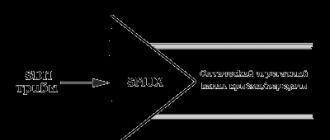
Just started working as a network administrator? Don't want to be confused? Our article will be useful to you. Have you heard how a time-tested administrator talks about network problems and mentions some levels? Have you ever been asked at work what levels are protected and working if you are using an old firewall? To understand the basics of information security, you need to understand the principle of the hierarchy of the OSI model. Let's try to see the capabilities of this model.
A self-respecting sysadmin should be well versed in networking terms
Translated from English - the basic reference model for the interaction of open systems. More precisely, the network model of the OSI / ISO network protocol stack. Introduced in 1984 as a conceptual framework that divided the process of sending data on the World Wide Web into seven easy steps. It is not the most popular, since the development of the OSI specification was delayed. The TCP / IP protocol stack is more cost effective and is considered the primary model used. However, you have a huge chance of encountering the OSI model as a system administrator or in the IT field.
Many specifications and technologies have been created for network devices. It's easy to get confused with such a variety. It is the model of interaction of open systems that helps network devices to understand each other using different methods of communication. Note that OSI is most useful for software and hardware vendors who design interoperable products.
Ask, what is the benefit to you? Knowledge of the multi-level model will give you the opportunity to freely communicate with employees of IT companies, discussing network problems will no longer be oppressive boredom. And when you learn to understand at what stage the failure occurred, you can easily find the causes and significantly reduce the range of your work.

OSI layers
The model contains seven simplified steps:
- Physical.
- Channel.
- Network.
- Transport.
- Session.
- Executive.
- Applied.
Why does decomposition into steps make life easier? Each of the levels corresponds to a certain stage of sending a network message. All steps are sequential, which means that the functions are performed independently, there is no need for information about the work at the previous level. The only necessary component is how the data from the previous step is received, and how the information is sent to the next step.
Let's move on to direct acquaintance with the levels.
Physical layer
The main task of the first stage is the transfer of bits through physical communication channels. Physical communication channels are devices designed to transmit and receive information signals. For example, fiber optic, coaxial cable, or twisted pair. The transfer can also take place wirelessly. The first stage is characterized by the data transmission medium: protection against interference, bandwidth, characteristic impedance. The qualities of the electrical end signals (type of coding, voltage levels and signal transmission rate) are also set and connected to standard types of connectors, contact connections are assigned.

The functions of the physical stage are carried out absolutely on every device connected to the network. For example, a network adapter implements these functions from the computer side. You may have already come across the first step protocols: RS-232, DSL and 10Base-T, which determine the physical characteristics of the communication channel.
Link layer
At the second stage, the abstract device address is associated with the physical device, and the availability of the transmission medium is checked. Bits are formed into sets - frames. The main task of the link layer is to identify and correct errors. For correct transmission, before and after the frame, specialized bit sequences are inserted and the calculated checksum is added. When the frame reaches the destination, the checksum of the already arrived data is calculated again, if it matches the checksum in the frame, the frame is recognized as correct. Otherwise, an error appears that can be corrected by re-transmission of information.

The channel stage makes it possible to transfer information, thanks to a special structure of links. In particular, buses, bridges, switches work through the link-level protocols. The second step specifications include Ethernet, Token Ring, and PPP. The functions of the channel stage in the computer are performed by network adapters and their drivers.
Network layer
In standard situations, the channel stage functions are not enough for high-quality information transfer. The specifications of the second step can only transfer data between nodes with the same topology, for example, a tree. There is a need for the third stage. It is necessary to form a unified transport system with a branched structure for several networks with an arbitrary structure and differing in the method of data transfer.

In other words, the third step processes the Internet protocol and acts as a router: finding the best path for information. A router is a device that collects data about the structure of interconnection and forwards packets to the destination network (transit transmissions - hops). If you encounter an error in the IP address, then this is a problem at the network level. The third stage protocols are broken down into network, routing or address resolution: ICMP, IPSec, ARP, and BGP.
Transport layer
In order for the data to reach applications and the upper levels of the stack, a fourth stage is required. It provides the required degree of information transmission reliability. There are five classes of transport services. Their difference lies in the urgency, the feasibility of restoring the interrupted communication, the ability to detect and correct transmission errors. For example, packet loss or duplication.

How to choose the class of services of the transport stage? When the quality of communication channels is high, a lightweight service will be an adequate choice. If communication channels at the very beginning work unsafely, it is advisable to resort to a developed service that will provide maximum opportunities for finding and solving problems (data delivery control, delivery timeouts). Stage 4 specifications: TCP and UDP stack TCP / IP, SPX stack Novell.
The union of the first four levels is called the transport subsystem. It fully provides the selected quality level.
Session level
The fifth stage helps in regulating dialogues. It is impossible for the interlocutors to interrupt each other or speak synchronously. The session layer remembers the active side at a specific moment and synchronizes information, coordinating and maintaining connections between devices. Its functions allow you to return to a checkpoint during a long transfer and not start over. Also, at the fifth stage, you can terminate the connection when the exchange of information is completed. Session-level specifications: NetBIOS.

Representative level
The sixth stage is involved in transforming data into a universal recognizable format without changing the content. Since different devices utilize different formats, the information processed at the representative level makes it possible for systems to understand each other, overcoming syntactic and code differences. In addition, at the sixth stage, it becomes possible to encrypt and decrypt data, which ensures secrecy. Examples of protocols: ASCII and MIDI, SSL.

Application level
The seventh stage on our list and the first if the program sends data over the network. Consists of a set of specifications, through which the user, Web pages. For example, when sending messages by mail, it is at the application level that a convenient protocol is selected. The composition of the specifications for the seventh stage is very diverse. For example, SMTP and HTTP, FTP, TFTP or SMB.
You may hear somewhere about the eighth level of the ISO model. Officially, it does not exist, but a comic eighth stage has appeared among IT workers. This is due to the fact that problems can arise through the fault of the user, and as you know, a person is at the top of evolution, so the eighth level appeared.

Having looked at the OSI model, you were able to understand the complex structure of the network, and now you understand the essence of your work. It gets pretty simple when the process is broken down!
Let's look at the purpose of the levels of the osi reference model in this article, with a detailed description of each of the seven levels of the model.
The process of organizing the principle of network interaction, in computer networks, is a rather complex and difficult task, therefore, to accomplish this task, we decided to use a well-known and universal approach - decomposition.
Decomposition is a scientific method that uses the division of one complex problem into several simpler problems - series (modules), interconnected.
Layered approach:
- all modules are split into separate groups and sorted by levels, thereby creating a hierarchy;
- modules of the same level to carry out their tasks sends requests only to modules of the immediately adjacent lower level;
- the principle of encapsulation is turned on - the level provides a service, hiding the details of its implementation from other levels.
The International Standards Organization (ISO, created in 1946) was entrusted with the task of creating a universal model that would clearly delineate and define the various levels of interaction between systems, with named levels and giving each level its specific task. This model was named open systems interaction model (Open System Interconnection, OSI) or iSO / OSI model .
The Open Systems Interconnection Reference Model (osi seven-level model) was introduced in 1977.
After the approval of this model, the problem of interaction was divided (decomposed) into seven particular problems, each of which can be solved independently of the others.
OSI Reference Model Layers are a vertical structure where all network functions are divided between seven levels. It should be emphasized that strictly described operations, equipment and protocols correspond to each such level.
The interaction between the levels is organized as follows:
- vertically - inside a separate computer and only with adjacent levels.
- horizontally - logical interaction is organized - with the same level of another computer at the other end of the communication channel (that is, the network level on one computer interacts with the network level on another computer).
Since the seven-level osi model consists of a strict subordinate structure, any higher level uses the functions of the lower level, and it recognizes in which form and in what way (i.e. through which interface) the data stream needs to be transmitted to it.

Let us consider how the transmission of messages over a computer network is organized in accordance with the OSI model. The application layer is the application layer, that is, this level is displayed to the user in the form of the operating system used and the programs with which data is sent. At the very beginning, it is the application layer that forms the message, then it is transmitted to the representative layer, that is, it goes down the OSI model. The representative level, in turn, analyzes the header of the application level, performs the required actions, and adds its service information to the beginning of the message, in the form of a header of the representative level, for the representative level of the destination node. Further, the movement of the message continues down, descends to the session layer, and it, in turn, also adds its service data, in the form of a header at the beginning of the message, and the process continues until it reaches the physical layer.
It should be noted that in addition to adding service information in the form of a header at the beginning of the message, layers can add service information at the end of the message, which is called the "trailer".
When the message has reached the physical layer, the message is already fully formed for transmission over the communication channel to the destination node, that is, it contains all the service information added at the layers of the OSI model.

In addition to the term "data", which is used in the OSI model at the application, presentation, and session layers, other terms are used in other layers of the OSI model so that you can immediately determine at which layer of the OSI model processing is performed.
In ISO standards, to designate a particular piece of data with which the protocols of different layers of the OSI model work, a common name is used - Protocol Data Unit (PDU). To designate blocks of data of certain layers, special names are often used: frame, packet, segment.

Physical layer functions

- at this level, connector types and pin assignments are standardized;
- defines how "0" and "1" are represented;
- the interface between the network medium and the network device (transmits electrical or optical signals to a cable or radio air, receives them and converts them into data bits);
- physical layer functions are implemented in all devices connected to the network;
- equipment operating at the physical level: hubs;
- Examples of physical layer network interfaces: RS-232C, RJ-11, RJ-45, AUI connectors, BNC.
Link layer functions

- 0s and 1s of the Physical layer are organized into frames - "frame". A frame is a chunk of data that has an independent logical value;
- organization of access to the transmission medium;
- handling data transmission errors;
- defines the structure of links between nodes and how they are addressed;
- equipment operating at the link level: switches, bridges;
- examples of protocols related to the data link layer: Ethernet, Token Ring, FDDI, Bluetooth, Wi-Fi, Wi-Max, X.25, FrameRelay, ATM.
For a LAN, the link layer is divided into two sublevels:
- LLC (LogicalLinkControl) —responsible for establishing a communication channel and for error-free sending and receiving data messages;
- MAC (MediaAccessControl) - provides sharing of network adapters to the physical layer, definition of frame boundaries, recognition of destination addresses (for example, access to a common bus).

Network layer functions

- Performs functions:
- determining the data transmission path;
- determining the shortest route;
- monitoring network problems and congestion.
- Solves tasks:
- transmission of messages through links with a non-standard structure;
- coordination of different technologies;
- simplification of addressing in large networks;
- creating barriers to unwanted traffic between networks.
- Equipment operating at the network level: router.
- Types of network layer protocols:
- network protocols (forwarding packets through the network:, ICMP);
- routing protocols: RIP, OSPF;
- address Resolution Protocols (ARP)
Osi transport functions

- provides applications (or application and session layers) with data transmission with the required degree of reliability, compensates for the lack of reliability of lower levels;
- multiplexing and demultiplexing i.e. collection and disassembly of packages;
- protocols are designed for point-to-point communication;
- starting from this level, the protocols are implemented by the software of the end nodes of the network - the components of their network OS;
- examples: TCP, UDP protocols.
Session layer functions

- maintaining a communication session, allowing applications to interact with each other for a long time;
- session creation / termination;
- information exchange;
- synchronization of tasks;
- determination of the right to data transfer;
- maintaining a session during periods of inactivity of applications.
- transmission synchronization is ensured by placing checkpoints into the data stream, from which the process resumes in case of failures.
Representative level functions

- responsible for protocol conversion and data encoding / decoding. It converts application requests received from the application layer into a format for transmission over the network, and converts the data received from the network into a format that applications can understand;
- possible implementation:
- compress / decompress or encode / decode data;
- redirecting requests to another network resource if they cannot be processed locally.
- example: sSL protocol (provides secret messaging for the TCP / IP application layer protocols).
Osi model application layer functions

- is a set of various protocols through which network users gain access to shared resources, organize collaboration;
- provides interaction between the network and the user;
- allows user applications to access network services such as database query processor, file access, e-mail forwarding;
- responsible for the transfer of service information;
- provides applications with error information;
- example: HTTP, POP3, SNMP, FTP.
Network-independent and network-independent layers of the seven-tier osi model
In terms of their functionality, the seven layers of the OSI model can be classified into one of two groups:
- a group in which the levels depend on the specific technical implementation of the computer network. Physical, data link and network layers are network dependent, in other words, these layers are inextricably linked with the specific network equipment used.
- a group in which the levels are mainly focused on working with applications. Session, representative and application levels are focused on the applications used and practically do not depend on what kind of network equipment is used in a computer network, that is, network independent.

The OSI network model is a reference model for open systems interconnection; in English it sounds like the Open Systems Interconnection Basic Reference Model. Its purpose in a generalized view of networking tools.
That is, the OSI model is a generalized standard for software developers, thanks to which any computer can equally decrypt data transmitted from another computer. To make it clear, I will give a life example. It is known that bees see everything around them in the morning violet light. That is, our eyes and bees perceive the same picture in completely different ways, and what insects see may be imperceptible to human vision.
The same is the case with computers - if one developer writes an application in any programming language that his own computer understands, but is not available to any other, then on any other device you will not be able to read the document created by this application. Therefore, we came up with the idea to follow a single set of rules, understandable for everyone, when writing applications.
OSI layers
For clarity, the process of network operation is usually divided into 7 levels, each of which has its own group of protocols.
The network protocol is the rules and technical procedures that enable computers on a network to communicate and exchange data.
A group of protocols united by a single end goal is called a protocol stack.
There are several protocols for performing different tasks that are involved in maintaining systems, such as the TCP / IP stack. Let's take a closer look here at how information from one computer is sent over the local network to another computer.
Tasks of the SENDER computer:
- Take data from application
- Break them into small packages if large volume
- Prepare for transmission, that is, indicate the route to follow, encrypt and re-encode to network format.
Tasks of the RECIPIENT's computer:
- Accept data packets
- Remove service information from it
- Copy data to clipboard
- After complete reception of all packets, form the original data block from them
- Give it to the application
In order to correctly perform all these operations, a single set of rules is needed, that is, the OSI reference model.
Let's go back to the OSI layers. It is customary to count them in reverse order and in the upper part of the table are network applications, and in the lower - the physical medium of information transmission. As data travels down from the computer directly to the network cable, protocols at different layers gradually transform it in preparation for physical transmission.
Let's analyze them in more detail.
7. Application Layer
Its task is to take data from the network application and send it to the 6th level.
6. Presentation Layer
Translates this data into a single universal language. The fact is that each computer processor has its own data processing format, but they must get into the network in one universal format - this is what the presentation layer does.
5. Session Layer
He has many tasks.
- Establish a communication session with the recipient. The software alerts the receiving computer that data will be sent to it.
- Name recognition and protection takes place here:
- identification - name recognition
- authentication - password check
- registration - assignment of powers
- Implementation of which side carries out the transfer of information and how long it will take.
- Arrangement of checkpoints in the general data flow so that in case of loss of some part it is easy to establish which part is lost and should be sent again.
- Segmentation is a breakdown of a large block into small packages.

4. Transport Layer
Provides applications with the required degree of protection when delivering messages. There are two groups of protocols:
- Protocols that are connection oriented - they track the delivery of data and, if necessary, request re-sending on failure. This is TCP - the information transfer control protocol.
- Connectionless (UDP) - they simply send blocks and no longer track their delivery.
3. Network Layer
Provides end-to-end transmission of a packet by calculating its route. At this level, in packets, the IP addresses of the sender and the recipient are added to all previous information generated by other levels. From this moment on, the data packet is called the PACKAGE itself, which has \u003e\u003e IP addresses (IP protocol is an internetworking protocol).
2. Data Link Layer
Here the packet is transmitted within one cable, that is, one local network. It only works up to the edge router of one LAN. To the received packet, the link layer adds its own header - the MAC addresses of the sender and receiver, and in this form the data block is already called FRAME.

When transmitted outside one local network, the packet is assigned the MAC not of the host (computer), but of the router of the other network. Hence, the question of gray and white IP appears, which was discussed in the article to which the link was given above. Gray is an address within one local network that is not used outside of it. White is a unique address throughout the global Internet.
When a packet arrives at the border router, the IP packet is replaced with the IP of this router and the entire local network goes to the global, that is, the Internet, under one single IP address. If the address is white, then the part of the data with the IP address does not change.

1. Physical layer (Transport layer)
Responsible for converting binary information into a physical signal, which is sent to the physical data transmission channel. If it is a cable, then the signal is electrical, if it is an optical fiber network, then it is an optical signal. This conversion is carried out using a network adapter.

Protocol stacks
TCP / IP is a protocol stack that controls the transmission of data both on the local network and on the global Internet. This stack contains 4 layers, that is, according to the OSI reference model, each of them combines several layers.

- Applied (according to OSI - applied, presentation and session)
The following protocols are responsible for this level:- TELNET - remote communication session as a command line
- FTP - File Transfer Protocol
- SMTP - Mail Transfer Protocol
- POP3 and IMAP - receiving mail
- HTTP - working with hypertext documents
- Transport (according to OSI the same) is the TCP and UDP already described above.
- Internet (according to OSI - network) is an IP protocol
- Network interface layer (OSI - channel and physical) Network adapter drivers are responsible for the operation of this layer.
Data block terminology
- Stream - the data that is operated at the application level
- A datagram is a data block at the output from a UPD, that is, which does not have a guaranteed delivery.
- Segment - a block guaranteed for delivery at the output from the TCP protocol
- A packet is a block of data output from the IP protocol. since at this level it is not yet guaranteed for delivery, it can also be called a datagram.
- A frame is a block with assigned MAC addresses.
For a unified representation of data in networks with heterogeneous devices and software, the International Standardization Organization (ISO) has developed a basic communication model for open systems OSI (Open System Interconnection). This model describes the rules and procedures for transmitting data in various network environments when establishing a communication session. The main elements of the model are layers, application processes, and physical connectivity. In fig. 1.10 shows the structure of the basic model.
Each layer of the OSI model performs a specific task in the process of transmitting data over the network. The basic model is the basis for the development of network protocols. OSI divides communication functions on a network into seven layers, each of which serves a different part of the open systems interconnection process.
The OSI model describes only system communications, not end-user applications. Applications implement their own communication protocols by accessing system tools.
Figure: 1.10. OSI model
If an application can take over the functions of some of the upper layers of the OSI model, then for data exchange it accesses the system tools that perform the functions of the remaining lower layers of the OSI model.
OSI Model Layer Interaction
The OSI model can be categorized into two different models, as shown in Fig. 1.11:
A horizontal protocol-based model that provides a mechanism for the interaction of programs and processes on different machines;
A vertical model based on services provided by adjacent layers to each other on the same machine.
Each level of the sending computer interacts with the same level of the receiving computer as if it were directly connected. Such a link is called a logical or virtual link. In reality, communication takes place between adjacent levels of the same computer.
So, the information on the sending computer must pass through all levels. Then it is transmitted through the physical medium to the receiving computer and again goes through all the layers until it reaches the same level from which it was sent on the sending computer.
In the horizontal model, the two programs require a common protocol to communicate. In the vertical model, adjacent layers communicate using APIs (Application Programming Interface).

Figure: 1.11. Diagram of the interaction of computers in the OSI basic reference model
The data is split into packets before being sent to the network. A packet is a unit of information transmitted between stations on a network.
When sending data, the packet goes sequentially through all layers of the software. At each level, control information of this level (header) is added to the packet, which is necessary for the successful transmission of data over the network, as shown in Fig. 1.12, where Zag is the packet header, Kon is the end of the packet.
On the receiving side, the packet goes through all the layers in reverse order. At each layer, the protocol of this layer reads the packet information, then removes the information added to the packet at the same level by the sending side, and passes the packet to the next layer. When the package reaches the Application layer, all control information will be removed from the package, and the data will return to its original form.

Figure: 1.12. Formation of the package of each level of the seven-level model
Each level of the model has its own function. The higher the level, the more difficult the problem it solves.
It is convenient to think of the individual layers of the OSI model as groups of programs designed to perform specific functions. One layer, for example, is responsible for ensuring the conversion of data from ASCII to EBCDIC and contains the programs required to accomplish this task.
Each layer provides a service to the higher layer, requesting in turn the service from the lower layer. The upper layers request the service in almost the same way: as a rule, this is the requirement to route some data from one network to another. The practical implementation of the principles of data addressing is assigned to the lower levels. In fig. 1.13 provides a brief description of the functions of all levels.

Figure: 1.13. OSI model layer functions
The considered model defines the interaction of open systems of different manufacturers in the same network. Therefore, she performs coordinating actions for them on:
Interaction of applied processes;
Data presentation forms;
Uniform data storage;
Network resource management;
Data security and information protection;
Diagnostics of programs and hardware.
Application layer
The application layer provides application processes with means of access to the interaction area, is the upper (seventh) level and directly adjoins the application processes.
In reality, the application layer is a collection of different protocols that allow network users to access shared resources such as files, printers, or hypertext Web pages, and organize their collaboration, such as using the e-mail protocol. Application-specific service elements provide a service for specific application programs such as file transfer and terminal emulation programs. If, for example, a program needs to send files, then the file transfer, access and management protocol FTAM (File Transfer, Access, and Management) will be used. In the OSI model, an application that needs to perform a specific task (for example, update a database on a computer) sends specific data as a Datagram to the application layer. One of the main tasks of this layer is to determine how an application's request should be handled, in other words, what kind of request a given request should accept.
The unit of data that the application layer operates on is usually called a message.
The application layer performs the following functions:
1. Performing various types of work.
File transfer;
Job management;
System management, etc.
2. Identification of users by their passwords, addresses, electronic signatures;
3. Determination of functioning subscribers and the possibility of access to new application processes;
4. Determination of the adequacy of the available resources;
5. Organization of requests for connection with other application processes;
6. Transfer of applications to the representative level for the necessary methods of describing information;
7. Selection of procedures for the planned dialogue of processes;
8. Management of data exchanged by application processes and synchronization of interaction of application processes;
9. Determination of the quality of service (delivery time of data blocks, permissible error rate);
10. Agreement on error correction and data validation;
11. Negotiation of restrictions imposed on syntax (character sets, data structure).
These functions define the types of services that the application layer provides to application processes. In addition, the application layer transfers to the application processes the service provided by the physical, channel, network, transport, session and presentation layers.
At the application level, it is necessary to provide users with the processed information. System and user software can handle this.
The application layer is responsible for the access of applications to the network. The tasks of this layer are file transfer, e-mail exchange, and network management.
The most common protocols of the upper three layers are:
FTP (File Transfer Protocol) file transfer protocol;
TFTP (Trivial File Transfer Protocol) is the simplest file transfer protocol;
X.400 email;
Telnet work with a remote terminal;
SMTP (Simple Mail Transfer Protocol) is a simple mail exchange protocol;
CMIP (Common Management Information Protocol) general information management protocol;
SLIP (Serial Line IP) IP for serial lines. Serial character-by-character data transfer protocol;
SNMP (Simple Network Management Protocol) is a simple network management protocol;
FTAM (File Transfer, Access, and Management) is a file transfer, access and management protocol.
Presentation layer
The functions of this level are the presentation of data transferred between application processes in the required form.
This layer ensures that the information conveyed by the application layer will be understood by the application layer in another system. If necessary, the presentation layer, at the time of information transmission, converts the data formats into a certain common presentation format, and at the time of reception, accordingly, performs the reverse transformation. In this way, application layers can overcome, for example, syntactic differences in data presentation. This situation can arise on a LAN with heterogeneous computers (IBM PC and Macintosh) that need to communicate. Thus, in the fields of databases, information should be presented in the form of letters and numbers, and often in the form of a graphic image. You need to process this data, for example, as floating point numbers.
The general presentation of data is based on the ASN.1 system unified for all levels of the model. This system serves to describe the structure of files, and also allows you to solve the problem of data encryption. At this level, data encryption and decryption can be performed, thanks to which the secrecy of data exchange is ensured immediately for all application services. An example of such a protocol is Secure Socket Layer (SSL), which provides secure messaging for the application layer protocols of the TCP / IP stack. This layer provides data conversion (encoding, compression, etc.) of the application layer into a stream of information for the transport layer.
The representative level performs the following main functions:
1. Generation of requests to establish sessions of interaction between application processes.
2. Coordination of data presentation between application processes.
3. Implementation of data presentation forms.
4. Presentation of graphic material (drawings, pictures, diagrams).
5. Classification of data.
6. Transfer of requests to terminate sessions.
Presentation layer protocols are usually part of the top three model layer protocols.
Session layer
The session layer is the layer that defines the procedure for conducting sessions between users or application processes.
The session layer provides control of the conversation in order to record which side is currently active, and also provides a means of synchronization. The latter allow breakpoints to be inserted into long transmissions so that in the event of a failure, you can go back to the last breakpoint instead of starting over. In practice, few applications use the session layer and it is rarely implemented.
The session layer manages the transfer of information between application processes, coordinates the reception, transmission and delivery of one communication session. In addition, the session layer additionally contains the functions of password management, dialog management, synchronization and cancellation of communication in the transmission session after failure due to errors in the lower layers. The functions of this layer are to coordinate communication between two applications running on different workstations. This happens in the form of a well-structured dialogue. These features include creating a session, controlling the transmission and reception of message packets during a session, and ending a session.
At the session level, it is determined what the transfer will be between two application processes:
Half-duplex (processes will transmit and receive data in turn);
Duplex (processes will transmit data and receive them at the same time).
In half-duplex mode, the session layer issues a data token to the process that starts the transfer. When the time comes for the second process to respond, a data token is passed to it. The session layer allows transmission only to the side that possesses the data token.
The session layer provides the following functions:
1. Establishment and termination at the session level of connections between interacting systems.
2. Performing normal and urgent data exchange between application processes.
3. Management of interaction of applied processes.
4. Synchronization of session connections.
5. Notifying application processes of exceptional situations.
6. Establishing labels in the application process that allow, after a failure or an error, to restore its execution from the nearest label.
7. Interruption, if necessary, of the application process and its correct resumption.
8. Termination of the session without data loss.
9. Sending special messages about the course of the session.
The session layer is responsible for organizing data exchange sessions between end machines. Session protocols are usually part of the top three layers of the model.
Transport Layer
The transport layer is designed for the transmission of packets over a communication network. At the transport level, packets are split into blocks.
On the way from sender to receiver, packets can be garbled or lost. While some applications have their own error handling facilities, there are others that prefer to deal with a reliable connection straight away. The job of the transport layer is to ensure that applications or the upper layers of the model (application and session) transfer data with the degree of reliability they require. The OSI model defines five classes of service provided by the transport layer. These types of services are distinguished by the quality of the services provided: urgency, the ability to restore an interrupted connection, the availability of multiplexing means for multiple connections between different application protocols through a common transport protocol, and most importantly, the ability to detect and correct transmission errors such as distortion, loss and duplication of packets.
The transport layer defines the addressing of physical devices (systems, their parts) in the network. This layer guarantees the delivery of blocks of information to the addressees and controls this delivery. Its main task is to provide efficient, convenient and reliable forms of information transfer between systems. When more than one packet is being processed, the transport layer controls the order in which the packets pass. If a duplicate of a previously received message passes, then this layer recognizes this and ignores the message.
The transport layer functions include:
1. Management of transmission over the network and ensuring the integrity of data blocks.
2. Detection of errors, their partial elimination and reporting of uncorrected errors.
3. Restoration of transmission after failures and malfunctions.
4. Consolidation or separation of data blocks.
5. Granting of priorities when transferring blocks (normal or urgent).
6. Confirmation of Transfer.
7. Elimination of blocks in case of deadlocks in the network.
Starting with the transport layer, all of the overlying protocols are implemented by software, usually included in the network operating system.
The most common transport layer protocols include:
TCP (Transmission Control Protocol) TCP / IP stack transmission control protocol;
UDP (User Datagram Protocol) is the TCP / IP stack's datagram protocol;
NCP (NetWare Core Protocol) is the basic protocol for NetWare networks;
SPX (Sequenced Packet eXchange) Sequenced packet exchange of the Novell stack;
TP4 (Transmission Protocol) is a class 4 transmission protocol.
Network Layer
The network layer provides the laying of channels connecting subscriber and administrative systems through the communication network, the choice of the route of the fastest and most reliable way.
The network layer establishes communication in a computer network between two systems and provides the laying of virtual channels between them. A virtual or logical channel is the operation of network components that creates the illusion of laying the necessary path between them for interacting components. In addition, the network layer reports errors to the transport layer. Network layer messages are commonly referred to as packets. Chunks of data are placed in them. The network layer is responsible for their addressing and delivery.
Placing the best path for data transmission is called routing, and its solution is the main task of the network layer. This problem is compounded by the fact that the shortest path is not always the best. Often a criterion for choosing a route is the time of data transmission along that route; it depends on the bandwidth of the communication channels and the traffic rate, which can change over time. Some routing algorithms try to adapt to changes in load, while others make decisions based on averages over time. Route selection can be carried out according to other criteria, for example, transmission reliability.
The link layer protocol ensures the delivery of data between any nodes only in a network with a corresponding typical topology. This is a very severe limitation that does not allow building networks with a developed structure, for example, networks that combine several enterprise networks into a single network, or highly reliable networks in which there are redundant connections between nodes.
Thus, within the network, data delivery is regulated by the data link layer, while the network layer is responsible for delivering data between networks. When organizing packet delivery at the network level, the concept of a network number is used. In this case, the recipient's address consists of a network number and a computer number on that network.
Networks are interconnected by special devices called routers. A router is a device that collects information about the topology of interconnection and, based on it, forwards network layer packets to the destination network. In order to transfer a message from a sender located in one network to a recipient located in another network, you need to make a certain number of hops between the networks, each time choosing a suitable route. Thus, a route is a sequence of routers through which a packet travels.
The network layer is responsible for dividing users into groups and routing packets based on the translation of MAC addresses into network addresses. The network layer also provides transparent transmission of packets to the transport layer.
The network layer performs the functions:
1. Creation of network connections and identification of their ports.
2. Detection and correction of errors occurring during transmission through the communication network.
3. Packet flow control.
4. Organization (ordering) of sequences of packets.
5. Routing and switching.
6. Segmentation and consolidation of packages.
At the network level, two kinds of protocols are defined. The first type refers to the definition of rules for the transfer of packets with data of end nodes from node to router and between routers. These are the protocols that are commonly referred to when talking about network layer protocols. However, another type of protocol is often referred to as the network layer, called routing information exchange protocols. Routers use these protocols to collect information about the topology of interconnection.
Network layer protocols are implemented by operating system software modules, as well as by software and hardware of routers.
The most commonly used protocols at the network level are:
IP (Internet Protocol) Internet Protocol, a network protocol of the TCP / IP stack that provides address and routing information;
IPX (Internetwork Packet Exchange) is an Internet packet exchange protocol designed for addressing and routing packets in Novell networks;
X.25 is an international standard for global packet-switched communications (this protocol is partially implemented at layer 2);
CLNP (Connection Less Network Protocol) is a connectionless network protocol.
Data Link
The unit of information of the link layer is frames (frame). Frames are a logically organized structure into which data can be placed. The task of the data link layer is to transfer frames from the network layer to the physical layer.
At the physical layer, bits are simply transferred. This does not take into account that in some networks, in which communication lines are used alternately by several pairs of interacting computers, the physical transmission medium may be busy. Therefore, one of the tasks of the link layer is to check the availability of the transmission medium. Another task of the data link layer is to implement error detection and correction mechanisms.
The link layer ensures that each frame is transmitted correctly by placing a special sequence of bits at the beginning and end of each frame to mark it, and also calculates a checksum by summing all the bytes of the frame in a specific way and adding the checksum to the frame. When a frame arrives, the receiver computes the checksum of the received data again and compares the result with the checksum from the frame. If they match, the frame is considered correct and accepted. If the checksums do not match, then an error is recorded.
The task of the link layer is to take packets coming from the network layer and prepare them for transmission, putting them in a frame of the appropriate size. This layer is required to determine where the block begins and ends, and also to detect transmission errors.
At the same level, the rules for using the physical layer by network nodes are determined. The electrical representation of data in the LAN (data bits, data encoding methods and markers) are recognized at this and only at this level. This is where errors are detected and corrected (through retransmission requests).
The link layer provides creation, transmission and reception of data frames. This layer serves network layer requests and uses the physical layer service to receive and transmit packets. IEEE 802.X specifications divide the data link layer into two sublayers:
LLC (Logical Link Control) Logical Link Control performs logical link control. The LLC sublayer provides network layer services and is associated with sending and receiving user messages.
MAC (Media Assess Control) media access control. The MAC sublayer regulates access to the shared physical medium (token passing or collision or collision detection) and controls access to the communication channel. The LLC sublayer is above the MAC sublayer.
The link layer defines media access and transmission control through a data link procedure.
When the size of the transmitted data blocks is large, the link layer divides them into frames and transmits the frames in the form of sequences.
When receiving frames, the layer forms the transmitted data blocks from them. The size of the data block depends on the transmission method, the quality of the channel over which it is transmitted.
In local area networks, link layer protocols are used by computers, bridges, switches, and routers. In computers, link layer functions are implemented jointly by network adapters and their drivers.
The link layer can perform the following types of functions:
1. Organization (establishment, management, termination) of channel connections and identification of their ports.
2. Organization and transfer of personnel.
3. Detection and correction of errors.
4. Data flow control.
5. Ensuring the transparency of logical channels (transmission of data encoded in any way).
The most commonly used link layer protocols include:
HDLC (High Level Data Link Control) high-level data link control protocol for serial connections;
IEEE 802.2 LLC (Type I and Type II) provide MAC for 802.x environments;
Ethernet networking technology according to the IEEE 802.3 standard for networks using a bus topology and shared access with carrier listening and collision detection;
Token ring network technology according to the IEEE 802.5 standard using a ring topology and a token passing method of access to the ring;
FDDI (Fiber Distributed Date Interface Station) is an IEEE 802.6 networking technology using fiber optic media;
X.25 is an international standard for global packet-switched communications;
Frame relay network, organized from X25 and ISDN technologies.
Physical Layer
The physical layer is designed to interface with physical connectivity. Physical connectivity is the collection of physical media, hardware, and software that transfers signals between systems.
The physical environment is a material substance through which signals are transmitted. The physical environment is the foundation upon which physical connectivity is built. Ether, metals, optical glass and quartz are widely used as a physical medium.
The physical layer consists of a Medium Docking Sublayer and a Transmission Conversion Sublayer.
The first of them provides the interface of the data stream with the used physical communication channel. The second one performs transformations related to the applied protocols. The physical layer provides a physical interface to the data channel, and also describes the procedures for transmitting signals to and from the channel. This level defines the electrical, mechanical, functional and procedural parameters for physical communication in systems. The physical layer receives data packets from the upper link layer and converts them into optical or electrical signals corresponding to 0 and 1 of the binary stream. These signals are sent through the transmission medium to the receiving node. The mechanical and electrical / optical properties of the transmission medium are determined at the physical level and include:
Type of cables and connectors;
Pinout in connectors;
Signal coding scheme for values \u200b\u200b0 and 1.
The physical layer performs the following functions:
1. Establishment and disconnection of physical connections.
2. Signal transmission in serial code and reception.
3. Listening, if necessary, channels.
4. Identification of channels.
5. Notification of malfunctions and failures.
Notification of faults and failures is due to the fact that a certain class of events is detected at the physical level that interfere with the normal operation of the network (collision of frames sent by several systems at once, channel break, power outage, loss of mechanical contact, etc.). The types of service provided to the data link layer are determined by the physical layer protocols. Listening to a channel is necessary when a group of systems is connected to one channel, but only one of them is allowed to transmit signals at the same time. Therefore, listening to the channel allows you to determine if it is free for transmission. In some cases, for a clearer definition of the structure, the physical layer is divided into several sublevels. For example, the physical layer of a wireless network is divided into three sublevels (Figure 1.14).

Figure: 1.14. Wireless LAN Physical Layer
Physical layer functions are implemented in all devices connected to the network. From the computer side, the physical layer functions are performed by the network adapter. Repeaters are the only type of equipment that only works at the physical layer.
The physical layer can provide both asynchronous (serial) and synchronous (parallel) transmission, which is used for some mainframes and mini-computers. At the Physical Layer, an encoding scheme must be defined to represent binary values \u200b\u200bfor transmission over a communication channel. Many local area networks use Manchester encoding.
An example of a physical layer protocol is the 10Base-T Ethernet specification, which defines the cable to be used as an unshielded twisted pair of category 3 with a characteristic impedance of 100 ohms, an RJ-45 connector, a maximum length of a physical segment of 100 meters, a Manchester code for data representation, and other characteristics. environment and electrical signals.
Some of the most common physical layer specifications are:
EIA-RS-232-C, CCITT V.24 / V.28 - mechanical / electrical characteristics of an unbalanced serial interface;
EIA-RS-422/449, CCITT V.10 - Balanced Serial Interface Mechanical, Electrical and Optical Characteristics;
Ethernet is an IEEE 802.3 networking technology for networks using a bus topology and shared access with carrier listening and collision detection;
Token ring is an IEEE 802.5 network technology that uses a ring topology and a token passing method of accessing the ring.
Network model OSI (the basic reference model for the interaction of open systems, English Open Systems Interconnection Basic Reference Model) - an abstract network model for communications and the development of network protocols.
The model consists of 7 levels located one above the other. The layers interact with each other (“vertically”) through interfaces, and can interact with the parallel layer of another system (“horizontally”) using protocols. Each level can interact only with its neighbors and perform the functions assigned only to it. Despite the existence of other models, most network vendors today are developing their products around this structure.
OSI layers
Each layer of the OSI model is responsible for part of the processing of preparing data for transmission over the network.
In the OSI model, during transmission, data literally travels from top to bottom through the OSI layers of the sending computer and up through the OSI layers of the receiving computer. On the receiving computer, the reverse of the encapsulation process takes place. The bits arrive at the physical layer of the OSI model of the receiving computer. In the process of moving up the OSI layers of the receiving computer, the data will go to the application layer.
| Level | Name | Description 1 | Description 2 |
| 7. | Applied | This is the level at which the end product users work. They don't care how the data is transmitted, why and through what place ... They said "I WANT!" - and we, programmers, must provide them with this. Any network game can be taken as an example: for the player it works at this level. | When a user wants to send data, such as email, the encapsulation process begins at the application layer. The application layer is responsible for providing network access to applications. Information travels through the top three levels and, when it gets down to the transport layer, is considered data. |
| 6. | Executive (Introduction to XML, SMB) | Here the programmer deals with data received from lower levels. Basically, this is the conversion and presentation of data in a form that is digestible for the user. | |
| 5. | Session (TLS, SSL certificates for website, mail, NetBios) | This layer allows users to conduct "communication sessions". That is, it is at this level that the transfer of packets becomes transparent for the programmer, and he can, without thinking about implementation, directly transfer data as a single stream. This is where HTTP, FTP, Telnet, SMTP, and more come into play. | |
| 4. | Transport (TCP, UDP ports) | Carries out control over the transmission of data (network packets). That is, it checks their integrity during transmission, distributes the load, etc. This layer implements protocols such as TCP, UDP, etc. It is of the greatest interest to us. | At the transport layer, data is broken up into more manageable segments, or transport PDUs, for orderly transport over the network. A PDU describes data as it moves from one layer of the OSI model to another. In addition, the transport PDU contains information such as port numbers, sequence numbers, and handshake numbers that are used to securely transport data. |
| 3. | Network (IP, ICMP Network Congestion Diagnostic Protocol) | Logically controls network addressing, routing, etc. Should be of interest to developers of new protocols and standards. At this level, the protocols IP, IPX, IGMP, ICMP, ARP are implemented. Mainly driven by drivers and operating systems. Of course, it's worth getting in here, but only when you know what you are doing and are completely confident in yourself. | At the network layer, every segment that arrives from the transport layer becomes a packet. The packet contains logical addressing and other layer 3 control data. |
| 2. | Channel (WI-FI, What is Ethernet) | This level controls the perception of electronic signals by the logic (radio electronic elements) of the hardware devices. That is, by interacting at this level, the hardware converts the bit stream into electrical signals and vice versa. We are not interested in it, because we do not develop hardware, chips, etc. The layer concerns network cards, bridges, switches, routers, etc. | At the data link layer, every packet from the network layer becomes a frame. The frame contains the physical address and error correction data. |
| 1. | Hardware (Physical) (laser, electricity, radio) | Controls the transmission of physical signals between hardware devices on the network. That is, it controls the transfer of electrons through wires. We are not interested in it, because everything at this level is controlled by hardware (the implementation of this level is the task of manufacturers of hubs, multiplexers, repeaters and other equipment). We are not amateur radio physicists, but game developers. | At the physical level, a frame becomes bits. Bits are transmitted one at a time over the network medium. |
We see that the higher the level, the higher the degree of abstraction from data transmission to working with the data itself. This is the meaning of the entire OSI model: as we climb higher and higher on the steps of its ladder, we care less and less about how data is transmitted, we become more and more interested in the data itself, rather than in the means for transmitting it. As programmers, we are interested in levels 3, 4, and 5. We must use the tools they provide to build levels 6 and 7 that end users can work with.
Network layer
At the OSI network layer, the protocols IP (Internet Protocol Structure IPv4, IPv6), IPX, IGMP, ICMP, ARP are implemented.
You need to understand why there was a need to build a network layer, why networks built using the means of the channel and physical layers could not meet the requirements of users.
It is also possible to create a complex, structured network with the integration of various basic network technologies by means of the link layer: for this, some types of bridges and switches can be used. Naturally, in general, traffic in such a network develops randomly, but on the other hand, it is also characterized by some regularities. As a rule, in such a network, some users working on a common task (for example, employees of one department) most often make requests either to each other or to a common server, and only sometimes they need access to the resources of computers in another department. Therefore, depending on the network traffic, computers on the network are divided into groups called network segments. Computers are grouped together if most of their messages are intended (addressed) to computers of the same group. The division of the network into segments can be carried out by bridges and switches. They shield local traffic within a segment, not transmitting any frames outside of it, except for those addressed to computers located in other segments. Thus, one network is split into separate subnets. From these subnets, in the future, composite networks of rather large sizes can be built.
The idea of \u200b\u200bsubnetting is the foundation for building composite networks.
The network is called composite (internetwork or internet), if it can be represented as a collection of several networks. The networks that make up a composite network are called subnets, constituent networks, or simply networks, each of which can operate on its own link-layer technology (although this is not required).
But, bringing this idea to life with repeaters, bridges, and switches has very significant limitations and disadvantages.
In the topology of a network built using both repeaters and bridges or switches, there should be no loops. Indeed, a bridge or a switch can solve the problem of delivering a packet to the addressee only when there is only one path between the sender and the recipient. Although, at the same time, the presence of redundant links, which form loops, is often necessary for better load balancing, as well as to improve network reliability by creating redundant paths.
Logical network segments located between bridges or switches are weakly isolated from each other. They are not immune to broadcast storms. If any station sends a broadcast message, then this message is transmitted to all stations on all logical network segments. The administrator must manually limit the number of broadcast packets that a certain node is allowed to generate per unit of time. In principle, we managed to eliminate the problem of broadcast storms in some way using the virtual network mechanism (Debian D-Link VLAN Setting), implemented in many switches. But in this case, although it is possible to create quite flexible traffic-isolated groups of stations, they are completely isolated, that is, the nodes of one virtual network cannot interact with the nodes of another virtual network.
In networks built on the basis of bridges and switches, it is rather difficult to solve the problem of traffic control based on the value of the data contained in the packet. On such networks, this is only possible with custom filters, which require the administrator to deal with the binary representation of the packet contents to define them.
The implementation of the transport subsystem only by means of the physical and link layers, which include bridges and switches, leads to an insufficiently flexible, single-level addressing system: the MAC address is used as the destination station address - an address that is rigidly connected to the network adapter.
All of the above disadvantages of bridges and switches are associated only with the fact that they operate using data link-layer protocols. The point is that these protocols do not explicitly define the concept of a part of a network (or a subnet, or a segment) that could be used when structuring a large network. Therefore, the developers of network technologies decided to entrust the task of building a composite network to a new level - the network.