In the last 3-4 years, news has regularly appeared in the feed with the headline: "The government wants to block Tor." But, this idea is somewhat utopian.
The darknet can be used in all fears of the world except North Korea, where a special permission from Kim Jong-un is required to access a computer with the Internet. Even China has failed to ban it. The Golden Shield automatically blocks all new Tor entry node addresses, but people who need to bypass this barrier using VPNs and proxy servers.
News about the "ban on the underground Internet" only fuel interest in it among the population. More and more Russians are joining the darknet, which is fraught with many dangers and temptations. The consequences of using Tor incorrectly should be known in advance.
This article will discuss the main types of shops and forums in Tor that should be avoided and the possible responsibility for using / building them.
Fragments of the article were deleted at the request of Roskomnadzor. The material has been edited.
2. Websites with job advertisements
A huge number of advertisements for sale *** contains a postscript: “Looking for ***. Activity, adequacy, professionalism are required. The salary is high. " For one *** an employee receives an average of 500-3000 rubles. On the forums, they write that an intelligent employee has up to 80-120 thousand rubles a month with a free schedule. And this is in the province. In capitals, the ceiling is much higher.
But this work is not nearly as simple as it seems at first glance. To make a good "***" and hide it - a whole science and experienced people write whole textbooks. There are many non-obvious problems that are difficult for a beginner to guess.
For example, how to protect yourself from "seagulls"? This is the name given to *** who are looking for and successfully find strangers *** in typical places (flower beds, holes in the asphalt, porches). Or how to disguise a ziplock bag inside an acorn or nut so that rain and wind won't damage the product?
Tor criminals need not only ***, but also parcel receivers, stencils (make announcements on the pavement), growers (grow plants at home), people to withdraw illegally received money from bank cards. Less often they look for strong guys to intimidate enemies. And each profession has unobvious subtleties that need to be learned in order not to get hold of problems with the law.
In the criminal field, there is a terrible turnover of personnel and new employees are constantly required. A really adequate and tidy person can work for a couple of years, and a simple *** / carrier / drop is free for only a few months. Most people are caught by the police sooner or later. People rarely manage to raise the dough, stop and leave on time.
Possible problems: According to article 228 of the Criminal Code of the Russian Federation, if a person is involved in the distribution or production of ***, then he can be imprisoned for a period of 8 years. We will talk about punishments for parcel receivers and cashiers below.
3. Shops of goods for committing crimes


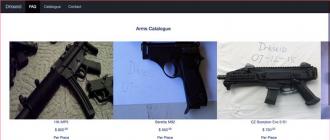
Tor is used to trade weapons, fake documents, left SIM cards, phones, ATM skimmers and a bunch of other interesting items. As with ***, bitcoins are used for anonymous payment. Surprisingly, there are no particular problems with the delivery of goods.
Sometimes it is done using regular mail. To receive and send parcels, they hire "drops" who go to receive / send parcels, shine their faces and passport data. Also, goods are shipped with the help of taxi drivers or private transport companies. Here's a quote from the RuOnion forum:
I somehow sent an optical sight through a transport company, naturally not a branded one. They asked what was inside, answered - a sniper scope, They: we will write it down - an optical device :-)))) They don't really care what to carry ...
But sellers still take many precautions: they disassemble the weapon into parts, which are distributed among several boxes, disguise them as other items, make packages with a double bottom, etc. They have no less tricks than ***.
Possible problems: According to article 222 of the Criminal Code of the Russian Federation, illegal acquisition or transfer of weapons can be punished by a decision of freedom for up to four years. About forged documents is written in article 327 of the Criminal Code of the Russian Federation, it says about a period of up to two years.
4. Pedophile forums
There are also a lot of people on the Tor network who are sexually attracted to children. There are a lot of "interesting" things for them here. First, there are huge archives of porn videos featuring minors. Secondly, these are forums where people share their personal experiences of seducing children and hiding this process from others.
Some pedophiles consider sex with children absolutely unacceptable and sit on the "conservative" sections of the forums, where they post just a little erotic photos of little girls and boys, with closed genitals.
But there are people for whom just watching a video is not enough and they strive to translate their fantasies into reality. The main shock in preparing this article for me was familiarization with a book for pedophiles in Russian.
200 pages on where to find a potentially available child and how to recognize him, how to gain confidence in him, how to leave no traces and how to make sure that the child never tells anyone about what the pervert or pervert did to him.
And judging by the forums, a lot of pedophiles do manage to turn things around in such a way that parents never find out about what happened to their child. Indeed, most often children are seduced not by maniacs on the streets, but by neighbors, relatives or family friends who have been entering the house for many years.
Do not leave your child alone with anyone and never without video surveillance... There are many more pedophiles among us than one might think.
Possible punishment: It is prohibited to store porn videos with the participation of minors on your computer. You can read more about this in the article:
5. Websites of extremist organizations

Terrorists, skinheads and oppositionists of radical views also create websites on the onion network, publish articles there and discuss plans for pogroms or seizing power on forums. Also, sect sites are gradually moving to Tor.
Since 2002, the Russian authorities have kept a list of Federal extremist materials ... It includes nearly 4,000 books, articles, paintings and musical pieces. Rospotrebnadzor forces the removal of such materials from sites in the clearnet, but in the Tor libraries they are distributed freely.
Possible punishment: According to Article 282.2 of the Criminal Code of the Russian Federation, for participation in an extremist organization, they can be imprisoned for up to six years. Also, you cannot copy materials from such sites in Tor and post them on social networks and blogs. There is also a separate article on this topic:
6. "Hacker" trading platforms and forums

International darkmarkets often have a Digital Goods section next to *** and weapons. It sells Trojans, Wi-Fi hacking tools, software hacking tools, DDOS tools, and many other varieties of "digital information illegal" tools.
Along with the programs, you can also buy instructions for their use and training books. They also sell digital goods that were stolen using the tools described above: pumped characters in games, paid accounts of various services, hacked programs, access to infected computers.
There are also many hacker forums on the darknet. There people share their experience, look for perpetrators and accomplices for various cyber crimes.
Possible punishment: If it is proved that a person has used any of the above programs, then according to article 272 of the Criminal Code of the Russian Federation, he can be imprisoned for up to two years.
7. "Black" cryptocurrency exchanges

The sites and organizations described above make financial settlements in bitcoins (less often in another cryptocurrency). And of course, they do not pay any taxes on this. With the help of cryptocurrencies, money obtained illegally is cashed out.
Tor has exchanges for withdrawing bitcoins to regular e-wallets or bank cards. It is also full of ads of people who withdraw money from cryptocurrency wallets to offshore accounts or transfer to the account of a "one-day firm". From the latter, money can be withdrawn using ordinary "cashiers".
There you can also order bank cards issued for dummies or "virtuals". And hire drops who will go to the ATM, shine their faces in front of cameras, withdraw cash from cards and deliver to you.
Possible punishment: According to article 159 of the Criminal Code of the Russian Federation, participation in group fraudulent schemes can lead to up to 10 years in prison.
Also in the State Duma they say from the adoption of a bill that provides for punishment of up to four years in prison simply for using bitcoins or other cryptocurrencies.
conclusions
Not all types of content that can be found on the Tor network are described above. Sites with erotica for animal lovers, stolen goods stores, sites for ordering killers and much more are not mentioned.
But the above is enough to understand why governments around the world seek to control the Internet. Personal freedom and privacy are good. But how to fight criminals on the Internet without blocking sites and controlling traffic?
P.S. Is Tor anonymous
There are so many tutorials on the dark web on how to secure online anonymity. Some of the authors consider a virtual machine with Tails -\u003e vpn -\u003e vpn -\u003e Tor a sufficient scheme. And someone recommends buying a computer from a flea market in the neighboring area and using a modem through the "left" SIM card. But one thing is for sure - if you just start the Tor browser, then your level of anonymity is quite low.
Intelligence agencies around the world are actively working to identify the criminals who use the "underground Internet". For example, in the fall of 2016, as part of the international Operation Titan, the Swedish police identified 3,000 customers *** in Tor. And there are more and more reports of such investigations every year.
We have released a new book, “Content Marketing on Social Media: How to Get Into the Heads of Subscribers and Fall in Love with Your Brand”.

The TOR network is a system designed for network connection in an anonymous mode, protected from eavesdropping and without the ability to track user actions.
More videos on our channel - learn internet marketing with SEMANTICA
![]()
In simple words, TOP is a network where the user completely retains his anonymity on the Internet. At the same time, it does not really matter what he will do - visit sites, maintain his own blog, send messages.
Traffic anonymity is possible due to the use of a server network distributed throughout the world with redirection to tens (and in some cases hundreds) of nodes. Anyone who downloads and installs it on a computer can use the capabilities of such a network.
The screenshot shows the procedure for determining the ip-address of the user's computer (the PC is physically located at this moment in Voronezh, Russia).
Why TOP technologies can be useful
There are several reasons why anonymity may be needed:
- the ability to access sites,
- blocked by regional providers;
- unwillingness to disclose data about the computer and its location;
- hiding personal data and ensuring the security of information on a PC.
Basic principles of the TOP network
To understand what TOR is, you need to understand how the system works. It consists of several main nodes:
- Input or watchdog - with the help of this node, a direct entrance to the network occurs. As a rule, the input nodes are stable and high-speed servers.
- Intermediate - designed to transfer information from the input node to the output, making it almost impossible to track all information movements. The number of intermediate nodes is constantly changing and in some situations can reach several hundreds.
- Egress - The point used to send traffic to the user.
The anonymous TOP network allows the use of numerous virtual servers of the DigitalOcean or EC2 standards, thanks to which, when tracking data, only traffic that has been repeatedly encrypted will be displayed.
How to install the TOP browser
Initially, to use TOR, it was necessary to have a lot of specialized knowledge and skills to connect to the network, but now the procedure is extremely simple - you need to download (the distribution kit can be found on the website http://tor-browser.ru/ - it is in the public domain) and install application to your computer.
You can download the TOP browser on many other resources, but it is important to remember that many not entirely honest developers hide viruses or spyware under the installation file. Therefore, it is important to download the file for installation only from trusted resources and after downloading the file, it is advisable to check it with an antivirus.
In order to install the TOP network, just open the downloaded file, select the installation language and click “install”.

The installation procedure is standard and rarely causes difficulties, but launching the program has certain peculiarities - every time the program starts, you must connect to the TOP network, otherwise you can forget about anonymity.

While working with the TOP network, the user can change the chain of servers for a particular site to make it almost impossible to track it.

An important feature of the browser and the network is that after the window is closed, the data on the sites and resources visited by the user is automatically deleted. Therefore, the next time you enter certain sites and resources, the login / password will have to be entered again.
Risks when using TOP
It doesn't take a lot of effort to set up a TOP network, but there are a few things that can cause a lot of hassle for users.
- An important aspect is the use of plugins and add-ons that send them user data to developers - anonymity in such a situation will be zero.
- Despite anonymous visits to sites, the user's computer with the installed TOP is completely unprotected from viruses, Trojans and hacker attacks. Therefore, it is important to use quality antiviruses and firewalls, which must be properly configured.
- You should be prepared for the fact that the page loading speed will fall dramatically, since the page requested by the user is transmitted for a long time by hundreds of servers located around the world. But this problem does not scare users, since you can completely hide your online activity.
Most of the Internet users have heard of Tor and imagine what this network is. Its main task is to allow people to hide their identity on the world wide web, as well as to interfere with surveillance mechanisms on the Internet. A browser of the same name is used to access this network.
At the same time, many people are seriously convinced that for anonymous web surfing, it is enough just to install and launch the Tor browser. But they are all deeply mistaken. In fact, the browser needs to be preconfigured for maximum privacy before diving into the dark web. Today's article will provide practical advice on where to download, how to install, configure and use Tor, as well as how to behave in the deep web and what absolutely should not be done.
Where to download and how to install Tor Browser
It would seem that there is nothing easier: download the application, run the installer and use it with a clear conscience. But no. The Tor browser can only be downloaded from the official website or trusted sources. It's better to forget about torrent trackers, file wipers and phishing sites. At best, there will be an outdated version of the software, at worst - a program infected with a virus. In the second case, there is no need to explain what is bad here, but the old version may have some vulnerabilities that were fixed in the update.
After that, you will need to run the installation file. In the window that appears, select the interface language, then specify the path (by default, the path where the installation file is located), click the "Install" button and wait for the operation to end.
Although any browser can be connected to the Tor network, it is important to use the original Tor Browser exclusively. The point is that this browser is configured appropriately, while others may leak confidential information.
Launching Tor Browser for the first time






After the installation of Tor is complete, you will be greeted by a window where you will be prompted to "Connect" or "Configure" the connection. You can immediately press the first button. If the browser cannot establish a connection, you need to click the "Configure" button and activate the item "Tor is prohibited in my country", where you also check one of the items. If the first item is activated, you need to select the type "obfs4" in the drop-down list, in the second, you will be asked to go through the captcha and then will be issued the so-called. bridges.



Also, when you first start on the About Tor home page, you need to click on the New to Tor Browser? Let's start "in the upper left corner and take the" Young Fighter Course ". In the "Security" section, you will need to select one of three parameters, in which JavaScript and some functions on sites are limited or completely disabled.
Tweaking Tor Browser
Now that the browser has managed to connect to the Tor services, it's time to fine tune it. There are several ways to do this, and we will now consider each of them.
Configuring the NoScript extension
The Tor browser comes with the NoScript extension preinstalled for a reason. In the right hands, this is a very powerful tool that allows you to reduce the risks of deanonymization to almost zero. By default, NoScript is configured pretty well, but it's worth talking about additional features of this extension that will make you even more secure.
To change the NoScript parameters, you need to click on the add-on icon in the upper right corner of the browser and go to the settings by clicking on the "Settings ..." button. Next, you need to change the settings for all levels of trust (default, trusted, untrusted).

For the "Default" and "Untrusted" levels, it is recommended to uncheck all the items, for "Trusted" - set all or a few necessary ones.

Here are the designations of this or that item:
- Script - different types of scripts that are executed on sites
- Object - HTML elements tagged with object
- Media - multimedia content
- Frame - the frames the site is trying to load
- Font - fonts
- WebGL - WebGL elements
- Fetch - API for making various HTTP requests
- Other - unknown elements
Also, on the "General" tab, do not activate the item "Disable restrictions globally", and on the "Advanced" tab, be sure to check the box for "Secure suspicious cross-site requests".

In addition, you can fine-tune various permissions for any site. For example, for one resource, allow only scripts and multimedia to be executed, for another, disable custom fonts. Trust levels can be set only temporarily or permanently.
Configuring hidden browser options
In addition to the NoScript extension, it would be nice to customize the browser itself in order to even better protect yourself from possible leakage of confidential data. Although Firefox is considered a safe browser, especially with an add-on from Tor, it still has controversial points that were not changed by default for various reasons.












To find the very hidden parameters, you need to enter "about: config" in the address bar. Then enter the following values \u200b\u200binto the search one by one and change them. To edit the parameters, double-click the left mouse button or right-click and select "Toggle". Here's a list of features to change:
- "Javascript.enabled" → false
- "Network.http.sendRefererHeader" → 0
- "Network.cookie.cookieBehavior" → 2
- "Browser.ping-center.telemetry" → false
- "Toolkit.telemetry.archive.enabled" → false
- "Toolkit.telemetry.bhrPing.enabled" → false
- "Toolkit.telemetry.firstShutdownPing.enabled" → false
- "Toolkit.telemetry.hybridContent.enabled" → false
- "Toolkit.telemetry.newProfilePing.enabled" → false
- "Toolkit.telemetry.reportingpolicy.firstRun" → false
- "Toolkit.telemetry.shutdownPingSender.enabled" → false
- "Toolkit.telemetry.updatePing.enabled" → false
- "Toolkit.telemetry.server" -\u003e delete all values \u200b\u200bin line
After the actions taken, some sites may not work correctly in this browser. Therefore, you can always return some settings to their previous state, but this, of course, is not recommended.
Modifying the Tor Browser config file
The Tor developers have provided a few other things that can help you to be even more secure and improve network performance. These values \u200b\u200bneed to be edited in the configuration file, they cannot be found in the graphical interface. However, this will not be difficult at all.
To edit the configuration file, you need to go to the folder where Tor Browser is installed and open the file along the path "/ Browser / TorBrowser / Data / Tor / torrc". You can now add the required values \u200b\u200bat the end of this file. We will list only the most important ones.
- ExitNodes (COUNTRY)
For example, ExitNodes (us) or ExitNodes (us), (de), (fr)
This parameter overrides the default output node. You can set one value or several. The country is specified as a 2-letter ISO3166 code. - EntryNodes (COUNTRY)
This parameter overrides the default input node. You can set one value or several. The country is specified as a 2-letter ISO3166 code. - ExcludeNodes (COUNTRY)
For example, EntryNodes (us) or EntryNodes (us), (de), (fr)
This parameter tells Tor through which nodes it cannot connect to the network and avoid them. You can set one value or several. The country is specified as a 2-letter ISO3166 code. - StrictNodes NUM
For example, StrictNodes 0 or StrictNodes 1
This parameter tells Tor whether it is possible to connect to forbidden nodes (defined in the previous paragraph). If the value is set to "1", then the browser, in the case of found nodes only from the list of exclusions, will not be able to access the network. If the value is "0", the network will continue to enter the network even through the excluded nodes.
As mentioned above, we have listed only a few of the most significant values \u200b\u200bthat are understandable to an ordinary user. And the entire list of relevant parameters and commands that can be set and what values \u200b\u200bto prescribe them can be found in the official documentation.
How to use Tor Browser
No matter how well you configure your browser, NoScript extension, fix configs, etc., this will not be able to save you 100% from personal data leakage and deanonymization. After all, the most important moment that determines this is the human factor. In this section, we will list what should in no case be done using the Tor browser.
- Do not install unnecessary and unverified extensions into the browser.
- Under no excuse not to disable the NoScript add-on.
- Update the node chain frequently and switch the "New Identity".
- Do not open Tor browser in full screen.
- Do not run the Tor browser as an administrator.
- Never log into your inbox, social media accounts or other resources that have any information about you or that are somehow connected with your real accounts. The only exceptions are Onion sites and forums. And, of course, you need to create a separate mail for registration on such resources.
- Use the main system instead of the virtual one to access the Tor network.
- Check all files downloaded on the darknet for viruses, run them in a virtual machine with the Internet disconnected and do not do this on the main system.
- Check your browser regularly for updates and install them in a timely manner.
- You should not blindly trust people “on the other end of the line” - there may be both law enforcement agencies (if you have done something illegal), and hackers or ordinary “scammers” who are looking for easy money.
If you adhere to these rules, the risk of revealing your identity will be very difficult. No one will ever be able to completely secure you: all technologies can be hacked by a person, since they are created by him, and the rest depends on you and your behavior.
In today's article, we have covered important topics on installing and configuring the Tor browser, as well as on the correct behavior on a secure network. Everyone can learn something important, whether you are paranoid or a regular user who wants to get to a blocked site. If you are not satisfied with the speed of connection in Tor and you do not need total deanonymization, but at the same time you need to switch to resources inaccessible in your country and protect your data from the provider or other inquisitive persons, we recommend that you.
If you still have any questions or have something to supplement the article - write about it in the comments.
TOR browser is perhaps the easiest and most affordable way to connect to the Internet anonymously. Now we will tell you how to set up the TOR browser on your computer, as well as where to download it and how to install it.
Step # 1. Download the TOP browser.
TOP Browser is a free browser built on top of Firefox. You can download it from the developer's official website. To do this, go to the site, select a language and click on the "Download" button. Then the download of the installation files will start.
By default, the site will offer to download the version of the TOP browser that is suitable for your operating system. If you want to download a version for another OS, then you can do this.
Step # 2. Installing the TOP browser.
At the stage of installing TOP, the browser does not require any additional configuration. Everything happens automatically, you just need to follow the instructions that appear on the screen. So first you need to select the browser language.

And then the folder where the TOP browser will be installed.

After that, it remains only to wait until the installation is completed.

Step # 3. Launch and configure the Tor browser.
After starting the TOR browser, you will see a window called "TOR network settings".
There are two buttons available here: Connect and Configure. If you click the "Connect" button, the TOP browser will start working with standard settings. This option is suitable for most cases.

The "Configure" button will start manual configuration of the TOP browser. This option can be useful if you connect to the Internet through a proxy server or if your ISP blocks the TOR network. First of all, the TOR browser will first ask if your ISP is blocking the TOR network. If there are no problems with connecting to the TOR network or you do not know for sure, then select the "NO" option.

If you select "Yes", then the TOP browser will offer to configure bridges. A bridge is a point in the TOR network whose address is not published in the TOR documentation. You can download the list of bridges on the website.

After configuring the TOP bridges, the browser will offer to configure an Internet connection through a proxy server. If you connect to the Internet directly (without using a proxy server), then here you need to select the "NO" option.

If a proxy server is used to connect to the Internet, then you need to select the "YES" option and configure the connections. The TOP browser will ask you to select the type of proxy server, its IP address, as well as other proxy-related settings.

After setting up the proxy server, you just need to click on the connect button and the TOR browser will connect to the Internet through the TOR network.
Step # 4. Checking the TOP browser settings.
If you have configured the TOP browser correctly, the following message should appear on the screen: “Congratulations! This browser is configured to use TOR. "

If the screen says: “Alas. You are not using TOR at the moment ”, this means that there is something wrong with the TOR browser settings and it was not possible to connect to the TOR network. In this case, you can click on the onion button and select "TOR Network Settings" or simply press the S key on your keyboard.

Then you can re-configure the TOR browser.
Step # 5. Change the IP address in the TOP browser.
Immediately after connecting to the Internet through the TOR network, you get a new IP address. But, if necessary, this address can be changed. To do this, press the onion-shaped button and select the menu item "New TOR chain for this site".

After that the page will be refreshed and you will receive a new IP address. You can check how it works on any site to check the IP address, for example, you can use the site.