Viruses are spies!
Spyware is the scourge of this century. Many millions of computers in the world are infected with these spyware malware, and many do not notice it.
Spies not only harm the security of your information, but also significantly reduce the speed of your computer. When you download one of the spy software packages, this program is automatically installed on your computer, regardless of your desire. Sometimes, during installation, the spy asks you to install the sponsor software. When installing a spyware program, it seeks to install itself in the system registry of your computer and is located in it until you completely remove it from there.
A spy, devouring the potential of a computer, reduces the efficiency of the central processor and memory. As a result of this, your PC slows down or even completely stops responding. The spy will not disappear on its own, but will only cause an ever greater delay, because Spyware will continue to collect information from your computer. There are three main ways to destroy your system with spyware:
1. There are spies who constantly monitor all your purchases. If you use your credit card, you may end up missing your finances, the spy program will find out your credit card number, and will give you the opportunity to use it for purchases by other people. You may not find out about this until you find a shortage of money.
2. Hackers (those behind the scenes) will be able to access your computer and information about it. They will be able to find out which keys you use in real time, penetrate your computer, change browser settings, install their programs without your consent. In addition, spies can also collect information about email addresses, passwords and even credit card numbers. But this problem can be solved, but just look through and carefully study all the available programs for removing spyware, reviews for them, because some of them can do more harm than good.
3. Spyware can find information about your email addresses. If this happens, then you will encounter a lot of problems, one of which, you just fill up with advertising letters.
Even if you are a simple user, there are several ways you can easily do to quickly and reliably increase the speed of your computer. The first and most affordable method you should definitely do is defragment your disks. "Defragmentation wizard" on your computer will help to carry it out. You might want to do this quickly, however, it can take a long time. The process should not be interrupted. With regular work, the next test will take less time.
The second way is to install and use a good program to destroy spyware. For example, Spyware Doctor understands them well.
Then it is possible to programmatically reduce the period of saving visited pages in browsers, if you do not need it from one month, as default, to 1-2 days or to delete them immediately after leaving the page of the site.
When you deactivate your desktop, the load on RAM will become less. And you won’t feel the difference in design and work.
Make sure you have a good antivirus program, use it constantly. If you remove viruses and prevent their spread, then you noticeably speed up your computer.
Once you follow these simple rules, you will be amazed at how much faster your computer started and how much disk space is freed up.
http://www.computermaster.ru/articles/secur2.html
What you need to know about computer viruses
(c) Alexander Frolov, Grigory Frolov, 2002
[email protected]; http://www.frolov.pp.ru, http://www.datarecovery.ru
Since the creation of personal computers accessible to specialists and the general public, the history of computer viruses has begun. It turned out that personal computers and programs distributed on floppy disks represent the very “breeding ground" in which computer viruses arise and carefree live. Myths and legends that arise around the ability of computer viruses to penetrate everywhere and everywhere, envelop these malicious creatures in a fog of incomprehensible and unknown.
Unfortunately, even experienced system administrators (not to mention ordinary users) do not always accurately imagine what computer viruses are, how they penetrate computers and computer networks, and which ones can be harmful. However, without understanding the mechanism of functioning and spread of viruses, it is impossible to organize effective antivirus protection. Even the best antivirus program will be powerless if it is used incorrectly.
A short history of computer virus history
What is a computer virus?
The most general definition of a computer virus can be given as self-propagating program code in the information environment of computers. It can be embedded in executable and batch files of programs, distributed through the boot sectors of floppy disks and hard disks, documents of office applications, via e-mail, Web sites, as well as other electronic channels.
Penetrating into a computer system, a virus can limit itself to harmless visual or sound effects, and can cause loss or distortion of data, as well as leakage of personal and confidential information. In the worst case scenario, a computer system affected by a virus may be under the complete control of an attacker.
Today, people trust computers to solve many critical tasks. Therefore, the failure of computer systems can have very, very serious consequences, up to human casualties (imagine a virus in computer systems of airfield services). This should not be forgotten by the developers of information computer systems and system administrators.
Today, tens of thousands of different viruses are known. Despite this abundance, there is a fairly limited number of types of viruses that differ from each other in the mechanism of distribution and the principle of action. There are combined viruses that can be attributed to several different types simultaneously. We will talk about different types of viruses, keeping to the chronological order of their appearance.
File viruses
Historically, file viruses appeared before other types of viruses, and originally spread in the environment of the MS-DOS operating system. Introducing COM and EXE program files into the body, viruses modify them in such a way that when they start, control is transferred not to the infected program, but to the virus. The virus can write its code to the end, beginning or middle of the file (Fig. 1). The virus can also split its code into blocks by placing them in different places of the infected program.
Fig. 1. Virus in the MOUSE.COM file
After gaining control, the virus can infect other programs, infiltrate the computer’s RAM and perform other malicious functions. Next, the virus transfers control to the infected program, and it executes in the usual way. As a result, the user who runs the program does not suspect that it is “sick”.
Note that file viruses can infect not only COM and EXE programs, but also other types of program files — MS-DOS overlays (OVL, OVI, OVR and others), SYS drivers, dynamic link libraries, and any files with program code . File viruses were developed not only for MS-DOS, but also for other OSs, such as Microsoft Windows, Linux, IBM OS / 2. However, the vast majority of viruses of this type lives in the environment of MS-DOS and Microsoft Windows.
In the days of MS-DOS, file viruses lived happily thanks to the free exchange of programs, gaming and business. In those days, program files were relatively small and distributed on floppy disks. The infected program could also be accidentally downloaded from the BBS bulletin board or from the Internet. And along with these programs, file viruses also spread.
Modern programs occupy a considerable amount and are distributed, as a rule, on CDs. The exchange of programs on floppy disks has long been a thing of the past. When installing the program from a licensed CD-ROM, you usually do not run the risk of infecting your computer with a virus. Another thing is pirated CDs. You can’t vouch for anything here (although we know examples of the spread of viruses on licensed CDs as well).
As a result, today file viruses have lost the lead in popularity to viruses of other types, which we will talk about.
Boot viruses
Boot viruses receive control at the initialization stage of the computer, even before the operating system starts to boot. To understand how they work, you need to remember the sequence of initializing the computer and loading the operating system.
Immediately after turning on the power of the computer, the POST (Power On Self Test) test procedure recorded in the BIOS starts working. During the check, the computer configuration is determined and the operability of its main subsystems is checked. The POST procedure then checks to see if a diskette is inserted in drive A :. If a floppy disk is inserted, then further loading of the operating system occurs from the floppy disk. Otherwise, the download is performed from the hard drive.
When booting from a diskette, the POST procedure reads a boot record (Boot Record, BR) from it into RAM. This entry is always located in the very first sector of a floppy disk and is a small program. In addition to the program, BR contains a data structure that defines the format of the diskette and some other characteristics. Then the POST procedure transfers control to BR. Having gained control, BR proceeds directly to loading the operating system.
When booting from a hard drive, the POST procedure reads the master boot record (MBR) and writes it to the computer’s RAM. This entry contains the boot program and a partition table that describes all partitions on the hard disk. It is stored in the very first sector of the hard drive.
After reading the MBR, control is transferred to the bootstrap program just read from disk. It analyzes the contents of the partition table, selects the active partition, and reads the boot record BR of the active partition. This record is similar to the BR record of a system diskette and performs the same functions.
Now about how the boot virus "works".
When a floppy disk or computer hard drive is infected, a boot virus replaces the BR boot record or the MBR master boot record (Fig. 2). The original BR or MBR records in this case usually do not disappear (although this is not always the case). The virus copies them to one of the free sectors of the disk.

Fig. 2. Virus in boot record
Thus, the virus gains control immediately after the completion of the POST procedure. Then he, as a rule, acts according to the standard algorithm. The virus copies itself to the end of RAM, while reducing its available volume. After that, it intercepts several BIOS functions, so accessing them transfers control to the virus. At the end of the infection procedure, the virus loads the real boot sector into the computer’s RAM and transfers control to it. Then the computer boots up as usual, but the virus is already in memory and can control the operation of all programs and drivers.
Combined viruses
Combined viruses that combine the properties of file and boot viruses are very common.
An example is the OneHalf file and boot virus, widely distributed in the past. Penetrating into a computer with the MS-DOS operating system, this virus infects the master boot record. At boot time, the virus gradually encrypts sectors of the hard drive, starting with the most recent sectors. When the virus resident module is in memory, it monitors all calls to encrypted sectors and decrypts them, so that all computer software works fine. If OneHalf is simply removed from the RAM and the boot sector, then it will become impossible to correctly read the information recorded in the encrypted sectors of the disk.
When the virus encrypts half the hard drive, it displays the following message on the screen:
Dis is one half. Press any key to continue ...
After that, the virus waits for the user to press a key and continues its work
The OneHalf virus uses various mechanisms to disguise itself. It is a stealth virus and uses polymorphic algorithms for distribution. Detection and removal of the OneHalf virus is a rather complicated task that is not accessible to all anti-virus programs.
Satellite viruses
As you know, in the operating systems MS-DOS and Microsoft Windows of various versions, there are three types of files that a user can run for execution. These are BAT command or batch files, as well as COM and EXE executables. At the same time, several executable files with the same name but different name extensions can be located in the same directory at the same time.
When the user starts the program and then enters its name in the system prompt of the operating system, it usually does not indicate the file extension. What file will be executed if there are several programs in the directory with the same name but with a different name extension?
It turns out that in this case the COM file will start. If only the EXE and BAT files exist in the current directory or in the directories specified in the PATH environment variable, the EXE file will be executed.
When a satellite virus infects an EXE or BAT file, it creates another file in the same directory with the same name, but with the extension COM. The virus writes itself to this COM file. Thus, when the program starts, the first to receive control is the satellite virus, which can then launch this program, but already under its control.
Viruses in batch files
There are several viruses that can infect BAT batch files. To do this, they use a very sophisticated method. We will consider it using the BAT.Batman virus as an example. When a batch file is infected, the following text is inserted at its beginning:
@ECHO OFF REM [...] copy% 0 b.com\u003e nul b.com del b.com rem [...]
The square brackets [...] here schematically show the location of bytes, which are processor instructions or virus data. The @ECHO OFF command disables the display of the names of the executed commands. The line starting with the REM command is a comment and is not interpreted in any way.
The copy% 0 b.com\u003e nul command copies the infected batch file to the B.COM file. This file is then launched and deleted from disk by the del b.com command.
The most interesting thing is that the B.COM file created by the virus, up to a single byte, coincides with the infected batch file. It turns out that if you interpret the first two lines of the infected BAT file as a program, it will consist of CPU commands that actually do nothing. The central processor executes these instructions, and then begins to execute the real virus code recorded after the REM comment statement. Having gained control, the virus intercepts OS interruptions and activates.
During the spread process, the virus monitors the writing of data to files. If the first line written to the file contains the @echo command, then the virus considers that the batch file is being written and infects it.
Encrypted and polymorphic viruses
To make detection difficult, some viruses encrypt their code. Each time a virus infects a new program, it encrypts its own code using a new key. As a result, two copies of such a virus can significantly differ from each other, even have different lengths. Encryption of the virus code greatly complicates the process of research. Conventional programs will not be able to disassemble such a virus.
Naturally, the virus is able to work only if the executable code is decrypted. When the infected program starts (or the download starts from the infected BR boot record) and the virus takes control, it must decrypt its code.
In order to make it more difficult to detect a virus, not only different keys are used for encryption, but also different encryption procedures. Two instances of such viruses do not have any matching code sequences. Such viruses, which can completely change their code, are called polymorphic viruses.
Stealth viruses
Stealth viruses try to hide their presence on the computer. They have a resident module, permanently located in the computer's RAM. This module is installed when the infected program starts or when it boots from a disk infected with a boot virus.
The resident virus module intercepts calls to the disk subsystem of the computer. If the operating system or another program reads the file of the infected program, then the virus substitutes the real, uninfected, program file. To do this, the resident virus module can temporarily remove the virus from the infected file. After working with the file, it becomes infected again.
Bootable stealth viruses act in the same way. When a program reads data from the boot sector, the real boot sector is substituted for the infected sector.
Masking stealth viruses only works if there is a virus resident module in the computer’s RAM. If the computer boots from a “clean”, not infected system diskette, the virus has no chance of getting control and therefore the stealth mechanism does not work.
Macro viruses
So far, we talked about viruses that live in executable files of programs and boot sectors of disks. The widespread distribution of the Microsoft Office suite of office programs has caused an avalanche-like appearance of a new type of virus that spreads not with programs, but with document files.
At first glance, this may seem impossible - in fact, where to hide viruses in Microsoft Word text documents or in Microsoft Excel spreadsheet cells?
However, in fact, Microsoft Office document files may contain small programs for processing these documents, compiled in the programming language Visual Basic for Applications. This applies not only to Word and Excel documents, but also to Access databases, as well as Power Point presentation files. Such programs are created using macros, so viruses that live in office documents are called macros.
How are macro viruses spread?
Together with document files. Users exchange files through floppy disks, network directories of corporate intranet file servers, via e-mail, and other channels. To infect a computer with a macro virus, simply open the document file in the appropriate office application - and the job is done!
Now, macro viruses are very common, which is largely due to the popularity of Microsoft Office. They can do no less harm, and in some cases even more, than "ordinary" viruses that infect executable files and boot sectors of disks and diskettes. The greatest danger of macro viruses, in our opinion, is that they can modify infected documents, undetected for a long time.
Currently, each user travels through the expanses of the network. On the Internet, a variety of threats can “attack” a user. Users should know as much information about spies as possible in order to protect themselves from them.
This kind of pest is allocated in a separate class of threats. This software allows some users to set up surveillance for others. In this case, it will be possible to view the actions of users without their knowledge.
Spies can sometimes be utilities, but more often they are viruses. These pests belong to the spyware class. The difference between one category and another is that spyware begins to activate only after installation.
Spyware can be like a narrow spectrum of action. That is, they are allocated to the number of screen and keyloggers. Comprehensive applications are also presented. Most often, this category of pests is used to monitor users and their actions.
Thus, the bosses can track all the manipulations of users. Parental controls may also be exercised. In general, a separate category of programs is incredibly useful in everyday life.
Features of virus spyware and programs
The variety of spyware utilities is great. Users may encounter a wide variety of elements that conduct surveillance. But still it is worth highlighting the distinguishing features of programs and viruses.
Quite often, antivirus programs block spyware, classifying them as malicious. However, these objects are not related to malware. But at the same time, they are blocked anyway.
What exactly is the difference between a real spyware pest and those services that are designed to conduct secret surveillance of a personal computer? The difference between these objects in the performance of work and scope.
Spyware viruses are independently downloaded to gadgets without user permission. That is, the user may not even be aware that pests have “settled” on his device. At the same time, they will commit various data thefts, copy files and damage documents. In general, pests behave accordingly.
Software spies, in turn, must be installed directly by the user. These programs are really helpers. They are needed in order to control other users.
Different types of spies. Keyboard typing control
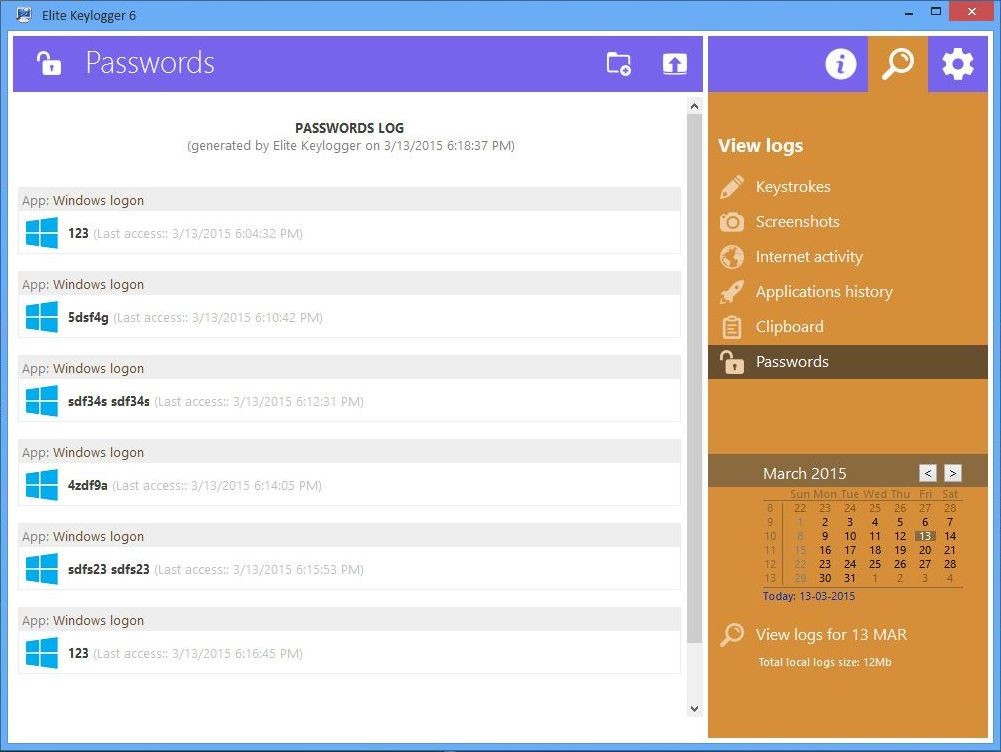
Each user may encounter such pests. But in some cases, users may not even be aware of this. The most dangerous type are keyloggers. It is these pests that are found much more often than all the others.
These objects can be specially built into the system for monitoring or it can be considered as an independent pest species. In their principle of operation, there is no particular difference.
Keyloggers are designed to monitor the actions that the user performs while working on a personal computer. Different keyloggers differ mainly according to the principle of actions. In some cases, they can only occasionally become active.
Moreover, these types of elements are often located on the hard drive.
In this case, the user may not even be aware that all of his passwords are successfully copied and transferred to third-party users. In the future, access to confidential information is provided, which is used by fraudsters at their discretion.
It is unlikely that spies simply "spy." They always copy information in order to further use it to realize their own goals. An attacker can hack someone else’s account, make adjustments to the settings, change the specified password and perform other manipulations in order to maximize damage to the account holder.
But since device administrators can install a spy, in this case these softwares will not be blocked. This is due to the fact that they are included in the exceptions. So they will not be perceived as threats.
Simple and very relevant spy
Users in the process of working on a PC could encounter SC-KeyLog. This: keylogger is free. But it is determined by the defenders installed on the device even at the time of loading such an object.
If the user has decided to install this software, then he can immediately add it to the list of utilities safe for the device. In this case, the antivirus program will not block the downloaded object.
Next, you will need to choose the place where the service file will be located in the future. After that, the executable file of the tracking module will be located on the previously indicated disk. As soon as the software installation is completed, users can already proceed to configure this service.
It is necessary to indicate the e-mail address on which data on the interception of information will be sent. When all the most important settings are implemented, the files of this service will be instantly added to the list of trusted antivirus programs. At this stage, all preparatory work is completed in full.
SC-KeyLog in the course of work displays the titles of all those windows that the user works with. Also, the utility fully controls all those actions that are performed on the keyboard. But there is one drawback: the inability to automatically switch layouts. So all texts are displayed exclusively in English letters.
Spies of a broader spectrum of action
Also, users may encounter complex pests. Although keyloggers are the most common, they are good only in cases where it is enough to know what exactly is entered on the keyboard and which utilities are launched.
But in some cases this information is not enough. Therefore, integrated software were created that work in the most difficult mode. They are used to conduct comprehensive espionage. These complex objects can be filled with several relevant components.
These include keyloggers, clipboard interceptors, spyware for tracking data displayed on the screen of the gadget. Also, users can use the built-in recorder launch and activity programs and much more.
Bright representatives of free complex spies
To evaluate the principle of operation of such kind of software products, it is necessary in practice to check their performance. For example, consider Softex Expert Home software. This is a free Russian-language system. This utility will instantly block a variety of keystrokes.
Detailed monitoring of running services is also carried out, as well as full control of their activity. All active user actions, work with their own accounts and much more are subject to verification.
But as well as in relation to other utilities of this direction, blocking is performed when loading this software. Installed antivirus programs instantly respond to the installation of such an application and take it as a threat. For this reason, blocking is the first thing the defenders do.
Therefore, it will be necessary to disable the operation of the antivirus. As soon as the installation of the selected service is completed, we again activate the defender. During the installation of the spy, you will need to specify a key combination, when pressed, the interface will be called.
You should also set a password that will open access to data collected during the operation of this software. After installation, the spy will need to be moved to a list with positive services whose actions should not be blocked.
Softex Expert Home can function not only in the usual, but also in the stationary mode. however, shortcuts and other program attributes will not be created on the screen. Pressing previously selected keys will immediately load the main software window.
In the window that appears, the secret key is indicated, and after that you will need to go to the settings section. We make adjustments to important parameters. The users of this service for spying on a home PC is enough.
Another free comprehensive program is Refog Free Keylogger. A simple interface will certainly delight users. This software helps to intercept correspondence in installed messengers, monitors social networks.
In general, the utility "knows how" to produce a huge number of very different actions using the standard Explorer. The application controls the entire operating system and all changes made to it. During operation, the utility can be blocked by an antivirus if necessary heuristic algorithms are used.
The main disadvantage of the free version is some limitations. This is due to some aspects of the surveillance. The rest of the failures are not observed.
Also, users can install this kind of spyware on mobile devices. On the network you can find several relevant helpers of such a plan. A prominent representative is the KidLogger utility. This is a very relevant multi-platform surveillance software.
Insidious traffic analyzers
Thanks to these types of applications, attackers connect to a session on the network. Moreover, they can perform all manipulations on behalf of the user.
Fraudsters can use all passwords, log on to various accounts and other sites.
For this reason, it is extremely important to encrypt traffic. Most of all, the threat falls on users who decide to work with public networks.
NirSoft SmartSniff is a classic representative of sniffers. This service helps to intercept data that fraudsters can steal. The utility also aims to debug the network.
But since users increasingly prefer to work on stationary devices, then for this category of devices software of this type is provided. For Android, WireShark Shark for Root is suitable.
Thanks to this service, fraudsters manage to steal data directly from a mobile phone. It is enough to connect a smartphone or tablet to a public access point.
Pest control. Countermeasures
Each user must certainly fight with spies. If you know the principle of their action, then it will be possible to choose the most relevant ways to eliminate this type of pest. Of course, users can independently monitor the actions on the devices, but this can be done with good intentions.
If the scammers try to infiltrate the device to obtain data that is confidential, in order to further use it. It is difficult to counteract spies, but this is a very feasible task.
The first thing to do is update the anti-virus database. You will also need to check all the objects that are in the white list of the defender. It is important to make sure that there are no suspicious objects in it.
Users must not work with simple antiviruses. The best in this category are AdwCleaner and AVZ. These software products are among the most frequently used to block threats of various types.
AnVir Task Manager can also help. A feature of the functioning of the application is that it is aimed at determining the names and addresses of all running processes. Moreover, the degree of harm that can be caused to the system is determined with accuracy. These utilities are reliable in quickly disabling even sniffers.
Virus classification
Currently, there is no single system for the classification and naming of viruses (although an attempt was made to create a standard at the CARO meeting in 1991). It is customary to share viruses:
· On affected objects (file viruses, boot viruses, scenario viruses, macro viruses, viruses that infect the source code):
· For affected operating systems and platforms (DOS, Windows, Unix, Linux, Android);
· By technologies used by the virus (polymorphic viruses, stealth viruses, rootkits);
· By the language in which the virus is written (assembler, high-level programming language, script language, etc.);
· For additional malicious functionality (backdoors, keyloggers, spies, botnets, etc.).
In most detail we will consider spyware viruses.
Spy Viruses
Spyware (spyware, spyware) - a program that is covertly installed on a computer in order to collect information about the configuration of the computer, user, user activity without the consent of the latter. Other actions can also be performed: changing settings, installing programs without the knowledge of the user, redirecting user actions
Spyware can carry out a wide range of tasks, for example:
· Collect information about Internet usage habits and the most frequently visited sites (tracking program);
· Memorize keystrokes on the keyboard (keyloggers) and record screenshots of the screen (screen scraper) and subsequently send information to the creator of spyware;
· Unauthorized and remote control of a computer (remote control software) - backdoors, botnets, droneware;
· Install additional programs on the user's computer;
· Used for unauthorized analysis of security systems (security analysis software) - port and vulnerability scanners and password crackers;
· Change the parameters of the operating system (system modifying software) - rootkits, control hooks (hijackers), etc. - resulting in a decrease in Internet connection speed or loss of connection as such, opening other home pages or removing certain programs;
· Redirect browser activity, which entails visiting websites blindly with the risk of virus infection.
1.3.1 Types of Spyware Viruses
By Kind of activity, Spy Viruses can be divided into three groups:
First group
The virus constantly monitors user actions. When making purchases over the Internet, the spy will receive credit card information and pass it on to interested parties. You may not notice this until an unauthorized debit of funds from your account occurs.
Second group
Third group
The virus receives information about your email inboxes. This poses a multitude of problems, the smallest of which is an avalanche of spam, junk and advertising emails that hit you.
There is also a specific mechanism for the spread of the virus.
1.3.2 Propagation mechanism
Viruses they spread by copying their body and ensuring its subsequent execution: introducing themselves into the executable code of other programs, replacing other programs with themselves, registering in autorun, and more. The virus or its carrier can be not only programs containing machine code, but also any information containing automatically executed commands - for example, batch files and Microsoft Word and Excel documents containing macros. In addition, to infiltrate a computer, a virus can exploit vulnerabilities in popular software (for example, Adobe Flash, Internet Explorer, Outlook), for which distributors embed it in ordinary data (pictures, texts, etc.) along with an exploit that uses vulnerability.
· Floppy disks. The most common infection channel in the 1980-1990s. Now it’s practically absent due to the emergence of more common and effective channels and the lack of floppy drives on many modern computers.
· Flash drives (flash drives). Currently, USB sticks replace floppy disks and repeat their fate - a large number of viruses spread through removable drives, including digital cameras, digital video cameras, portable digital players, and since the 2000s, mobile phones, especially smartphones, have played an increasing role mobile viruses). The use of this channel was previously mainly due to the possibility of creating a special file autorun.inf on the drive, in which you can specify the program that Windows Explorer launches when such a drive is opened. In Windows 7, the ability to autorun files from portable media has been disabled.
· Email. Usually viruses in e-mails are disguised as harmless attachments: pictures, documents, music, links to sites. Some letters can really contain only links, that is, the letters themselves may not contain malicious code, but if you open such a link, you can get to a specially created website containing virus code. Many mail viruses, once on the user's computer, then use the address book from installed mail clients such as Outlook to send themselves further.
· Instant messaging systems. Distribution of links to allegedly photos, music or programs that are actually viruses, via ICQ and other instant messaging programs, is also common here.
· Web pages. It is also possible infection through Internet pages due to the presence on the World Wide Web pages of various "active" content: scripts, ActiveX-component. In this case, vulnerabilities are used in the software installed on the user's computer, or vulnerabilities in the software of the site owner (which is more dangerous, since good sites with a large flow of visitors are infected), and unsuspecting users who visit such a site run the risk of infecting their computer .
· Internet and local area networks (worms). Worms are a type of virus that infect a victim computer without user intervention. Worms use so-called “holes” (vulnerabilities) in operating system software to infiltrate a computer. Vulnerabilities are errors and flaws in the software that allow you to remotely download and execute machine code, as a result of which the worm virus enters the operating system and, as a rule, initiates actions to infect other computers via the local network or the Internet. Attackers use infected computers of users to send spam or for DDoS attacks.
The beginning of the 21st century can definitely be called the beginning of a real, genuine information age. A few years ago, most people were amazed at how widespread the so-called “computers” were. Amazing stories and urban legends about hackers capable of stealing millions of dollars, decent salaries of metropolitan programmers working in large corporations - all this, of course, no longer surprises the average man as much, but clearly illustrates the power of computer technology and those who are well versed in this . The field of information technology has grown so much that it has become one of the key elements of basic logistics for many enterprises.
But along with new useful features, along with new conveniences and ways to send and process data, new ways of stealing them appeared. In the information space this problem will always exist. The most famous information space available to almost anyone without exception is the Internet. And the opportunities that he offers, the prospects that open up to any visitor to the World Wide Web, are fraught with many openly dangerous and terrible things. The Internet, as many people believe, is not just one search engine, and not millions of sites that you can just pick up and find. The visible part of this network is just the surface of the ocean, and you can safely give a guarantee that most living people should not even try to dive deeper. This is fraught with at least criminal liability.
However, there are more commonplace things, for example, viruses. They were created over the past 20 years, very, very many. Without jokes and exaggerations, we can say that their number is growing every minute. Speaking of criminal liability, punishment is provided for by law.
One type of computer virus is spyware viruses. Their name corresponds to their activities: being in the active system in the operating system, they collect information from the user's computer and send it to the attacker who created the virus.
Many will ask: "what information?" The answer is quite simple. Many people use payment systems, work with a bank account on their computer, make any transactions, order something in online stores.
All this is interesting to those who create such software. Any information on the Internet has a price. By stealing an email address, an attacker can add it to the spam mailing list. Having received the password for this email, he can read any letters that come there, including registration data and personal data. Access to an electronic wallet means that an attacker can manage the finances of his victim, and so on and so forth. As you can see, even on computers people have something to steal. Therefore, it is not worth doubting the danger of spyware viruses.
What can be done to protect yourself from spyware:
- Get an antivirus. The most banal, easiest and most reliable way. Despite his triviality, he has almost undeniable advantages over everyone else. Before starting new files, the antivirus always checks them, automatically blocks them in case of a threat, and allows the user to check the computer for viruses at any time.
- Be more attentive. Again, banal advice, but quite effective. It is simple to impossibility - do not download anything horrible, do not install cheap programs that promise mountains of gold or the solution to all problems in the world. Free cheese happens only in one place, and rodents, not people, should get there.
- Improve your computer literacy. This is not an easy task, especially for those who do not get along well with computers. However, it is worth remembering that every year computerization covers more and more areas of our lives. The better each of us will begin to understand how electronic computers work, the safer we will feel. This advice, however, applies not only to computers, but to everything else. Times are such that “being able to do something” is gradually becoming a thing of the past, and in its place is becoming “able to learn how to do something”. Technology is developing too fast to get used to it. One and the same way to perform a task inevitably becomes obsolete, and at a breakneck pace. In order to truly protect yourself, your information, and the chances of success in life, you need to learn to find ways, and not learn the ways themselves.
- Clean your computer of important information. Unlike the previous tip, everything is simple. Every day, delete the browsing history in the browser, do not save passwords, do not remain logged in to the sites of banks and payment systems. Thus, stealing information will be more difficult, because most of the time it will not be on the computer itself.
The simplest precautions can preserve savings, confidential correspondence and important information. They simply should not be neglected. After all, there is nothing complicated in installing any free antivirus on your computer, no. Even if you just do this, then the probability of “getting into trouble" is reduced several times.