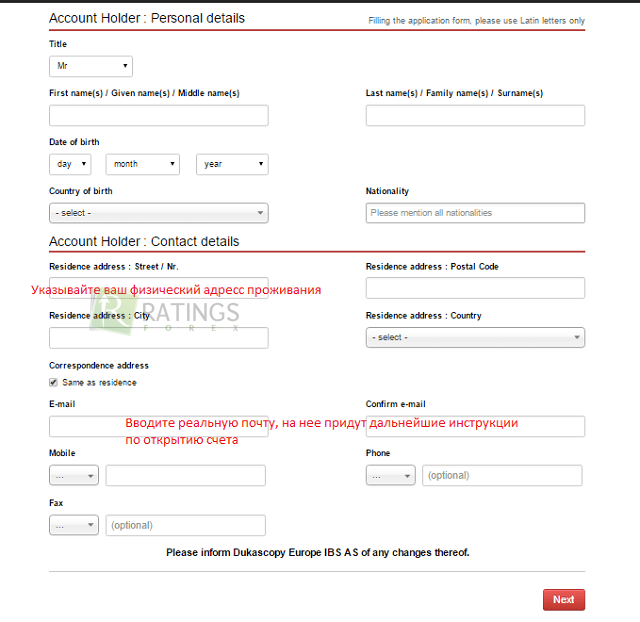
The biggest concern for companies is the protection of external cloud services. For example, respondents worry that incidents can occur from suppliers who outsource business processes, from third-party cloud services, or from an IT infrastructure where a company leases computing power. However, despite all this concern, only 15% of companies check compliance with third-party security requirements.
“Despite the fact that recent large-scale hacks have occurred inside the data center, traditional security systems still focus only on protecting the network perimeter and controlling access rights. At the same time, the negative impact of solutions to protect physical infrastructure on the performance of virtual environments is rarely taken into account, ”explained Veniamin Levtsov, Kaspersky Lab’s Vice President of Corporate Sales and Business Development. - Therefore, in converged environments it is so important to use appropriate comprehensive protection, ensuring the security of virtual systems with specially designed solutions. We are implementing an approach in which, regardless of the type of infrastructure for all systems, a single security coverage of the entire corporate network is provided. And this is where our technologies and modern VMware developments (such as microsegmentation) complement each other perfectly. ”
2014: Ponemon and SafeNet data
Most IT organizations are unaware of how corporate data is protected in the cloud — as a result, companies endanger their user accounts and confidential information. This is just one of the findings of a recent fall 2014 study by the Ponemon Institute commissioned by SafeNet. As part of a study entitled “Challenges of Information Management in the Cloud: A Global Data Security Survey,” more than 1800 IT and IT security experts were surveyed worldwide.
Among other findings, the study found that while organizations are increasingly leveraging the power of cloud computing, corporate IT departments are struggling with data management and cloud security. The survey showed that only 38% of organizations clearly defined roles and responsibilities for ensuring the protection of confidential and other sensitive information in the cloud. The situation is aggravated by the fact that 44% of corporate data stored in a cloud environment is beyond the control of IT departments and is not managed by them. In addition, more than two-thirds (71%) of respondents said that they face ever new difficulties when using traditional security mechanisms and techniques to protect confidential data in the cloud.
With the growing popularity of cloud infrastructures, the risks of confidential data leaks also increase. About two-thirds of the IT professionals surveyed (71%) confirmed that cloud computing today is of great importance to corporations, and more than two-thirds (78%) believe that the relevance of cloud computing will remain in two years. In addition, according to respondents, about 33% of all the needs of their organizations in information technology and data processing infrastructure can be met today using cloud resources, and over the next two years this share will increase on average to 41%.
However, the majority of respondents (70%) agree that it is becoming increasingly difficult to comply with the requirements for maintaining data confidentiality and protecting them in a cloud environment. In addition, respondents noted that the types of corporate data stored in the cloud, such as email addresses, customer and customer data, and billing information, are most at risk of leaks.
On average, the implementation of more than half of all cloud services in enterprises is carried out by third-party departments, not corporate IT departments, and on average about 44% of corporate data located in the cloud is not controlled or managed by IT departments. As a result of this, only 19% of respondents could declare their confidence that they are aware of all the cloud applications, platforms or infrastructure services currently in use in their organizations.
Along with the lack of control over the installation and use of cloud services, there was no consensus among the respondents as to who is actually responsible for the security of data stored in the cloud. Thirty-five percent of respondents said that responsibility is shared between users and cloud service providers, 33% believe that the responsibility lies entirely with users, and 32% believe that the cloud service provider is responsible for data security.
More than two-thirds (71%) of respondents said that it is becoming increasingly difficult to protect user confidential data stored in the cloud using traditional security tools and methods, and about half (48%) say that it is becoming more difficult for them to control or limit end users access to cloud data. As a result, more than a third (34%) of IT professionals surveyed said that their organizations have already implemented corporate policies that require security mechanisms such as encryption to work with certain cloud computing services. Seventy-one (71) percent of respondents noted that the ability to encrypt or tokenize confidential or other sensitive data is of great importance for them, and 79% believe that the importance of these technologies will increase over the next two years.
When asked what exactly is being done in their companies to protect data in the cloud, 43% of respondents said that their organizations use private networks to transmit data. About two fifths (39%) of respondents said that their companies use encryption, tokenization, and other cryptographic tools to protect data in the cloud. Another 33% of respondents do not know what security solutions are implemented in their organizations, and 29% said they use paid security services provided by their cloud service providers.
Respondents also believe that managing corporate encryption keys is important for securing data in the cloud, given the growing number of key management and encryption platforms used by their companies. In particular, 54% of respondents said that their organizations retain control over encryption keys when storing data in the cloud. However, 45% of respondents said that they store their encryption keys in a software form, in the same place where the data itself is stored, and only 27% store the keys in more secure environments, for example, on hardware devices.
Regarding access to data stored in the cloud, sixty-eight (68) percent of respondents say that managing user accounts in a cloud-based environment is becoming more difficult, with sixty-two (62) percent of respondents saying that they have access to the cloud in organizations provided for third parties. About half (46 percent) of respondents said that their companies use multi-factor authentication to protect third-party access to data stored in a cloud environment. About the same number (48 percent) of respondents said that their companies use multi-factor authentication technologies, including to protect the access of their employees to the cloud.
Why are customers dissatisfied with cloud providers?
Opaque cloud
A recent study by Forrester Consulting shows that many organizations believe that cloud service providers do not provide them with enough information about interacting with the cloud, and this harms their business.
In addition to insufficient transparency, there are other factors that reduce the enthusiasm for moving to the cloud: this is the level of service for customers, additional costs and adaptation during migration (on-boarding). Organizations are very fond of the cloud, but not of its suppliers - in any case, not as much.
The study was commissioned by iland, a provider of corporate cloud hosting, conducted during May and encompassed professionals in the field of infrastructure and ongoing support from 275 organizations in and Singapore.
“Among all the complexities of today's cloud, there are annoying flaws,” writes Lilac Schoenbeck, vice president of product support and marketing, iland. “Such important metadata is not communicated, significantly hampering the adoption of the cloud, and yet organizations make growth plans based on the assumption of unlimited cloud resources.”
Where is the key to achieving harmony in business relations? This is what the VAR’s need to know in order to try to resolve the problems and bring the parties to reconciliation.
Inattention to customers
Apparently, many users of the cloud do not feel the same individual approach.
So, 44% of respondents said that their provider does not know their company and does not understand their business needs, and 43% believe that if their organization was simply larger, then probably the supplier would pay more attention to them. In short, they feel the chill of an ordinary deal buying cloud services, and they don't like it.
And one more thing: there is one practice pointed out by a third of the companies surveyed, which also instills a sense of pettiness in the transaction - they charge a fee for the slightest question or incomprehensibility.
Too many secrets
The reluctance of the supplier to provide all the information not only annoys customers, but often costs them money.
All respondents who participated in the Forrester survey responded that they felt certain financial consequences and impact on their current work due to missing or closed data on their use of the cloud.
“The lack of clear data on cloud usage parameters leads to performance problems, reporting difficulties to management about the real cost of use, payment for resources that have never been consumed by users, and unforeseen bills,” Forrester says.
Where is the metadata?
The IT executives who are responsible for the cloud infrastructure in their organizations want a cost and performance metric that provides clarity and transparency, but it’s obviously hard for them to communicate to suppliers.
Survey participants noted that the metadata they receive about cloud workloads is usually incomplete. Almost half of the companies replied that there was no regulatory compliance data, 44% indicated that there were no data on usage parameters, 43% said retrospective data, 39% said security data, and 33% said billing and cost data.
Transparency issue
The lack of metadata causes all kinds of problems, respondents say. Nearly two-thirds of respondents said that lack of transparency does not allow them to fully understand all the benefits of the cloud.
“The lack of transparency gives rise to various problems, and first of all it is a question about the use parameters and interruptions in work,” the report says.
Approximately 40% try to fill these gaps themselves by purchasing additional tools from their own cloud providers, while the other 40% simply purchase the services of another provider where such transparency is present.
Regulatory Compliance
Like it or not, organizations are responsible for all their data, whether on local storage or sent to the cloud.
More than 70% of respondents in the study said that their organizations are regularly audited, and they must confirm compliance with existing standards, wherever their data is located. And this puts an obstacle to the adoption of the cloud for almost half of the companies surveyed.
“But the aspect of your regulatory compliance needs to be transparent to your end users. When cloud providers hold or do not disclose this information, they do not allow you to achieve this, ”the report said.
Compliance Issues
More than 60% of companies surveyed said regulatory compliance constraints further cloud adoption.
The main problems are:
- 55% of companies associated with such requirements said that it was most difficult for them to implement appropriate controls.
- About half say they find it difficult to understand the level of compliance provided by their cloud provider.
- Another half of the respondents replied that it was difficult for them to obtain the necessary documentation from the provider on compliance with these requirements in order to pass the audit. And 42% find it difficult to obtain documentation on their own compliance with the requirements for workloads running in the cloud.
Migration issues
The on-boarding process seems to be another area of \u200b\u200bgeneral dissatisfaction: just over half of the companies surveyed said they were not satisfied with the migration and support processes that cloud providers offered them.
Of the 51% unsatisfied with the migration process, 26% replied that it took too long, and 21% complained about the lack of live participation from the provider staff.
More than half were also not satisfied with the support process: 22% indicated a long wait for an answer, 20% indicated insufficient knowledge of the support staff, 19% indicated a lengthy process of resolving problems, and 18% received bills with a higher than expected support cost.
Obstacles to the cloud
Many of the companies surveyed by Forrester are forced to restrain their expansion plans in the cloud due to the problems they experience with existing services.
To exchange files between computers and mobile gadgets, cables and flash drives are no longer needed. If the devices have Internet access, files can “fly” between them “on the cloud”. More precisely, they can "settle" in the cloud storage, which is a collection of servers scattered around the world (combined into one virtual - cloud server), where users post their data for free or for free. Files are stored in the cloud in the same way as on the computer’s hard drive, but are accessible not from one, but from different devices that can connect to it.
Every second or third Internet user has already taken the cloud storage technology into service and is happy to use it, but someone is still saved by flash drives. After all, not everyone knows about such an opportunity, and some simply cannot decide which service they should choose and how to use it. Well, let's get it together.
What are cloud storages from the point of view of the user and how they work
If you look through the eyes of an inexperienced user, cloud storage is an ordinary application. It only does that creates a folder on the computer under its own name. But not simple. Everything that you put in it is simultaneously copied to the same cloud Internet server and becomes accessible from other devices. The size of this folder is limited and can increase within the allocated disk space (on average, from 2 GB).
If the cloud storage application is running and the computer (mobile gadget) is connected to the global network, the data on the hard drive and in the cloud are synchronized in real time. When working offline, as well as when the application does not work, all changes are saved only in the local folder. When the machine connects to the Internet, access to the storage becomes possible, including through a browser.
Files and folders uploaded to the cloud are full-fledged web objects, the same as any content on websites and ftp-stores. You can link to them and share links with other people, even those who do not use this service. But you can download or see an object from your repository only to those to whom you yourself have allowed it. In the cloud, your data is hidden from prying eyes and is password protected.
The bulk of cloud services has additional functionality - a file viewer, built-in document editors, screenshot creation tools, etc. This is plus the amount of space provided and creates the main differences between them.

- A cloud storage service that does not need to be introduced to Windows users. Indeed, in the latest releases of this OS (in the “top ten”), it directly climbs on top of everything on the screen, as it is set to autorun by default.
For Windows users, the advantage of the Microsoft OneDrive service over analogues is, perhaps, only one thing - it does not need to be installed. Also, you do not need to create a separate account for it - to enter the cloud, just enter your Microsoft account information.
The owner of one account Microsoft OneDrive provides 5 GB of free disk space for storing any information. To get additional volume, you have to pay extra. The maximum is 5 TB and costs 3 399 rubles per year, but this package includes not only disk space, but also the Office 365 application (home release). More affordable tariff plans are 1 Tb (2,699 rubles per year - storage and Office 365 personal) and 50 GB (140 rubles per month - only storage).
Additional features of all tariffs:
- Support for other operating systems - Mac OS X, iOS, and Android.
- View and edit documents with Office Embedded applications.
- Remote access to all the contents of the computer (not just the OneDrive folders) on which the service is installed and your Microsoft account is used.
- Create photo albums.
- Built-in messenger (Skype).
- Create and store text notes.
- Search.
Paid versions only:
- Create links with a limited duration.
- Offline folders.
- Multipage scanning with saving documents to a PDF file.
In general, the service is not bad, but sometimes there are problems logging into the account. If you intend to work with the web version of the repository (through a browser) and access it under a different IP address than before, Microsoft sometimes runs an account ownership check for you, which takes a lot of time.
There were also complaints about the removal of user-generated content from OneDrive - when Microsoft suspected that it was unlicensed.

- One of the oldest cross-platform cloud storage. Unlike the previous one, it supports all major operating systems, as well as some rarely used ones, for example, Symbian and MeeGo. The service is very easy to use, it works quickly and stably.
Free DropBox user is provided with only 2 GB of disk space for storing personal files, but this amount can be doubled by creating and connecting to your account another one - a working one (which can actually be personal). Together get 4 GB.
Switching between personal and working disk space on the DropBox website and in the application is carried out without exiting the account (you do not need to enter a username and password each time). A separate folder is created on the computer for both accounts - 2 GB each.
DropBox, as expected, also has several tariff plans. About free, it was said above, Paid - this is “Plus” (1 TB, $ 8.25 per month, intended for personal use), “Standard” (2 TB, $ 12.50 per month, for business), “Advanced” (unlimited volume, $ 20 per month for 1 user) and Enterprise (unlimited volume, individually set price). The differences between the last two are in the set of additional options.
In addition to storage, free users can access:
- DropBox Paper Collaboration Service.
- Ability to share links and create shared folders.
- File change log with the ability to restore them to the previous version (up to 30 days).
- Commenting files - both your own and other users, if the file is available for viewing.
- Search function.
- Receive event notifications (configured individually).
- Automatically upload photos from the camera (by the way, for enabling this option some time ago DropBox provided users with additional space).
- The choice of full or selective synchronization.
- Data encryption during storage and transmission.
The possibilities of paid tariffs can be listed for a very long time, so we only note the main ones:
- Removing data from DropBox remotely on a lost or stolen device.
- Limit the duration of the link.
- Two-factor account authentication.
- Setting access levels for different data.
- Enhanced protection of HIPAA / HITECH class information (safe storage of medical records).
- 24/7 technical support.
DropBox, if not the best, then a very decent service. Despite the small volume of free space by today's standards, it is used by millions of people around the world.
Mega (Megasynk)

As you can see from the description, Amazon Web Services is focused only on the corporate sector and is not intended for storing albums with photographs of cats, although it is possible that someone uses it for this. After all, cloud file storage - Amazon Glacier, like Yandex disk, provides users with 10 free GB. The cost of additional volume is $ 0.004 per 1 GB per month.
Comparison of Amazon Glacier with the web resources described above is probably incorrect, because they have a slightly different purpose. The functionality and capabilities of this service are determined by the tasks of the business, including:
- Uninterrupted operation, increased reliability.
- Compliance with enhanced data protection standards.
- Multilingual interface.
- Unlimited volume (expansion for a fee).
- Ease of use and flexibility of settings.
- Integration with other Amazon Web Services.
Those interested in Amazon's features can check out the full AWS product documentation on the official website.
Mail.ru

It occupies the second or third place in the ranking of the popularity of file web storages among a Russian-speaking audience. In terms of features, it is comparable to Google Drive and Yandex Disk: in it, like in them, there are web applications for creating and editing documents (texts, tables, presentations) and a screenshoter (utility for taking screenshots). It is also integrated with other Mail.ru projects - mail, My World and Odnoklassniki social networks, Mail. Acquaintances ”, etc., has a convenient file viewer with a flash player and is also very affordable (for those who do not have enough allocated volume).
The size of the free disk space of the Mail cloud is 8 GB (previously this figure has changed several times). The premium tariff for 64 GB costs 690 rubles per year. For 128 GB, you will have to pay 1,490 rubles a year, for 256 GB - 2,290 rubles a year. The maximum amount - 512 GB, will cost 3,790 rubles per year.
Other functions of the service are not much different from similar ones. It:
- Shared folders.
- Synchronization.
- Built-in search.
- The ability to share links.
The Mail.ru client application runs on Windows, OS X, iOS, and Android.

Cloud storage is a proprietary web service for owners of smartphones and tablets of the same manufacturer. Designed for storing backup copies of data from mobile devices - multimedia content, OS files and other things at the discretion of the user.
The Samsung Cloud client application is preinstalled on phones and tablets released later than the second half of 2016 (more precisely, after the release of the Samsung Galaxy Note 7). Registration of an account on the service is possible only through it, apparently, for screening outsiders.
Free storage is 15 GB. An additional 50 GB costs $ 0.99 per month, and 200 GB costs $ 2.99.
iCloud (Apple)

- A favorite among cloud data warehouses among users of Apple products. Indeed, it is free (though not very capacious) and is integrated with other apple services. The service is designed to store backup copies of data from iPhone, iPad and iPod, as well as user media files, mail and documents (the latter are automatically synchronized with the contents of iCloud Drive).
The free iCloud storage capacity is 5 GB. Additional storage is priced at $ 0.99 for 50 GB, $ 2.99 for 200 GB, and $ 9.99 for 2 TB.
The iCloud client application supports Mac OS X, iOS, and Windows operating systems. An official Android application has not been developed, but owners of devices based on this OS can view mail from the Apple cloud on their device.

Chinese service completes the top parade of cloud storage. As you can see from the screenshot, it is clearly not adapted for you and me. Why, then, is it needed if there are domestic, European and American counterparts more familiar to the Russian-speaking person? The fact is that Baidu provides users with a terabyte of free disk space. For the sake of this, it is worth overcoming the difficulties of translation and other obstacles.
Registering for Baidu Cloud is significantly more time consuming than competing. It requires confirmation by a code sent by SMS, and SMS from a Chinese server does not come to Russian, Belarusian and Ukrainian numbers. Our fellow citizens have to get out by renting a virtual phone number, but that's not all. The second difficulty is that the account cannot be registered to some email addresses. In particular, on gmail services (Google is blocked in China), fastmail and Yandex. And the third difficulty is the need to install the Baidu Cloud mobile application on a phone or tablet, since that’s why 1 TB is given for this (when registering on a computer, you will get only 5 GB). And it, as you know, is entirely in Chinese.
Not scared? Dare - and you will be rewarded. Information on how to create an account on Baidu with your own hands is on the Internet.
FalcongazeCloud data storages gave us many pleasant opportunities - you can access the necessary files from any device connected to the Internet, and several people can edit them at the same time, in addition, such technologies can rely on the preservation of important information in the event of a failure on the local storage. However, not everything is so rosy - as in any advanced technology, when confronted with reality, a number of different problems come to light in cloud services. One of the most important is safety. It is focusing on the security of the service provided, the analytical center Falcongaze ranked the most popular cloud data warehouses.
Like most competitors, Dropbox encrypts client data on the server side, however, refuses encryption in the client part of the program. Also, streaming files from company servers is not always encrypted. Thus, it becomes possible to compromise data during the upload and download of files on the server. Dropbox also has an impressive history of security incidents. The most egregious of them occurred in June 2011 (in fairness it should be said that at that time most of the competitors simply did not exist): then for four hours anyone could get access to any account on the service. What happened was made possible due to an error in the updated server software. Due to the above issues, Dropbox ended up on the last place in the ranking of popular cloud storage. In addition to the basic version, Dropbox has a business plan. It provides additional encryption during data transfer and in applications, storage of contents of files in the form of encrypted blocks, as well as separate storage of metadata and data blocks.
One of the most popular domestic competitors Dropbox and Google Drive - cloud service Yandex.Diskranked Falcongaze Fourth a place. Integration with other Yandex services is built into it, in addition, there is two-factor authentication, including using a PIN code, QR code and TouchID. When downloading files are checked for viruses, and data is transmitted via an encrypted channel. In 2013, there was a big scandal in connection with the cloud service from Yandex - there was a critical error in the next update, due to which the installer of the client program tried to delete the system partition of the operating system. As a result, some of the users who installed the update stopped running a number of programs, and Windows registration was deactivated. Yandex provided 200 GB of free space on Yandex.Disk to all victims of the incident for perpetual use.
On third ranked place Google drive. It contains two-factor authentication, account recovery is performed using a secret question, the service itself checks the password invented by the user for reliability and does not allow the use of easily cracked passwords. The service provides a user from 15GB of server space for free use. In 2014, Google Drive totaled more than 240 million users. Data is encrypted during transmission, which eliminates their compromise during the download, however, third-party programs will be required to encrypt data on the server. In addition, Google Drive has a version for business accounts, which allows you to provide a higher level of file protection. It, for example, lacks analysis of the transmitted information for displaying advertisements and contains a single sign-on system, email protection rules, for example, forced inclusion of the TLS protocol, as well as IRM and DLP technologies.
For users of the apple ecosystem, Apple’s cloud storage exists - iCloud drive. Probably the largest scandal in the history of cloud storage is associated with this service. This is an incident that took place in 2014. Then there was a massive hacking of accounts in iCloud, as a result of which a lot of user personal data got into the network. The widespread scandal was facilitated by the fact that the leaked data contained personal photos of a number of celebrities such as Jennifer Lawrence, Kaylee Cuoco and Jenny McCarthy. After the incident, Apple took serious steps to improve the security of the service - now the data in iCloud Drive is encrypted both during transmission and on the server, the password is checked for reliability, and two-factor authentication is present. Based on the above, Apple’s cloud storage came in second rank line.
Due to the popularity of office products from Microsoft, it gained considerable fame and the cloud service from this company - OneDrive. OneDrive provides up to 5 GB of free server space for use, and also supports integration with Microsoft Office and Outlook products. The basic version of the product provides encryption of data transmitted between the client and the server, as well as two-factor authentication, in addition, the password from the Microsoft account is checked for reliability. In addition to the basic one, OneDrive also has a business version with improved security features. In the business version, OneDrive provides "data center physical security, network security, access security, application and data security." The types of storages used in the business version of OneDrive — the encrypted content repository, the content database, and the key repository — are physically separated, so you cannot compromise information when you hack any of them. All this brought OneDrive to the first place in the ranking of cloud services in terms of security.
“It seems to me that the more data we send to the network, to the clouds, the less we actually control it.”
Can you trust cloud storage?
I think the majority will answer negatively to the first question, but positively to the second.
Currently, cloud services have become so widespread and tightly integrated with the equipment of leading manufacturers of computers and various gadgets that many do not even think about where exactly their data is stored and what can happen to them.
Are clouds so scary, and are our home computers so safe?
Let's look at Steve's arguments.
The first argument is "nothing belongs to you in the clouds." Information created by you, especially information about yourself (personal data), always belongs to you, regardless of where it is located. By transferring it to a cloud service for storage, you do not transfer any rights to the information to its owner. She was and remains yours.
The second argument is "the more data we send to the network, to the clouds, the less we actually control it." You have not encountered this situation: are you trying to boot the computer, it is not loading, and the screen displays an offer to pay money for unlocking, or you access the file, and it is encrypted, and again require a certain amount for decryption? Millions of computers in the world are infected and are part of botnets. Perhaps your computer is no longer under your control, and, accordingly, all the data that is on it.
Do we have reason not to trust cloud services?
The theory teaches that to protect information, it is necessary to ensure its confidentiality, integrity and accessibility. Let's see if these properties are provided when using clouds.
Legal aspects
Cloud service user agreements almost never contain a commitment to maintaining the confidentiality and integrity of your data. Organizations should remember that, as PD operators, they need to provide the full range of processing requirements and, which is not always feasible in the cloud.
In addition, in the near future, a ban on storing PDs in databases located outside of Russia should come into force (this provision should come into force on September 1, 2016, although the transfer of this date to September 1, 2015 is actively lobbying .).
In terms of cloud service availability, at first glance, everything is fine. Most cloud service providers guarantee high availability. But let's estimate where the responsibility area of \u200b\u200bthe cloud service provider ends and where you are with your Internet access devices.
There are dozens of reasons why your data stored in the cloud may not be available to you, even though the cloud service itself will be fully operational. Therefore, the real availability of the cloud service is much lower than the numbers stated in the user agreement.
To this should be added the risks associated with Western sanctions against Russia. Most, I think, have heard about the decree of the US president about additional sanctions against Crimea, the consequences of which may be blocking services such as Gmail, Skype or iCIoud on the peninsula. In the current difficult political situation, you cannot be sure that at one fine moment you simply will not be disconnected from the cloud service, especially if this service is provided by an American company.
Let’s try to evaluate what is the real situation with ensuring the integrity and confidentiality of information in the cloud.
Despite the fact that the provider does not have formal obligations to ensure these information properties, all well-known global IT companies, when organizing cloud services, provide a fairly high level both from unauthorized access to them and from destruction for some technical reasons. Those. a direct attack on the resources of the cloud service provider is unlikely for attackers to achieve the goal. Although, as they say, the old woman also has a flaw, as evidenced by the loud statements periodically appearing in the media about the leak of user data from large IT companies and Internet services.
The main vulnerability of Internet services is the use of almost exclusively password authentication and the use of not quite reliable ways to recover forgotten authentication data - logins and passwords (primarily through e-mail). However, recently there has been a clear tendency to complicate authentication data recovery.
When connecting cloud services, organizations should immediately take care of implementing some kind of two-factor authentication mechanism. The maturity of cloud services regarding information security currently leaves much to be desired. You are unlikely to find in them a wide range of authentication methods, a very flexible access control system, advanced event auditing with support for SIEM systems, built-in cryptography tools, etc.

If you do not trust the cloud service provider or want to provide additional protection for information in the cloud, then you should apply. This method of protection is possible if you do not plan to process information in the cloud (for example, edit a photo or text), but only store and transfer data in its original form.
At the same time, it is necessary to take into account the difficulties with the distribution and management of cryptographic keys (especially for large organizations) and the loss in mobility (in order to access the data, you must have an actual cryptographic key stored in a secure manner on your device, and this may cause technical or technological problems) .
Yes, we have reason to not trust cloud services. Yes, large organizations that invest heavily in data security can provide a higher level of protection when placing information in their data center than in the cloud.
But at the same time, it is obvious that the use of cloud services will only expand. It’s convenient when you don’t need to think about creating this or that IT service and maintaining it in working condition, but you can use the clouds almost instantly.
Drawing an analogy, most people prefer to buy a cake rather than bake it themselves. Moreover, a cloud service, as a rule, allows you to quickly change the parameters of the service, which is not just convenient, but for most organizations it is necessary with significantly increased rates of change in business requirements. It should be noted that cloud services are much more adaptable for mobile users, and business and we ourselves are becoming more mobile every year.
Therefore, regardless of whether you trust the clouds or not, they have already entered or will soon enter your life. And it’s worth it now to think about what information you are ready to entrust to the clouds and how to minimize the risks that we discussed in this article.
Anatoly Skorodumov
Cloud file storage technologies today are considered a must-have tool for a modern Internet user. Each of them has an account on one of the cloud drives: Google Drive, Yandex.Disk or Mail.ru. Most have at least two of these services. In this article, we will consider the main network file storage services, ways to increase disk space on them, and give tips on their effective and safe use.
What is cloud storage?
Local drives and memory cards are physically connected to our computer or tablet with wires. Network drives are physically located in special server centers, where a stable power supply and a comfortable temperature mode are provided. The local computer supports communication with them via the Internet. When you go through your browser or mobile client application to your cloud drive, the system displays a list of files lying on the server. When the user transfers the file from the local folder My Documents to the Cloud Storage, the document is physically copied over the Internet and gets to the server.
Therefore, even after the physical destruction of the phone or computer, the files will remain safe and sound. They can be viewed through a web browser on any computer or tablet.
To assess the popularity of disk storages, it is enough to give one fact of statistics. As of 2014, Google Drive was the most popular cloud. The repository works by default on all Android devices, except Chinese, where access to Google is limited. Its users were 240 million people.
What you can use Cloud Disk for
The main tasks performed by users using network attached storage:
Developers are constantly improving the security system of their services. The standard today is the storage of user files in encrypted form. Without a special key, this is a useless set of bytes.
Security services should not be overestimated. In 2011, the reputable company IDC published its report, which unsatisfactorily assesses the level of their secrecy and resistance to hacking. Experts recommended increasing the level of authorization and encrypting files in the storage location and during transfer. Most developers listened to the recommendations and made changes to their applications.
The entrance to the Cloud Storage can be protected by two-factor authorization: specifying the password and confirming the entrance using the phone. But most users only need one password.
When compiling this rating, the company's experts took into account technological solutions to ensure the security of user data and the presence of failures in the service in the past. Considering that all the repositories presented on the diagram have been working for more than 5 years, the history of statistics of failed situations is comparable.
- The safest recognized OneDrive. The experts added to the advantages of the service innovative security system when the keys to encrypted files and the data itself are stored on separate servers. By gaining access to only one of these arrays, an attacker will not be able to obtain benefits. Recall that OneDrive is focused on the corporate market and is the default drive when you sign up for Office365. Subscribers are allocated up to 100 GB immediately, while free users receive only 6 GB.
- The second for security is named iCloud Drive. This cloud serves users of the apple ecosystem: iPhone, MacBook and other corporate solutions of the corporation. Data encryption is performed both during storage and during transmission. In general, the storage is reliable and comparable to OneDrive in terms of security, but earned a negative point for a crash in 2014. This scandal attracted many users. Private photos of the stars stored on their iPhone went online. if you use the Apple technique, then you can’t do without a corporate cloud. It backs up data and system settings of the phone and laptop. With it, deleted photos and documents are restored.
- Third place given Google drive. The reason is insufficient security when storing files . When data is transmitted to the server and to the client device, traffic is encrypted. In the advantages of the cloud, experts brought in two-factor authorization with a password confirmation via SMS to the phone specified during registration. Experts note that in business accounts designed for corporations, Google Drive provides an increased level of security comparable to OneDrive. Ordinary users are encouraged to encrypt sensitive data on their own. For example, archive them with a password.
- Fourth place in Russian Yandex.Disk. The security advantages of this cloud included a wide range of authentication methods, including TouchID, PIN and QR codes. An important advantage for ordinary users - file scanning for viruses . The transfer channel at the Yandex store is encrypted, like competitors. The only serious malfunction is considered to be a mistake in the client program of the service for Windows, made by the company's programmers in 2013. Users on the bill did not stay. He allocated 200 GB of disk space for unlimited free use as compensation.
- Fifth place at the old-timer of the market - Dropbox. The lack of safety is no client side encryption . Theoretically, this allows an attacker to intercept data when transferring from a local device to a server. In 2011, there was a serious malfunction in the DropBox service. It lasted only 4 hours. During this period of time, it was possible to access the entire repository, and not just the data area of \u200b\u200ba specific user. But we note that in 2011 there were simply no other competitors from the rating. DropBox was a pioneer in the field of network storage and was entitled to errors.
How to get more free disk space
All cloud storage is commercial. Their main task is to earn the money required to cover the costs of supporting the development team and developing the server infrastructure. Therefore, free space is provided to users for a limited amount of space. To get an additional free place to store photos and documents, you will need to fulfill certain conditions of the service or participate in promotions.
For example. Yandex.Disk offers 32 gigabytes of free space. Startup photos on your mobile device.
Other cloud services also offer the opportunity to increase space for free:
- For inviting friends.
- For installing a mobile cloud disk application or program on a computer.
- Students and teachers for providing photographs of student ID cards or university admissions. Yandex.Disk on this promotion allocates an additional 32 free gigabytes.
Also, cloud file storage services provide a free space on an affiliate scheme. For example, when buying laptops or tablets of a certain brand.
A universal way to repeatedly increase the space on cloud storage for free is to create several accounts.
How to install a cloud drive on a computer
Three network storages are most suitable for a computer:
- Google Drive He is chosen by active users of GMail services and Google Docs, a powerful online document and spreadsheet editor.
- Yandex.Disk. A good choice when you don’t need to use Google services. This is a reliable Russian cloud drive, for which without difficulties you can get up to 42 GB or more free space by turning on autoload photos on your mobile device.
- OneDrive Users of computers and laptops with the Windows 10 operating system get support for this network drive “to the load”. If you have a Windows account, 5 GB of space is allocated on OneDrive. In the shortcut This computer creates the folder of the same name, synchronized with the cloud.
Installing the program on a computer is required only for the first two services. OneDrive support is implemented at the system level. We give step-by-step instructions for installing the application using the example of Yandex.Disk.
Every modern smartphone out of the box includes support for at least one cloud storage.
- Apple phones come with iCloud support to back up settings, system files, and sync photos. In addition, you can connect Yandex storage using the program downloaded and installed from the official store of the Apple application.
- Samsung phones include support for two clouds at once: the proprietary Samsung Cloud and Google Drive. Owners of smartphones of this brand have a Google account, as Android users and a Samsung account for the manufacturer’s branded services.
- Xiaomi phones “out of the box” communicate with Xiaomi's own MiCloud cloud. Everything works by analogy with the iPhone: backups are made to the network storage on the network and photos are sent from the camera.
- Windows Phone smartphones come with OneDrive enabled. If you have a subscription to Office365, the amount of available volume increases by 100 GB.
- Android smartphones from other manufacturers have support for one cloud storage - Google Drive.
You can purchase additional space by fulfilling the requirements of shares of services or buying it for money.
Please note that Android smartphones support Google Drive, but to work with Google Docs and spreadsheets, you will need to install separate mobile applications. There is also a client program from Google Drive for easy navigation through network storage. The latter is most often preinstalled on the phone.
If you do not have enough features of the preinstalled network drive, install a third-party one. The most popular: Yandex.Disk, DropBox, Mail.ru.
We will show the installation of the application for them using the example of Yandex Drive.

Create a complex password. The likelihood of your private photos and videos leaking online is more likely if you come up with a simple password. Complex can be generated using a special program or invented by yourself according to the following algorithm:! -! 123HELLO-WoRlD123! - !. This combination is easy to remember, but it is very difficult to crack a password.
Encrypt sensitive data before uploading to the network. It’s dangerous to store passwords and account keys in the clear. If there is no special program for encryption, archive confidential files with a password before sending them to the network.
Use dual authorization. A number of network attached storage supports dual authorization. You need to enter the password and confirm the entry by sending the code from the SMS sent by the service. This procedure seems less convenient, but provides more data protection.
History of Cloud File Storage Technologies
The phrase “cloud technology” was first used in 1997. The new global global network required a new computing paradigm. Professor Ramnat Cellap of the University of Texas proposed a move to cloud computing as an alternative to building the power of local computing.
Real developments regarding the sharing of resources on the network date back to 2000. We owe Amazon the commercial launch of the service on the new cloud-based work scheme. This happened in 2002.
Google pioneered the introduction and development of cloud-based applications running through a browser. New technology has been launched on the market since 2009.
The idea of \u200b\u200bcreating cloud storage on the Internet is described by its inventor Drew Hauston as follows. The guy was sitting on the bus from Boston to New York, with a laptop, but without a flash drive left at home. To defeat poverty, he began to think about accessing files without wires and came up with an application that implements this idea. The first DropBox code is written, according to this version of events, right on the bus.
According to the founder of DropBox, the project in the startup phase wanted to acquire Steve Jobs, but was refused. Today, the company costs about 4 billion US dollars.
All subsequent network storages: iCloud, Google and Yandex, appeared much later. Their main promotion paradigm is the shareware service. The user receives part of gigabytes at once, free of charge and unconditionally. The rest should be bought by subscription.
Modern cloud drives have become not only a place to store information, but they offer a number of technological solutions for collaborating on files to people living in different parts of the world. About the most popular problems solved with their help, further.
Report Content
Copyright Infringement Spam Inappropriate Content Broken Links