updates his "manuscript" in accordance with the realities. Article 1 (in part): Clients own their data · No manufacturer (or supplier) should, in the process of interacting with customers of any plan, discuss the rights to any data uploaded, created, generated, modified or any other rights to which the customer has. · Manufacturers should initially provide minimal access to customer data at the stage of developing solutions and services. · Customers own their data, which means that they are responsible for ensuring that the data complies with legal regulations and laws. · Since data compliance, security and safety compliance issues are very important, it is imperative that the customer geographically locates their own data. Otherwise, manufacturers must provide users with all guarantees that their data will be stored in accordance with all rules and regulations. Clause 2: Manufacturers and Customers jointly own and manage service levels in the system · Manufacturers own and must do everything in order to meet the level of service for each client individually. All the necessary resources and efforts made to achieve the proper level of service in working with clients should be free for the client, that is, not included in the cost of the service. · Customers, in turn, are responsible for and own the level of service provided to their own internal and external customers. When using the manufacturer's solutions to provide their own services, the responsibility of the client and the level of such service should not entirely depend on the manufacturer. · If it is necessary to integrate the systems of the manufacturer and the customer, the manufacturers should offer the customers the ability to monitor the integration process. If the client has corporate standards for the integration of information systems, the manufacturer must comply with these standards. · Under no circumstances should manufacturers close customer accounts for political statements, inappropriate speech, religious comments, unless it is contrary to specific legal regulations, is not an expression of hatred, etc. Article 3: Manufacturers Own Their Interfaces · Manufacturers are not required to provide standard or open source interfaces unless otherwise specified in customer agreements. Manufacturers have rights to interfaces. If the manufacturer does not consider it possible to provide the client with the opportunity to refine the interface in a familiar programming language, the client can purchase from the manufacturer or third-party developers services for finalizing the interfaces in accordance with his own requirements. · The client, however, has the right to use the purchased service for his own purposes, as well as expand its capabilities, replicate and improve. This clause does not relieve customers of patent and intellectual property rights. The above three articles are the foundation for customers and vendors in the cloud. You can find their full text in the public domain on the Internet. Of course, this bill is not a complete legal document, much less an official one. Its articles can be changed and expanded at any time, just as the bill can be supplemented by new articles. This is an attempt to formalize "ownership" in the cloud in order to somehow standardize this freedom-loving area of knowledge and technology. Relationship between the parties By far the best cloud security expert is the Cloud Security Alliance (CSA). The organization has released and recently updated a guide that includes hundreds of nuances and best practices to consider when assessing cloud computing risks. Another organization that deals with aspects of cloud security is the Trusted Computing Group (TCG). She is the author of several standards in this and other areas, including the widely used Trusted Storage, Trusted Network Connect (TNC), and Trusted Platform Module (TPM) today. These organizations jointly worked out a number of issues that the customer and the provider must work through when concluding a contract. These questions will solve most of the problems when using the cloud, force majeure, changing cloud service providers and other situations. 1. Safety of stored data. How does the service provider ensure the safety of the stored data?
The best measure to protect data stored in a data warehouse is to use encryption technologies. The provider must always encrypt the client information stored on its servers to prevent cases of unauthorized access. The provider must also permanently delete data when it is no longer needed and will not be required in the future. 2. Data protection during transmission. How does the provider ensure the safety of data during its transfer (inside the cloud and on the way from / to the cloud)?
The transmitted data must always be encrypted and accessible to the user only after authentication. This approach ensures that this data cannot be changed or read by anyone, even if they gain access to it through untrusted nodes on the network. These technologies have been developed over "thousands of man-years" and have led to the creation of reliable protocols and algorithms (for example, TLS, IPsec and AES). Providers should use these protocols, not invent their own. 3. Authentication. How does the provider know the authenticity of the client?
The most common authentication method is password protection. However, ISPs looking to offer their customers greater reliability are looking to more powerful tools such as certificates and tokens. In addition to using more secure authentication means, providers should be able to work with standards such as LDAP and SAML. This is necessary to ensure that the provider interacts with the client's user identification system when authorizing and defining the authorizations given to the user. Thanks to this, the provider will always have up-to-date information about the authorized users. The worst case scenario is when the client provides the provider with a specific list of authorized users. As a rule, in this case, when an employee is fired or moved to another position, difficulties may arise. 4. User isolation. How are the data and applications of one customer separated from the data and applications of other customers?
Best option: when each of the clients uses an individual virtual machine (VM) and virtual network. The separation between VMs, and therefore between users, is provided by the hypervisor. Virtual networks, in turn, are deployed using standard technologies such as VLAN (Virtual Local Area Network), VPLS (Virtual Private LAN Service) and VPN (Virtual Private Network). Some providers put all customer data in a single software environment and try to isolate customer data from each other by changes in its code. This approach is reckless and unreliable. First, an attacker can find a flaw in non-standard code that would allow him to gain access to data that he should not see. Secondly, a mistake in the code can lead to the fact that one client accidentally "sees" the data of another. Recently, there have been both those and other cases. Therefore, to differentiate user data, using different virtual machines and virtual networks is a more reasonable step. 5. Regulatory issues. How well is the provider complying with the laws and regulations applicable to the cloud computing industry?
Depending on the jurisdiction, laws, regulations and any special provisions may vary. For example, they can prohibit the export of data, require strictly defined safeguards, be compliant with certain standards, and be auditable. Ultimately, they can demand that government departments and courts can access information when needed. The provider's negligence to these moments can lead its customers to significant costs due to legal consequences. The provider must follow strict rules and adhere to a unified legal and regulatory strategy. This concerns the security of user data, their export, compliance with standards, auditing, data safety and deletion, as well as information disclosure (the latter is especially important when information of several clients can be stored on one physical server). To find out, clients are strongly encouraged to seek help from specialists who will study this issue thoroughly. 6. Reaction to incidents. How does the provider respond to incidents, and to what extent may its customers be involved in the incident?
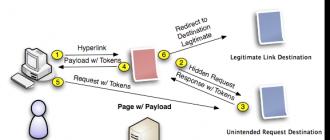
Sometimes not everything goes according to plan. Therefore, the service provider is obliged to adhere to specific rules of conduct in the event of unforeseen circumstances. These rules should be documented. It is imperative for providers to identify incidents and minimize their consequences by informing users about the current situation. Ideally, they should regularly provide clients with information that is as detailed as possible on the issue. In addition, it is up to customers to assess the likelihood of a security issue and take the necessary action. The evolution of cloud technology has outpaced efforts to create and modify the required industry standards, many of which have not been updated in years. Therefore, law-making in the field of cloud technologies is one of the most important steps towards ensuring security. The IEEE, one of the world's largest standards development organizations, has announced the launch of a dedicated Cloud Computing Initiative. This is the first international cloud standardization initiative - to date, cloud computing standards have been dominated by industry consortia. The initiative currently includes 2 projects: IEEE P2301 (tm), "Draft Guide to Portability and Interoperability of Cloud Profiles", and IEEE P2302 (tm) - "Draft Standard for Interoperability and Distributed Interoperability (Federation) of Cloud Systems ”. Within the framework of the IEEE Standards Development Association, 2 new working groups have been created to work on drafts IEEE P2301 and IEEE P2302, respectively. IEEE P2301 will contain profiles of existing and pending application, portability, management, and interoperability standards, as well as file formats and operating agreements. The information in the document will be logically structured according to different target audience groups: vendors, service providers and other interested market participants. Upon completion, the standard is expected to be usable in the procurement, development, construction and use of cloud products and services based on standard technologies. The IEEE P2302 standard will describe the underlying topology, protocols, functionality, and management techniques required for the interaction of various cloud structures (for example, for the interaction of a private cloud and a public one such as EC2). This standard will enable providers of cloud products and services to reap economic benefits from economies of scale, while providing transparency to users of services and applications. ISO is preparing a special standard for cloud computing security. The main focus of the new standard is to address organizational issues related to clouds. However, due to the complexity of ISO's harmonization procedures, the final version of the document should not be released until 2013. The value of the document is that not only government organizations (NIST, ENISA) are involved in its preparation, but also representatives of expert communities and associations such as ISACA and CSA. Moreover, one document contains recommendations for both cloud service providers and their consumers - client organizations. The main purpose of this document is to describe in detail the best practices associated with the use of cloud computing from an information security perspective. At the same time, the standard does not focus only on the technical aspects, but rather on the organizational aspects that must not be forgotten in the transition to cloud computing. This is the separation of rights and responsibilities, and the signing of agreements with third parties, and the management of assets owned by different participants in the "cloud" process, and issues of personnel management, and so on. The new document largely incorporates materials previously developed in the IT industry. Australian government After months of brainstorming, the Australian Government has released a series of cloud-based migration guides on February 15, 2012 on the Australian Government Information Management Office (AGIMO) blog. To make it easier for companies to migrate to the cloud, we have provided best practice guidelines for using cloud services to meet the requirements of the 1997 Better Practice Guides for Financial Management and Accountability Act 1997. The guides deal with financial, legal and data protection issues in general terms. The guidelines talk about the need to constantly monitor and control the use of cloud services through daily analysis of bills and reports. This will help avoid hidden markups and dependence on cloud service providers. The first guide is titled Privacy and Cloud Computing for Australian Government Agencies (9 pages). This document focuses on privacy and data security issues. In addition to this guide, Negotiating the Cloud - Legal Issues in Cloud Computing Agreements (19 pages) has also been prepared to help you understand the clauses included in contract. The final, third handbook, Financial Considerations for Government use of Cloud Computing (6 pages), discusses the financial issues that a company should look out for if it decides to use cloud computing in its business. In addition to those covered in the guides, there are a number of other issues that need to be addressed when using cloud computing, including issues related to government, procurement and business management policy. Public discussion of this policy paper provides an opportunity for stakeholders to consider and comment on the following issues of concern: · Unauthorized access to classified information; · Loss of access to data; Failure to ensure the integrity and authenticity of data, and · Understanding the practical aspects of providing cloud services. There are a number of regulations in different countries that require sensitive data to remain within the country. While keeping data within a given territory is not at first glance difficult, cloud service providers often cannot guarantee it. In systems with a high degree of virtualization, data and virtual machines can move from one country to another for various purposes - load balancing, fault tolerance. Some of the major players in the SaaS market (such as Google, Symantec) can provide a guarantee of data storage in the respective country. But these are, rather, exceptions, in general, the fulfillment of these requirements is still quite rare. Even if the data remains in the country, there is no way for customers to verify it. In addition, one should not forget about the mobility of company employees. If a specialist working in Moscow travels to New York, then it is better (or at least faster) for him to receive data from a data center in the United States. To ensure this is already an order of magnitude more difficult task. At the moment, there is no serious regulatory framework for cloud technologies in our country, although developments in this area are already underway. So, by order of the President of the Russian Federation No. 146 of 8.02.2012. it was determined that the federal executive bodies authorized in the field of data security in information systems created using supercomputer and grid technologies are the FSB of Russia and the FSTEC of Russia. In connection with this decree, the powers of these services have been expanded. The FSB of Russia now develops and approves regulatory and methodological documents on ensuring the security of these systems, organizes and conducts research in the field of information security. The service also carries out expert cryptographic, engineering-cryptographic and special studies of these information systems and prepares expert opinions on proposals for work on their creation. The document also stipulates that the FSTEC of Russia develops a strategy and determines priority areas for ensuring the security of information in information systems created using supercomputer and grid technologies that process limited access data, and also monitors the state of work to ensure this security. FSTEC ordered a study, which resulted in a beta version of the "terminology system in the field of" cloud technologies " As you can understand, this whole Terminological System is an adapted translation of two documents: "Focus Group on Cloud Computing Technical Report" and "The NIST Definition of Cloud Computing". Well, the fact that these two documents are not very consistent with each other is a separate issue. But visually it is still visible: in the Russian "Terminosystem" the authors simply did not provide links to these English documents for a start. The fact is that for such work, you first need to discuss the concept, goals and objectives, methods of their solution. There are many questions and comments. The main methodological note: it is necessary to very clearly formulate what problem this research solves, its purpose. I would like to point out right away that "the creation of a terminological system" cannot be a goal, it is a means, but the achievement of what is not yet very clear. Not to mention that a normal study should include a status quo section. It is difficult to discuss the results of a study without knowing the original formulation of the problem and how the authors solved it. But one fundamental error of the Terminology System is clearly visible: it is impossible to discuss the "cloudy subject" in isolation from the "non-cloudy" one. Out of the general IT context. But this context is not visible in the study. And the result of this is that in practice it will be impossible to apply such a Terminology System. It can only confuse the situation further. A cloud server protection system in its minimum configuration should ensure the security of network equipment, data storage, server and hypervisor. Additionally, it is possible to place an anti-virus in a dedicated core to prevent infection of the hypervisor through a virtual machine, a data encryption system for storing user information in encrypted form and means for implementing encrypted tunneling between the virtual server and the client machine. To do this, we need a server that supports virtualization. Solutions of this kind are offered by Cisco, Microsoft, VMWare, Xen, KVM. It is also permissible to use a classic server, and provide virtualization on it using a hypervisor. Any servers with compatible processors are suitable for virtualization of operating systems for x86-64 platforms. Such a solution will simplify the transition to computing virtualization without making additional financial investments in hardware upgrades. Scheme of work: Rice. 11. An example of a "cloud" server Rice. 12. Server response to hardware block failure At the moment, the market for cloud computing security tools is still quite empty. And this is not surprising. In the absence of a regulatory framework and uncertainty about future standards, development companies do not know what to focus their efforts on. However, even in such conditions, specialized software and hardware systems appear that make it possible to secure the cloud structure from the main types of threats. Integrity violation Hacking a hypervisor Insiders Identification Authentication Encryption Accord-B Hardware and software system Accord-B. designed to protect virtualization infrastructure VMware vSphere 4.1, VMware vSphere 4.0 and VMware Infrastructure 3.5. Accord-B. provides protection for all components of the virtualization environment: ESX servers and virtual machines themselves, vCenter management servers and additional servers with VMware services (for example, VMware Consolidated Backup). The following protection mechanisms are implemented in the Accord-V hardware and software complex: · Step-by-step control of the integrity of the hypervisor, virtual machines, files inside virtual machines and infrastructure management servers; · Differentiation of access for administrators of virtual infrastructure and security administrators; · Differentiation of user access inside virtual machines; · Hardware identification of all users and administrators of the virtualization infrastructure. INFORMATION ABOUT THE AVAILABILITY OF CERTIFICATES: The FSTEC of Russia Certificate of Conformity No. 2598 dated 03/20/2012 certifies that the hardware and software complex of information protection means from unauthorized access "Accord-V." complies with the requirements of the guidance documents "Computer facilities. Protection against unauthorized access to information. Indicators of security against unauthorized access to information" (State Technical Commission of Russia, 1992) - according to 5
security class, "Protection against unauthorized access to information. Part 1. Software for information protection. Classification by the level of control of the absence of undeclared capabilities" (State Technical Commission of Russia, 1999) - according to 4
the level of control and technical conditions TU 4012-028-11443195-2010, and can also be used to create automated systems up to security class 1G inclusive and to protect information in personal data information systems up to class 1 inclusive. vGate R2 vGate R2 is a certified means of information protection against unauthorized access and control of the implementation of information security policies for virtual infrastructure based on VMware vSphere 4 and VMware vSphere 5.S R2 systems - a version of the product applicable to protect information in virtual infrastructures of public companies, whose IP is applied requirements for the use of information security systems with a high level of certification. Allows you to automate the work of administrators to configure and operate the security system. Helps counteract errors and abuse in virtual infrastructure management. Allows you to bring the virtual infrastructure in line with legislation, industry standards and world best practices. <#"783809.files/image017.gif"> <#"783809.files/image018.gif"> <#"783809.files/image019.gif"> <#"783809.files/image020.gif"> Rice. 13 vGate R2 announced capabilities Thus, to summarize, we present the main tools that vGate R2 possesses to protect the service provider's data center from internal threats emanating from its own administrators: Organizational and technical separation of powers for vSphere administrators Allocation of a separate role of the IS administrator who will manage the security of the resources of the data center based on vSphere Dividing the cloud into security zones, within which administrators operate with the appropriate level of authority Integrity control of virtual machines Ability to receive a report on the security of the vSphere infrastructure at any time, as well as audit information security events In principle, this is almost all that is needed to protect the infrastructure of a virtual data center from internal threats from the point of view of the virtual infrastructure. Of course, you also need protection at the level of hardware, applications and guest OS, but this is another problem, which is also solved by means of the company's products Security Code<#"783809.files/image021.gif"> Rice. 14. Server structure. To ensure safety at such an object, it is necessary to ensure safety, according to Table 2. For this, I suggest using the software product vGate R2. It will allow you to solve such problems as: · Stronger authentication for virtual infrastructure administrators and information security administrators. · Protection of virtual infrastructure management tools from tampering. · Protection of ESX-servers from tampering. · Mandatory access control. · Monitoring the integrity of the configuration of virtual machines and trusted boot. · Control of access of VI administrators to data of virtual machines. · Registration of events related to information security. · Integrity control and protection against tampering of information security components. · Centralized management and monitoring. Table 2. Security Needs Mapping for the PaaS Model
FSTEC certificate of Russia In addition, to protect against insiders, you will need to install a security alarm. These solutions are quite richly provided in the server protection market. The price of such a solution with limited access to the controlled area, an alarm and video surveillance system ranges from 200,000 rubles and more For example, let's take the amount of 250,000 rubles. To protect virtual machines from virus infections, one server core will run McAfee Total Protection for Virtualization. The cost of the solution is from 42,200 rubles. Symantec Netbackup will be used to prevent data loss on the storages. It allows you to reliably back up information and system images. The total cost of implementing such a project will be: A Microsoft-based implementation of such a design solution can be downloaded from here: http://www.microsoft.com/en-us/download/confirmation. aspx? id = 2494 "Cloud technologies" is one of the most actively developing areas of the IT market at the present time. If the rate of growth of technologies does not decrease, then by 2015 they will contribute to the treasury of European countries more than 170 million euros per year. In our country, cloud technologies are treated with caution. This is partly due to the ossified views of the leadership, partly a lack of confidence in security. But this type of technology, with all its advantages and disadvantages, is a new locomotive of IT progress. The application "on the other side of the cloud" does not matter at all whether you form your request on a computer with x86 processor Intel, AMD, VIA or compose it on a phone or smartphone based on ARM-processor Freescale, OMAP, Tegra. Moreover, by and large it will not matter if you are running Linux operating systems Google Chrome, OHA Android, Intel Moblin, Windows CE, Windows Mobile Windows XP / Vista / 7, or using something even more exotic for this. ... If only the request was composed correctly and understandably, and your system could "master" the received answer. The issue of security is one of the main issues in cloud computing and its solution will improve the quality of services in the computer sphere. However, much remains to be done in this direction. In our country, it is worth starting with a unified vocabulary of terms for the entire IT field. Develop standards based on international experience. Put forward requirements for security systems. 1. Financial Considerations for Government Use of Cloud Computing - Australian Government 2010. 2. Privacy and Cloud Computing for Australian Government Agencies 2007. Negotiating the cloud - legal issues in cloud computing agreements 2009. Journal "Modern Science: Actual Problems of Theory and Practice" 2012.
7. Security audit
8. Investigation of incidents and forensics in cloud computing
9. Threat model

10. International and domestic standards
11. Territorial identity of the data
12. State standards
13. Cloud Security Means


Output
Literature
Similar work to - Information security in cloud computing: vulnerabilities, methods and means of protection, tools for auditing and incident investigation
There are several methods for building a corporate IT infrastructure. Deploying all resources and services on a cloud platform is just one of them. However, prejudice about the security of cloud solutions often gets in the way. In this article, we will understand how the security system is arranged in the cloud of one of the most famous Russian providers - Yandex.
A fairy tale is a lie, but there is a hint in it
The beginning of this story can be told like a famous fairy tale. There were three administrators in the firm: the senior was a smart fellow, the middle one was this and that, the youngest was ... a trainee-enikeyschik. I started up users in Active Directory and twisted tails to tsiska. The time has come for the company to expand, and the king, that is, the boss, called on his admin army. I wish, he says, new web services for our clients, our own file storage, managed databases and virtual machines for software testing.
The youngest immediately suggested creating his own infrastructure from scratch: purchasing servers, installing and configuring software, expanding the main Internet channel and adding a backup one to it - for reliability. And the company is calmer: hardware is always at hand, at any time you can replace or reconfigure something, and he himself will have an excellent opportunity to pump his admin skills. They calculated and shed tears: the company will not be able to afford such costs. Large businesses can do this, but for medium and small businesses it turns out to be too expensive. Well, you need not just purchase equipment, equip a server room, install air conditioners and set up fire alarms, you also need to organize shift duty in order to keep order day and night and repel the network attacks of dashing people from the Internet. And for some reason, the administrators did not want to work at night and on weekends. If only for double payment.
The senior admin looked thoughtfully at the terminal window and suggested putting all the services in the cloud. But then his colleagues began to scare each other with horror stories: they say that the cloud infrastructure has unprotected interfaces and APIs, does not balance the load of different clients, which can damage your own resources, and is also unstable to data theft and external attacks. And in general, it is scary to transfer control over critical data and software to outsiders, with whom you did not eat a pound of salt and did not drink a bucket of beer.
Mediocre came up with the idea to place the entire IT system in the provider's data center, on its channels. On that and decided. However, there were several surprises awaiting our trio, not all of which were pleasant.
First, any network infrastructure requires the mandatory availability of security and protection tools, which, of course, have been deployed, configured and launched. However, the cost of the hardware resources they use, as it turned out, must be paid by the client himself. A modern information security system consumes considerable resources.
Secondly, the business continued to grow and the infrastructure built from the beginning quickly hit the scalability ceiling. Moreover, to expand it, a simple change of the tariff was not enough: in this case, many services would have to be transferred to other servers, reconfigured, and something completely redesigned from scratch.
Finally, one day, due to a critical vulnerability in one of the applications, the entire system crashed. The admins quickly picked it up from the backups, but they didn't manage to quickly figure out the reasons for what happened, because they forgot to set up backup for the logging services. Valuable time was lost, and time, as popular wisdom says, is money.
Calculating costs and summing up the results led the company's management to disappointing conclusions: the admin who from the very beginning suggested using the cloud model of IaaS - "infrastructure as a service", was right. As for the security of such platforms, it is worth talking about it separately. And we will do this using the example of the most popular of these services - Yandex.Cloud.
Security in Yandex.Cloud
Let's start, as the Cheshire Cat advised the girl Alice, from the beginning. That is, from the issue of delineation of responsibility. In Yandex.Cloud, as in any other similar platforms, the provider is responsible for the security of the services provided to users, while the client himself is responsible for ensuring the correct operation of the applications he develops, organizing and delimiting remote access to dedicated resources, configuring databases and virtual machines, control over logging. However, for this he is provided with all the necessary tools.
The security of Yandex cloud infrastructure has several levels, each of which implements its own protection principles and uses a separate arsenal of technologies.
Physical layer
It's no secret that Yandex has its own data centers, which are maintained by their own security departments. We are talking not only about video surveillance and access control services designed to prevent outsiders from entering the server rooms, but also about climate control systems, fire extinguishing and uninterruptible power supplies. Stern security guards are of little use if the rack with your servers is once flooded with water from the fire sprinklers or they overheat after an air conditioner failure. This will definitely not happen to them in Yandex data centers.
In addition, the Cloud hardware is physically separated from the "big Yandex": they are located in different racks, but in exactly the same way they undergo regular routine maintenance and replacement of components. On the border of these two infrastructures, hardware firewalls are used, and inside the Cloud - a software Host-based Firewall. In addition, the Top-of-the-rack switches use the Access Control List (ACL) system, which greatly enhances the security of the entire infrastructure. Yandex on an ongoing basis scans the Cloud from the outside in search of open ports and configuration errors, so that a potential vulnerability can be recognized and eliminated in advance. For employees working with Cloud resources, a centralized authentication system using SSH keys with a role-based access model has been implemented, and all administrator sessions are logged. This approach is part of the Secure by default model, widely used by Yandex: security is incorporated into the IT infrastructure at the stage of its design and development, and is not added later, when everything has already been put into operation.
Infrastructure level
At the “hardware-software logic” level, Yandex.Cloud uses three infrastructure services: Compute Cloud, Virtual Private Cloud, and Yandex Managed Services. And now about each of them in a little more detail.
Compute Cloud
This service provides scalable computing power for various tasks, such as hosting web projects and high-load services, testing and prototyping, or temporary migration of IT infrastructure for the period of repair or replacement of your own equipment. The service can be controlled through the console, command line (CLI), SDK, or API.
Compute Cloud security is based on the fact that all client virtual machines use at least two cores, and there is no overcommitment in memory allocation. Since in this case only the client code is executed on the kernel, the system is not susceptible to vulnerabilities such as L1TF, Specter and Meltdown, or side-channel attacks.
In addition, Yandex uses its own assembly Qemu / KVM, in which everything unnecessary is disabled, leaving only the minimum set of code and libraries required for the operation of hypervisors. At the same time, the processes are launched under the control of AppArmor-based instrumentation, which, using security policies, determines which system resources and with which privileges a particular application can access. AppArmor running on top of each virtual machine reduces the risk of a client application being able to access the hypervisor from the VM. To receive and process logs, Yandex has built a process for delivering data from AppArmor and sandboxes to its own Splunk.
Virtual private cloud
The Virtual Private Cloud service allows you to create cloud networks used to transfer information between different resources and their connection to the Internet. Physically, this service is supported by three independent data centers. In this environment, logical isolation is performed at the level of multi-protocol communication - MPLS. At the same time, Yandex constantly fuzzing the SDN and hypervisor interface, that is, from the side of virtual machines, a stream of malformed packets is continuously sent to the external environment in order to receive a response from SDN, analyze it and close possible configuration gaps. DDoS protection is automatically enabled when virtual machines are created.
Yandex Managed Services
Yandex Managed Services is a software environment for managing various services: DBMS, Kubernetes clusters, virtual servers in the Yandex.Cloud infrastructure. This is where the service takes over most of the security work. All backups, encryption of backups, Vulnerability management, and so on are provided automatically by Yandex.Cloud software.
Incident response tools
To respond in a timely manner to information security incidents, it is necessary to identify the source of the problem in time. For this, it is necessary to use reliable monitoring tools that must work around the clock and without interruptions. Such systems will inevitably consume resources, but Yandex.Cloud does not shift the cost of computing power of security tools onto platform users.
When choosing the toolkit, Yandex was guided by another important requirement: in case of successful exploitation of a 0day vulnerability in one of the applications, the attacker should not leave the application host, while the security team must instantly learn about the incident and react as needed.
Last but not least, the wish was that all tools should be open source. These criteria are fully met by the AppArmor + Osquery bundle, which it was decided to use in Yandex.Cloud.
AppArmor
AppArmor was mentioned above: it is a proactive defense software tool based on customizable security profiles. The profiles use the Mandatory Access Control (MAC) privacy labeling technology implemented using LSM directly in the Linux kernel itself since version 2.6. Yandex developers chose AppArmor for the following reasons:
- lightness and speed, since the tool relies on part of the Linux kernel;
- it is an open source solution;
- AppArmor can be deployed very quickly on Linux without writing any code;
- flexible configuration is possible using configuration files.
Osquery
Osquery is a system security monitoring tool developed by Facebook and is now successfully used in many IT industries. At the same time, the tool is cross-platform and has an open source code.
With the help of Osquery, you can collect information about the state of various components of the operating system, accumulate it, transform it into a standardized JSON format and send it to the chosen recipient. This tool allows you to write and route standard SQL queries to your application, which are stored in the rocksdb database. You can customize the frequency and conditions for these requests to be executed or processed.
In the standard tables, many features are already implemented, for example, you can get a list of processes running on the system, installed packages, the current set of iptables rules, crontab entities, and so on. Out of the box, support for receiving and parsing events from the kernel audit system has been implemented (used in Yandex.Cloud to handle AppArmor events).
Osquery itself is written in C ++ and distributed with open source, you can modify them and both add new tables to the main code base, and create your own extensions in C, Go or Python.
A useful feature of Osquery is the presence of a distributed query system, with which you can query all virtual machines on the network in real time. This can be useful, for example, if a vulnerability is found in a package: with a single query, you can get a list of machines on which this package is installed. This feature is widely used when administering large distributed systems with complex infrastructure.
conclusions
If we return to the story told at the very beginning of this article, we will see that the fears that made our heroes refuse to deploy infrastructure on a cloud platform turned out to be unfounded. At least when it comes to Yandex.Cloud. The security of the cloud infrastructure created by Yandex has a multi-layered echeloned architecture and therefore provides a high level of protection against most of the currently known threats.
At the same time, due to savings on routine maintenance of hardware and payment for resources consumed by monitoring and incident warning systems that Yandex undertakes, the use of Yandex.Cloud significantly saves money for small and medium-sized businesses. Of course, completely abandoning the IT department or the department responsible for information security (especially if both of these roles are combined into one team) will not work. But Yandex.Cloud will significantly reduce labor costs and overhead costs.
Since Yandex.Cloud provides its customers with a secure infrastructure with all the necessary security tools, they can focus on business processes, leaving the tasks of service maintenance and hardware monitoring to the provider. This does not eliminate the need for the current administration of VMs, databases and applications, but such a range of tasks would have to be solved in any case. In general, we can say that Yandex.Cloud saves not only money, but also time. And the second, unlike the first, is an irreplaceable resource.
2019
McAfee: 19 Cloud Security Best Practices in 2019
The biggest concern for companies is the protection of external cloud services. For example, respondents worry that incidents may occur from vendors who outsource business processes, from third-party cloud services, or in IT infrastructure where the company leases computing power. Despite all these concerns, however, only 15% of companies conduct third-party security reviews.
“Despite the fact that recent large-scale hacks have taken place inside the data center, traditional security systems still focus only on protecting the network perimeter and controlling access rights. At the same time, the negative impact of solutions for protecting physical infrastructure on the performance of virtual environments is rarely considered, - explained Veniamin Levtsov, vice president of corporate sales and business development at Kaspersky Lab. “This is why it is so important in converged environments to use appropriate end-to-end protection while securing virtual systems with dedicated solutions. We are implementing an approach in which, regardless of the type of infrastructure, for all systems, a uniform coverage of the entire corporate network is provided. And this is where our technologies and modern VMware developments (such as micro-segmentation) complement each other perfectly ”.
2015: Forrester: Why are customers unhappy with cloud providers?
Opaque cloud
A recent study by Forrester Consulting shows that many organizations believe that cloud service providers are not providing them with enough information about how they interact with the cloud, and this harms their business.
In addition to lack of transparency, there are other factors that diminish the enthusiasm for moving to the cloud: the level of service for customers, additional costs and on-boarding. Organizations love the cloud very much, but not the cloud providers — or not nearly as much.
The study, commissioned by iland, an enterprise cloud hosting provider, was conducted during May and included infrastructure and maintenance professionals from 275 organizations in, and Singapore.
“Among all the complexities of today's cloud, there are some annoying flaws,” writes Lilac Schoenbeck, vice president of product support and marketing for iland. "This critical metadata is not communicated, dramatically inhibiting cloud adoption, and yet organizations are making growth plans based on the premise of cloud infinity."
Where is the key to achieving harmony in business relationships? Here's what the VARs need to know in order to try to settle the problems and bring the parties to reconciliation.
Lack of attention to customers
Apparently, many cloud users do not feel that personal touch.
Thus, 44% of respondents answered that their provider does not know their company and does not understand their business needs, and 43% believe that if their organization were simply larger, then the supplier would probably pay more attention to them. In short, they feel the coldness of a bargain buying cloud services and they don't like it.
And one more thing: there is one practice, which was pointed out by a third of the companies surveyed, that also instills a feeling of pettiness in a transaction - they are charged a fee for the slightest question or incomprehensibility.
Too many secrets
A supplier's reluctance to provide all the information not only annoys customers, but often costs them money.
All respondents to the Forrester survey responded that they experience some financial impact and impact on their day-to-day operations from missing or disclosed data about their cloud usage.
“The lack of clear data on cloud usage is leading to performance issues, difficult reporting to management about actual cost of use, billing for resources that were never consumed by users, and unexpected bills,” says Forrester.
Where is the metadata?
CIOs responsible for cloud infrastructure in their organizations want cost and performance metrics that provide clarity and transparency, but they obviously have a hard time communicating this to vendors.
Survey participants noted that the metadata they receive about cloud workloads is usually incomplete. Nearly half of companies reported no compliance data, 44% lacked usage data, 43% no historical data, 39% security data, and 33% no billing and cost data.
The issue of transparency
The lack of metadata is causing all sorts of problems, respondents say. Nearly two-thirds of those surveyed reported that lack of transparency prevents them from fully understanding the full benefits of the cloud.
“The lack of transparency creates a variety of problems, primarily the issue of usage parameters and outages,” the report says.
Roughly 40% try to close these gaps themselves by purchasing additional tools from their own cloud providers, while another 40% simply purchase services from another provider where such transparency is present.
Compliance with regulations
Anyway, organizations are responsible for all of their data, whether on-premises storage or sent to the cloud.
More than 70% of the survey respondents said that their organizations are regularly audited and must confirm compliance with existing regulations wherever their data is located. And it poses a barrier to cloud adoption for nearly half of the companies surveyed.
“But the aspect of your compliance with regulations must be transparent to your end users. When cloud providers withhold or do not disclose this information, they prevent you from achieving it, ”the report said.
Compliance issues
More than 60% of companies surveyed said compliance issues are limiting continued adoption of the cloud.
The main problems are:
- 55% of companies faced with these requirements reported that it is most difficult for them to implement appropriate controls.
- Roughly half say they find it difficult to understand the compliance level of their cloud provider.
- Another half of the respondents answered that it is difficult for them to obtain the necessary documentation from the provider on compliance with these requirements in order to pass the audit. And 42% find it difficult to obtain documentation of their own compliance with workloads running in the cloud.
Migration issues
The on-boarding process appears to be another area of general dissatisfaction, with just over half of the companies surveyed responding that they are not satisfied with the migration and support processes that cloud providers have offered them.
Of the 51% dissatisfied with the migration process, 26% said it took too long and 21% complained about the lack of live participation from the provider's staff.
More than half were also dissatisfied with the support process: 22% indicated a long wait for a response, 20% indicated insufficient knowledge of support personnel, 19% indicated a lengthy problem-solving process, and 18% received invoices with higher than expected support costs.
Obstacles on the way to the cloud
Many of the companies Forrester surveyed are holding back their plans for cloud expansion because of the problems they are having with existing services.
At least 60% responded that a lack of transparency in use, regulatory compliance information, and robust support is holding them back from using the cloud more widely. If not for these issues, they would have moved more workloads to the cloud, respondents say.
2014
- The role of IT departments is gradually changing as they face the challenge of adapting to the new realities of cloud IT. IT departments must educate employees about security issues, develop comprehensive data governance and compliance policies, develop cloud implementation guidelines, and establish rules for what data can and cannot be stored in the cloud.
- IT departments are able to fulfill their mission of protecting corporate data and at the same time act as a tool in the implementation of "Shadow IT", implementing measures to ensure data security, for example, introducing an `encryption-as-a-service` approach. service "). This approach allows IT departments to centrally manage data protection in the cloud, allowing other parts of the company to independently find and use cloud services as needed.
- As more companies store their data in the cloud and their employees increasingly use cloud services, IT departments need to pay more attention to implementing better mechanisms to control user access, such as multi-factor authentication. This is especially true for companies that provide third parties and vendors with access to their data in the cloud. Multi-factor authentication solutions can be centrally managed and provide more secure access to all applications and data, whether they reside in the cloud or on a company's own hardware.
Ponemon and SafeNet data
Most IT organizations are unaware of how corporate data is protected in the cloud — as a result, companies put their users' accounts and confidential information at risk. This is just one of the findings of a recent fall 2014 study commissioned by the Ponemon Institute for SafeNet. The study, titled "Cloud Information Management Challenges: A Global Data Security Survey," surveyed more than 1,800 information technology and IT security professionals around the world.
Among other findings, the study found that while organizations are increasingly leveraging the power of cloud computing, corporate IT departments face challenges in managing and securing data in the cloud. The survey found that only 38% of organizations have clearly defined roles and responsibilities for protecting confidential and other sensitive information in the cloud. To make matters worse, 44% of corporate data stored in the cloud is not controlled or managed by IT departments. In addition, more than two-thirds (71%) of respondents noted that they face increasing difficulties when using traditional mechanisms and methods of ensuring security to protect confidential data in the cloud.
As the popularity of cloud infrastructures increases, so does the risk of confidential data leaksAbout two-thirds of IT professionals surveyed (71%) confirmed that cloud computing is of great importance to corporations today, and more than two-thirds (78%) believe that cloud computing will remain relevant and in two years. In addition, according to respondents, about 33% of all needs of their organizations for information technology and data processing infrastructure today can be met with the help of cloud resources, and over the next two years this share will increase to an average of 41%.
However, the majority of respondents (70%) agree that it is becoming more and more difficult to comply with the requirements for maintaining the confidentiality of data and protecting it in the cloud environment. In addition, the types of corporate data stored in the cloud, such as email addresses, customer and customer data, and payment information, are most at risk of leaks from respondents.
On average, more than half of all cloud services in enterprises are deployed by third-party departments rather than corporate IT departments, and on average, about 44% of corporate data hosted in the cloud is not controlled or managed by IT departments. As a result, only 19% of those surveyed could say they were confident they knew about all the cloud applications, platforms, or infrastructure services currently in use in their organizations.
Along with the lack of control over the installation and use of cloud services, there was no consensus among the respondents as to who is actually responsible for the security of data stored in the cloud. Thirty-five percent of respondents said that responsibility is shared between users and cloud providers, 33% believe that the responsibility rests entirely with the users, and 32% believe that the cloud provider is responsible for keeping data safe.
More than two-thirds (71%) of respondents noted that it is becoming more difficult to protect confidential user data stored in the cloud using traditional security tools and methods, and about half (48%) say that it is becoming more difficult for them to control or restrict for end users access to cloud data. As a result, more than a third (34%) of IT professionals surveyed said that their organizations have already implemented corporate policies that require the use of security mechanisms such as encryption as a prerequisite for working with certain cloud computing services. Seventy-one (71) percent of respondents indicated that the ability to encrypt or tokenize confidential or other sensitive data is of great importance to them, and 79% believe that the importance of these technologies will increase over the next two years.
When asked what exactly their companies are doing to protect data in the cloud, 43% of respondents said their organizations use private networks to transfer data. About two-fifths (39%) of respondents said their companies use encryption, tokenization, and other cryptographic tools to protect data in the cloud. Another 33% of those surveyed are unaware of what security solutions their organizations have in place, and 29% said they use paid security services provided by their cloud service providers.
Respondents also believe that managing corporate encryption keys is essential to securing data in the cloud, given the growing number of key management and encryption platforms in use in their companies. Specifically, 54% of respondents said their organizations retain control over encryption keys when storing data in the cloud. However, 45% of those surveyed said that they store their encryption keys in software, in the same place where the data itself is stored, and only 27% store keys in more secure environments, for example, on hardware devices.
When it comes to accessing data stored in the cloud, sixty-eight (68) percent of respondents say it is becoming more difficult to manage user accounts in a cloud environment, with sixty-two (62) percent of respondents saying they have access to the cloud in their organizations. provided for third parties as well. About half (46 percent) of those surveyed said their companies use multi-factor authentication to protect third-party access to data stored in the cloud. Approximately the same number (48 percent) of respondents said that their companies use multifactor authentication technologies, including to protect their employees' access to the cloud.
2013: Research of Cloud Security Alliance
The Cloud Security Alliance (CSA), a not-for-profit industry organization that promotes protection in the cloud, recently updated its list of top threats in a report entitled “Cloud Evil: Top 9 Threats in Cloud Services in 2013”.
CSA indicates that the report reflects the consensus of experts on the most significant security threats in the cloud and focuses on the threats arising from sharing cloud resources and being accessed by multiple users on demand.
So, the main threats ...
Data theft
Theft of confidential corporate information is always intimidating to organizations in any IT infrastructure, but the cloud model opens up "new, significant attack routes," the CSA points out. "If a multi-lease cloud database is not well thought out, a flaw in one client's application could give attackers access to not only that client's data, but all other cloud users," CSA warns.
Any "cloud" has several levels of protection, each of which protects information from different types of "attacks".
So, for example, the physical protection of the server. Here we are not even talking about hacking, but about theft or damage to information carriers. Moving the server out of the room can be difficult in the truest sense of the word. In addition, any self-respecting company stores information in data centers with security, video surveillance and restricted access not only to outsiders, but also to most of the company's employees. So the likelihood that an attacker will simply come and take the information is close to zero.
Just as an experienced traveler, fearing robbery, does not keep all money and valuables in one place,
Remuneration for labor is a motivating factor only if it is directly related to the results of labor. Employees must be convinced of a stable relationship between the material remuneration received and labor productivity. There must be a component in wages that depends on the results achieved. The Russian mentality is characterized by the desire for collective work, recognition and respect of colleagues, and so on.
Today, when high wages are difficult due to the difficult economic situation, special attention should be paid to non-material incentives, creating a flexible system of benefits for employees, humanizing labor, including:
1.recognize the value of the employee for the organization, provide him with creative freedom;
2. to apply programs of enrichment of labor and rotation of personnel;
3. use a sliding schedule, part-time work week, the opportunity to work both at the workplace and at home;
4. to establish discounts for employees on products manufactured by the company in which they work;
5. to provide funds for recreation and leisure, to provide free travel tickets, to issue loans for the purchase of housing, a garden plot, cars, and so on.
Below will be formulated the motivating factors of the organization of labor, which lead to the satisfaction of the needs of the highest levels.
At his workplace, everyone wants to show what he is capable of and what he means to others, therefore, it is necessary to recognize the results of the activity of a particular employee, to provide an opportunity to make decisions on issues related to his competence, to advise other employees. At workplaces, the worldview of a single team should be formulated: it is impossible to destroy the emerging informal groups if they do not cause real damage to the goals of the organization.
Almost everyone has their own point of view on how to improve their work. Relying on the committed support of the management, without fear of sanctions, work should be organized so that the employee does not lose the desire to implement his plans. Therefore, in what form, at what speed and in what way employees receive information, they assess their real significance in the eyes of management, therefore it is impossible to make decisions regarding changes in the work of employees without their knowledge, even if the changes are positive, as well as make it difficult to access the necessary information.
Information about the quality of an employee's work should be prompt, large-scale and timely. The employee should be given the greatest possible degree of self-control. Most people strive to acquire new knowledge in the process of work. Therefore, it is so important to provide subordinates with the opportunity to learn, to encourage and develop their creativity.
Every person strives for success. Success is accomplished goals, for the achievement of which the employee has made every effort. Success without recognition leads to disappointment, kills initiative. This will not happen if the subordinates who have achieved success are delegated additional rights and powers, and they are promoted up the career ladder.
CONCLUSION
The effectiveness of this or that motivational system in practice largely depends on the management bodies, although in recent years certain steps have been taken to increase the role of enterprises themselves to develop their own systems of motivation, which, at a specific period of time, make it possible to implement the goals and objectives of enterprises in conditions of market relations.
Now it is hardly necessary to convince anyone that motivation is the fundamental factor in motivating workers to work highly productively. In turn, the functioning of motivation systems, their development mainly depend on the employees of the management apparatus, on their qualifications, business qualities and other qualitative characteristics. At the same time, both in the period before Russia's transition to market relations, and at the present time, the problem of motivation remains the most urgent and, unfortunately, the most unresolved problem in practical terms. The solution to this problem mainly depends on ourselves. We ourselves are responsible for our lives and motivation to work. However, it seems that many of us spend too much time before daring to take primary responsibility for the content of our lives and the desire to work. We are accustomed to looking for the causes of our life and work problems at first outside of us.
The reasons are found quickly: close colleagues at work, bosses, subordinates, division of labor, atmosphere, management method, economic conditions, unreasonable government policy and many other factors that lie even outside our country. Many of us spend so much time explaining the effectiveness of our work or unwillingness to work, that during this time, if used correctly, we could achieve significantly higher motivation, both ourselves and those closest to us.
Send your good work in the knowledge base is simple. Use the form below
Students, graduate students, young scientists who use the knowledge base in their studies and work will be very grateful to you.
Similar documents
Essence, forms, principles and systems of remuneration. Analysis of the wage fund on the example of NKMZ JSC. The methods of remuneration of employees used in the enterprise. Directions for improving the system of remuneration and labor motivation in market conditions.
Analysis of the activities of OOO UMTS "Splav", characteristics of the system of organizing the accounting of wages. The system of wages as a necessary element of the organization of remuneration. Features of methods of motivating workers, the structure of the wage fund.
term paper, added 09/01/2012
The essence and content of the category "labor motivation". Motivation theories, their essence and meaning. Analysis of the current state of the system of labor motivation for workers in LLC "Svetlana". Strengthening motivational factors in the field of remuneration, the effectiveness of measures.
term paper, added 05/18/2010
Consideration of forms, sources of formation of wage funds, bonus systems and incentives for employees. Characteristics of production and economic activities of PA "Baker": analysis of the cost of production, profitability, organization and remuneration.
thesis, added 05/25/2010
The problem of stimulating labor in the economy. Characteristics of the traditional system of remuneration at the enterprise. Diagnostics of work motivation, value orientations and job satisfaction of company personnel. Development of a corporate remuneration system.
thesis, added 09/08/2010
The system of remuneration: types, forms and procedure for its calculation. The procedure for remuneration of workers in medical institutions. Accounting for financing in budgetary organizations, analysis of key indicators. Draft measures to improve the remuneration system.
thesis, added 12/22/2012
The essence and principles of remuneration in a market economy. Modern forms and systems of remuneration. Analysis of labor remuneration at OOO Sigma, Kostroma. Analysis of the system of remuneration of workers. Improvement of the remuneration system at the studied enterprise.
thesis, added 04/11/2012
All material motivation is based on the material reward of a person for his work. It can be carried out in the form of payment of wages, as well as in the form of social programs provided for by Russian legislation and the rules adopted in this organization.
Salary is the leading form of material motivation of personnel. It expresses in monetary terms the efforts and time that a person spends in the labor process.
Wages are the basic factor driving the need for work for most people.
But the very fact of obtaining it does not always ensure conscientious and productive work. Therefore, if we talk about wages as a factor that enhances the motivation of workers, it is necessary to establish the dependence of its size on the final result of labor. In this case, employees who perform their duties responsibly and showing high performance, will receive more pay than everyone else. This brings a sense of satisfaction with the results of their work to the "foremost workers" and serves as an incentive for the best work of the whole team.
In order to understand how you can practically implement this task, first we will analyze the basics of building wage systems in the organization.
The remuneration of employees in the organization is based on the legislation of the Russian Federation and is regulated by the state. State regulation extends to the establishment of the minimum wage, taxation of funds allocated by the organization for wages, the establishment of state guarantees of wages.
The standards confirming the previously listed functions are contained in the Labor Code of the Russian Federation and, as a rule, are fixed in labor and collective agreements that the organization concludes with its employees.
Compliance with legal norms is the basis for an organization to build a remuneration system for its employees, but in addition to legal norms, a number of factors must be taken into account.
The form of remuneration. There are two main forms of remuneration: time-based and piece-rate. Time-based pay involves the calculation of wages based on the cost of one hour of work or the salary for the actual hours worked. This form of wages is used when remunerating specialists and managers, since they do not produce specific products, which are counted in pieces, meters and kilograms. Their work is measured by the time spent on their work.
Piecework wages depend on the amount of products produced and calculated based on the unit cost of the product produced. By piecework wages, the work of workers is assessed, the results of which can be measured quantitatively.
Coverage of workers. Coverage of workers implies individual and collective remuneration. Individual payment is the calculation of wages for each specific employee. Collective pay is calculated based on the results of the work of a group and then distributed within this group according to the established rules.
Means of payment. Means of payment - cash and in-kind components. As a rule, wages are paid in cash, but by agreement with the employee and in accordance with the legislation of the Russian Federation, part of the payment in kind is possible - in goods, securities or services.
The duration of the billing period. The duration of the billing period is the frequency of payments. Labor remuneration can be daily, weekly, monthly.
The study and analysis of the listed factors makes it possible to develop and implement a payment system that would correspond to the goals and objectives of the organization, as well as its financial capabilities. But it is necessary not only to create a personnel remuneration system, but to make it so that it becomes a labor incentive.
To do this, during development, it is necessary to follow the rules that ensure an increase in the efficiency of workers' labor:
■ the wage system should orient the employee to achieve the desired result for the enterprise, therefore, the amount of wages is linked to the performance indicators of the entire organization (profit, sales volume, plan fulfillment);
■ the payment system should be a means of personnel management; for this, the manager needs to be able to both material incentives and punishments;
■ The remuneration system must meet the expectations of employees and be commensurate with conditions in other organizations.
As we have already said, the payment system at each enterprise has its own characteristics, reflecting the requirements of production, the type of activity and the adopted personnel policy.
Recently, however, many organizations have come to use a remuneration scheme, which involves the division of payments to staff into three parts.
First part is the base salary. It is paid for the performance of official duties and remains unchanged (with the exception of the piece-rate form of remuneration). All employees of the organization receive salaries.
Second part- these are preferential payments and compensations - a social package that the organization provides to its employees. This includes payments for vacations, sick leaves, meals, employee training, life and health insurance, and annual inflation compensation. The compensatory part of the remuneration is individual and depends on the number of years that the employee has worked and the availability of additional social programs adopted by the organization. All employees also receive the compensation part.
The third part- these are additional payments that the organization makes for labor achievements in the previous period. Additional payments can be made in the form of bonuses, percentages from sales of products, additional payments to leave, as well as allowances and coefficients for the complexity and quality of work performed. This part of payments is variable. It is different for all employees and depends on individual performance indicators. This part is received not by all employees, but only by those who have achieved certain results in their work.
The presented system of remuneration includes all types of payments to personnel established by law and makes it possible to stimulate the efficiency of employees through additional premiums for high-quality and productive work.
It should be noted that, when creating a remuneration system, the head of the organization and the personnel department need to remember that the meaning of monetary remuneration for the employee is not limited only to compensation for the costs of forces that he spends in the performance of his work. Monetary remuneration, forms of its receipt and size are perceived as evidence of its value for the organization, form self-esteem, and talk about social status. Thus, the money received by the employee is an indicator of personal and professional self-realization.
Bibliographic description:
A.K. Nesterov Personnel labor motivation in the organization [Electronic resource] // Educational encyclopedia site
Managing work motivation is a key factor in the organization's personnel management system, since there is a direct relationship between employee motivation and the efficiency of his work.
The concept and essence of labor motivation
Motivation Is the process of creating incentives to achieve set goals. Needs and motives are involved in the process of motivation. Needs are an inner drive to action. The process of motivation ends with the development of a motive; in addition to needs, value orientations, beliefs and views are also involved in this process. This is a hidden process, it is not observable and it cannot be determined empirically.
You can only see the result of motivation - human behavior.
Effective motivation affects not only the increase in the social and creative activity of a particular employee, but also the final results of the enterprise.
Each of the existing theories of motivation proceeds from the results of theoretical and applied certain aspects, laying them in the basis of its concept, however, a unified approach to the definition of the concept of motivation has not been developed.
Approaches to the definition of the concept of labor motivation
Within the framework of this article, we will use the following thesis that characterizes the essence of labor motivation.
Personnel labor motivation- This is a combination of internal and external driving forces that induce a person to carry out conscious activities.
As an element of the management system, personnel motivation is aimed at encouraging people to perform their work most effectively within the framework of their rights and obligations. In this regard, motivation directly affects - the employee's skills will not bring results if he is not interested in him. In managing an organization, a complex of internal and external factors is used to motivate personnel.
Separately, these factors are insignificant for a person and in modern conditions their impact is not so strong, but with a complex influence they multiply each other, creating a multiplier effect.
Personnel motivation theories
The table shows substantive and procedural theories of motivation, in which complexes of motives and incentives are formed, which act as elements of motivating staff labor in an organization.
|
1. The theory of needs A. Maslow |
||
|---|---|---|
|
Needs |
||
|
1.1. Physiological needs |
- quality food; - pure water; - good living conditions; - favorable conditions for rest. |
- fair salary; - housing loans; - sanatorium vouchers; - social package. |
|
1.2. Security needs |
- protection from physical and moral hazards from the environment; - confidence that physiological needs will be met. |
- good moral and psychological climate in the team; - democratic management style of the leader; - health insurance; - help in extreme situations |
|
1.3. Social needs |
- communication; - imitation; - involvement; - solidarity, support, friendship, mutual assistance. |
- the ability to communicate; - democratic leadership style; - equal opportunities, "equality of chances"; - Hall of Fame; - making gratitude; - recognition of merits; - fairness in everything (in the distribution of work, estimates, remuneration); - programs of cultural and recreational activities. |
|
1.4. Needs for recognition and respect |
- self-respect; - personal achievements; - competence; - respect from others; - recognition. |
- decent salary; - expansion of powers; - personal benefits; - an increase in the number of subordinates; - universal recognition and respect. |
|
1.5. Needs of self-expression |
–Realization of potential opportunities; - personal growth; - vocation; - self-expression; - curiosity; - creation; - invention; - innovation; - doing science. |
- participation in management and decision-making; - participation in project teams; - ample opportunities for training and advanced training; - active career growth; - provision of work according to interests, vocation; - vocational guidance; - increasing the creative nature of work; - taking into account the personal qualities and abilities of the employee; - prizes for innovation, inventions, discoveries; - nomination for state and international awards. |
|
2. The theory of existence, connection and growth by K. Alderfer |
||
|
Needs |
||
|
2.1. The necessities of existence: physiological, security security, salary |
- food, water, shelter, rest; - protection from physical hazards; - confidence that physiological needs will be met. |
- a sufficient level of salary; - payment for housing; - social package; - the pension system; - health insurance. |
|
2.2. Communication needs: establishment contacts, respect, appreciation personality |
- communication; - involvement; - support, friendship, mutual assistance. |
- the ability to communicate; - a favorable psychological climate in the team; - equal opportunities; - making gratitude; - recognition of merits. |
|
2.3. Growth needs: development creative potential, self-realization |
- respect, recognition; - realization of potential opportunities; - personal growth; - self-expression, creativity. |
- universal recognition and respect; - the right to implement their proposals; - opportunities for training and professional development; - awards for inventions. |
|
3. D. McClelland's theory of acquired needs |
||
|
Needs |
||
|
3.1. The need for power |
- the desire to influence other people, to feel useful and significant |
- participation in management and decision-making; - expansion of powers; - an increase in the number of subordinates. |
|
3.2. The need for success |
- participation in promising works; - goal achievement; - prestige; - career development. |
Providing initiative, broad powers; Reward for results; Participation in success; International recognition; Awarded the title of "Best Employee of the Year". |
|
3.3. Need for involvement |
- communication; - imitation; - involvement; - solidarity, support, friendship. |
- the ability to communicate; - favorable social microclimate; - participation in management and decision-making; - holding meetings; - helping others; - business contacts. |
|
4. The theory of two factors F. Herzberg |
||
|
Needs |
||
|
4.1. Hygienic |
- career advancement; - recognition and approval of the results of work; - a high degree of responsibility; - opportunities for creative and business growth. |
- good moral and psychological climate; - normal working conditions; - fair salary; - friendly atmosphere; - moderate control over work. |
|
4.2. Motivation |
- provision of initiative, broad powers; - reward for results; - participation in success; - career planning; - fair remuneration; - providing a high degree of responsibility; - study and professional development. |
|
|
Procedural theories of motivation |
||
|
5. Theory of expectations by V. Vroom |
||
|
Needs |
||
|
5.1. Cost - results |
- the significance of the task; - the feasibility of the task; - carrying out the necessary consultations. |
- evaluation of results |
|
5.2. Reward results |
- certainty and timeliness of remuneration. |
- trust in the leader; - the efficiency of the enterprise. |
|
5.3. Valence |
- remuneration for the achieved work performance. |
- guarantee of remuneration; - exact correspondence of remuneration to the results of work. |
|
6. The theory of justice by S. Adams |
||
|
Needs |
||
|
- correspondence of remuneration to the average value of remuneration of other specialists for similar work. |
Application of compensation wages at the "market price" of the employee. |
|
|
7. The concept of participatory governance |
||
|
Needs |
||
|
- awareness of the importance and significance of their work for the development of the enterprise |
- participation in management and decision-making; - participation in projects; - self-control; - personal and group responsibility for the results. |
|
Source: Vikhansky, O.S. Management: textbook / O.S. Vikhansky, A.I. Naumov. - 5th ed., Stereotype. - M .: Master: INFRA -M, 2012.
The construction of a motivation system according to meaningful theories of motivation is based on the identification and satisfaction of the dominant needs of employees, and procedural theories of motivation assign a key role to the formation of motivational behavior of employees.
Methods of motivating personnel in the organization
The methods of labor motivation are presented as managerial regulatory influences of three types: passive, indirect and active.
- Passive influences do not affect employees, but are aimed at creating working conditions and include the development of norms, rules, regulations relating to personnel labor.
- Indirect influences affect the employees of the organization indirectly and are implemented in the form of complex bonus programs, incentives aimed at the collective of the enterprise as a whole.
- Active influences imply a direct impact on specific employees or groups of employees.
Motivation methods are presented in the diagram
Staff motivation methods
Economic methods of motivation are based on obtaining certain benefits for employees, which increases their well-being.
Direct forms of economic methods:
- basic wages;
- additional payments, taking into account the complexity of work and qualifications, excess work, etc .;
- remuneration in the form of bonuses and payments depending on the employee's contribution to the results of the production activity of the enterprise;
- other types of payments.
Indirect forms of economic methods:
- provision of a company car for use;
- use of social institutions of the organization;
- purchase of the organization's products at a price lower than the selling price;
- providing various benefits.
Organizational methods:
- Motivation by interesting goals for the main work of employees;
- Motivation by enriching the content of labor activity;
- Motivation by participation in the affairs of the organization.
Moral psychological methods:
- Pride in the work entrusted and performed;
- Responsibility for the results of work;
- A challenge, an opportunity to show your abilities;
- Acknowledgment of authorship of the result of the work or project done;
- High rating, can be personal or public.

Requirements for the methods of motivating the work of the organization's personnel
Directions for improving and increasing the efficiency of personnel labor motivation in the organization
Employee motivation system Is a flexible personnel management tool focused on achieving the goals of the company using administrative, economic and socio-psychological methods.
Enterprises need to build an effective human resource management system that would ensure the activation of the human factor; for this, organizations use methods of staff motivation in order to orient people to the most effective solution of the assigned tasks. Labor motivation is aimed at increasing labor productivity, increasing the profits of the organization, which ultimately leads to the achievement of the strategic goals of the organization.
The main problem is the issue of creating an effective and efficient system of staff motivation in the organization. Since every manager strives to ensure that the employee does not lose interest in work, organizations develop special events and a motivation system is built to keep employees interested in work.
An earlier study found that there is a stable relationship between, it is expressed through the types of motivation and factors affecting interest in work.
An ineffective motivation system leads to a decrease in labor productivity, therefore, the importance of the rational use of effective methods of stimulating labor is obvious.
The interdependence of the motivation of employees and the results of the economic activity of the organization is the basis of the enterprise.

The task of any manager is to organize the work process so that people work effectively. The productivity and climate of relationships in the enterprise directly depend on how much the employees agree with their position in the company and the existing incentive system. This, in turn, affects the reduction of the rigid formalization of intrafirm relations, aimed at transforming them in the context of objective reality in an enterprise.
The typical direction of improving the system of personnel labor motivation in the organization is the expansion of the forms and type of incentives. For example, if material incentives are most pronounced in the enterprise motivation system or non-material types of incentives are practically absent, it is necessary to use more types of moral incentives for employees, for example:
- Putting various records of the employee's achievements in his personal file.
- Oral thanks on behalf of the company's management.
- Additional training at the expense of the organization.
- A paid invitation to dinner at a restaurant that the company gives out to the employee.
- Flexible working hours.
- Providing a car park and free gasoline.
- Higher quality of workplace equipment, as well as the purchase of new equipment for the best employees at the end of the year.
- Placement of a photo in a wall newspaper.
- A souvenir with a special mark "Best Employee".
- Placing grateful customer feedback in a way that everyone can see.
- Subscription to specialized periodicals.
To increase the motivation of employees, it is necessary to create conditions for the self-expression of employees, provide them with a certain initiative in making decisions and create conditions for employees to have the opportunity to influence the processes taking place in the company. To do this, the director can delegate some of his powers directly to the heads of the company's divisions.
It will be useful for the leader to use some significant events in the personal life of subordinates (birthdays, weddings, etc.) in order to show attention to them, to congratulate them all as a team. On the part of employees, such actions are also possible.
Also, in order to increase the involvement of employees in the company's affairs, it is necessary to introduce a system of actions denoted by the term "open door policy". This means the readiness of a leader of any rank to listen to the suggestions of his subordinates. The motto of this policy is: "The doors of my office are always open for you." However, the question arises as to how this relates to the manager's time resource. Indeed, what if the subordinates decide that they can enter the chief’s office whenever they want. In fact, if employees are busy, they visit the manager's office much less often than you might expect. In addition, you can use some techniques to organize this kind of contacts:
- The manager can set the time of the meeting himself, not denying the employee an audience, but postponing it at a convenient time for him.
- The use of written forms of presentation of information also helps to reduce communication with subordinates. Presenting ideas in writing is characterized by conciseness and definiteness.
- Evaluation and promotion of specific business proposals. Sometimes, when submitting an idea, employees accompany it with a large amount of related information, although you only need to specifically state the essence.
Increasing employee motivation through methods of moral incentives and the implementation of an "open door" policy at all levels of management will significantly increase the participation of employees in the organization as a whole, as well as in decisions made by managers. This will contribute to the optimization of intra-firm relations through subjective-objective methods of achieving a balance in formal and informal relationships that exist in the organization. It will also improve the quality of information available to management and necessary for decision-making. Moral incentives will also help employees feel committed to the goals and values of the organization.
A promising direction for increasing the efficiency of the personnel motivation system is the implementation of the personnel adaptation program. Even if there is no separate service for managing the adaptation of personnel in the enterprise, then the work of adaptation of a new employee can be performed by an employee of the personnel department.
An onboarding program is a set of specific actions that need to be performed by an employee responsible for onboarding. The adaptation program is divided into general and special. The general adaptation program applies to the whole organization as a whole, and it includes such issues as a general idea of the company, organization policy, remuneration, additional benefits, labor protection and safety, working conditions of an employee in the organization, service of everyday life, economic factors.
A special adaptation program covers issues related specifically to any department or workplace and is carried out both in the form of special conversations with employees of the department in which the newcomer came, and interviews with the head (immediate and higher). But the organization of these conversations is entrusted to the employee of the personnel department. The main issues that need to be highlighted in the process of a special adaptation program are: the functions of the unit, work duties and responsibilities, the required reporting, procedures, rules, regulations and representation of the employees of the unit.
Wages are the most important part of the system of remuneration and incentives for labor, one of the tools for influencing the efficiency of an employee's work. This is the pinnacle of the company's personnel incentive system, but for all its significance, wages in most successful foreign firms do not exceed 70% of the employee's income, the remaining 30% of income is involved in the distribution of profits.
In order for wages to fulfill their motivating function, there must be a direct link between its level and the qualifications of the employee, the complexity of the work performed, and the degree of responsibility.
The remuneration system is understood as a method of calculating the amount of remuneration to be paid to employees of an enterprise in accordance with the labor input they have made or according to the results of labor.
There are two systems for organizing remuneration: tariff and non-tariff. Tariff system allows you to measure a variety of specific types of work, taking into account their complexity and conditions of performance, that is, take into account the quality of work. It is the most common in domestic enterprises.
The most widespread at enterprises of various forms of ownership are two forms of the tariff system of remuneration:
Piecework - for each unit of production or the amount of work performed;
Time-based - for the standard hours worked, which is provided for by the tariff system.
At each specific enterprise, depending on the nature of the products, the presence of certain technological processes, the level of organization of production and labor, one or another form of wages is used.
In terms of wages and salaries, it is quite difficult to get rid of equalization, to overcome the contradiction between the interests of an individual employee and the entire team.
As a possible option for improving the organization and stimulating labor, use tariff-free wage system , which has found application at many enterprises in the transition to market conditions of management. Under this system, the wages of all employees of an enterprise, from director to worker, represent the employee's share in the wage bill (payroll) or the entire enterprise or a separate subdivision. Under these conditions, the actual value of the wages of each employee depends on a number of factors:
The qualification level of the employee;
Labor participation rate (KTU);
Actual hours worked.
The qualification level of an employee of an enterprise is established for all members of the labor collective.
All employees of the enterprise are divided into ten qualification groups, based on the qualification level of employees and qualification requirements for employees of various professions. For each of the groups, its own qualification level is established, which can be increased throughout the course of his labor activity. The system of qualification levels creates great opportunities for material incentives for more qualified labor than the system of wage grades.
KTU is exposed to all employees of the enterprise, including the director, and is approved by the council of the labor collective, which itself decides the frequency of its determination (once a month, quarterly, etc.) and the composition of indicators for its calculation.
A variation of the tariff-free system is contractual remuneration system, aimed at attracting and retaining highly qualified personnel at enterprises, mainly managers and specialists, at forming a team of professionals who are able to achieve ever higher goals in a tough competition. It is based on the conclusion of an agreement (contract) between the employer and the employee, which stipulates the working conditions , the rights and obligations of the parties, the level of remuneration, etc. Compared with the tariff system of remuneration in our economy in its time-based and piece-rate forms, the contract system has two undoubted advantages. Firstly, workers can be paid much more than it is prescribed by salaries, tariff rates and rates under the existing state payment system. Secondly, the contract system makes it easy and simple to get rid of a negligent employee by terminating the contract, without conflicting with the Labor Code, without coordinating this dismissal with the trade union. These advantages make the contract system extremely attractive for those enterprises that really want to achieve dramatic improvements in production efficiency.
Subscribe to news