So, we will try to hide from the user's eyes in the Windows Task Manager. The way in which we will achieve this is extremely simple with respect to those based on the interception of nuclear (often undocumented) functions and on creating our own drivers.
The essence of the method: Search for the Task Manager window -\u003e Search for a child window (list) in it containing the names of all processes -\u003e Delete our process from the list.
As you can see, no manipulations will be carried out with our process: it worked as it did and will work for itself. As a standard ordinary Windows user, as a rule, does not use any other tools to view the running processes on his computer, this will only play into our hands. The process will not be detected in most cases.
What was used for research:
1) Spy ++ from Microsoft (to study the hierarchy of child windows Task Manager)
2) OllyDBG to view the functions used by the dispatcher to get a snapshot of processes.
3) Actually, myself taskmng.exe(Task Manager)
For writing code, we will use the Delphi environment. Rather, Delphi will be more convenient in our case than C ++. But this is only my humble opinion.
Well, first of all we will try to find out what the list of processes is and how it works. From a half-view, it is clear that this is a regular window of the class “SysListView32” (list), which is updated at a frequency of 2 frames per second (every 0.5 seconds). We look at the hierarchy of windows:
As you can see, the list of processes, in fact, is the usual window of the class “SysListView32”, which is a child of the “Processes” window (tab), which is also a child of the main window of the Task Manager. We have only a double level of nesting. In addition, the list has one child window of the “SysHeader32” class, which, as it is not difficult to guess, is a header (field marker) for the list of processes.
Since we have a regular list, we have a whole set of macros at our disposal to manage its contents. Their diversity, at first glance, delights. But many of them work only from the parent process, that is, in order for us to use them, it will be necessary to imitate, as if they are executed in the parent process. But not everyone has such a property, in particular, the ListView_DeleteItem macro command, which deletes an item from the list window (class “SysListView32”).
We will use it in the process. of our applications. This function is the second parameter gets the index of the item to be deleted.
Now we need to somehow figure out what kind of index the element has with the label of the hidden process in the task manager. To do this, we need to somehow pull out all the elements (labels with process names) from the list of processes in the task manager and consistently compare them with the name of the process that we want to hide.
Using macro commands of the ListView_GetItemText type, our actions would be approximately as follows:
1) The allocation of memory in the task manager process (VirtualAllocEx)
2) Sending the Task Manager child window a message LVM_GETITEMTEXT (SendMessage)
3) Write to the selected memory area of the Task Manager information about the item in the list (WriteProcessMemory)
4) Reading from the memory of the dispatcher that information that interests us about the process (ReadProcessMemory)
Using this method, you can easily "shoot yourself in the foot" by counting the offset bytes from the beginning of the various structures used in the code. Also, this method will be quite difficult for those who are not very deep in WinAPI, so we immediately remove it to the side. In other matters, to find the implementation of this method on the Internet will not be difficult. Instead, I will suggest that you form your own list of processes, and already focusing on it, look for the cherished process index in the Task Manager process list.
Microsoft decided not to worry about the tool called Task Manager, and used the usual WinAPI functions to get all the processes in the system. Superficially look taskmng.exe under the debugger:
We see the use of WinAPI functions CreateToolHelp32SnapShot.
Everyone knows that “this function can be used not only to obtain a snapshot of processes, but also process flows or modules, for example. But in this case it is unlikely. It is unlikely that they will use something like the process enumerator (EnumProcesses).
We stopped at the fact that we want to create our own list of processes and look for our process in it. To do this, use the function found in the debugger. If we open the task manager on the “Processes” tab, we note that all processes are sorted alphabetically for easy retrieval. Therefore, we need to get a list of names of all processes in the system. and sort them by increasing alphabetically. Let's start writing code in Delphi.
To begin with, we will create a demo window application with two timers: the first will reshape the list with processes with the same frequency as the Windows Task Manager does (every two seconds); the second will trigger 1000 times per second and will serve to track the update of the list of processes in the manager and, therefore, the appearance of our hidden process. Also add a button to the form.
Code:
var ind integer; h: Thandle; last_c: integer; procedure UpdateList (); var th: THandle; entry: PROCESSENTRY32; b: boolean; i, new_ind: integer; plist: TStringList; begin // Process list plist: = TStringList.Create; // Create a list of processes th: = CreateToolHelp32SnapShot (TH32CS_SNAPPROCESS, 0); entry.dwSize: = sizeof (PROCESSENTRY32); b: = Process32First (th, entry); while (b) do begin plist.Add (entry.szExeFile); b: = Process32Next (th, entry); end; // Sort it so that the indexes of the elements // are the same as those in the task manager plist.Sort; last_c: = plist.Count; // Search the index of our process "explorer.exe" for i: = 1 to plist.Count-1 do if (LowerCase (plist [i]) = "explorer.exe") then new_ind: = i-1; // Remove an object from the list if (new_ind<>ind) then ListView_DeleteItem (h, ind); ind: = new_ind; plist.Free; // Start the update tracking timer in the process list if (Form1.Timer2.Enabled = false) then Form1.Timer2.Enabled: = true; end; procedure TForm1.HideProcessButton (Sender: TObject); begin // Looking for a child window of the class "SysListView32" h: = FindWindow (nil, "Windows Task Manager"); h: = FindWindowEx (h, 0, nil, "Processes"); h: = FindWindowEx (h, 0, "SysListView32", nil); // Start the process list re-formation timer Timer1.Enabled: = true; end; procedure TForm1.Timer1Timer (Sender: TObject); begin UpdateList (); end; procedure TForm1.Timer2Timer (Sender: TObject); begin // Search for changes in the list if (ListView_GetItemCount (h)\u003e last_c) then ListView_DeleteItem (h, ind); last_c: = ListView_GetItemCount (h); end;That's the whole code.
We hide, for example, in the Task Manager the process of the Task Manager itself:
Here it is:
And by clicking on the "Hide process" button, the process disappears from the list:

All traces of presence in the system are erased, and he calmly runs as usual somewhere in the depths of the processor :)
Outro
Well, I think this way deserves to exist, though it requires minor improvements. Yes, of course, it cannot be used to hide the process from the system itself, but hiding in the standard Windows tool, which is used by the lion’s share of all users, is not bad either.I hope I managed to interest you at least a little bit with this topic.
See you later! And may the power of anonymity be with you ...
Tags:
The spy hides his location, hides his process and hides his service in the system. But that's not all surprises. He knows how to defend himself by blocking all possible ways to complete his processes and delete files. Spyware does it in case you find them. However, simple ways to detect the presence of a spy in the system is impossible. For this reason, many users lose their personal information without even knowing it.
In order to find out whether you are being monitored using this spy or not, it is useless to view standard monitors, trying to search for it manually or by scanning the system. When testing, antiviruses do not detect spyware, so the user gets the impression that everything is in order.
To detect surveillance, go to the "System Processes" monitor. Then open the “Hidden Processes Monitor” by clicking on the “Hidden Processes” button. In the opened window, the processes that hide themselves from the system are highlighted in red.

All In One Keylogger is detected. Add the process name to the threat database via the program context menu. In different test systems, the spy had different names of processes and files. When you try to complete a hidden process, you will receive an error message. You can get into the folder with the spy application through the item in the context menu, it will not work in another way. Using the uninstaller will not work either - the spy protects itself from being deleted, which means that there are other processes in the system that control the situation with the spy’s work. Open “Hidden Services Monitor” (only in Pro versions) in the “System Services” window. Any service hiding itself from the system will be highlighted in red. In the standard version of the list of system services, this surveillance cannot be identified.
Hidden service from spy All In One Keylogger is also detected. This service and process protect themselves and do not allow to stop. Add it to the threat database via the context menu. The first task is completed - shadowing is revealed. Now you know for sure that you are under surveillance.
To remove the All In One Keylogger spy, enter the COVERT security platform by clicking on the button that says: “Log into the security platform”.
In the “System Processes” window you will see the processes highlighted in red. Through the context menu, complete them. In the defense platform, the spy cannot hide and protect itself.

Next, open the “System Services” window. In the standard list “Active services”, via the context menu, stop and delete the service highlighted in red (or in the list “All services” it can be highlighted in yellow). In the platform of protection, the spy cannot hide and protect itself.

After the actions performed, exit the protection platform and delete the spy folder with the files. It will not be hidden and protected.
If you have installed COVERT Base or COVERT USB, which do not have the “Hidden Services Monitor” function, go to the COVERT protection platform and work with any applications to disguise your actions from the All In One Keylogger spy. Spyware will not be able to get data about your activity while you are inside the platform of any version of the COVERT program.
Material from the site
This article describes the methods and methods for extracting hidden files (rootkits, drivers) using the undocumented features of the Dr.Web® anti-virus scanner and additional third-party utilities.
Dr.Web Scanner
If you know the name of the driver in the current session, then you can copy it to quarantine using a scanner and send it to the virus lab.
- Create a text file in the Drweb anti-virus directory, for example
If you have version 5.0 or higher installed, the creation of the filelist.txt file in the anti-virus directory will be blocked by self-defense. In this case, create the file filelist.txt in another directory (see example).
- Write the full path to the rootkit driver file, for example
Lines in one file can be many.
- Run the scanner with the parameters:
For example: I have an antivirus installed in the C: \\ Program Files \\ DrWeb directory, and I created a text file in the root of the C: \\ filelist.txt drive
"C: \\ Program Files \\ DrWeb \\ drweb32w.exe" /copy:C:\\filelist.txt
Attention! Quotes are required in this case!
- Or if you use CureIT, then
After that, if such a driver exists on a disk, it is in quarantine in the C: \\ Program Files \\ DrWeb \\ Infected folder. !!! (or in the% USERPROFILE% \\ DoctorWeb \\ Quarantine \\ folder for KureIta) there will be a file.sys.sys.dwq. Now we archive it and send to virlab.
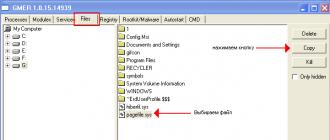
Gmer
- On the Rootkit / Malware tab, click the Scan button. We will wait until the program collects all the data. After you need to click the mouse on the tab "\u003e\u003e\u003e\u003e
- Right-click on the required module and select "Copy" through the context menu.
- If the "Copy" menu is not active, then select "dump module"
- On the tab "Processes" we look at the necessary process and in the field "Command" enter the command cmd.exe / c copy
For example:
Cmd.exe / c copy c: \\ drweb \\ spidernt.exe c: \\ spidernt.exe
In this case, we will get on disk C: the executable file of the spidernt.exe process
If none of these methods helped, then you can try to find the file.
- It is necessary to click the mouse on the tab "\u003e\u003e\u003e\u003e" in order to open the hidden tabs.
- Go to the "Files" tab
- We are looking for a file like in Explorer, select it.
- Press the "Copy" button. Save the file to the directory you need.

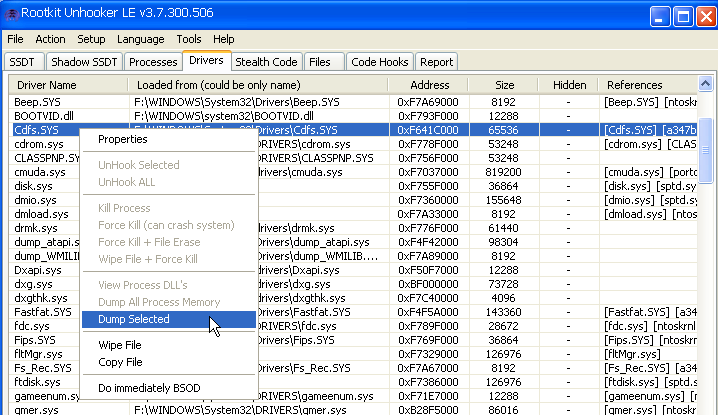
Rku
- Select the "Drivers" tab and select "Copy" through the context menu.
- If you can not copy - make a dump. To do this, select the command "Dump Selected" via the context menu.
Rootrepeal
- Select the "Process" tab and click the "Scan" button
- Right click on the suspicious process and select the menu item "Copy file ..."
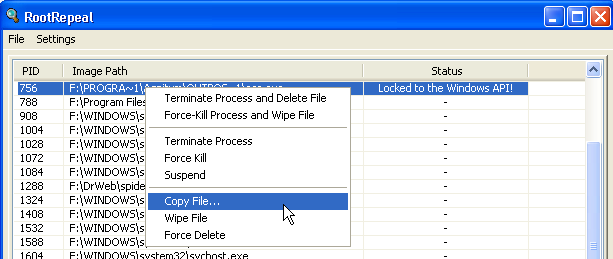
Delayed deletion using
Sometimes a situation arises when it is necessary to delete a file (trojan), but this does not work with standard tools from Explorer. To do this, use HJ. After launching HJ, click on the "Open the Misc Tools section" button and then click on the "Delete a file on reboot ..." button. A file selection dialog box will appear (if the file is not visible, you can select the folder where it is located and manually enter the file name and extension ... or use the recommendations
All modern multitasking operating systems, including Linux, run several processes to perform each of the tasks. Using notepad, terminal window, SSH server, SSH connection and so on are all separate processes. The operating system, in our case Linux distributes system resources (CPU time, memory, I / O), between processes, so that each process can work.
To view a list of currently running processes, use the ps utility:
The aux parameters indicate to the utility that it is necessary to output all system processes with information about the user from which they were started and the call command.
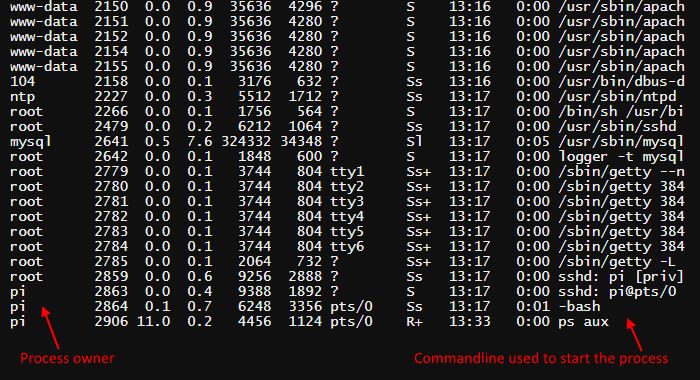
As you can see, the list contains processes belonging to various users, including pi - the default user in Raspberry Pi, root and www-data. Here is another screenshot that shows the processes and information about their startup command and parameters:
If you look to the bottom of the list, you will see the nano command MYBANKACCOUNTNUMBER.TXT executed by user john. This data is provided to all users of the system and can be used for malicious purposes.
In the kernel version 3.2 and above, the function of prohibiting the user from viewing information about processes that do not belong to him is implemented. The ps command retrieves process information from the / proc file system. A new parameter, hidepid, has been added which is used when mounting the file system. It allows you to hide information about processes from users who do not have access to them.
- hidepid = 0 is the default value, all users can read the / proc / pid files
- hidepid = 1 - users can only access their own / proc / pid subdirectory, but the cmdline, io, sched *, status files are available to everyone
- hidepid = 2 - all / proc / pid subdirectories are hidden from users
The / proc file system can be remounted on the fly using the mount option of the mount utility. To test hidepid, you can use the following command:
sudo mount -o remount, rw, hidepid = 2 / proc
Then try to run ps again:
Now we will see only processes running from user pi.
To make these changes permanent you need to edit the / etc / fstab file. This file controls the mounting of file systems at startup.
sudo nano / etc / fstab
Find this line:
proc / proc proc defaults 0 0
And replace it with:
proc / proc proc defaults, hidepid = 2 0 0
Close the editor with the keyboard shortcut Ctrl + C and restart your computer. After reboot, / proc will be mounted with the correct options. To check mount options, use the mount and grep commands.
mount | grep hidepid
Now try to run ps:
As you can see, only the processes belonging to the current user are visible. But there is one remark. The superuser can still see all call processes and parameters.
One way to detect viruses on a PC is to view running processes in the Task Manager. Anti-virus programs do not always cope 100% with the tasks assigned to them. Sometimes you have to catch viruses manually.
Many viruses hide their presence in the Task Manager - they are invisible. In this case, alternative task managers come to the rescue. Any of them can be downloaded online and enjoy. Built-in Windows, its own Task Manager is uninformative and does not show hidden processes. Third-party, similar utilities are deprived of this disadvantage and show hidden processes. If there are no processes in the standard dispatcher that appear in the analysis window of an alternative utility, then you need to pay careful attention to these processes, perhaps this is malicious applications. It is necessary to look at the manufacturer of the process, usually it is always clearly and clearly indicated, and also how much resources this process consumes. If a lot, compared with others, then it is extremely suspicious.
Such an inspection should be done when the applications are turned off, so that the standard processes and viruses remain, of course. Best done in Safe mode. Very good, when you just installed Windows, take a snapshot of the Task Manager page with standard processes to be able to compare the differences. The snapshot is due to the saved file with the screen, and not the snapshot by the camera (done by pressing the Print Screen button on the keyboard, who does not know how to do it, ask in the comments).
So, consider the standard processes:
- Sistem - system processes no extension exe.If such a process you have with the extension - this virus is disguised as a system process.
- Smss.exe -process managing the launch of user accounts. If you have enabled, at the moment one session account, and processes Smss.exe more - draw the appropriate conclusions.
- Csrss .exe. - the process governing the creation of windows, it must be, always one.
- Winlogon.exe. - is responsible for the authoritarian user login. Only one.
- Services.exe. - provides the operating system services, runs on behalf of the System, also one.
- Lsass.exe - ensures the safety of the OS, always one.
- Svchost.exe. - run Dll-files (dynamically connected library, this includes drivers, ActiveX controls) user name: LOCAL SERVICE, NETWORK SERVICE and SYSTEM, should be a maximum of six.
- SYSTEM - is responsible for the keyboard layout and language bar on the taskbar. Must be one.
- Explorer.exe. - manages the desktop (labels, icons, etc.), its interface. Runs once.
- Spoolsv.exe. - puts objects in the print queue. One. No printer - and you can turn off the process is not critical.
- Wdfmgr .exe. - is responsible for the correct operation of the media player driver, is also not a critical process.
- Taskmgr.exe. - Task Manager itself
- Well, the latest - Idle system. Shows free resources.
In normal mode, in addition to these processes, you will have the processes of running applications and drivers. To disable a suspicious process, select it and click Stop Process.
This is one of the ways that is safer than, let's say, experimenting with the system registry.