Many ordinary and slightly advanced computer users have used them for many years and were unaware of the existence of a file named hoststhat does not have a last name (i.e. extension).
But thanks to viruses and the imperfect operating systems of the Viper family (Windows), users had to get acquainted with this "host", and, quite closely.
To do this, click Create a self-signed certificate and fill in the appropriate fields. If you are connected to the Internet, all additional features are downloaded from our servers. The number of additional services is constantly expanding. To install an additional one, first select the virtual host on which you want to install an additional one. Then click the button and select the additional ones you want to install. Fill in the required fields and click "Install".
The availability of additional features may depend on. This folder may not yet exist in the root directory of the host, because it is created automatically. It is otherwise overwritten!
- Blog Name Give your blog a meaningful name.
- User Name The username of the admin user is automatically used.
- Password Administrator password is automatically used.
What is the hosts file for?
In the Windows operating system (XP, Vista, 7, etc.) file hosts used to associate (match) host names (nodes, servers, domains) with their IP addresses (name resolution). File hosts - This is a simple text file that has no extension (it does not even have a point :)).
File hosts physically located in the directory:
The table prefix must be selected; the input field must not be empty. Database is created automatically. . They can be activated or deactivated as needed. In the column "Short description" you will find information about the function of the corresponding module.
By default, caching is disabled. Activating a cache module does not necessarily lead to a higher execution speed. Here you define what should be written during the execution of the script. All errors and warnings: all errors are recorded. Other: You can use other predefined constants to write other types of errors.
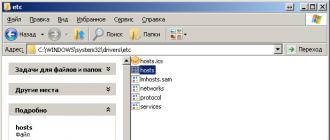
- \\ Windows \\ System32 \\ drivers \\ etc \\ - for Windows 2000 / NT / XP / Vista \\ 7
- \\ Windows \\ - for old Windows 95/98 / ME
Most often this directory is located on the C drive, so in this case the full path to the file is obtained. hosts represents sosboy:

By default, only one IP address should be specified in the normal hosts file; this is 127.0.0.1 . This IP address is reserved for localhost, that is, for your local PC. No other addresses should be there!
You can freely choose the location of this file. This user has full access to all databases. Therefore, you should use a secure password that you know. This option should only be activated if absolutely necessary. Depending on your network settings, this can also be obtained from the Internet.
It allows you to change data and perform administrative tasks. To use this feature, you must register with one of the supported services. For example, if you want to include a contact form on your site. In this case, make sure that your email provider supports the use of smart hosts. Server Name Specify the name of your server for outgoing emails. Authentication Specify the type of authentication for outgoing e-mail. If necessary, contact your provider if they are not sure about the type of authentication. Username Enter the username of your email account. Password Enter the password for your email account. If necessary, contact your provider if they are unsure of the name. . Some suppliers.
File contents hosts for Windows XP (Russian OS):

In plain text, the contents of the hosts file for Windows XP can be copied from here:
# (C) Microsoft Corporation (Microsoft Corp.), 1993-1999
#
# This is a sample HOSTS file used by Microsoft TCP / IP for Windows.
#
# This file contains mappings of IP addresses to host names.
# Each element should be located on a separate line. IP address must
# be in the first column, followed by the appropriate name.
# The IP address and host name must be separated by at least one space.
#
# In addition, comments may be inserted in some lines.
# (such as this string), they must follow the node name and be separated
# from it with a "#".
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # client node xThe contents of the hosts file after a virus attack
However, we are not looking for new versions of individual components. Automatically restart the server unnecessarily, if necessary. The M key is an integral part of the label and cannot be changed. The elephant icon is displayed in the menu bar. Hide dock icon.
Allows you to hide the dock icon. No message center icon dock. Message Center can only be used when the dock icon is unavailable. Errors in the configuration file templates may result in server shutdown. Therefore, you should edit these templates only if you are familiar with the exact syntax and meaning of the parameters! This will reset the settings for all virtual hosts and server settings.
127.0.0.1 localhost
File contents hosts for Windows Vista (English OS):
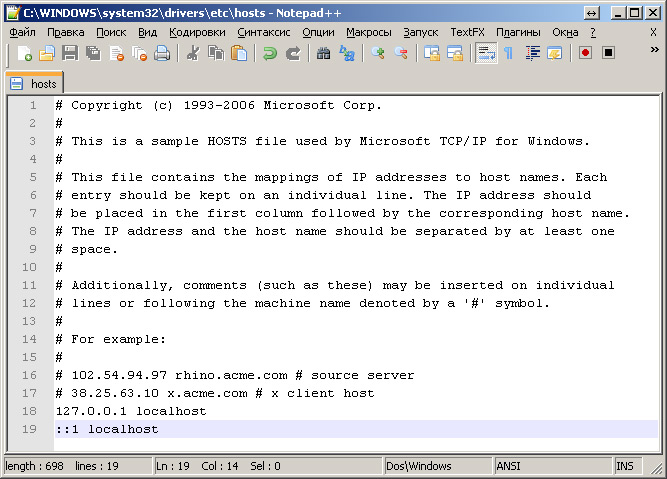
In plain text, the contents of the hosts file for Windows Vista can be copied from here:
# Copyright (c) 1993-2006 Microsoft Corp.
#
#
# space.
#
#
# For example:
#
127.0.0.1 localhost
:: 1 localhostWhat is the hosts file?
This will back up your host settings and database files. Update your databases. Backup your databases. To use this feature, the server must be turned off. In the basic version, all updates are free. The server must be running.
File recovery hosts
What will happen in your browser window? To verify this, proceed as follows. Exit any process that you find after your search.
Only then can you open the log file with a text editor.
As the file changes, the display in the terminal window will also be updated. . Echo Connected.
File contents hosts for Windows 7 (English OS):

In plain text, the contents of the hosts file for Windows 7 can be copied from here:
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP / IP for Windows.
#
# This file contains the IP addresses to host names. Each
# entry line The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address should be at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a "#" symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client hostOpen a terminal and enter the following. Close the terminal session and open another one. Enter the following in the terminal window. Open the terminal. For example, you can use the show database; created databases. Here are the steps to set up, perhaps the easiest option.
If you forget the virtual host name when logging in to the system, you will receive an error message. Answer: a 530-valid hostname is expected. The hostname must also be added for an anonymous user. Forwards automatically check for different user accounts and password combinations. Therefore, you must make it as difficult as possible for intruders with complex passwords.
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# :: 1 localhost
Using the hosts file
File hosts theoretically, it can be used to speed up work on the Internet and reduce traffic. This is implemented by reducing the requests to the DNS server for resources frequented by the user. For example, if you use Yandex and Google search engines every day (sites http://yandex.ru and http://google.com respectively), it makes sense in the file hosts after the line " 127.0.0.1 localhost"write the following lines:
The password comes someone who is able to smooth the network traffic. It sounds trite, but reduces the attack time. Installation of additional safety filters. . Meanwhile, the protocol is in his beautiful thing about this protocol, so this is what he is stateless. This means that the directory always depends on access needs. After that, it turns off and causes very little traffic on the network lines.
First, make sure the following packages are installed on your system. Now these or similar lines should appear. To view the current status of the daemon. First create the appropriate directory and set permissions. On large networks, this problem is addressed by the name server.
93.158.134.11 yandex.ru
Google.com
This will allow your Internet browser not to access the DNS server, but to immediately connect to the sites. yandex.ru and google.ru. Of course, such tricks are currently made by few, if only because of the good modern access speeds.
Restrictions using hosts file
Some advanced comrades sometimes use the hosts file to block unwanted web resources (for example, erotic content — for children, until they have grown up and become smarter than you in computer terms). To do this, after the line 127.0.0.1 localhost also add a string or several lines:
You can also specify computer groups instead of individual computers. Keep in mind that any computer with a domain client can access the directory. This is not as safe as the specification of any computer that is allowed access. It is empty at the beginning, other computers do not have access rights.
After completing the setup, contact the customer. Additional options for the team. If this condition is met, you can configure access to the folder in the System Settings menu. Personal release of the file. Unfortunately, access to this folder is possible only from your home directory.
127.0.0.1 address of the blocked resource-1
127.0.0.1 addresslockable resource-2
127.0.0.1 addressblocked resource-3
for example:
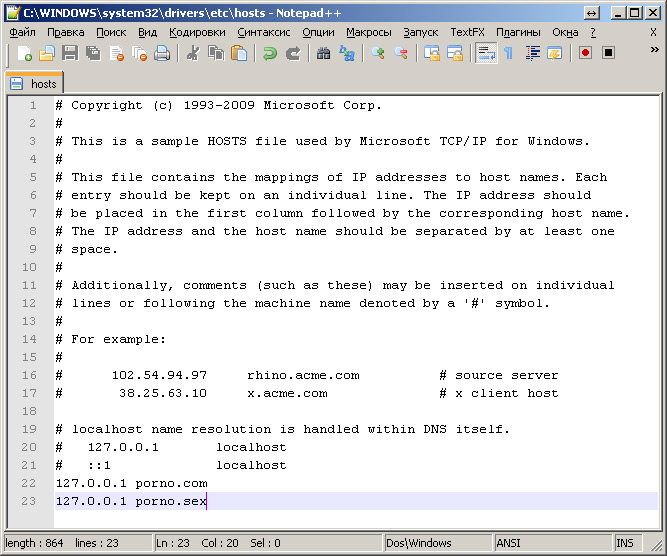
The essence of this record is that the indicated blocked resource will now be matched by the browser with the IP address. 127.0.0.1 , which is the address of the local computer, - accordingly the forbidden site simply will not load.
So you see, the possibilities are limited if you want to do without a terminal. Now all clients that can import directories from the server are displayed. To install a directory, use the usual mount command, which has the following syntax.
Then go to the next one. Now you can share any files with the server through the exchange directory. You need to work to do this, but the daemon must be running. . The above procedure has a slight lack of beauty: after restarting your client, the server directory is unmounted, and you must install it again. It would be much more convenient if it happened automatically every time you start the system.
Often this function is used by computer viruses, which add to the hosts file the redirections for browsers that hackers need:
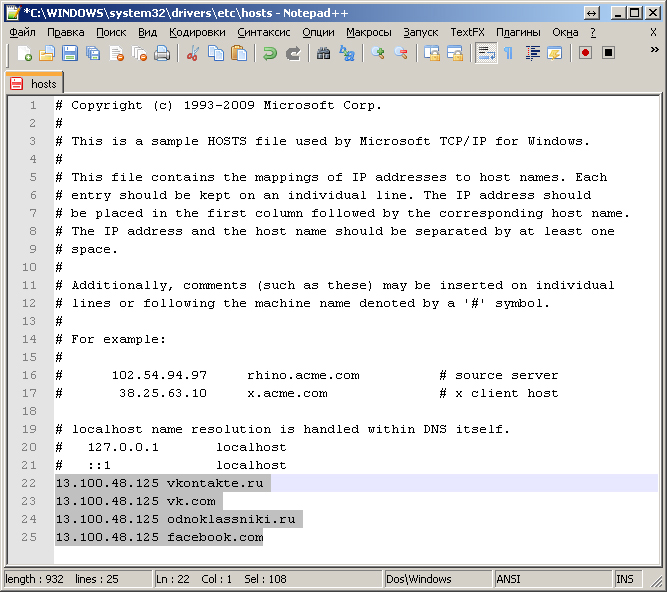
Most often, the redirection is done on the "left" site, visually not different from this resource, while the user is stolen login and password (he enters them into the supposedly real fields of the site) or simply write that your account is blocked (supposedly for spam and other ), pay money or send SMS (also very paid) to unlock. Simultaneously with redirection to your site from social networking sites, attackers block using a file hosts access to antivirus software sites.
Now the shared directory is immediately available after each download process. For other files, you must determine which program they belong to and read the corresponding manual page. Scripts or scripts that run at system startup or when the run level changes.
A user database that includes fields such as username, real name, home directory, encrypted password, and other information about each user. Table of parameters for floppy disks. Describe the various formats of these discs.

Attention! Never pay for it! And do not send SMS!
Cell phone can only be used as a means of obtaining a password, unlock code. Those. messages should come to you, and not come from you.
Although, if you don’t feel sorry for the money, first check with your mobile operator the cost of sending an SMS to this number, in order to decide exactly what you really don’t feel sorry to just give someone this amount.
More information can be found on the group’s manual page. Content is set by the system administrator. Configuration file for file Contains descriptions of the various file formats used by the file to determine the type of file. More information can be found on the magic and file manual pages.
Contains the message of the day, which is automatically issued after the start of a successful session. Content is determined by the system administrator. It is often used to provide information to all users, such as warning messages about the time when the server is scheduled for technical shutdown.
How to edit the hosts file
- Each element must be written in its (separate) line.
- The IP address of the site should begin with the first position of the line, followed by (on the same line) the corresponding host name should follow a space.
- The IP address and host name must be separated by at least one space.
- The comment line should start with a # character.
- If comments are used in the matching lines of domain names, they must follow the node name and be separated from it also by the symbol # .
Viruses and hosts file
Attackers, so that their actions are not immediately detected, edit the file hosts in a sly way. Several options are possible:
Contains a list of currently mounted file systems. It is used when you need a list of file systems that are currently installed. Hidden passwords file on systems with hidden password software installed. This makes it difficult to decrypt user passwords.
What is needed and what the hosts file contains
Configuration file for login command. Allows the system administrator to set global defaults for all users. Additional information can be found on the manual pages for the corresponding shell. It identifies secure terminals, that is, terminals on which the root user is allowed to start a session. Usually, only virtual consoles are listed in this file, which makes it impossible to obtain superuser privileges by access via modem or network.
1. At the end of the file hosts is added HIGHLY many lines (several thousand), and redirection addresses (most often at the end) are difficult to notice, especially if you look at the contents of the file hosts using the built-in notepad in Windows - very poor editor.
To view the contents and edit the file hosts it is best to use a text editor that shows the number of lines in a document, for example, Notepad ++.
Restrictions using hosts file
List of supported shells. Terminal features database. As a result, most programs work with most types of existing terminals. This file is the first line to protect the system from unwanted access. It must be kept scrupulously and without errors and security breaches. In it, we have registered user accounts, as well as access keys and privileges.
An example of a line in this file. Different fields are separated by two points, and the meaning is the same. A number of rules that should be considered in the content of this file. The opposite would mean granting administrator permissions to the appropriate account. To find accounts with a different root name, but root permissions exist, but due to the lack of one, we can use the following command. Pseudo-users and user accounts that are temporarily closed should have an asterisk in the key field. You should not use keys that are dictionary words, names, personal data, registrations, etc. There are programs that can decrypt these types of keys. Use at least 7 characters and interpolate numbers and letters in upper and lower case. In small systems, where all users know each other and trust between them, this is not a big problem, but in systems with a large number of users it is not recommended to configure the system in this way. To avoid this, you can set "Shadow Passwords".
- This is the first thing a hacker usually does to install a backdoor into the system.
- Another thing to keep in mind is the choice of a good key.
Also, you should tune up the rather large size of the hosts file, well, in no way in the normal state can it be more than a few kilobytes in size!
2. The original hosts file is edited, after which the attribute " Hidden" or " Systemic"because by default, hidden files and folders in Windows operating systems are not displayed. In the folder C: \\ WINDOWS \\ system32 \\ drivers \\ etc file is created hosts.txt (by default, for registered file types, extensions are not displayed, and the system does not accept the file hosts.txtshe only needs hosts), in which either it is completely empty, or everything is written, as it should be in this file hosts.
3. Similarly, as in the second version, only here the attackers have already foreseen the option that extensions for the registered file types are displayed in the operating system (the user has turned on himself). Therefore, instead of the file hosts.txt the virus creates a file hostswhich has the letter " about"Russian, not English. Visually, the file looks like a real one, but it is also not perceived by the system.
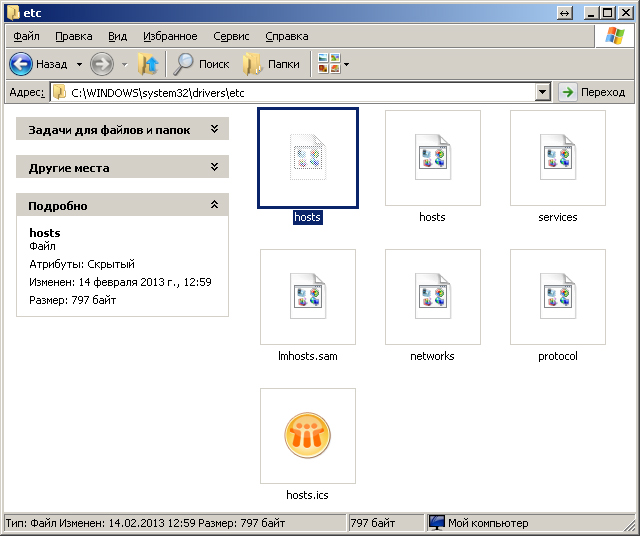
In this picture, the first file hosts - hidden, the virus has made changes to it. Second file hosts - not real, it contains the Russian letter " about"in the title, most often this file hosts empty, viruses do not bother to copy content from a real file.
File recovery hosts
If you identified similar changes to your file host, you need to restore everything to its original state. To do this, do the following:
- Disable real-time protection from your antivirus program, because many normal modern antivirus programs (for example, Avira) do not allow making changes to the file hosts.
- Open directory C: \\ WINDOWS \\ system32 \\ drivers \\ etc
- Enable the display of extensions for registered file types, hidden and system files.
- Click on file hosts Right-click and select in the context menu the string " Edit with Notepad ++":

If you do not have the Notepad ++ text editor installed, I recommend installing it first and not using Notepad. If you do not have the Internet at the moment or just too lazy to download Notepad ++, then you can use a poor notebook to edit the file hosts.
To open a file hosts Notepad you need to click on it with the left mouse button, a Windows window will appear with the message " Could not open next file ...". Set the switch to " Manual selection of a program". Click Ok. In the window " Program selection"find in the list Notebook and press Ok.
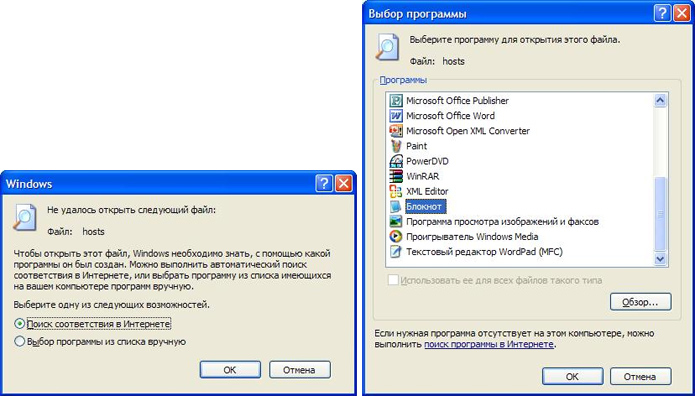
- Edit the contents of the hosts file to become as indicated at the beginning of this article.
- Save changes.
- Activate antivirus protection (if disabled).
- Launch a browser and check the ability to view the desired sites.
How hosts file works
When the user types in the browser the address (URL) of a site and presses Enter, the user's browser:
- Checks in the hosts file whether the entered name is not a proper computer name (localhost).
- If not, the browser searches for the requested address (host name) in the hosts file.
- If a host name is found, the browser accesses the corresponding IP address for this host specified in the hosts file.
- If the host name is not found in the hosts file, then the browser accesses the DNS resolver cache (DNS cache).
- If the host name is found in the cache, the browser accesses the corresponding IP address stored in the DNS cache;
- If the host name is not found in the DNS resolver cache, the browser accesses the DNS server;
- If the requested web page (site) exists, then the DNS server translates the user-defined URL into an IP address;
- The web browser loads the requested resource.
The hosts file is quite a weak point in the Windows operating system. This file is the number one target for almost all viruses and trojans that manage to infect a computer. In this article we will talk about what the hosts file is, where it is located, what it is used for and how to restore it after a computer is infected with viruses.
What is the hosts file?
The task of this file is to keep a list of domains and their corresponding ip-addresses. The operating system uses this list to convert domains to ip-addresses and vice versa.
Every time you enter the address you need for a site into the address bar of your browser, a request is made to convert a domain to an ip address. Now this conversion is performed by a service called DNS. But, at the dawn of the development of the Internet, the hosts file was the only way to associate a symbolic name (domain) with a specific ip-address.
Even now, this file has a direct impact on the conversion of symbolic names. If you add an entry to the hosts file that will associate an ip address with a domain, then such an entry will work fine. This is exactly what the developers of viruses, trojans and other malware use.
As for the file structure, the hosts file is a plain text file in the expansion box. That is, this file is not called hosts.txt, but simply hosts. To edit it, you can use a plain text editor Notepad.

The standard hosts file consists of several lines that begin with the “#” character. Such lines are not taken into account by the operating system and are just comments.
Also in the standard hosts file there is an entry “127.0.0.1 localhost”. This entry means that when you access the symbolic name localhost, you will be accessing your own computer.
Frauds with the hosts file
There are two classic ways to benefit from making changes to the hosts file. Firstly, it can be used to block access to sites and servers of anti-virus programs.
For example, infecting a computer, the virus adds There is an entry in the hosts file: “127.0.0.1 kaspersky.com”. When you try to open the kaspersky.com website, the operating system will connect to the ip-address 127.0.0.1. Naturally, this is the wrong ip-address. This leads to access to this site is completely blocked. As a result, the user of the infected computer cannot download antivirus or updates of antivirus databases.
In addition, developers can use another technique. By adding entries to the hosts file, they can redirect users to a fake website.
For example, after infecting a computer, the virus adds the following entry to the hosts file: “90.80.70.60 vkontakte.ru”. Where "90.80.70.60" is the ip-address of the attacker's server. As a result, when trying to access a well-known site, the user enters a site that looks exactly the same, but is located on a foreign server. As a result of such actions, fraudsters can get logins, passwords and other personal information of the user.
So in case of any suspicion of a virus infection or the substitution of sites, the first thing to do is to check the HOSTS file.
Where is the hosts file
Depending on the version of the Windows operating system, the hosts file may be located in different folders. For example, if you use Windows XP, Windows Vista, Windows 7 or Windows 8, the file is located in the WINDOWS \\ system32 \\ drivers \\ etc \\ folder.
On Windows NT and Windows 2000 operating systems, this file is located in the WINNT \\ system32 \\ drivers \\ etc \\ folder.
In very ancient versions of the operating system, for example in Windows 95, Windows 98 and Windows ME, this file can be found simply in the WINDOWS folder.
File recovery hosts
Many hacked users are interested in where to download the hosts file. However, searching and downloading the original hosts file is not necessary at all. You can fix it yourself; to do this, you need to open it with a text editor and delete everything except the line except “127.0.0.1 localhost”. This will allow you to unblock access to all sites and update the antivirus.
Let us consider in more detail the process of restoring the hosts file:
- Open the folder where this file is located. In order not to wander through the directories for a long time in search of the desired folder, you can use a little trick. Press the key combination Windows + R to open the Run menu". In the window that opens, enter the command "% Systemroot% \\ system32 \\ drivers \\ etc" and click OK.
- After you open the folder in which the hosts file is located, make a backup copy of the current file. In case something goes wrong. If the hosts file exists, just rename it to hosts.old. If the hosts file is not in this folder at all, then this item can be skipped.
- Create a new empty hosts file. To do this, right-click in the etc folder and select "Create a text document".
- When the file is created, it must be renamed to hosts. When renaming, a window will appear in which there will be a warning that the file will be saved without an extension. Close the warning window by pressing the OK button.
- After the new hosts file is created, it can be edited. To do this, open the file using Notepad.
- Depending on the version of the operating system, the contents of the standard hosts file may vary.
- For Windows XP and Windows Server 2003, you need to add "127.0.0.1 localhost".
- Windows Vista, Windows Server 2008, Windows 7 and Windows 8 need to add two lines: "127.0.0.1 localhost" and ":: 1 localhost".