We have at our disposal a database of more than eight thousand links to sites on the darknet. This is an almost complete registry of running open source resources available from Tor Hidden Services. We have selected the most interesting ones to tell you how to search for data on the darknet.
Forum of carders, a collection of photographs of women who crush animals with heels, a mirror of the Russian forum on Counter-Strike, women with marijuana leaves and cones in intimate places, someone's file cleaning service with a bunch of books and a file of old issues of "Hacker", a forum for weapon lovers, photos peeing women, an archive of books in Chinese, a forum for men who are keen on penis enlargement, and, of course, drugs in all forms, forms and states of aggregation. All of this can be seen in less than ten minutes of exploring the dark side of the web.
It is not so easy to dig something out of this pile of rubbish. We automatically went through all the links, and out of eight thousand pages only 4300 were opened. About a thousand sites on the fly require authorization or show a login form without any explanations - you can't drive up on a crooked goat. There were also a lot of blank pages, pages with the default response of the web server, as well as various mirrors, clones and stubs. In general, even if we take into account that some potentially useful sites are not available 100% of the time and simply did not get into our database, in general, there are not so many living resources - maybe a couple of thousand.
Using Tor from Python
Requesting pages from your scripts through Tor is not much more difficult than from the regular Internet. All you need is a local Tor node (just open the Tor Browser), Python, and a library. Here is a script that downloads The Pirate Bay's home page via Tor and displays its contents. You can probably figure out how to download something else.
import socks, socket, urllib url \u003d "http://hss3uro2hsxfogfq.onion" def create_connection (address, timeout \u003d None, source_address \u003d None): sock \u003d socks.socksocket () sock.connect (address) return sock socks.setdefaultproxy ( socks.PROXY_TYPE_SOCKS5, "127.0.0.1", 9150, True) socket.socket \u003d socks.socksocket socket.create_connection \u003d create_connection contents \u003d urllib.urlopen (url) .read () print contents
import socks, socket, urllib url \u003d "http://hss3uro2hsxfogfq.onion" def create_connection (address, timeout \u003d None, source_address \u003d None): sock \u003d socks .socksocket () sock .connect (address) return sock socks .setdefaultproxy (socks .PROXY_TYPE_SOCKS5, "127.0.0.1", 9150, True) socket .socket \u003d socks .socksocket socket .create_connection \u003d create_connection contents \u003d urllib .urlopen (url) .read () print contents |
What are these resources? After preliminary sorting, it turned out that the set of topics is extremely narrow. A significant part of the sites are shops and marketplaces, made in the form of forums or auctions in the manner of eBay. Drugs, weapons, fake documents, stolen goods, credit cards, exploits, botnets - all this can be found in abundance on virtual ruins. We will talk about specific examples in more detail.
Sites that offer services ranging from money laundering to contract killings can also be classified in this category. And if the first one sounds believable, then the second is probably a hoax. Fraud, consider it adjacent to the store segment, making it even bigger.
Another large segment is all sorts of pornography. From delights like those listed at the beginning of the article to the usual variety, which is full and on the open Internet.
Actually, a considerable share of the resources raises the question: well, why was it hidden in .onion? Libertarian blogs, hacker manifestos, homepages ... It often seems like someone just wanted to show off or practice hosting a site in a fashionable way. Such resources disappear one after another - their owners quickly realize that keeping the server is expensive, but there is no sense in it.
Search and catalogs
The first thing you want to provide yourself with, finding yourself in an alternative version of the Internet, is a search engine. There seems to be no problem here: there are Torch, Grams, not Evil, Fess, Candle, Ahima, and maybe a couple more lesser-known attempts to replicate Google's success on the dark web.
We will not undertake to compare search engines, objectively assessing the quality of the issue: this requires cunning metrics and methods that we do not have. From purely subjective feelings, Grams has seriously spam results, and not Evil and Torch poorly sort the results: at the top, instead of large sites, there may be completely random garbage. This is not always a drawback (bullshit can be interesting too), but in the end we found Fess the most pleasant.

But in the case of the dark web, search a la Google is far from the same cool and universal solution as on the regular Internet. Firstly, the most interesting things are hidden in the forums, which often require authorization, and search engines find themselves in flight. Secondly, there are so few resources in general that the search loses all meaning: for different queries you will come across the same sites plus a variety of irrelevant garbage. And that's not to mention the fact that in the dark web, search engines have little chance of tracking user behavior through the analogs of Google Analytics and AdWords in order to improve the quality of results.

The solution to the problem on the regular Internet was found even before the advent of modern search engines and looks like a directory of useful links. In a sense, this article is just such a directory, we just selected the most interesting resources alive at the moment, and, of course, we do not earn money by placing links.
With popular directories on the dark web, the situation is different: on the well-known Hidden Wiki, a significant part of the links do not open at all, and the prioritization and selection principle raise serious questions for the resource owners. There is also Onion URL Repository, OnionDir, Yet another Tor Directory, TorLinks, HD Wiki, Russian "Godnotaba" (by the way, it is really quite useful, albeit small) and hundreds of collections - large and small, curated and not so much, posted as in dark web, and on the regular, light Internet.


A completely anonymized mailbox is useful, and of course such services exist. But you understand, the demand here is very specific: not only hackers, spies, political dissidents and informers want to send letters and leave no traces, but also spammers, extortionists, bot bots and other automation lovers of all stripes. This imposes a lot of restrictions.
The most popular Tor client is called Sigaint. Its logo is an eye with menacing bloody drops below it. “Blood from the eyes” is a very accurate metaphor in this case. An interface straight from the nineties, a torn-eyed palette, advertisements crammed here and there, evil captcha (it must be entered both when logging in and when sending a letter), a mailbox size limit of 50 MB, problems with Russian encoding when sending letters ... In short, user experience roughly the level of medieval torture.

Sigaint alternatives seem to exist, but they are either paid (for example, Lenatos costs 0.016 BTC for six months, AnonInbox - 0.1 BTC per year), or they send letters only to other addresses in Tor. The second group includes, for example, TorBox and Mail2Tor. In order for a message sent from one of them to be delivered to regular mail in clearnet, you will have to use a relay, and this is a separate headache.
There is a whole class of servers based on the open source OnionMail. If you master the setup, you can connect to one of them through a regular mail client (via POP3 and SMTP). Thunderbird with the TorBirdy plugin will do, for example. For an up-to-date list of servers, see the Servers section of the OnionMail website. If you are using Linux (preferably Tails), the onion.py script will help facilitate the configuration.

Hosting
The early Internet was distinguished by the fact that for those who wanted to open their own site there were many opportunities to do it for a penny or even free of charge - in exchange for a banner or at least a link to a hoster. In Onion, the situation is different: free hosting services have not caught on, and paid ones do not look very attractive.
The reason for this is simple: mostly drug dealers and other bandits are willing to pay for hosting, which can be accessed only through Tor. If you are not planning to join them, then you can easily deploy a server even at home, or find a hosting provider who will not resent the fact that you run Tor on their server. Even for criminal activity, they often resort to the services of so-called bulletproof hosters, which also work with clearnet.

But since we're talking about hosting on the darknet, here are a couple of examples. Hidden Host promises 20 GB of space and unlimited traffic for 0.1 BTC per year; costs 0.25 BTC per year and gives only 256 MB of space and 1 TB of traffic; Kowloon Hosting Services has flexible pricing - from 0.04 BTC per month for 256 MB to 0.8 BTC for six months and 2 GB.

By the way, Kowloon (reads “Kowloon” or “Kowloon.” This, by the way, is a terribly overpopulated part of Hong Kong) has a free trial plan. If you write a letter with the subject TRIAL domain_name to a special mail, then in response you will receive the data necessary for access. That is why, apparently, during our impromptu indexing of the dark web, we found about six hundred links to empty default pages hosted by Kowloon.
Sharing
If Onion is tight with free hosting, there are plenty of places where you can temporarily host a file, picture or piece of text. For files less than 500 Kb, there are PopFiles, you can upload a picture to a site with an unpretentious name Image Hosting, text to, CrypTor, ZeroBin or Pasta.

Any of them allows you to set a timer by which the information will be erased. Stronghold Paste has a section with archives - you can ask what kind of nonsense they post there. To prevent your data from being included in this list, do not forget to check the Private checkbox. Note that Pasta has a text size limit of as much as 10 MB. If desired, it is quite possible to post a file encoded in Base64 here.
Torrents
What is usually hiding in the dark corners of the Internet, besides drugs and naked pussies? Of course, warez! In our time, however, there is no particular fun here: there is a mirror of The Pirate Bay, and it generally covers most of the pirate needs. RuTracker does not have a separate service in Onion (Tor already allows you to access RuTracker.org bypassing the blocking), but Rutor does. You can also take a look at "Buried" - this site is an order of magnitude smaller (1.6 million hands versus 25 million for Rutor), but an extra chance to find something rare will not hurt.

Books
For book lovers, the dark web also has everything you need - first of all, it is "Flibusta" and an excellent search engine for the "Traum library" called "Verbal Bogatyr". English and German books can be found in the place with the pretentious name of the Imperial Library of Trantor, but with new arrivals there is a bit tough. There is also Caliber, although the database of 1600 books is somehow not very serious. In the ruins of computer and educational literature in English, you can delve into this link. And of course, the mirror of the pirate aggregator of scientific works Sci-Hub seriously claims to be in the bookmarks.

Communication
Going to hidden services just to get worn out is definitely fun for everyone. On the regular web, there are enough resources on which you can register anonymously (or not register at all) and chat about whatever you want. Onion sites talk mostly about business. What - you probably already understood.
There are not many places for free communication, but they do exist. Until recently, a 2ch.hk mirror worked in Onion - here's a link in case it comes to life. There are other image boards: the famous in narrow circles foreign 8chan, Russian-speaking Neboard and Khaibane.

Galaxy2 can be considered the main social network on Onion - if you dig around, you can find interesting thematic groups or meet interesting people. Those who prefer to communicate in Russian will be interested in the onelon resource. This is a rather unusual blogging platform with a small but vibrant community. Please note that in order to register, you will need to create a PGP key for yourself (by the way, this is a common phenomenon in the dark web).

The Hidden Answers website may also be helpful. This is something like Yahoo Answers or Answers @ Mail.Ru, but with a focus on the dark web and related things. The main topics are the reliability of marketplaces, configuring Tor and, of course, finding thematic resources. The latter makes Hidden Answers an interesting place to start surfing.
At the very least, it's worth mentioning that Onion has a Facebook mirror. For those living in Russia, it makes little sense, but, for example, in China Facebook is blocked, so going to it through Tor is the most it.
Generally speaking, much of the correspondence on the shady side of the internet does not take place on websites, but on Jabber and IRC. Choosing suitable clients, setting up anonymous connection, and finding servers and groups is a topic for a separate article, so here we will limit ourselves to just a couple of links. TorXMPP, Cyruserv, securejabber.me - Jabber servers located in Onion; CgAn IRC and Volatile - IRC clients that can work directly in the Tor Browser; ChatTor is a primitive but convenient web chat with the ability to create your own rooms.

Well, if you suddenly become completely bored and have no one to talk to about the weather and the latest research on the darknet, then take a look at Chat with strangers - a local analogue of Chatroulette.
The shops
Stores and marketplaces seem to be the main use of Tor's hidden services so far. Therefore, we will dwell on them in a little more detail and (solely for research purposes) go through the main markets. In general, when you look through the lists of links, all these "acropolis", "alexandriy", "oases", "ghettos", "shops", "shops", "shops", "pharmacies" and other nooks start to spin your head. The competition is enormous, and every creepy drug dealer is trying to snatch his own, get lost and figure out how to stand out. What do you think of the name of the store Shimmering Circus of Vengeance? We liked it too - purely from a literary point of view.
AlphaBay

AlphaBay is one of the largest markets to share the hidden market after the closure of the famous Silk Road. "Officially" it is believed that the site was "founded by a carder under the nickname alpha02, a well-known member of most carder forums and a well-known personality among advanced carders." European researchers assure, however, that the market operates under the patronage of the "Russian mafia", since the servers are located in Russia and are administered from Russian IP addresses. (It would be nice, by the way, to come up with a more catchy name like "yakuza" for the "Russian mafia"!)
The mafia may be Russian, but the site is completely English. Registration is free, but very difficult - with a couple of dozen fields. Trading, as in the vast majority of markets, goes for bitcoins. There is an escrow service. Buyers note that the site is promptly moderated by cleaning up spam and scam. However, judging by some sections, crammed with advertisements and offers of intimate services, this is still not enough.
AlphaBay's biggest advantage is, of course, the range. The market contains 147 thousand offers in the Drugs & Chemicals section (offering, as expected, drugs and illegal drugs), 27 thousand - in the Fraud section (where database dumps and personal data are sold) and 13 thousand - in the Digital Products section (access to accounts, game keys and a variety of software). Several thousand items each contain other sections: weapons, jewelry, carding, malware, hosting and other services. Unexpectedly interesting is the Guides & Tutorials section, which offers a wide variety of information for sale: from harmless site directories or guides on "hacking Wi-Fi" to ready-made botnets, including lists of existing bots, instructions for use and management software.
Dream Market

The market is close in functionality, quality and content to AlphaBay. Specializes in drugs and digital products. There are an order of magnitude less positions, but in general the range of products is the same. The market is not remarkable in any way, except perhaps the intriguing question: why would anyone use it if there are better markets?
We decided to show you this site for one reason: other English-language stores have an even scarier assortment. In other words, if AlphaBay is “the best of the best,” then Dream Market is the “worst of the best,” a kind of “first step” in the quality of a typical hidden market.
Hydra

Hail Hydra! Oh, stop, this is not about that. Hydra calls itself an "anonymous trading platform", but in essence it is a social network for drug dealers. Specializes exclusively in drugs (amphetamine and its salts, cocaine and derivatives, bookmark exchange). At the same time, the owners do not hesitate to advertise even on the open Internet: the hydra.ooo site is on the first pages of Google, which is strange. Children's typos and frivolous emoticons do not add confidence either.
The site is Russian-language, and judging by the comments in the code and the applications used, it is originally Russian. Registration is minimalistic (username and password) without any confirmation. There is a chat. Spam is not cleaned: administrators do not consider those who paid money for placement as spammers, which is reported on the first page. In addition to the sections on selling, hiring and discussing sellers in different regions and countries, it has three interesting sections: "FAQULT" (in topics of which the details and secrets of the shadow drug business are revealed), "HYPERLAB" (recipes and methods for synthesizing drugs) and "WORK" ( the scorching hidden relationship of some seemingly legal professions with the world of drug trafficking).
T * chka

Another drug market, but unlike the rest - with an ideology. "Tochka" (as the name implies, the creator is Russian) was created a year and a half ago and positioned itself as the first drug market that controls the honesty and security of the transaction: before "Tochka" in the English language Onion, the concept of "bookmark" (dead drop, drop-off) did not receive wide distribution. The site administrator admitted that he is trying to invest in the market "honesty, security and tolerance in every way": this can be seen already during registration, in the warning about the prohibition of the distribution of low-quality and untested drugs, weapons, poisons, porn, extremist materials and discrimination on the basis of race, politics or religion.
The interface can be selected in Russian, but the description of all offers is in English. As you can see on the screenshot, there are three orders of magnitude less offers than on AlphaBay, but the emphasis is on the "purity" and "quality" of the product. The goods, by the way, are not always drugs - they are sold on the market and rare and expensive drugs, which in a number of countries cannot be obtained legally, documents and programs for falsification, some hacker services.
Forums
RAMP

Another Russian-language semi-forum-semi-market for drug dealers. There is no communication, discussion of hacking, security, cryptography, leaks, malware, carding, and so on is prohibited already at registration, during which you have to dig into this list of prohibitions for two minutes. All activity on the site is reduced to drug trafficking.
The hub

A dull English-language forum about everything that is not allowed on the white fluffy Internet. The vast majority of comments are in the For Beginners, Darknet In General and Off Topic sections, which seem to hint at the quality of the audience and discussions. Doesn't work without JavaScript. The Vendors section contains dull self-promotion attempts by a huge number of drug dealers and stretched monotonous reviews of various drug markets. God, how tiring it is.
Closed hacker forums and sites
Hacking topics can be found here and there, but the specialized forums are generally not very friendly, and even free registration is rare. For example, entrance to Hell, one of the most famous forums, costs 0.1 BTC (about $ 60).
 Hell
Hell GroundZero, SiphON, and BlackHat look open at first glance, but suspiciously empty. There is no doubt that all the most interesting is hidden in sections that are not visible to a simple visitor.

When registering on most of these forums, they offer to enter an invitation code, and even if you own it, it is not a fact that all branches will be immediately open to you. There are quite a few public sections on the 0day forum, but you can be sure - and here, too, the main movement takes place in sections where you cannot get from the street.
 0day
0day Very little remains in the public domain. The most popular topic is carding: bays, CVV, cashing for various payment systems, ways to bypass antifraud, discussing where to get dumps. In general, the battle crobers from Carder Planet will be boring here, but if you are just interested in the topic, you will definitely learn something new: read the FAQ and click on the links for newbies that the community generously shares.
As for the rest of the sections in the public, there is a real chagrin: the chance of finding 0day is generally lower than in clearnet. But you can look at the section Accounts and Database Dumps, sometimes you can find familiar words like VK or Rambler.
Of course, hacker groups also have personal sites on the dark web. Take CyberGuerrilla, The Hack Lair, Hacker4Hire and Hackmasters as examples, but to be honest, there isn't much to catch. The only thing that stands out is the Anonymous International exchange, where you can take part in trades where the contents of the accounts of Russian officials are played out.
Weapons, espionage, special operations
Runion

Russian Onion Union is the most popular and informative Russian-language dark web forum, specializing in defense and self-defense. In the section "Weapons" you can find basic concepts and FAQs on weapons, instructions and books on making homemade means of protection, calculations of the power of explosives, discussion of military equipment, weapons and ammunition, lessons on self-defense and sabotage, as well as warnings of knowledgeable people about the weapon web -forums selling information about their visitors.
The section "Security Techniques" discusses methods of wiretapping, surveillance, detection and protection from them, typical mistakes of beginner anonymous and high-profile mistakes of well-known terrorists. There are FAQs, rules and tips for safe behavior around the world, as well as ways to circumvent official bans, hide potential evidence, and cover your tracks. An instruction called "Cleaning Day", listing the ways to maintain personal information purity, will be useful to any visitor, even if he entered the forum with the most innocent intentions.
The "Information Security" section will tell you about methods of encrypting and hiding traffic, secure services and utilities, as well as ways to increase bullet resistance of some popular programs, devices and web servers. A topic titled "Tails: FAQ" explaining what The Amnesic Incognito Live System is will be a great start for an anonymous person taking their first steps.
Raegdan's Fukken Saved

Russian-language archive containing full and partial dumps of some clearnet sites that were "cleaned up" at the time. For weapon lovers, there are many interesting things here.
- Dump of the weapons forum steelrats.org, storing content at the end of 2012. The forum contains a number of materials on the handicraft design of weapons, special equipment and reconnaissance equipment. You can compare it with Runion and appreciate how pathetic Anonymous looked at that time.
- Drawings, photosets and video instructions for 3D-printing homemade weapons, saved from the defunct site of American James Patrick. The weapon, however, is suitable only for self-defense, because it is plastic.
- Guides of a young rebel for putting together his own armed gang: "The ABC of Domestic Terrorism", "Guerrilla Warfare" and "Textbook of the Urban Guerrilla". Of course, after reading these books, you will not be able to make any "urban partisan" (partisans generally do not read books very much), but this can help to better understand the psychology of bandits and avoid contact with them if riots arise.
Cryptostorm

Tor version of the forum of the eponymous VPN provider Cryptostorm, located in Iceland. A fairly informative English-language resource containing discussions on protecting and encrypting information about personal life and travel. Basically, of course, it contains sections on how VPN Cryptostorm works and how their Cryptostorm Widget "absolute protection" utility is developed. The Stormphone section contains some small but valuable information and discussion on the topic of data protection on mobile devices.
Black Market

A store that claims to be "Number One in the Tor network" and behaves almost legally. The owners claim that they provide a quality guarantee in all countries of the world, the weapon is tested and can be replaced in case of its failure (within one week), delivery is already included in the prices, and ten free rounds are attached upon delivery. In short, an epic and very beautiful divorce, the impression of which is not spoiled even by the gold Desert Eagle listed in the product list. Indeed, suddenly someone wants to anonymously and secretly buy a pistol to show off to friends. Why not.
Black Market Guns

In contrast to the previous one, there is a real weapons store located in the United States and legally selling weapons, parts, parts, and ammunition permitted in the United States. Contains 26 items, among which there are even a pair of night vision devices. The owners tacitly bypass all the questions of legalizing the purchase on the buyer's side, offering only delivery via FedEx. Zipped product and assembly instructions included. The official email at tutanota.com also makes one believe the offer is serious. But we certainly did not check.
No Background Check Gun Store

A store of unknown origin (we suspect the owners are from the United States, but there is no confirmation anywhere), which positions itself as "the largest catalog of weapons on the Deep Web." The number of positions is really impressive: the owners offer a choice of 570 pistols, 230 rifles and 30 pump action shotguns. The choice is so great that there is a catalog search. Only three facts are confusing: the round number of positions in the sections, mail on gmail.com and the most famous manufacturers in each of the categories. Too pretty to be true.
Euro Guns and UK Guns

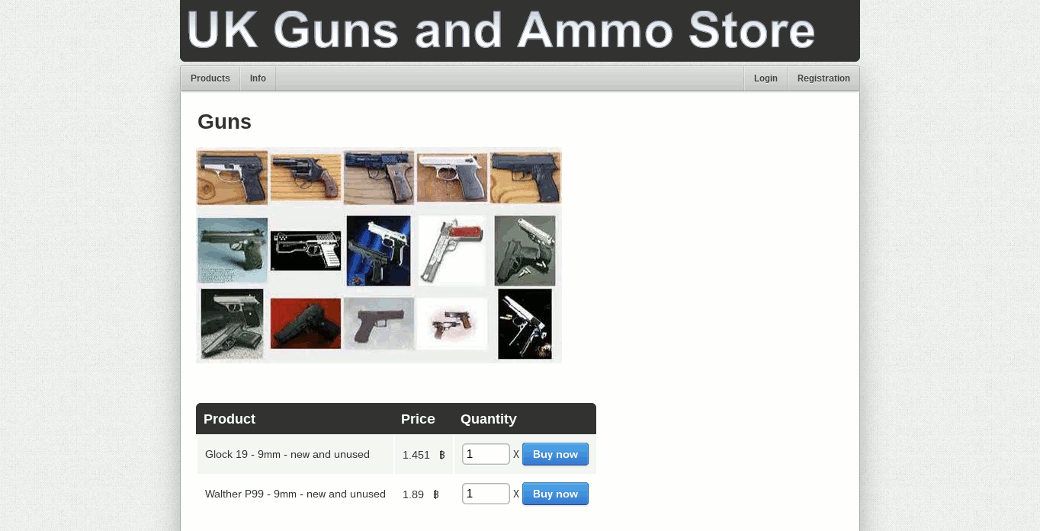
Two stores of the same owner, operating, respectively, from Europe (presumably the Netherlands) and the UK. The owner carefully offers customers registration (why?), A referral program with a deduction of 1% (well, that's why), several ways to buy bitcoins for cash and free shipping. At the same time, the assortment is small and absolutely the same, which suggests the presence of a common owner (and most likely, one person in general, who is neither in the UK nor in Europe). If you successfully acquire something here (which is very unlikely), do not forget to deduct us 1% for a tip!
MaskRabbit

A fun site that bills itself as "an anonymous agency for real-world operations." Specializes in delivery, theft, espionage, sabotage, banditry and burglary. At the same time, he immediately amuses himself with the fact that he declares to work "only with professional agents", while at the same time offering to send an application to join the ranks of these "agents". Take a rest, 47th, a worthy replacement has been found for you - you see, a letter came from Vasya from Voronezh!
C'thulhu

An even more fun site, the name of which already speaks of the high professional level of its creators. The intentions of the "organized criminal group C'thulhu" are so serious that they have to explain why you should hire them and precisely through Tor. To the reasonable question “Where are the proofs, Billy? We need proofs! " the developers give a weighty answer: we remove all the proofs after completing the order (for your own safety), and our customers have absolutely no time to sit on the forums and answer any letters. Nuff said.
However, the degree of fun is somewhat reduced by the presence of a public PGP key, email to bitmessage.ch and a detailed price list. Perhaps, behind the deliberately ridiculous, "averting" facade, there is still a serious business.
Besa Mafia

Not at all funny site of the current Albanian mafia group. Open it only after making sure that there are no children nearby.
Besa Mafia operates in the United States, Canada, Europe and many other countries, offering such brutal services as debt collection (with self-harm), murder to intimidate (however, covert elimination too), setting fire to cars and houses, and the sale of unregistered weapons. In the sections of the site you can find instructions for maintaining anonymity when ordering, a step-by-step description of the secure payment process for an order, a price list, FAQ and even a disclaimer, which states that Besa Mafia services are provided solely to protect the client from the threat looming over him. To place an order, you need to indicate the contact of a person who is already in the group, otherwise you yourself can become the next target. The creators of the site also declare that they are not executors: they are intermediaries and receive 20% of the amount for this. The performer gets 80%.
Well, did you believe it? Convincing enough? And now it's true: this site is a police scam. Administrators of Besa Mafia are leaking correspondence with "customers" and contacts of "executors" to law enforcement agencies of different countries. If you are paranoid, you might have suspected this even while watching the "Video" section: the videos posted there are a simple cut from American news, which is pulled from YouTube and does not work without JavaScript. However, after the Silk Road leaked, most Tor sites have become a similar scam.
Other usefulness
Dead drop - service for the transmission of encrypted messages. To register, you need a PGP key, it will also help to leave the message without an addressee. Those who want to read it will be able to enter your public key for this, and the service will display the text.
Deep web radio... Considering that there is not much tension with music on the "clean web", the existence of an underground radio station is not easy to justify. But nevertheless it exists. You can listen to one of the five "broadcasts" and be delighted that you do it through Tor.

Bitcoin Block Explorer, a mirror of Blockchain.info, a site that helps track Bitcoin transactions.
Keybase - Keybase.io mirror. It allows you to associate your public PGP keys with a user profile. It doesn't hurt to sign up, but remember that Keybase is famous for its long virtual queue that must be defended before an invitation is sent.
Cryptome - a mirror of the legendary site about privacy and cryptography Cryptome.org. The last time it was synchronized in 2013, but while the main site has not disappeared anywhere, the meaning of using the hidden service instead is in doubt.
Total
Of course, it is impossible to take and survey the entire dark web. First of all, because two thousand links are still two thousand links and it is not easy to go through them all (and it is not necessary). You probably got the general idea, and, we hope, the questions "what to see?" and "where to start?" we answered.
The second, even more important point - “dark” in the word “darknet” still implies that sites are hidden from outsiders and it is impossible to get to them from a swoop. No indexing will save you, and this requires an individual approach.
In general, the open part of the dark web is so reminiscent of the Internet of the nineties with its characteristic anti-design and general carelessness that nostalgia immediately rolls over. The main difference is that the sites in Onion are much smaller and they are much more criminal. But here you can, as if in the good old days, surf the net and feel the wind of freedom blowing from all sides!
Remember that the Tor browser is absolutely not enough for anonymous surfing, and even more so for any active activities on the dark web. We recommend using the onion browser in conjunction with a VPN. CyberGhost is best suited for these purposes:
- does not save any logs (even connection metadata);
- does not allow IP, DNS or WebRTC leaks;
- better data encryption AES-256;
- high speed of work and a bunch of locations to choose from;
- the cheapest VPN for DarkNet surfing.
DarkNet list of sites for Russian-speaking users:
http://hydraruzxpnew4af.onion - Hydra, the largest shadow market in Tor, from pavs to documents and VK hacking;
http://lwplxqzvmgu43uff.onion - Runion, Anonymous Forum: Bitcoin, Tor, Free Market;
http://bitmixbizymuphkc.onion is the best bitcoin mixer, you can mix BTC, ETH, LTC.
buybit4xcbat2cwn.onion RU BuyBit - instant purchase and sale of bitcoin (with Qiwi integration), the service does not require any confirmation and accepts payment from terminals. Good online support that solves your questions online. Online discussion;
http://totetxidh73fm4e3.onion - Totet, bitcoin tote;
https://onion.cab - clearnet (!) onion.cab, view hidden onion sites without Tor;
http://facebookcorewwwi.onion - Facebook, the same one));
http://sms4tor3vcr2geip.onion - SMS4TOR, a self-destruct message service;
http://oi4bvjslpt5gabjq.onion - République de Hackers, another French-language hacker forum;
http://pwoah7foa6au2pul.onion - Alphabay market;
http://mail2tor2zyjdctd.onion - Mail2Tor, e-mail service;
http://torbox3uiot6wchz.onion - TorBox, e-mail service inside .onion;
http://zw3crggtadila2sg.onion/imageboard - TorChan, "Tor's # 1 imageboard";
http://cyjabr4pfzupo7pg.onion - CYRUSERV, a jabber service from CYRUSERV;
http://rusilkusru6f57uw.onion - Russian plagiarism of the legendary "SilkRoad" [Marketplace with a forum];
http://rutorc6mqdinc4cz.onion - RuTor.org, a well-known torrent tracker;
http://flibustahezeous3.onion is a famous electronic library in an “onion” version.
Darknet search engines:
http://hss3uro2hsxfogfq.onion - not Evil search engine;
http://xmh57jrzrnw6insl.onion/ - search engine Torch;
http://gjobqjj7wyczbqie.onion/ - search engine Candle;
http://msydqstlz2kzerdg.onion - Ahmia search engine;
https://3g2upl4pq6kufc4m.onion/ - DuckDuckGo search engine;
http://grams7enufi7jmdl.onion/ - search engine Grams;
https://tor2web.org - Find darknet sites without Tor.
Denial of responsibility: This article is written for educational purposes only. The author or publisher did not publish this article for malicious purposes. If readers would like to use the information for personal gain, then the author and the publisher are not responsible for any harm or damage caused.The last 10 years have become the brightest in the history of the Web. During this period, there have been a huge number of discoveries and scandals. All this happened here, on our virtual "land". But many people know that there is a "dark side" of it. Today we'll talk about what the darknet is.
general information
It is known that this concept can be interpreted in different ways. First of all, the darknet is a special private network that has a secure connection and is established between trusted individuals. They are often called “friends”.
What is the darknet? Non-standard protocols and ports are used here. The main feature of such a resource is anonymity. It differs from all usual networks in that file sharing is done anonymously, which means that all users communicate freely.
Difference
From all of the above, it becomes clear that this resource is often applicable in cases where you need to hide something. Accordingly, this is how any illegal activity is carried out. The Darknet is becoming part of non-profit networks and may be associated with "underground" communication and technology.
It so happened that it is not easy to understand exactly all the terminology. Most ordinary users associate DarkNet with the Deep Web. The Dark web is also credited here. On the one hand, all these concepts very often become synonymous when trying to explain the basic network phenomenon. On the other hand, each of these concepts has its own interpretation, which it is desirable to separate. What is meant?
The Deep Web is a phenomenon that describes many web pages that are not crawled by a search engine. This is also attributed to the "deep web", which is represented by web pages created by queries to online databases.
The Dark web is considered to be the "dark web". It is represented by network segments that require special software for free access, but at the same time all data belongs to the general Network.
History
So what is the darknet and how do you get there? Obviously, this implies a certain phenomenon that has existed for a long time. It is often called the "dark internet" by the people.

The term itself was formed in the distant 70th year of the last century. For security, it has been interpreted as part of networks isolated from the ARPANET.
The latter concept denotes a computer network, which was developed by American specialists back in 1969. As studies later showed, there is a high probability that it was this invention that became the modern prototype of the Internet as such.
These networks at that time were free to collect the necessary data from the ARPANET, but at the same time remained anonymous visitors. This concept gained great popularity in 2002. Then a quarter of employees from Microsoft published the corresponding work. In it, experts disassembled the darknet according to several main ideas:
- Objects that are available to any user can be transferred to him in case of obtaining the appropriate permission to copy.
- The user is free to copy files (if possible).
- There are some channels for users with high bandwidth.
Using
It is said that people want to know how to get on the darknet for three reasons:
- To get privacy and avoid political reprisals.
- Committing crimes in the field of information technology.
- Distribute or search for documents that are copyrighted.
Dark side
Despite such a rather peaceful interpretation of this concept, we are still dealing with the "dark Internet". It is about him that users often try to find out. Those who are not familiar with this concept present it as something illegal and forbidden.

It is in this segment of hidden networks that the most important crimes take place: murder, drug trafficking, pornography, etc. Here you can find online stores with weapons, drugs, and false documents. And most importantly, all this is inviolable. That is, no state is able to control such activities.
In simple terms, the Russian darknet or any other is a segment of the deep Internet. It is represented by non-indexable sites that cannot be crawled by any one, and it is impossible to find them through any modern browser.
The current situation
It so happened that the latest innovations of the authorities of Russia and Ukraine made many users learn about VPN, Tor, IP2P, proxy. All this helps to bypass the blocking of various resources and social networks. But we must not forget that such tools significantly reduce the speed of working with websites, which ultimately leaves a negative impression.
The dark internet has become even more difficult. It so happened that a lot has to be done for anonymity and security. And the excursion to dangerous places itself has its own atmosphere.
Structure
For those who still poorly understand what the darknet is, it is easier to show the entire structure of the modern Web. So, at the very top is the regular Internet. There are social networks and simple resources for working, selling and buying everything legal. That is, everything that a regular PC user uses.

The next rung (posted below) is the "deep internet". For it, you already need to acquire a proxy. On it you can find hacker forums, various blocked sites and other content that does not quite fall into the legal framework.
Further, it is worth mentioning the darknet we are monitoring. The "dark internet" is only accessible through special services like Tor. Here everything is already very bad, illegal and illegal. You can watch the drug trade, the sale of weapons, documents and even people. Here you can send important and secret files or prohibited books.
If you think that the dark web is the bottom of the modern web, then you are wrong. Then there is the "closed internet". Few people talk about him, but his traces have been confirmed more than once. Although for many, its existence is in doubt. It is possible to get here only through closed systems. There are reports of government figures, secret experiments, snuff and connections with killers.
Well, even that's not all. There is the concept of the "Mariana Internet". It could, of course, be based on hearsay. But there is no smoke without fire, which means that it can also be mentioned in our structure. They say that all secret knowledge is kept here. Maybe even correspondence with aliens.
Transition
So, of course, not everyone knows how to enter the darknet. And very few people need weapons and drugs right now. There are many ways to get there, and how you can do it is described even on "Lukmore". The most common and easiest option is This program alone can open sites that end in ".onion". Therefore, it is sometimes called the "onion" browser ("onion" is translated from English as "onion").
You need to understand right away that search engines will not help you much to find anything. It's not worth asking Google to find an online drug store. For this, it is better to use special search engines such as Torch or Fess. There is even an analogue of the legal Google called Grams.

But even such programs, most likely, will not help you find even the slightest bit interesting information. Usually everything is stored on forums where registration is needed. Sometimes you need to get tested or donate bitcoins.
There are a large number of directories on the dark web for easy searching. But they all work disgustingly. Some do not indicate links, some have broken addresses. But if you dig well, you can find the data you need.
Anonymity
Despite the fact that most rely on the absolute anonymity of the darknet, the reality is not that cool. Even the most advanced hackers have already been found by the special services. For example, in 2013, Eric Márquez was arrested, who became the founder of a child pornography site. In the same year, Ross Ulbricht, the creator of the popular online drug store, was also found. Although his arrest is a rather random and stupid business.
Ordinary users have also more than once come under the attack of some kind of spy codes that easily calculate the IP address and send them to the necessary services. Even now, you can stumble upon some kind of trouble.
Prosperity
Usually, all the resources that were prohibited on the surface go down to the "deep internet". So Pink Meth is still actively thriving here. Previously, he was popular with angry exes. Intimate photos of their soulmate were uploaded here, indicating even a link to a page on social networks.

Discussion of illegal types of earnings continues on Russian-language forums: blackmail, fraud. Psychics and prostitutes "live" here. Discussions lead to absurd conclusions. Someone needs to stock up on weapons to survive in the zombie apocalypse, someone buys tickets to other planets.
In addition to the above, you can still find a flamethrower, a new passport or driver's license, buy counterfeit banknotes or buy a gold bar. There is information that even slaves and human organs are being sold here, but such data simply cannot be found.
Russian segment
There are a lot of darknet sites in Russian. Moreover, in addition to some illegal and illegal trading, you can find forums where anarchists and neo-Nazis are still preserved. There are also a lot of platforms for journalists and political oppositionists. They calmly exchange hot information.
Apart from this, there are interesting libraries of music and books. You can try to find here those books that you previously could not purchase in stores. You can also rummage through the catalog and download your favorite work for free.
Finance
You already know what the darknet is. Many associate with this network BitCoin. This is not surprising. The fact is that it is the main currency on the darknet. Only it can pay for all purchases. The cryptocurrency was introduced by hackers from the moment it first appeared. To use it, you can register a special wallet.

conclusions
In general, if you do not need anything specific from the "dark Internet", then there is nothing special to do here. Of course, figuring out how to find the darknet can be for general development. But aimlessly exploring this network is pretty boring. You need to understand which services to go to, it is better to know certain sites. As already mentioned, all very important and classified materials cannot be found even by cool hackers. An ordinary user can’t do it all the more.
For the rest, at first glance, the darknet fascinates. Here, as if everything is allowed and possible. On the other hand, who needs a UK driver's license? All this looks like pampering for the average user.
Interest in the darknet is growing, this is a sad fact. But many people misunderstand what it is. And confused with other terms.
We will tell you what the darknet is, why you need it and how to use it. All information provided below is solely at your own risk.
What is the darknet

There are many darknet networks in the world. Some are in trend today, others are out of date. But the first visit to any darknet will be a shock and a revelation for you. Especially if you do not remember the Internet of the early 2000s, the creak of a dial-up modem and payment for traffic over the cable.
On the darknet, connections are established only between trusted nodes (friend-to-friend "friend-to-friend") using special ports and protocols. Server IP addresses are hidden. You can't access the darknet through a regular browser like Safari or Chrome.
The networks are decentralized, so they are not controlled by one single person. This provides users with some leeway.
Sites on the dark web often use Tor encryption technology. It allows you to hide the identity of the user and spoof the IP address, as well as hide the resource from prying eyes outside the network.
But that doesn't mean that the entire darknet is only accessible through Tor. If you need a website protected by Tor encryption technology, you must use the browser of the same name. However, there are also networks based on I2P and other technologies.
Darknet or deepweb

The darknet is often confused with the "deep internet". In fact, the darknet is a part of the Internet, a network within a network that operates according to its own protocols and algorithms. Deepweb is pages that are not indexed by search engines. They may not exist at all until someone needs them. For example, they will be created in response to a database query.
The search engine cannot find pages in deepweb. And on the darknet, it's easy. This, of course, is not about Google or Yandex.
Will they be jailed for entering the darknet

In this case, the laws do not work against an ordinary user, but against the creators of blocking bypass tools and providers. For example, the Tor browser is prohibited in Russia, as it makes it possible to bypass blockages. But there is no responsibility for using it yet.
So if you go to the darknet to “see it cleanly” and “just ask”, you will not be punished or fined. But it should be understood that all other actions also qualify from the point of view of the current legislation. For example, selling drugs, distributing porn or stealing money from bank cards.
How to search for sites on the darknet

Another popular service is Fess. It indexes the .onion segment better because it is built on the Tor engine. You can also use the search engines not Evil, TORCH, Ahmia:

And then there are link directories like The Hidden Wiki and oneirun. The resource "Godnotaba" is known from the Russian ones.

Of course, search engines on the dark web are weak. Ranking is set by programmers, in many cases manual filtering is used, and the speed is extremely slow. There is no question of setting up search and taking into account personal preferences. But, as they say, what are they rich in ...
Search results are entirely up to you. Requests in Russian are not a problem, of course. For example, here's what they offer for treasure men (people who make bookmarks with prohibited substances in residential areas):

This, by the way, is considered a cool design:

And what, there is only weapons, porn and drugs?

Not at all. For example, one online library previously popular in Russia has gone to the darknet.
Tor has mirrors of major torrent trackers, resources like the anonymous Q&A service Hidden Answers, gaming and entertainment portals, and even its own literary magazine Torist. Since the connection speed is low, you don't have much fun.

However, there are enough hacker sites and resources with other illegal goods and services. For example, you can buy fake documents, government documents. a number on a car, order assistance with a loan, an attack on a server or breaking through a mobile or a copy of someone else's SIM card.
There are also resources of banned organizations - nationalist, neo-Nazi, terrorist, extremist. This is where the content really blooms and smells, falls out in tons and is actively discussed.
The censorship is not the most aggressive in Russia. In the same China, the "Golden Shield" system operates, which blocks access to the vast majority of resources, as well as new nodes of the Tor network. However, VPN and proxy solve the problem. And the authorities will not ban VPN, because they know that all external business communications are built on VPN.

North Korea was out of luck. They don't even have access to the darknet, and they can only access the Internet with Kim Jong-un's permission. Moreover, the entrance to the rooms where the computers connected to the Internet are located is carried out by passes.
Why the darknet is dangerous

There are many sites on the darknet that exploit "zero-day vulnerabilities" - holes that developers are not yet aware of. Such vulnerabilities allow, for example, to spy on you through a laptop camera and microphone.
By opening Tor, you make your computer part of the onion network. And due to this, you can become an accomplice in major crimes that hackers commit - for example, brute-force passwords or DDoS attacks.
Or your computer starts to slow down because someone starts mining on it. And recently, tools have appeared that continue to exploit the power of your computer, even when you closed your browser (an invisible window remains).
Often, pages on the darknet can disappear from the access zone for a while or disappear forever.
It is dangerous to download files on the dark web, including documents for Word and Excel. The likelihood of contracting a virus from them is much higher than in the open part of the Internet.
13-02-2016
"DarkNet" is the dark layer of the Internet, which can be connected only through a special browser - Tor. The Darknet is characterized by a higher degree of anonymity, which is why it is in it that communities engaged in illegal activities are concentrated - arms, drugs and bank cards. But there are also legal projects - libraries,. People choose this network for freedom of speech and privacy.
How to enter the "Darknet"
It's pretty simple. It is necessary download Tor browser from the official site. It is highly discouraged to download Tor from other resources. such a distribution may contain Trojans that can declassify your online presence. Next you need install browser.When you first log in, you need to choose from two options: just connect or configure the network parameters. If you want to use a browser to access a blocked site, for example rutracker.org, then select "connect". If you want anonymity, then you need the "customize" option. Tor works in the same way as regular browsers, but in a more complex scheme, which negatively affects page loading speed. With it, you can visit both hidden and regular sites. Make sure it is configured correctly, follow the link - https://check.torproject.org/?lang\u003dru.
How Tor Browser works
The essence of the work is reflected in the onion logo. Just like her, the connection consists of layers - a chain of proxies. The information passes through 3 randomly selected network nodes. On the client side, before the packet is sent, sequential encryption occurs for each of the nodes.
Thor browser for mobile devices
For information on how to log into the darknet from a mobile phone, see.Darknet sites
You can find links to popular sites in the Russian darknet at godnotaba.top. The project was created for informational purposes only. All transactions on prohibited sites of the Tor network are illegal and punishable by law. The project is for informational purposes only and is intended for a general understanding of the TOR network.
Sites in the Tor network are located in the domain zone .onion... Below is a list of some of the resources:
not Evil - search engine on the Tor network
TORCH is another search engine
Flibusta - book library
More links in the material.
If you are confused by the address hss3uro2hsxfogfq.onion, then it should be noted that almost all sites on this network look like this.
The Onionland community also exists on Reddit. You can find all kinds of links there too.
Safety
It should be noted that using the Tor browser does not guarantee the anonymity of your actions. Information and offers from the web may be false. Beware of scammers!