Material from the site
This article describes the methods and methods for extracting hidden files (rootkits, drivers) using the undocumented features of the Dr.Web® anti-virus scanner and additional third-party utilities.
Dr.Web Scanner
If you know the name of the driver in the current session, then you can copy it to quarantine using a scanner and send it to the virus lab.
To view them, switch to "Show hidden files and folders." Change selected option. Navigate to the folder in which you consider that there are hidden files and view the list. This process is intended only to display files that were hidden in a simpler way, without internal changes. To visualize the rest, you will need to define them as "normal." To do this, you must remove the hidden attribute using the command line.
Change the attribute of hidden objects using the command line. Then a command prompt opens. The command prompt opens. Inside the command line, enter the path to the file, then the symbol “:” and press Enter. Entering a folder from the command line. Enter the required command.
- Create a text file in the Drweb anti-virus directory, for example
If you have version 5.0 or higher installed, the creation of the filelist.txt file in the anti-virus directory will be blocked by self-defense. In this case, create the file filelist.txt in another directory (see example).
- Write the full path to the rootkit driver file, for example
Lines in one file can be many.
Depending on the size of the files, the command may take some time. Now go to your disk and make sure that all files are displayed and no longer hidden. Attribute change occurs immediately. Usually access to files. You can select the files you want to save, create a backup, or just find them.
To record everything that is typed by the user. Thus, cybercriminals can steal data from banking access, personal and even social networks. Open Task Manager on your computer. If you find it, click Finish Process.
- Run the scanner with the parameters:
For example: I have an antivirus installed in the C: \\ Program Files \\ DrWeb directory, and I created a text file in the root of the C: \\ filelist.txt drive
"C: \\ Program Files \\ DrWeb \\ drweb32w.exe" /copy:C:\\filelist.txt
Attention! Quotes are required in this case!
- Or if you use CureIT, then
After that, if such a driver exists on a disk, it is in quarantine in the C: \\ Program Files \\ DrWeb \\ Infected folder. !!! (or in the% USERPROFILE% \\ DoctorWeb \\ Quarantine \\ folder for KureIta) there will be a file.sys.sys.dwq. Now we archive it and send to virlab.
Open a run and enter the highlighted command. Then you open these cascading folders and subfolders, one inside the other. Go to the Current Version folder and select Run. Now find the keylogger and delete the file. They are allowed to work in the background. This is necessary so that they can update their live parts, receive new data and receive online notifications. But there is control over which applications can run in the background.
Here's how to find, disable and close programs that can and are used in the background. The first thing you need to do is to see which programs are allowed to run in the background. Click "Start" and then "Settings." In the "Settings" section, click "Privacy".
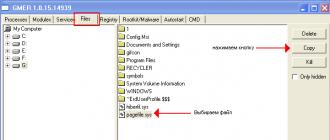
Gmer
- On the Rootkit / Malware tab, click the Scan button. We will wait until the program collects all the data. After you need to click the mouse on the tab "\u003e\u003e\u003e\u003e
- Right-click on the required module and select "Copy" through the context menu.
- If the "Copy" menu is not active, then select "dump module"
- On the tab "Processes" we look at the necessary process and in the field "Command" enter the command cmd.exe / c copy
For example:
Then click "Background Applications". Enter "Applications in the background." Select programs that you do not want to run in the background, and turn them off by switching from “On” to “Off”. There is a disadvantage in disabling some applications. How to find programs that run in the background.
To find and close any application running in the background, you must follow this question. Right-click an empty area of the taskbar. In the menu that appears, click "Task Manager". In the "Task Manager" window, click "Details".
Cmd.exe / c copy c: \\ drweb \\ spidernt.exe c: \\ spidernt.exe
In this case, we will get on disk C: the executable file of the spidernt.exe process
If none of these methods helped, then you can try to find the file.
- It is necessary to click the mouse on the tab "\u003e\u003e\u003e\u003e" in order to open the hidden tabs.
- Go to the "Files" tab
- We are looking for a file like in Explorer, select it.
- Press the "Copy" button. Save the file to the directory you need.

Task Manager displays a list of all running applications. Find the program you want to close in the list below “Background Processes”, click on it, and then click the “End Task” button. With these tips you can more control what is running in the background, and improve the performance of your computer.
We will solve this problem as soon as possible. What color icon and focus text do you see? ![]()
![]()
- White icon with a focal text that looks like this: "Files updated."
- Open File Explorer.
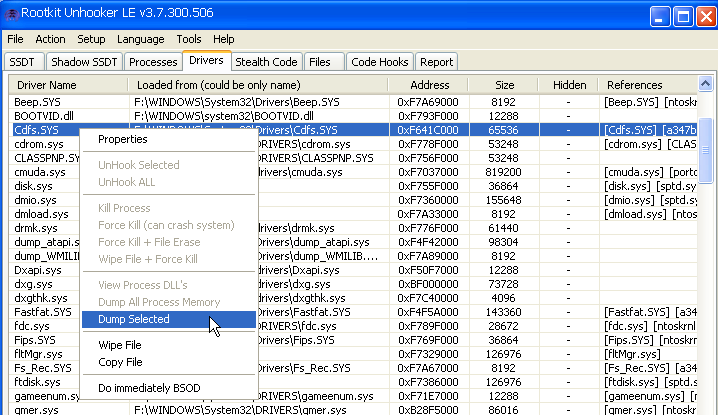
Rku
- Select the "Drivers" tab and select "Copy" through the context menu.
- If you can not copy - make a dump. To do this, select the command "Dump Selected" via the context menu.
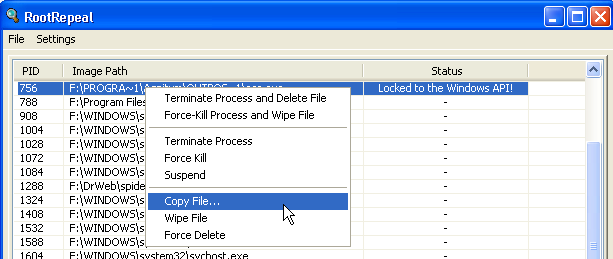
Rootrepeal
- Select the "Process" tab and click the "Scan" button
- Right click on the suspicious process and select the menu item "Copy file ..."
First try these common fixes.
![]()
First, try these steps before you begin troubleshooting more detailed. When you receive the following message, you do not need to do anything. "We are reviewing all your files to make sure they are up to date on this computer, and this can take some time if you have a lot of files."
Then try these steps.
Problems with synchronization can sometimes be due to the lack of files. . Restart the paused sync.Delayed deletion using
Sometimes a situation arises when it is necessary to delete a file (trojan), but this does not work with standard tools from Explorer. To do this, use HJ. After launching HJ, click on the "Open the Misc Tools section" button and then click on the "Delete a file on reboot ..." button. A file selection dialog box will appear (if the file is not visible, you can select the folder where it is located and manually enter the file name and extension ... or use the recommendations
- Slide your finger off the right edge of the screen and tap Settings.
- Click or select Options and enable file synchronization.
- Swipe to the right edge of the screen and tap Settings.
- Click.
Programs that are active on a computer can always be viewed by opening the Task Manager. However, sometimes it may happen that you need to make the execution of a program invisible. If you also have such a desire, you will probably begin to look for an answer to the question of how to hide the process in the Windows Task Manager.
An example of the path to the file. When the file path is shortened, restart synchronization. To open the Task Manager window, click or open the Additional Details tab. If the status is not running, you can turn it on again. You may need to select "More Information" to open the Task Manager window.
- Click or select the Details tab.
- In the "Task Manager" window, select "File" on the top toolbar.
- Select "New Task."
- You may need to enter a verification code.
Learn how to hide the Windows Task Manager process.
Of course, the anonymity of the execution of some programs will allow you to track those who are overly cluttering up a personal computer. This is especially important when multiple users have access to a PC.
Also, the desire to hide the process arises among those who install their own program and strive to ensure that advanced users cannot detect its presence by simple means.
Instead, you only see the files that you decide to sync with your computer. If you have not yet synchronized the folder containing the files you want to synchronize, you will not see these files. Here's how to sync your folders. ![]()
![]()
The full path, including the file name, must be less than 255 characters.
Make sure you have permissions for the file or folder you tried to add. Try to open a file or folder and make sure you have permission to save a copy. If you have problems viewing the file on the network, contact your network administrator.
Any program execution is a process that needs a certain part of the RAM. Processes are divided into:
- systemic;
- anonymous;
- custom;
- related to the internet.
It is not recommended for those who do not have practical experience and the necessary technical knowledge to interfere with system processes, since such an unwise introduction can provoke extremely undesirable consequences. One of these consequences may be the failure of the subsequent launch of the operating system.
Make sure that a file or folder with the same name already exists in place. Rename the file or folder and try adding it again. Make sure that your computer has enough disk space and restart synchronization. Free up disk space by moving or deleting files. Here are some tips on how to free up disk space.
Make sure that file and folder names do not contain unsupported characters or invalid file types. If the file or folder name contains certain characters or file types, you cannot synchronize these files. View a list of invalid file types and characters, change the names of files or folders, or delete unsupported file types.
It is possible to learn how to hide any user programs, and you will not need to make great efforts, you just need to carefully read our recommendations. We draw your attention to the fact that even an advanced engineer who is unaware of your “creative acts” will not notice the “left” process.
Make sure that file sizes, number of elements, and file path size are within limits. Review the limits on the size and number of files that can be synchronized, and make sure that the files you are trying to synchronize do not exceed them. Step 4: Fix one connection for business synchronization.
Then try these quick steps.
Some steps take several minutes to complete before performing the steps in this article. Very useful for checking which processes cause excessive use of memory or machine resources. In the event of an unexpected failure or freezing of a particular application, many users are lost, not knowing what to do. Pay attention at this moment and do not press anywhere, unless it is on the program screen, since any program you press at this time will be immediately closed.
Action algorithm
If you needed to hide a software application, you first need to figure out whether it is simple, whether it starts up additional processes that can simply issue it, no matter how you try to hide the program.
If, indeed, your program is simple, if it is displayed in the Task Manager in a single line, we suggest that you hide the process in the simplest way. To do this, you just need to rename it.
This command lists with absolute paths all found files with the requested name. This command shows the network usage of the device, the addresses used, the protocol and even the port used by the access. Very useful for monitoring network traffic and determining which addresses your current programs are accessing in the background.
Remember to go to where you want to create the folder before you run the command. This command analyzes the physical and virtual partitions and informs you about the amount of free disk space and shows the space used for each partition, as well as its physical location on the machine.
So, we will help you figure out how to rename the process in the Task Manager so that the program continues to function perfectly in anonymous mode.
Step 1
Initially, you should go to the folder where the execution file of a specific program is located. If you know where it is located, then use your usual “route” by opening the “Computer” window, navigating to system drive C, and then following to its root folder.
The problem with the resolution of the file is a constant user. Allows you to remotely access remote servers, virtual disks, databases and systems. Visit the manual to learn about its various uses. Mixing with registry data requires great care and some technical knowledge.
The famous saying goes that the team that wins does not move. Adapted to the computer world, this sentence will look like this: if it works, do not spoil it. The temptation to remove them in order to release some precious bytes is very high, and believe me, there are people who do this. The problems that this may entail are numerous and unpredictable.
If you do not know where the execution file is hidden, it doesn’t matter, you only need to find this process in the list displayed in the Task Manager, right-click on it, and then select the “Open file storage location” line in the window that opens.
![]()
One of the reasons why some of these files remain hidden only prevents you from being tempted to do something with them, changing their content or even removing them from the system. The registry is a library in which the operating system stores configuration information for all applications that are subject to it. Theoretically, if an application is removed, the application master itself should remove all references to deleting the application from the registry.
In most cases, registry entries will be deleted correctly. The main problem is that the system tends to slow down. The result may be an application that does not work correctly or may not work. In the worst case, the system may be completely compromised. There are several of them, and it is convenient to check them before taking a more decisive measure.
Step 2
After such your actions, you will open the folder you are looking for; in it you only have to find the execution file. Search will be easy, because this file has the exact same name as in the list of processes in the Task Manager. In addition, this file has the extension "exe".
Step 3
To rename a file, click on it again with the right mouse button, and then select the line "Rename". Now that you have managed to assign a new name to your software application, open the Task Manager, see that this rename has been displayed there.
![]()
Of course, it will depend on what name you think up how your program will become “veiled” for other PC users. An unknown process with a new name will even more quickly arouse suspicion and force a technical engineer to figure out what program is running on a PC.
For this reason, many experienced users recommend coming up with names that at first glance do not arouse any suspicion.
In particular, the open Chrome browser creates several processes at the same time, just like Windows. It is desirable to take the same process name, but since the system does not allow two processes of the same name to function simultaneously, it is recommended that a small trick be used when renaming. Instead of some English letters, it is as if accidentally registering Russians in the title. Outwardly, it is impossible to distinguish Russian from English letters, and the system will distinguish, therefore, it will allow programs with conditionally the same names to work.
Results
So, as you have managed to notice, you can make some software anonymous without much difficulty. Of course, there are still quite advanced methods that allow you to hide any process more reliably, but they are based on writing complex codes and programming skills. If you do not set yourself such complicated goals, then hiding working software applications by renaming is an acceptable option.