The life of a modern person is already impossible to imagine without mobile gadgets. They simplify our life, make it more comfortable. But only attackers often use this, therefore, today we will talk about how to find out if a mobile phone is being tapped. Consider the main signs that indicate the presence of wiretapping.
First of all, people whose profession is connected with confidential data, as well as overly jealous spouses, are at risk. It is possible to understand that information is “merged” by phone to third parties after people who are not initiated into these secrets find themselves in the course of secret information. There are technical signs that make it possible to suspect and find out that the device is being tapped.
- Extraneous sounds, echo during a conversation. If during a call you regularly hear extraneous sounds - this is a clear cause for concern. There may be noise, clicks, gurgling, hum, claps, and more. To check such extraneous noise, you can use the sound sensor set to a low frequency. When the arrow rolls over with regularity several times per minute - this is an alarm.
- Mobile does not work correctly. You should always pay attention to the stability of the phone. If it reboots on its own, the battery charge decreases too quickly for no particular reason - maybe the device is being tapped. Another sign is that the battery is very hot. This is because eavesdropping equipment uses the battery in the background.

There are many options that indicate that your phone calls are of interest to third parties. Regardless of the brand of the gadget, loopholes for wiretapping are always there. If in doubt, you should pay attention to such signs:
- call connection is established for a long time;
- the device turns off slowly;
- the device spontaneously turns on, deactivates and starts installing software.
How do I know if a mobile phone is currently being tapped?
Simple household appliances can help in this situation. You should approach the TV during the call, if there is interference caused by extraneous electronic equipment - this is wiretapping. There are devices that are close to the FM range and can make a piercing sound when the radio is in mono mode. This also applies to turning on the TV in the UHF frequency mode.
Operator Services
Be sure to pay attention to all messages arriving on the phone. In suspicious SMS, strange combinations of letters, numbers, symbols are usually spelled out. They come from unfamiliar numbers. This is a distribution of commands sent by listening programs. Sometimes scammers use the mobile Internet to introduce, so that the payment account is increased. If you have not connected the Conference Call option from the provider, but it is activated all the time, this is also a symptom of wiretapping.
We use specialized equipment
Special devices have been developed for a long time that immediately reveal all listening attempts. They are connected to a mobile phone and measure the resistance, capacitance, signal changes at very high frequencies. In order to find out if a smartphone is being tapped, you should connect a similar device to your gadget and look at the difference in performance.
Verification Code
There are several combinations that may help. For example, dial * 33 * on the phone and enter any characters further. If you cannot enter a character after the second asterisk, then the gadget is listened to. Some professionals consider this option ineffective, so you should use others.

*#21# - this code determines whether call forwarding is activated on your device, that is, whether your calls and SMS can be transferred to unauthorized persons.
*#62# - You will find out what number the call forwarding is set to, where the wiretap is directed, it will work if the device is disabled or outside the access zone.

##002# - deactivates any call forwarding.
We will use applications
Mobile software developers have long released decent products that can help you find out. Most popular programs:
- - Paid, but many users consider it effective;

- Darshak - A free application that not only detects any suspicious activity, but also evaluates the security capabilities of the mobile operator;
- - distributed free of charge, version in Russian. Has a good rating in Google Play.

Provider Help
If you suspect that the smartphone is being tapped, you can contact your operator. There, experts have all the necessary technical means to make an analysis of the condition of the line. According to the results of this procedure, it is easy to identify the fact of wiretapping. If necessary, you can then install the software so that third parties can no longer "listen" to you.

How can a device be tapped?
There are several ways that you can "follow" on your smartphone:
- official - special services request access to the telephone conversations of the subscriber;
- the signal is intercepted - with the help of equipment fraudsters intercept the signal and receive all the necessary information;
- malware is installed - the gadget starts recording all conversations on a USB flash drive, sending them to another phone, and more;
- installation of listening devices - “bugs” send a signal to the equipment of fraudsters.
It is better not to transfer important and confidential information about your bank cards, passwords, information about large payments in telephone conversations. It is worth reporting such data in person.
Now you can answer the question of how to find out if a user is listening on a mobile phone. So, if necessary, you can use one of the proposed methods. Subscribe to blog updates in order not to miss the most relevant and useful information.
You need to understand that the attackers will not hide the bug in a wardrobe, mattress (under the bed) or under the wallpaper - all these places make it difficult to hear, therefore they are not suitable for installing wiretapping. If it comes to video tracking, then the camera is most often attached so that there is a good overview - that is, under the ceiling or on the TV.
How to find a wiretap using a mobile phone
If you are going to organize in your home or office, then you need to prepare for this.
- Firstly, you should not tell anyone about your suspicions, and even less so in the room where the alleged wiretapping is located. Because many spy devices can be turned off remotely: they heard you, clicked on a button, and that’s all, finding an eavesdropping will become even more difficult than before. If you are afraid of video tracking, pretend that you have lost something before searching for a bug.
- Secondly, carefully inspect the entire housing or office, paying great attention to the places described above. Before that, think about who was in the room and how much time he spent there - such an analysis can give an idea of \u200b\u200bthe place where the wiretap is hidden.
- Thirdly - use your cellular. If a secrets hunter does not have a multi-million dollar fortune, he is likely to choose the equipment cheaper. And such a wiretap can be found using a mobile phone, because they will definitely respond to its waves. Walk around the whole room slowly, talking on your cell phone - approaching the bug will cause a reaction in the form of noises, crackles and other noise.
When trying to detect a bug using your phone, you must understand that the percentage of success in this matter is very small. Finding listening devices is a matter that is best left to professionals. After all, you can search for a wiretap for a very long time, but never find it - and continue to remain “on the hook”. And the purchase of special equipment will cost a lot of money and time to learn how to use it. Therefore, in order not to leave doubts, it is best to turn to specialists who will do their job quickly, confidentially and efficiently.
On any iphone or ipad, you can install wiretapping as easily as on any android phone or tablet. It’s just that the programs will be different, and they are also put in different ways. But there are no problems. There are problems when this is your phone and you suspect that you installed a spyware program on it. What to do, where to run, how to find and how to remove? Everything is not simple, but if there is a need, then there is a way out too, and we will show it now.
We have already described the general protective theory:
If you are too lazy to read, the point in short is that you can find a spyware program on your phone, but this is a matter of probability and does not guarantee anything. You need to search by indirect signs by the method of mathematical deduction. To completely remove distrust in the phone, you need to completely reflash the phone.
In this article, we’ll elaborate on iPhones a bit. Let's talk about how to check the iPhone for wiretapping and how to remove it with guarantee.

About how to find out the wiretapping of an iPhone can be found at the link above, in a general orientation material. However, there is one nuance specific to iPhones, whose name is jailbreak. This is literally an iOS hack, necessary for installing applications not from the AppStore. It is done by many on their own, to expand the capabilities of their phone. But if you didn’t do it, but it exists, that is, there is a possibility that a spyware program was downloaded on the phone. Just without a jailbreak, a mobile spy will not be fully spyware. It will be (if it turns out to be filled at all) with the usual application and by scrolling through the lists of installed you can delete it. If there is a suspicion of draining information about you through your iPhone, while there is a jailbreak that you did not do, that is, there is a very high probability that you are being watched through the phone.
There are special utilities for determining jailbreak on iphone, for example, iFunBox. Or you can search for the installed Cydia program, which it actually does (and which is often hidden). But the first method is more reliable.
We figured out how to check an iPhone for wiretapping (in the lists of installed applications we are looking for something “obviously spyware” or by indirect signs and the presence of a jailbreak). Now about how it is guaranteed to demolish it, if it did not work to find the spy program on the phone, and there are more than enough suspicions. Or just not at ease and I want to be sure of the cleanliness of the phone.
Alas, only a full flashing of the iphone can give a guarantee. This, as they say on the Internet, is not difficult to do. You just need to backup the data, download the correct version of the OS (in accordance with the inscription on the back cover of the iPhone) and disable the device’s search function in case of loss. Next, using itunes, re-download the OS to your apple in accordance with the step-by-step instructions. As an option - give the phone to specialists.
Related materials:

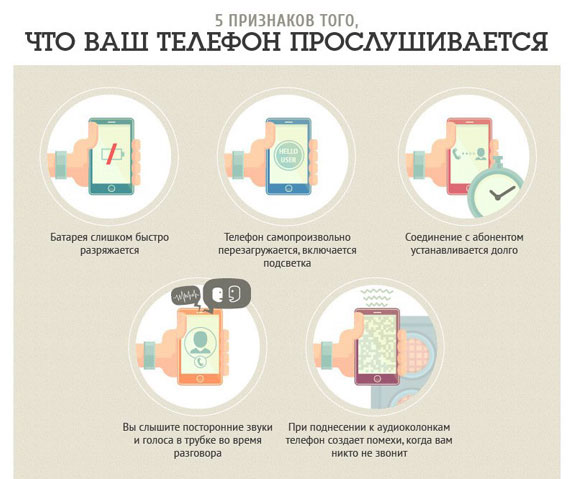
With modern technology and permissiveness, wiretapping is becoming a fairly simple task. We tell you how to determine what they are listening to, and how to protect yourself from this.
1. The phone is noisy when talking

Hissing and other suspicious sounds during a conversation is the first sign of wiretapping. If the sound is like a steady hum or rustling, the probability of wiretapping is higher. If this is an occasional crack or loss of sound - below.
Of course, you can also hear echo, static noise, or clicks due to interference on the line. But it’s worth checking. By the way, sometimes diagnostics of the speaker and microphone help get rid of suspicions.
2. The smartphone makes strange noises in standby mode

You put the phone near the speaker, and it emits a characteristic creak? The mess.
Generally speaking, the device can fonit and generate interference several times per hour or less, since it periodically connects to the base station to check the network location. But if the speaker, next to which the smartphone lies, creaks much more often, and the story repeats with other speakers, this is one of the signs of wiretapping.
It also happens that there are sounds, but you do not hear them. Use the low frequency sound sensor. If his arrow rolls over several times a minute, this is suspicious.
Important: the sound meter application on the smartphone may not detect such sounds. A significant part of the input paths of smartphones is tuned to a human voice (300-3400 Hz, 40-60 dB) and cut off all out-of-band signals. In addition, sometimes smartphones limit the input signal level in hardware, and this affects the accuracy of the measurements.
3. Connection established too long

If a smartphone with a delay connects to a subscriber and does not turn off immediately after a conversation, this is an occasion to think. Most often this happens if a malicious application for wiretapping is installed on it.
4. The phone heats up and consumes power too quickly

A gadget that just lies in your pocket should not heat up. If you notice a problem, either they are listening to you, or some other virus, a miner, for example, has got on your smartphone.
Find out where the energy goes:
- iOS: “Settings” - “Battery”.
- Android: “Settings” - “Battery” (or “Battery”).
In addition, apps like BatteryLife LX or Battery LED for iOS, AccuBattery, and Android effectively track energy consumption.
5. The device began to shut down, slow down, reboot without a reason

Another indirect feature of the wiretap application installed on your smartphone. Malicious applications often overload the device’s resources or crashes in its operation.
6. Traffic consumption increased sharply

Some wiretap applications store data and then transfer it over Wi-Fi. But there are those who take advantage of every opportunity and include the transfer of data on the mobile network to give the collected information.
If you are not more than usual sitting on and on Facebook, but the packet megabytes have literally disappeared, check which application can consume traffic. Wi-Fi statistics will also be worth looking into.
- iOS: “Settings” - “Cellular communication” () and a third-party application (for example, Traffic Monitor) for Wi-Fi.
- Android: “Settings” - “Data Transfer”, usually there are two tabs: “Mobile traffic” and “Wi-Fi”.
There are also applications like Internet Speed \u200b\u200bMeter Lite or My Data Manager that help monitor traffic consumption.
7. Strange SMS arrive

Messages with incomprehensible letters and numbers sent from unknown numbers can be encrypted commands for listening applications. Try to rearrange the SIM-card in the button "dialer". If messages still arrive, this is not a glitch, but a serious reason for suspicion.
And if a suspicious van is on duty under the windows?

So you've seen enough spy movies. Nowadays, stations are rarely used for wiretapping - it is easier to request data from SORM, which is installed by each operator, or to infect with malware like FinFisher.
But still, the mobile systems for wiretapping, to which your phone wants to connect, are pretty easy to calculate. Type the following combination:
- iOS * 3001 # 12345 # *
- Android * # * # 4636 # * # * or * # * # 197328640 # * # *
It will open access to the data of the netmonitor utility. It will produce something like this:

In Android, usually all data is available immediately. We are interested in the Cell ID (CID) and LAC (Local Area Code) fields.
On iPhone, go to the UMTS Cell Environment tab - UMTS RR info and see the value of the Cell ID field. And the LAC is shown on the tab MM info - Serving PLMN.
The Cell ID value changes over time: the smartphone selects the base station taking into account the range, signal strength, etc. While the phone is in one place, it usually goes through no more than 3-5 base stations. Their Cell ID must be written out and stored. And if with the advent of a strange van outside the window in netmonitor you see the Cell ID of the new base station, then you are being listened to.
In the service http://xinit.ru/bs/ you can find out the coordinates of the base station by LAC and Cell ID:

Here's what I got:

Can law enforcement listen on a smartphone

Yes they can. But only by court order.
But in fact, you can listen to the desired number if you add it to the case, referring to the “operational necessity”. Or use a corruption scheme. It is clear that such options are illegal, but it will be extremely difficult to prove it.
What to do if your smartphone is tapped

The most difficult thing is to understand why someone needed to listen to your smartphone at all. A spouse can collect evidence of infidelity, a boss or colleague - suspect you of kickbacks or a drain of information, thieves - check your schedule to choose the best time for a robbery.
- Technically, you should start by checking your smartphone for viruses and unwanted software. Try several anti-virus programs with fresh databases, because it often happens that each of them does not see all the malware.
- Save all the necessary data and reset the smartphone to the factory settings. Turn off data transfer and Wi-Fi, insert a SIM card with zero balance and take your smartphone where there is no Wi-Fi. Perhaps after some time the malware will display an error message and detect itself.
- Practical advice: find the person you trust and share “super-secret” (but actually false) information with him. If outsiders find out about this, then either your friend is not that kind of friend, or they still listen to you. In the second option, get a button “dialer” for secret conversations and communicate, putting the smartphone away - its microphone should not hear your conversations.
- To protect your smartphone from connecting to false base stations, use
https: //www.site/2013-08-19/kto_kak_i_zachem_proslushivaet_vashi_razgovory_i_chitaet_perepisku_issledovanie_site
“Tc-ss. This is not by telephone. ”
Who, how and why listens to your conversations and reads correspondence. Study site

Not on the phone. “Now I’ll call you from another number.” "Let's go outside, take a walk, it's better not to talk here." Such phrases have firmly entered the life of the Russian establishment, and even a few years ago they complained of complaining about wiretapping phones and cabinets as half-crazy, like those who wear foil caps and believe in the KGB zombie rays. Today everyone knows: they listen to everyone, they listen without regard to the law and the materials of these wiretaps are often used not in court, but in political intrigues, denunciations, provocations. the site spoke with one of the professionals in the shadow market for electronic intelligence to find out how this area works.
Who is listening
In the language of law enforcement, wiretapping of phones and control of Internet traffic are called the abbreviation "SORM" - "System of technical means to ensure the functions of operational-search measures." SORM-1 is a set of measures aimed at wiretapping mobile communications, SORM-2 is a mobile Internet traffic. Today, such investigative techniques come to the fore, overshadowing traditional forensic approaches. Accordingly, the units responsible for SORM are becoming more and more influential within the internal affairs bodies. In the Sverdlovsk region, this is, for example, the Bureau of Special Technical Events (BSTM) of the Main Directorate of the Ministry of Internal Affairs in the Sverdlovsk Region and the Operational and Technical Department (UTO) of the UFSB in the Sverdlovsk Region.
By law, wiretapping of phones and control of Internet traffic are possible only by court order. True, the law allows investigators to “turn on the record” even without it, if the case is urgent and wiretapping is necessary to prevent an impending crime. Approximately by the same principle, “as an exception” investigators are allowed to conduct searches, receiving court authorization after the fact. As in the case of searches, law enforcement officers often use this rule to gain uncontrolled access to other people's secrets.
There are also ways to legalize illegal wiretapping by putting the name and phone number of the person you want on a long list of suspects in a criminal case. According to sources in the authorities, judges almost never delve into how a given surname is related to a criminal case, and sign permits in one fell swoop. Such court decisions are classified as “secret”, and who is on the wiretap lists will never be known to citizens.

However, wiretapping experts say: today, more and more often, citizens are “put on record" even without any court decisions. Each telecom operator has equipment installed that allows security forces to access any client’s conversations at any time (the law obliges operators to do this). And in the regional administration of the FSB there is a remote access terminal with which you can start listening to any mobile user in a few clicks.
By law, several special services have the right to wiretap. In addition to the FSB itself, these are the Ministry of Internal Affairs, FSKN, GUFSIN, customs, FSO, and SVR. But the control over the equipment itself, which ensures the operation of SORM-1 and SORM-2, lies with the FSB. As experts explain, in order to put this or that number on the wiretap, it is not necessary for employees from the police bureau of special technical events to flee to the FSB and ask to press a button: the Ministry of Internal Affairs and other agencies conducting operational-search activities have their own access terminals. But they are connected “through the FSB”, that is, the main key is still located at the KGB.
“Therefore, for example, in the case of Roizman’s wiretaps, it will be difficult to transfer all the arrows to the police and pretend that the FSB has nothing to do with it,” the source said. According to him, the responsibility for unauthorized wiretapping and its leak in any case lies with two departments.
“Why do you need so many phones?”
How to protect yourself from wiretapping? Almost nothing. Firstly, it is useless to change SIM cards: they’re not listening to a mobile number, but to a unique telephone number (IMEI). Whatever SIM card is installed on the phone, it will still be “live”.
Many representatives of the establishment and businessmen carry several telephones with them, believing that one is “normal” and others are “left” - .. - If a person is put on wiretap, government officials constantly receive information about the location of his phone. To do this, the phone does not have to have a GPS module installed, the location of even the simplest and cheapest handset is determined by base stations with an accuracy of one meter. And if you carry several tubes with you, according to geolocation data, it can be seen that there are always 2-3 others next to your “main” number. They are also immediately tapped, so walking with a bunch of phones is completely pointless. ”

However, there is a small trick with two handsets, which allows you to relatively reliably keep the secret of negotiations. “Suppose there are two devices - A and B. A is used constantly, and there is reason to believe that they are listening to it. B - for confidential conversations, registered to another person. In this case, A and B should never be turned on simultaneously and side by side. If you need to make a call on the "secret" telephone B, you turn off A, drive away, into the coverage area of \u200b\u200banother base station, then turn on B, make a call. Then turn off B, again go to another base station and then turn on A, ”says our interlocutor. Another way is to constantly store the "secret" phone in some hidden place, each time coming to him with the "main" mobile phone turned off.
Particularly cautious victims of wiretaps prefer to turn off the phone during an important conversation or hide it to hell. The interlocutor of the site confirms that the possibility of recording via the phone in standby mode exists, but such technology is rarely used. “In these cases, the so-called microphone effect. This can be done only if a team of specialists works in the immediate vicinity of the interlocutors. The signal receiver and recorder should be somewhere nearby, ”he explains.
How does it work
Another thing is ordinary wiretapping. It can be massive. Today in Yekaterinburg, FSB capacities allow listening to 25-50 thousand subscribers at the same time, in Moscow - hundreds of times more. The main problem is not how to record information, but how to decrypt and process it. For example, the State Department of the Ministry of Internal Affairs in the Sverdlovsk Region has a special department of “analysts” who are busy simply decrypting recorded conversations, turning audio into text. Now Sverdlovsk law enforcement officers, using the preparation for the 2018 World Cup and EXPO 2020 as an excuse, set themselves the task of increasing the wiretapping hardware capacities. And to create more advanced systems for processing the information received is already a task for security officials not only at the Russian, but also at the global level. Recent scandals in the United States show that Russian intelligence agencies are far from the only ones involved in illegal or semi-legal "monitoring."

The world leader in creating data analysis and processing systems for special services is the American company Palantir Technologies. According to the site's interlocutor, Palantir technologies are used by both American government organizations, such as the CIA, and Russian ones, including the FSB and the information and analytical center of the Russian government. “The latter hardly fits into the head. It turns out that the entire amount of government information, including classified information, goes through the American system ..
In Russia, Avicomp Services is also one of the largest suppliers of “analytical” software for special services. And hardware solutions and programs for "monitoring" (that is, wiretapping) are actively sold by the Novosibirsk company Signatek. Her site says that she offers “subjects of operational investigative activities” “systems for monitoring communications of objects: telephone conversations, facsimile sessions, video calls, SMS, DVO, ICQ, e-mail messages”, as well as “Monitoring systems for moving objects with visualization on map. "
The product catalog contains examples of how the program interface for “monitoring” looks:

What’sApp or Viber?
With the analysis of the Internet traffic of suspicious citizens (SORM-2), security officials are doing somewhat worse than with wiretapping conversations. Although telecom operators provide any information to the special services in the same way, the analysis of this data itself is rather complicated. “Any smartphone constantly downloads and sends a huge amount of data. Until recently, there was a huge problem in extracting interesting information from all this mass, for example, correspondence in Skype or WhatsApp. However, now this problem has been generally resolved, and even in the regions they learned to read Internet instant messengers, ”says our interlocutor.
He calls the popular What’s App an extremely unsafe messenger - the transmitted information is not encrypted in it. Skype has such encryption, and it would be reliable if the service owners, having entered the domestic market, did not share decryption codes with the Russian security forces. Therefore, today Viber communication can be considered the most reliable, in which all data (both correspondence and voice calls) are encrypted and are not yet available for domestic special services (“This is why Viber is first of all trying to ban,” our interlocutor is sure). The source does not trust the Telegram service claimed to be a “super-reliable” messenger service “Telegram”, “like everything that has been done in Russia, including Pavel Durov”.

Another relatively reliable way to chat is to use BlackBerry phones, which have their own BlackBerry Messenger messaging service. The data in it is encrypted even more reliable than in Viber, the Russian security forces do not have access to it, and that is probably why BBM is prohibited in Russia. To use it, you have to buy a phone in the USA and “unlock” it from Russian specialists.
A major developer of programs and equipment for SORM-2 in Russia is the MFISOFT company, which supplies software for the FSB. The description of the SORMovich hardware and software complex on their website says that it can put users in control by account name, phone number, email address, IP and ICQ number. The complex provides “detection and interception of mail messages by e-mail address”, “interception of files transmitted via FTP”, “listening to IP-telephony”, etc.
Who is being watched
Maybe the security officials would like to “listen to everyone,” but in reality, under the constant supervision of only 200-300 people in Yekaterinburg, the site’s source said. Most of them are suspects of extremism (primarily of the Islamist type) and terrorism, members of the organized criminal group, participants in large-scale non-transparent financial transactions (“cash-outs”, etc.) ..

“They definitely listen to the governor, his closest associates, the top officials of the city. Deputies of the Legislative Assembly and the City Duma are unlikely, only if someone was ordered by competitors. But this is a rare case, no one has said anything important for a long time on the phone, and not many are ready to spend 70 thousand rubles a day on wiretapping a competitor, ”says our source.
Recently, there has been another proven way to become a victim of wiretapping - regularly criticize the current government or go to protest demonstrations. Of course, they will not listen to all the participants in the street rallies, but they are quite the most active. In Yekaterinburg, Yevgeny Roizman and Aksana Panova have long been listened to as opponents of the Sverdlovsk governor Yevgeny Kuyvashev. Surrounded by the governor, they do not hide the fact that printouts of their conversations regularly lay on the table to the head of the region.
FSBuk
Recently, an analysis of the information collected on social networks has been playing an increasingly significant role in the SORM structure. With Facebook, things are more complicated, but here the secret of communication is not guaranteed. “A relatively safe way of communication is through Western mail services: Gmail, Hotmail, Yahoo,” the site’s source said. - The Tor network is still effective, guaranteeing anonymity to users. With its help, including, American journalists communicate with their informants. "
To exchange information, more and more people and organizations use cloud services like Dropbox, Yandex.Disk, Google disk and others. They are also interested in law enforcement. Of the popular services, Google’s proposal is considered to be relatively reliable, but our source advises paying attention to Wuala: a storage that supports encryption with servers in Switzerland. True, if you are saving your secrets not from the Russian special services, but from the American ones, hardly anything will help you. A few days ago, another “ultra-secure” Lavabit cloud service was mysteriously closed and all its users lost their information. Apparently, the fact is that former CIA agent Edward Snowden used Lavabit mail.
Under the hood
A rare Russian businessman and politician today discusses on the phone something more important than fishing and football. Therefore, in addition to analyzing the actual negotiation texts, electronic intelligence professionals are engaged in processing large amounts of data, identifying mathematical patterns, implicit relationships, building on this basis hypotheses about the interaction of certain groups or persons. The material for this can be telephone calls, emails, banking, registration or liquidation of legal entities, etc. It turns out large schemes, similar to the one given in one of the presentations of the already mentioned Avicomp company:

The monitoring of electronic correspondence, the monitoring of telephone conversations went as far as the authors of anti-utopian novels did not even dream of. Probably, often the power of SORM helps prevent genuine terrorist attacks or real crimes. But it’s much more noticeable for society when electronic intelligence methods are used for political persecution and have nothing to do with legal procedures. At the same time, not only oppositionists suffer from uncontrolled surveillance, but also politicians loyal to the Kremlin. Electronic evidence collected by electronic means often becomes an instrument of the elite struggle against those who had recently ordered wiretapping of their enemies. In this sense, electronic intelligence has become a danger from which no one is safe.
Our reference: How Ural politicians suffer from surveillance and try to escape
Everyone suffers from illegal wiretapping. Aleksey Tabalov, director of the Legal Mission Civic Initiatives Support Fund (Chelyabinsk), told the site that “he was listening to all his phone calls” and he was convinced of this more than once. The chairman of the board of the Golos-Ural foundation, Yuri Gurman, also assured us that in his organization, special services listen to phones and look through correspondence to e-mail. “I know that they are listening, and let them listen. Although it’s getting nasty, ”he says.
The deputy of the Legislative Assembly of the Perm Territory Vladimir Nelyubin told the site that it is now customary to take the phone to the secretary at the entrance to some high offices. The banker himself uses the classic Nokia, does not recognize modern messengers and is not going to defend himself against wiretapping. And the former head of the administration of the governor of Prikamye, Firdus Aliyev, is convinced that it is impossible to defend oneself from wiretapping. “Such measures do not exist, this is an illusion. Only personal communication can eliminate leaks to the maximum, so you have to fly [in meetings], ”he said.
In the "Tyumen Matryoshka" only in the South, in Tyumen, they accustomed themselves to messengers like Viber and WhatsApp: in Khanty-Mansi Autonomous Okrug and Yamalo-Nenets Autonomous Okrug 3G coverage is much worse and it is unprofitable to use them. But northern officials are actively using hardware against wiretapping. For example, in the office of one of the senior officials behind the curtain is a “jammer”, which he turns on during important conversations. They say that the sound of this device is creepy, so it’s physically hard to speak for a long time when it works.
The same manager tells absolutely fantastic stories about mobile communications. According to him, today the KGB officers have equipment that once having recorded the timbre of your voice, in case they need to write you in the future, it will automatically turn on, no matter what telephone you speak. Therefore, changing numbers and devices does not make sense. The official is quite suspicious of Apple products, although she has been using it since Dmitry Medvedev became the president, who introduced fashion among public servants on the iPhone and iPad. However, he sealed the black lens with camera lenses on both gadgets. The official is confident that with the help of cameras, the owner of the devices can be monitored.
One of the governors of the "Tyumen Matryoshka" was watched without any iPhones. The video camera was discovered right above the first-person bed in the office building. Who has been the customer of the surveillance (FSB or private individuals) has still not been found out.
In the Tyumen North, in order not to become a “find for spies,” they used the old grandfather methods a few years ago - they liked to change mobile phones and SIM cards there. One of the leaders of a large company told the site that there was a place near the shore of the Irtysh in Khanty-Mansiysk, passing over which the boat could run aground, so many phones were recessed there.
The most sophisticated officials and businessmen will always prefer private conversations over telephone conversations. Moreover, as one of them admitted, the most reliable way of communication is to write on a sheet, after which this sheet is simply burned.