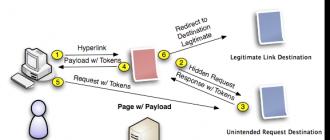
The methods of protecting information at the enterprise, as well as the methods of obtaining it, are constantly changing. New offers from companies providing information security services appear regularly. Of course, there is no panacea, but there are several basic steps to building the protection of an enterprise information system, which you definitely need to pay attention to.
Many are probably familiar with the concept of deep protection against hacking of an information network. Its main idea is to use several levels of defense. This will allow, at a minimum, to minimize the damage associated with a possible violation of the security perimeter of your information system.
Next, we will consider the general aspects of computer security, and also create a certain checklist that serves as the basis for building the basic protection of an enterprise information system.
1. Firewall (firewall, firewall)
A firewall or firewall is the first line of defense that meets intruders.
According to the level of access control, the following types of firewalls are distinguished:
- In the simplest case, the filtering of network packets occurs according to the established rules, i.e. based on source and destination addresses of network packets, network port numbers;
- A stateful firewall. It monitors active connections and drops spoofed packets that violate TCP / IP specifications;
- Application-level firewall. Filters based on the analysis of application data passed within the packet.
The increased attention to network security and the development of e-commerce has led to the fact that an increasing number of users use encrypted connections (SSL, VPN) for their protection. This makes it quite difficult to analyze traffic passing through firewalls. As you might guess, the same technologies are used by malicious software developers. Viruses that use traffic encryption have become practically indistinguishable from legitimate user traffic.
2. Virtual Private Networks (VPN)
Situations when an employee needs access to company resources from public places (Wi-Fi at an airport or hotel) or from home (your administrators do not control the employees' home network) are especially dangerous for corporate information. To protect them, you just need to use encrypted VPN tunnels. Direct access to remote desktop (RDP) without encryption is out of the question. The same applies to the use of third-party software: Teamviewer, Aammy Admin, etc. to access the work network. The traffic through these programs is encrypted, but passes through the servers of the developers of this software beyond your control.
Disadvantages of a VPN include the relative complexity of deployment, additional costs for authentication keys, and an increase in Internet bandwidth. Authentication keys can also be compromised. Stolen mobile devices of a company or employees (laptops, tablets, smartphones) with pre-configured VPN connection settings can become a potential hole for unauthorized access to company resources.
3. Intrusion detection and prevention systems (IDS, IPS)
Intrusion Detection System (IDS) is a software or hardware tool designed to detect the facts of unauthorized access to a computer system (network), or unauthorized control of such a system. In the simplest case, such a system helps detect network port scans on your system or attempts to log on to the server. In the first case, this indicates an initial reconnaissance by the attacker, and in the second, an attempt to hack your server. You can also detect attacks aimed at elevating privileges on the system, unauthorized access to important files, and malicious software activity. Advanced network switches allow intrusion detection systems to be connected using port mirroring or traffic taps.
Intrusion Prevention System (IPS) is a software or hardware security system that actively blocks intrusions as they are detected. If an intrusion is detected, suspicious network traffic can be automatically blocked, and a notification about this is immediately sent to the administrator.
4. Antivirus protection
Antivirus software is the main line of defense for most businesses today. According to the research company Gartner, the volume of the antivirus software market in 2012 amounted to $ 19.14 billion. The main consumers are the segment of medium and small businesses.
First of all, anti-virus protection is aimed at client devices and workstations. Business versions of anti-viruses include centralized management functions for transmitting anti-virus database updates to client devices, as well as the ability to centrally configure security policies. The range of antivirus companies includes specialized solutions for servers.
Given that most malware infections occur as a result of user actions, antivirus suites offer comprehensive protection options. For example, protection of e-mail programs, chat rooms, checking sites visited by users. In addition, anti-virus packages increasingly include software firewalls, proactive defense mechanisms, and spam filtering mechanisms.
5. White lists
What are whitelisting? There are two main approaches to information security. The first approach assumes that the operating system is allowed to run any applications by default, if they are not previously blacklisted. The second approach, on the other hand, assumes that only those programs that were previously included in the "white list" are allowed to run, and all other programs are blocked by default. The second approach to security is, of course, more preferable in the corporate world. Whitelists can be created using either the built-in tools of the operating system or third-party software. Antivirus software often offers this feature in its composition. Most antivirus applications that offer whitelisting filtering allow for very quick initial configuration with minimal user attention.
However, there may be situations in which the dependencies of the whitelisted program files have not been correctly identified by you or the antivirus software. This will cause the application to crash or not install correctly. In addition, whitelisting is powerless against attacks that exploit document processing vulnerabilities by whitelisted programs. You should also pay attention to the weakest link in any protection: employees themselves in a hurry can ignore the warning of antivirus software and add malicious software to the whitelist.
6. Filtering spam
Spam mailings are often used to carry out phishing attacks that are used to inject a Trojan or other malware into a corporate network. Users who process large amounts of email on a daily basis are more susceptible to phishing emails. Therefore, the task of the company's IT department is to filter out the maximum amount of spam from the general e-mail flow.
The main ways to filter spam:
- Specialized providers of spam filtering services;
- Spam filtering software on our own mail servers;
- Specialized hardware solutions deployed in a corporate data center.
7. Software support up to date
Timely software updates and the application of the latest security patches are an important element in protecting your corporate network from unauthorized access. Software vendors usually do not provide complete information about the newly discovered security hole. However, a general description of the vulnerability is enough for cybercriminals to write software to exploit this vulnerability literally in a couple of hours after the publication of a description of a new hole and a patch to it.
In fact, this is a rather big problem for small and medium-sized businesses, since a wide range of software products from different manufacturers are usually used. Often, updates of the entire software fleet are not given due attention, and this is practically an open window in the enterprise security system. Currently, a large number of software is independently updated from the manufacturer's servers and this removes part of the problem. Why part? Because the servers of the manufacturer can be hacked and, under the guise of legal updates, you will receive fresh malware. And also the manufacturers themselves sometimes release updates that disrupt the normal operation of their software. In critical areas of the business, this is unacceptable. To prevent such incidents, all received updates, firstly, must be applied immediately after their release, and secondly, they must be thoroughly tested before being applied.
8. Physical security
The physical security of a corporate network is one of the most important factors that cannot be overestimated. Having physical access to a network device, an attacker, in most cases, will easily gain access to your network. For example, if there is physical access to the switch and the network does not filter MAC addresses. Although MAC filtering will not save you in this case. Another problem is theft or neglect of hard drives after replacement in a server or other device. Given that the passwords found there can be decrypted, server cabinets and rooms or equipment boxes must always be reliably protected from intruders.
We have touched on just a few of the most common security aspects. It is also important to pay attention to user training, periodic independent audit of information security, creation and adherence to a reliable information security policy.
Please note that protecting your corporate network is a complex topic that is constantly changing. You need to be sure that the company does not depend on just one or two lines of defense. Always try to keep up with the latest information and fresh solutions in the information security market.
Take advantage of reliable protection of your corporate network within the framework of the service "servicing corporate computers" in Novosibirsk.
If we consider the information security system of any large company, then this is not only an antivirus, but also several other programs for protection in all directions. The time for simple IT security solutions is long gone.
Of course, the basis of a general information security system for any organization is the protection of a standard workstation from viruses. And here the need to use an antivirus remains unchanged.
But the requirements for corporate security in general have changed. Companies need complete end-to-end solutions that can not only protect against today's most complex threats, but also stay ahead of the curve.
"More and more large companies are building a security system based on the defense-in-depth principle."
Moreover, earlier echelons were lined up on various elements of the IT infrastructure, but now multilevel protection should be even on individual elements of the IT environment, primarily on workstations and servers.
What threats faced companies in 2014
In terms of threats, targeted attacks on corporations and government structures have become a huge information security problem in recent years. Many of the techniques that hackers used to attack home users are now being applied to businesses as well.
These include modified banking Trojans that target employees of financial departments and accounting departments, and various ransomware programs that began to work within corporate information networks, and the use of social engineering methods.
In addition, network worms have gained popularity, and in order to remove them, the entire corporate network must be shut down. If a similar problem is faced by companies with a large number of branch offices located in different time zones, then any network interruption will inevitably lead to financial losses.
According to a study conducted by Kaspersky Lab in 2014 among information security specialists, most often Russian companies are faced with
- malware,
- unwanted mail (spam),
- attempts to unauthorized entry into the system by phishing.
- vulnerabilities in the installed software,
- risks associated with the behavior of company employees.
The problem is aggravated by the fact that cyber threats are far from static: they multiply every day, become more diverse and complex. To better understand the current situation in the field of information security and the consequences to which even a single computer incident can lead, let us present everything in figures and facts obtained on the basis of data from Kaspersky Lab on the analysis of the events of 2014.
Cyber Threat Statistics

By the way, it is mobile devices that continue to be a separate "headache" for information security specialists today. The use of personal smartphones and tablets for work purposes is already permissible in most organizations, but proper management of these devices and their inclusion in the general information security system of a company is not practiced everywhere.
"According to data from Kaspersky Lab, 99% of malware specializing in mobile devices is currently targeting the Android platform."

To understand where such a number of threats come from, and to imagine how fast they are increasing in number, it is enough to say that every day Kaspersky Lab specialists process 325,000 samples of new malware.
Malware most often reaches users' computers in two ways:
- through vulnerabilities in legal software
- using social engineering methods.
Of course, a combination of these two techniques is very common, but attackers do not neglect other tricks either.
Targeted attacks, which are becoming more common, are a separate threat to businesses.
"The use of illegal software, of course, further increases the risks of becoming a successful target for a cyberattack, primarily due to the presence of more vulnerabilities in it."
 Vulnerabilities sooner or later appear in any software. These can be errors during the development of the program, obsolete versions or individual code elements. Be that as it may, the main problem is not the presence of a vulnerability, but its timely detection and closure.
Vulnerabilities sooner or later appear in any software. These can be errors during the development of the program, obsolete versions or individual code elements. Be that as it may, the main problem is not the presence of a vulnerability, but its timely detection and closure.
By the way, recently, and 2014 is a vivid evidence of this, software manufacturers are increasingly beginning to close the vulnerabilities in their programs. However, application gaps are still abundant, and cybercriminals are actively using them to penetrate corporate networks.
In 2014, 45% of all vulnerability incidents were triggered by holes in the popular Oracle Java software.
In addition, in the past year, there was a kind of turning point - a vulnerability was discovered in the popular encryption protocol OpenSSL, called Heartbleed. This bug allowed an attacker to read the contents of memory and intercept personal data on systems using vulnerable versions of the protocol.
OpenSSL is widely used to protect data transmitted over the Internet (including information that the user exchanges with web pages, emails, messages in Internet messengers), and data transmitted over VPN (Virtual Private Networks) channels, therefore potential damage from this vulnerability was huge. It is possible that attackers could use this vulnerability as a start for new cyber espionage campaigns.
Attack victims
In general, in 2014, the number of organizations that have become victims of targeted cyber attacks and cyber espionage campaigns increased by almost 2.5 times. Over the past year, almost 4.5 thousand organizations in at least 55 countries, including Russia, have become the target of cybercriminals.
Data theft has occurred in at least 20 different sectors of the economy:
- state,
- telecommunication,
- energy,
- research,
- industrial,
- healthcare,
- construction and other companies.
Cybercriminals gained access to such information:
- passwords,
- files,
- geolocation information,
- audio data,
- screenshots
- webcam snapshots.
Most likely, in some cases these attacks were supported by government agencies, while others were more likely carried out by professional groups of cyber mercenaries.
In recent years, Kaspersky Lab's Global Threat Research and Analysis Center has tracked the activities of more than 60 criminal groups responsible for cyberattacks around the world. Their participants speak different languages: Russian, Chinese, German, Spanish, Arabic, Persian and others.
The consequences of targeted cyber espionage operations and campaigns are always severe. They inevitably end in hacking and infection of the corporate network, disruption of business processes, leakage of confidential information, in particular intellectual property. In 2014, 98% of Russian companies encountered some kind of cyber incidents, the sources of which were usually located outside the enterprises themselves. In addition, another 87% of organizations had incidents caused by internal threats.
"The total amount of damage for large companies averaged 20 million rubles for each successful example of a cyber attack."
What companies fear and how things really are
Every year Kaspersky Lab conducts research in order to find out the attitude of IT specialists to information security issues. A 2014 study showed that the vast majority of Russian companies, or rather 91%, underestimate the amount of malware that exists today. Moreover, they do not even assume that the number of malware is constantly increasing.


Curiously, 13% of IT professionals said they weren't worried about internal threats.
Perhaps this is due to the fact that in a number of companies it is not customary to separate cyber threats into external and internal. In addition, there are those among Russian IT and information security managers who still prefer to solve all problems with internal threats by means of prohibitions.
However, if something is forbidden to a person, this does not mean that he does not do it. Therefore, any security policy, including prohibition, requires appropriate control tools to ensure that all requirements are met.
As for the types of information that cybercriminals are primarily interested in, the study has shown that companies' perceptions and the actual state of affairs are quite different.
So, the companies themselves are most afraid of losing
- customer information,
- financial and operational data,
- intellectual property.
- information on the analysis of competitors' activities,
- payment information,
- personal data of employees
- data on corporate bank accounts.
"In fact, it turns out that cybercriminals most often steal internal operational information of companies (in 58% of cases), but only 15% of companies consider it necessary to protect this data in the first place."
For safety, it is equally important to think over not only technologies and systems, but also to take into account the human factor: the understanding of the goals by the specialists who build the system, and the understanding of the responsibility of the employees who use the devices.
 Recently, attackers are increasingly relying not only on technical means, but also on the weaknesses of people: they use social engineering methods that help to extract almost any information.
Recently, attackers are increasingly relying not only on technical means, but also on the weaknesses of people: they use social engineering methods that help to extract almost any information.
Employees, taking away data on their device, should understand that they bear exactly the same responsibility as if they took paper copies of documents with them.
The company's personnel should also be well aware that any modern technically complex device contains defects that can be exploited by an attacker. But in order to take advantage of these defects, an attacker must gain access to the device. Therefore, when downloading mail, applications, music and pictures, you must check the reputation of the source.
It is important to be wary of provocative SMS and emails and to check the source's credibility before opening an email and following a link.
In order for the company to still have protection against such accidental or intentional actions of employees, it should use modules to protect data from leaks.
"Companies need to regularly remember about working with personnel: starting with improving the qualifications of IT employees and ending with explanations of the basic rules for safe working on the Internet, no matter what devices they use to get there."
For example, this year Kaspersky Lab released a new module that implements data leakage protection functions -
Cloud protection
 Many large companies use the cloud in one way or another, in Russia most often in the form of a private cloud. It is important to remember here that, like any other human-made information system, cloud services contain potential vulnerabilities that can be exploited by virus writers.
Many large companies use the cloud in one way or another, in Russia most often in the form of a private cloud. It is important to remember here that, like any other human-made information system, cloud services contain potential vulnerabilities that can be exploited by virus writers.
Therefore, when organizing access even to your own cloud, you need to remember about the security of the communication channel and about the end devices that are used on the side of employees. Equally important are internal policies governing which employees have access to data in the cloud, or what level of secrecy information can be stored in the cloud, etc. The company should formulate transparent rules:
- what services and services will run from the cloud,
- what - on local resources,
- what information should be placed in the clouds,
- what should be kept "at home".
Based on the article: Time for "hard" decisions: security in the Enterprise segment.
In an effort to ensure the company's viability, security services are focusing on securing the network perimeter - services accessible from the Internet. The image of a gloomy attacker who is ready to attack the published services of the company from anywhere in the world scares business owners in earnest. But how fair is this, given that the most valuable information is not located on the perimeter of the organization, but in the depths of its corporate networks? How to assess the proportionality of infrastructure protection against external and internal attacks?
"A ship in port is safe, but ships are not built for this purpose"
Feeling safe is deceiving
In the context of total informatization and globalization, business makes new demands on corporate networks; flexibility and independence of corporate resources in relation to its end users: employees and partners come to the fore. For this reason, today's corporate networks are very far from the traditional notion of isolation (despite the fact that they were originally defined as such).
Imagine an office: walls protect from the outside world, partitions and walls divide the total area into smaller specialized zones: kitchen, library, service rooms, workplaces, etc. The transition from zone to zone occurs in certain places - in doorways, and, if necessary, it is also controlled there by additional means: video cameras, access control systems, smiling guards ... Entering such a room, we feel safe, there is a feeling of trust and goodwill. However, it should be admitted that this feeling is only a psychological effect based on the "theater of security", when the goal of the measures being taken is to increase security, but in fact only an opinion is formed about its existence. After all, if an attacker really wants to do something, then being in the office will not become an insurmountable difficulty, and perhaps even on the contrary, there will be additional opportunities.
The same thing happens on corporate networks. In an environment where there is a possibility of being inside a corporate network, classical approaches to security are insufficient. The fact is that protection methods are built on the basis of an internal threat model and are aimed at counteracting employees who, accidentally or deliberately, but without proper qualifications, violate the security policy. But what if there is a skilled hacker inside? The cost of penetrating the network perimeter of an organization in the underground market has an almost fixed price for each organization and does not exceed $ 500 on average. So, for example, in the black market of hacker services from Dell for April 2016, the following price list is shown:
As a result, you can buy hacking a corporate mailbox, the account from which is likely to fit all other corporate services of the company due to the common principle of Single Sign-on authorization. Or purchase polymorphic viruses that are not tracked by antiviruses and infect unwary users with the help of phishing mailings, thereby taking control of a computer within the corporate network. For well-protected network perimeters, the flaws of human consciousness are used, for example, by purchasing new identification documents and obtaining data about the work and personal life of an organization employee through ordering cyber espionage, you can use social engineering and obtain confidential information.
Our experience with penetration tests shows that the outer perimeter is overcome in 83% of cases, and in 54% this does not require highly qualified training. At the same time, according to statistics, approximately every fifth employee of the company is willing to deliberately sell their credentials, including from remote access, thereby enormously simplifying overcoming the network perimeter. Under such conditions, internal and external attackers become indistinguishable, which poses a new challenge to the security of corporate networks.
Take critical data and not protect
Within the corporate network, logins to all systems are monitored and accessible only to already authenticated users. But this very check turns out to be the usual "theater of security" mentioned earlier, since the real state of affairs looks very gloomy, and this is confirmed by the statistics of the vulnerabilities of corporate information systems. Here are some of the major disadvantages of corporate networks.
- Dictionary passwords
Oddly enough, the use of weak passwords is common not only for ordinary company personnel, but also for IT administrators themselves. So, for example, often the passwords set by the manufacturer by default remain in services and equipment, or the same elementary combination is used for all devices. For example, one of the most popular combinations is admin with admin or password. Also popular are short passwords consisting of lowercase letters of the Latin alphabet and simple numeric passwords such as 123456. Thus, you can brute force a password quickly enough to find the correct combination and gain access to corporate resources.
- Storing critical information within the network in clear text
Imagine a situation: an attacker gained access to the internal network, there can be two scenarios for the development of events. In the first case, the information is stored in an open form, and the company immediately bears serious risks. Otherwise, the data on the network is encrypted, the key is stored in a different place - and the company has the chance and time to resist the attacker and save important documents from theft.
- Using outdated versions of operating systems and their components
Every time an update is released, a whitepaper is released at the same time that it details what bugs and bugs have been fixed in the new version. If a security issue is discovered, attackers begin to actively research the topic, find related bugs, and develop hacking tools on this basis.
Up to 50% of companies either do not update their software, or they do it too late. In early 2016, the Royal Melbourne Hospital suffered from the fact that its computers were running Windows XP. Initially hitting the computer of the pathology department, the virus rapidly spread over the network, blocking the automated operation of the entire hospital for some time.
- Using self-developed business applications without security control
The main task of our own development is functional performance. Such applications have a low security threshold, and are often released in conditions of scarcity of resources and proper support from the manufacturer. The product actually works, performs tasks, but at the same time it is very easy to hack it and get access to the necessary data.
- Lack of effective anti-virus protection and other means of protection
It is believed that what is hidden from the outside is protected, that is, the internal network is, as it were, safe. Security guards closely monitor the outer perimeter, and if it is so well guarded, then the internal hacker will not get into. And in fact, in 88% of cases, companies do not implement vulnerability detection processes, there are no intrusion prevention systems and centralized storage of security events. Taken together, this does not effectively ensure the security of the corporate network.
At the same time, the information that is stored within the corporate network has a high degree of significance for the operation of the enterprise: customer bases in CRM systems and billing, critical business indicators in ERP, business communication in mail, document flow contained on portals and file resources, etc. NS.
The line between the corporate and the public network has become so blurred that it has become very difficult and expensive to fully control its security. After all, they almost never use countermeasures against theft or trading of accounts, negligence of a network administrator, threats implemented through social engineering, etc. What makes attackers use these methods of overcoming external protection and get closer to vulnerable infrastructure with more valuable information.
The solution can be the concept of information security, in which the security of the internal and external networks is ensured on the basis of a single threat model, and with the likelihood of transformation of one type of attacker into another.
Attackers versus defenders - who will take it?
Information security as a state is possible only in the case of the elusive Joe - because of his uselessness. The confrontation between attackers and defenders takes place on fundamentally different levels. Attackers benefit from a breach of confidentiality, availability, or integrity of information, and the more efficient and effective they are, the more benefit they can get. Defenders, on the other hand, do not benefit from the security process at all; any step is a non-refundable investment. That is why risk-based security management has become widespread, in which the attention of defenders is focused on the most expensive (in terms of damage assessment) risks with the lowest cost to cover them. Risks with an overlap price higher than that of a protected resource are deliberately accepted or insured. The goal of this approach is to increase the cost of overcoming the least security vulnerability of the organization as much as possible, so critical services must be well protected, regardless of whether this resource is located within the network or at the network perimeter.
The risk-based approach is only a forced measure that allows the concept of information security to exist in the real world. In fact, it puts the defenders in a difficult position: they play their game with black, only responding to the emerging threats.
At the initial stage of development of network technologies, the damage from virus and other types of computer attacks was small, since the dependence of the world economy on information technology was small. At present, in the context of a significant dependence of business on electronic means of access and exchange of information and an ever-growing number of attacks, the damage from the smallest attacks leading to wasted computer time is estimated at millions of dollars, and the total annual damage to the global economy is tens of billions of dollars.
Information processed in corporate networks is especially vulnerable, which is facilitated by:
- an increase in the amount of information processed, transmitted and stored in computers;
- concentration in databases of information of various levels of importance and confidentiality;
- expanding the access of the circle of users to the information stored in the databases and to the resources of the computer network;
- an increase in the number of remote workplaces;
- widespread use of the global Internet and various communication channels;
- automation of information exchange between users' computers.
Analysis of the most common threats to today's wired corporate networks shows that threat sources can range from unauthorized intrusions to computer viruses, and human error is a significant security threat. It should be borne in mind that sources of security threats can be located both inside the corporate information system - internal sources, and outside it - external sources. This division is entirely justified because for the same threat (for example, theft), the methods of counteraction for external and internal sources are different. Knowledge of possible threats, as well as vulnerabilities of corporate information systems is necessary to select the most effective means of ensuring security.
The most frequent and dangerous (in terms of the amount of damage) are unintentional mistakes made by users, operators and system administrators serving the corporate information system. Sometimes such errors lead to direct damage (incorrectly entered data, an error in the program that caused the system to stop or crash), and sometimes they create weak points that can be exploited by attackers (these are usually administrative errors).
According to the US National Institute of Standards and Technology (NIST), 55% of IP security breaches are due to unintentional errors. Working in the global IS makes this factor quite relevant, and the source of damage can be both the actions of users of the organization and users of the global network, which is especially dangerous. In fig. 2.4 is a pie chart illustrating statistics on the sources of security breaches in the corporate information system.
Theft and fraud are in second place in terms of damage. In most of the cases investigated, the perpetrators were staff members of the organizations, who were very familiar with working hours and protective measures. The presence of a powerful information channel of communication with global networks in the absence of proper control over its work can further facilitate such activities.
Dishonest
Outside attacks
Offended
User and staff errors
4% Viruses
Rice. 2.4. Sources of security breaches
employees
Problems
physical
security
Offended employees, even former ones, are familiar with the order in the organization and are able to harm very effectively. Therefore, upon dismissal of an employee, his access rights to information resources should be canceled.
Deliberate attempts to obtain NSD through external communications account for about 10% of all possible violations. Although this figure does not seem to be that significant, experience with Interpe1 shows that almost every Interne1 server is exposed to penetration attempts several times a day. Tests by the Agency for the Protection of Information Systems (USA) showed that 88% of computers have weaknesses in terms of information security, which can be actively used to obtain NSD. Cases of remote access to information structures of an organization should be considered separately.
Before building a security policy, it is necessary to assess the risks to the organization's computing environment and take appropriate action. It is obvious that the costs of the organization to control and prevent security threats should not exceed the expected losses.
These statistics can provide guidance to the administration and personnel of the organization where to direct efforts to effectively reduce threats to the security of the corporate network and system. Of course, it is necessary to address physical security issues and measures to reduce the negative impact on security of human errors, but at the same time, it is necessary to pay the most serious attention to solving network security problems to prevent attacks on the corporate network and system, both from the outside and from within the system.
Threats and vulnerabilities of wired corporate networks
At the initial stage of development of network technologies, the damage from virus and other types of computer attacks was small, since the dependence of the world economy on information technology was small. At present, in the context of a significant dependence of business on electronic means of access and exchange of information and an ever-growing number of attacks, the damage from the smallest attacks leading to wasted computer time is estimated at millions of dollars, and the total annual damage to the global economy is tens of billions of dollars.
Information processed in corporate networks is especially vulnerable, which is facilitated by:
an increase in the amount of information processed, transmitted and stored in computers;
concentration in databases of information of various levels of importance and confidentiality;
expanding the access of the circle of users to the information stored in the databases and to the resources of the computer network;
an increase in the number of remote workplaces;
widespread use of the global Internet and various communication channels;
automation of information exchange between users' computers.
Analysis of the most common threats to today's wired corporate networks shows that threat sources can range from unauthorized intrusions to computer viruses, and human error is a significant security threat. It should be borne in mind that sources of security threats can be located both inside the corporate information system - internal sources, and outside it - external sources. This division is entirely justified because for the same threat (for example, theft), the methods of counteraction for external and internal sources are different. Knowledge of possible threats, as well as vulnerabilities of corporate information systems is necessary to select the most effective means of ensuring security.
The most frequent and dangerous (in terms of the amount of damage) are unintentional mistakes made by users, operators and system administrators serving the corporate information system. Sometimes such errors lead to direct damage (incorrectly entered data, an error in the program that caused the system to stop or crash), and sometimes they create weak points that can be exploited by attackers (these are usually administrative errors).
According to the US National Institute of Standards and Technology (NIST), 55% of IP security breaches are due to unintentional errors. Working in the global IP makes this factor quite relevant, and the source of damage can be both the actions of users of the organization and users of the global network, which is especially dangerous. In fig. 2.4 is a pie chart illustrating statistics on the sources of security breaches in the corporate information system.
Theft and fraud are in second place in terms of damage. In most of the cases investigated, the perpetrators were staff members of the organizations, who were very familiar with working hours and protective measures. The presence of a powerful information channel of communication with global networks in the absence of proper control over its work can further facilitate such activities.
Rice. 2.4. Sources of security breaches
Offended employees, even former ones, are familiar with the order in the organization and are able to harm very effectively. Therefore, upon dismissal of an employee, his access rights to information resources should be canceled.
Deliberate attempts to obtain NSD through external communications account for about 10% of all possible violations. Although this figure does not seem to be that significant, experience with the Internet shows that almost every Internet server is subjected to intrusion attempts several times a day. Tests by the Agency for the Protection of Information Systems (USA) showed that 88% of computers have weaknesses in terms of information security, which can be actively used to obtain NSD. Cases of remote access to information structures of organizations should be considered separately.
Before building a security policy, it is necessary to assess the risks to the organization's computing environment and take appropriate action. It is obvious that the costs of the organization to control and prevent security threats should not exceed the expected losses.
These statistics can provide guidance to the administration and personnel of the organization where to direct efforts to effectively reduce threats to the security of the corporate network and system. Of course, it is necessary to address physical security issues and measures to reduce the negative impact on security of human errors, but at the same time, it is necessary to pay the most serious attention to solving network security problems to prevent attacks on the corporate network and system, both from the outside and from within the system.