In modern smartphones, an incredibly many ways to protect personal data from prying eyes have been introduced - this is a graphic password, and a digital one, a password from characters, or even a fingerprint scanner in some phone models. If you have forgotten your password, you can use some methods to unlock any Xiaomi device: Xiaomi Redmi 4 Pro, Xiaomi Mi5, Redmi Note 3, Xiaomi Mi Max, Xiaomi Redmi Note 4 or Mi4 Plus. We recommend unlocking with these methods only in order to access your smartphone, and not someone else's.
If your gadget is locked, then you will most likely try to enter the password more than once, hoping that this time you will guess for sure. But repeatedly entering the wrong password leads to the fact that the device is locked for a while, and the more often you enter the wrong password, the longer the phone remains locked. In addition, problems often arise due to the fact that it is impossible to use the fingerprint scanner - the user relaxes and forgets the pattern.
To date, there are at least three proven ways to unlock the device - each user resets the password the way he likes best. They differ not only in their essence, but also in several nuances that are associated with different firmware versions. For example, in MIUI 7 there is a password reset function by pressing the standard button "Forgot your password?”, but in MIUI 8 this button is no longer there, so you need to deal with the removal of the lock a little longer. Let's look at the main methods for solving the above problem. 
Give gifts
Standard way
- If incorrect (incorrect password or pattern entry) on Redmi, you will see a standard message stating that the smartphone is locked. Therefore, the one who removes the lock must press the button "Forgot your password?" at the bottom of the screen, after which it will be transferred to the page for unlocking through Mi or Google accounts. Here you need to enter authorization data (login and password) and log in to your account. Done - now you can remove pattern keys, change the device lock method or change the password to a new, more memorable one.
- If your firmware version is higher than 7th, then click on the button "Forgot your password" you can't - it just doesn't exist. In this case, remove the lock using one of the methods described below (these methods also work for combinations of numbers or symbols).

Through the recovery
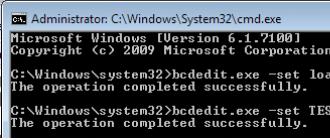
Graphical unlocking, according to this method, is carried out through a complete reset of all phone settings to the original ones through the Recovery menu. In some models, such as Xiaomi Mi Max, it is available immediately after purchasing the phone, but most often you will need to ask Xiaomi for permission to unlock the bootloader.
Compliance with all conditions will delete personal data from the phone and completely reset the settings to factory settings, so we recommend that you first remove the memory card from your smartphone. Next, follow these steps:
- Turn off your phone. Simultaneously press the power button and the volume key up;
- If the bootloader is unlocked, the Recovery menu will open on the phone;
- From the menu that appears, select Wipe & Reset» — Wipe all data. This action will reset all settings and delete data on the device;
- The smartphone will reboot, after that the phone will be clean, like “out of the box” - there will be no more graphic lock.

If the smartphone annoys you with the presence of any other shortcomings, and not just a forgotten graphic password, you can reflash the phone through the laptop and the utility. You can also remove the pattern in this way, however, we will consider this topic in more detail in a separate article, since flashing the device is much more difficult and time consuming than simply removing the pattern on Xiaomi.
How to remove the password through the phone finder
If you have not removed the blocking using the methods described above, try doing this through Google services. To do this, log in to your smartphone settings through your Google account. Then, on any Android device, go to it, enter Google Play and install the free official application for remote device control - Find My Device. Next, select your device in the window, after which the program will be remotely installed on the locked smartphone.

After installing the application, go to the tab "Device Management" and enter your google account password. Then select the locked phone in the list and turn on the clear function, so we reset the password at the same time. After performing this operation, all user data will be deleted from the phone, and the settings will be reset to factory settings. Therefore, we advise you to remove the SIM card and memory card from the device before unlocking in this way.
How to turn off the password restriction
Sometimes it happens that after the child has played with the gadget and entered the wrong password several times, for some time no one will remove the block - the smartphone is blocked for a while. Sometimes this time can take up to several days - agree, you don’t want to wait for unlocking for so long.

The easiest way to solve this problem is to unlock it by calling. To do this, call from someone else's phone to your own, accept the call and minimize the conversation window. You will be able to control the device until the call is completed. To do this, go to settings and uncheck the box. "graphic password", then enter the correct combination and press "OK". Done, old passwords reset! This method will only work if you remember the correct password, or someone accidentally blocked your phone.
conclusions
The conclusions can be drawn quite simple - if the question arose “how to reset the lock”, then it is very easy to get an answer to it. If your smartphone is running MIUI 7 firmware, then you can easily unlock your phone using the button "Forgot your password", and on newer phones, you will have to make a little more effort - you need the owner of the gadget to first unlock the bootloader.
When working with money in the HYIP industry, special attention must be paid to the security of personal data and information. Next in importance after installing a firewall and antivirus is choosing, creating and storing your passwords. It's no secret that all privacy in the world of the Internet and computers is based on authorized access. When investing in HYIPs, you will have to create, invent and store a lot of passwords. Therefore, the quality of protection of your personal data will depend on what passwords you use and how you store them. In this article, we will analyze the basics of security in HYIP projects and show you how to correctly choose and store your passwords securely.
Basic rules for choosing and creating passwords wisely

How to store and not lose passwords
 Surely, you have lost or forgotten your logins, passwords from payment systems, mail or accounts more than once. At the same time, you spent a lot of time to find or restore information. In order not to store passwords from many projects, payment systems and forums in your head or in a txt document, you can use the special manager KeePassX. This is a free program designed to store passwords. The downloaded and installed file is securely encrypted, takes several kilobytes and can be opened on any computer where the software is installed.
Surely, you have lost or forgotten your logins, passwords from payment systems, mail or accounts more than once. At the same time, you spent a lot of time to find or restore information. In order not to store passwords from many projects, payment systems and forums in your head or in a txt document, you can use the special manager KeePassX. This is a free program designed to store passwords. The downloaded and installed file is securely encrypted, takes several kilobytes and can be opened on any computer where the software is installed.
Greetings to everyone who watches this video!
This is not my first article, but in the field of user education not to do stupid things, the first.
In this video and the text of the article, I will tell and show what should and should not be done when entering a password, or choosing it.
Passwords are different, someone keeps them in his head, someone writes them down on a piece of paper, someone in text documents.
Keeping passwords in your head means the following:
passwords will be:
1. small length;
2. the same on different resources,
and therefore if you register at the mail, and then in the chat, then the person after the chat is hacked will have access to your mail, which is not good ...
store passwords on paper, the same is not an option, although it is better than the first, but since we are moving away even from books on paper,
electronic media, I suggest storing passwords in text form.
This method also has disadvantages as well as advantages.
Disadvantage: an attacker gaining access to your password file will know all the resources and can gain access on your behalf.
Advantages: getting access to resources (third-party is more difficult) since you can create complex passwords and not be afraid to forget them
You can improve this method by remembering 1 complex 10 digit password or more,
and just use it to decrypt a password-protected archive with passwords.
I'll show you later...
And now I'll show you how difficult it can be to decrypt a normal password.
At present, quite a lot of encryption algorithms have been invented. The most popular in my opinion is MD5 and its modifications.
Let's take, for example, different passwords and their hashes, and try to decrypt, and clearly see how long it will take.
And so, now we will decipher and look at the time ...
first we will use only numbers, and then increase the complexity ...
Fractions of a second...
The same…
The same, but we know that the password contains only numbers, and if it contained signs, it would take much more time ...
Next password...
The password was not found by numbers ... let's connect the characters ... lowercase ...
added 1 character (not a number and that's how it made the process more difficult)
On a rather not weak machine, a password of 8 characters using upper and lower case letters will take a very, very long time to decrypt, and this is provided that MD5 is not modified ...
It’s a pity that not every site / service / server can use additional characters ...
Attention to the screen, that's how they use them would complicate the process of direct enumeration ...
With their use, the password is practically not vulnerable, unless, of course, supercomputers are used to decrypt it.
And as promised, I show how you can store passwords for accessing resources knowing one password:
Of course, such a password is difficult to remember, so we will simplify it a bit ... a little later
w1W4W5a$4PYi
By using this password, your passwords will be safe.
You can shorten it, as I said, to 10 characters ... Well, or so ...
It’s easier to remember, in fact, like hacking, but I don’t think that your passwords will be hacked on purpose
Oh, and the name of the file "Passwords" will attract attention, so change the name to something less catchy ...
That's actually all!
Article author
Elizaveta Kompaniets, student of MBOU secondary school No. 28, 11th grade A
Goals
What is the password history?
How do passwords protect data on computers and drives?
How do hackers crack passwords?
How to make a password resistant to cracking?
Hypothesis
The password is the most accepted and therefore the most commonly used means of authentication based on the knowledge of the accessing subjects.
Data protection using a computer
Password history
Password(French parole - word) is a secret word or set of characters designed to confirm identity or authority. Passwords are often used to protect information from unauthorized access. In most computing systems, a username-password combination is used to authenticate a user. Passwords have been used since ancient times.
Polybius describes the use of passwords in ancient Rome as follows:
The way they ensure safe passage at night is as follows: from ten maniples of each branch of infantry and cavalry, which is located at the bottom of the street, the commander chooses who is exempt from guard duty, and he goes every night to the tribune, and receives from his password - a wooden tablet with the word. He returns to his unit, and then passes with a password and a sign to the next commander, who in turn passes the sign to the next.
Passwords are used to prevent unauthorized access to data stored on the computer. The computer allows access to its resources only to those users who are registered and have entered the correct password. Each specific user may be allowed access only to certain information resources. In this case, all unauthorized access attempts can be logged.
Computer access protection.
Protection of user settings is available in the operating system Windows (when the system boots, the user must enter his password), but this protection is easily overcome, since the user can refuse to enter a password. Password login can be set in the program BIOS Setup , the computer will not start loading the operating system unless the correct password is entered. It is not easy to overcome such protection, moreover, there will be serious data access problems if the user forgets this password.
Disk data protection.
Each disk, folder and file of the local computer, as well as a computer connected to the local network, can be protected from unauthorized access. Certain access rights can be set for them (full, read only, by password), and the rights can be different for different users.
Cracking computer passwords
Password cracking is one of the common types of attacks on information systems that use password or username-password authentication. The essence of the attack is reduced to the intruder taking possession of the password of a user who has the right to enter the system. The attractiveness of the attack for an attacker is that if he successfully obtains a password, he is guaranteed to receive all the rights of the user whose account has been compromised, and in addition, logging in under an existing account usually causes less suspicion among system administrators. Technically, the attack can be implemented in two ways: by multiple attempts of direct authentication in the system, or by analyzing password hashes obtained in another way, for example, by intercepting traffic. In this case, the following approaches can be used:
Direct override. Enumeration of all possible combinations of characters allowed in the password. For example, the password “qwerty” is often cracked, since it is very easy to pick it up by the first keys on the keyboard.
Dictionary selection. The method is based on the assumption that the password uses existing words of any language or their combinations.
Method of social engineering. Based on the assumption that the user used personal information as a password, such as his first or last name, date of birth, etc. Eg. Vasya Pupkin, born December 31, 1999 often has a password like "vp31121999" or "vp991231". Many tools have been developed to carry out the attack, for example, John the Ripper.

Password strength criteria
Based on the approaches to conducting an attack, it is possible to formulate criteria for the strength of a password to it. The password should not be too short, as this makes it easier to brute-force it. The most common minimum length is eight characters. For the same reason, it should not consist of only numbers.
The password should not be a dictionary word or a simple combination of them, this simplifies its selection from a dictionary.
The password should not consist only of public information about the user.
As a recommendation for compiling a password, one can name the use of a combination of words with numbers and special characters (#, $, *, etc.), the use of rare or non-existent words, and the observance of the minimum length.
Conclusion
Passwords have been in use since the early days of their creation to this day. They successfully help us protect information from unauthorized access.
In today's world, more and more personal data gets on the Internet. Among them are various financial services and applications. This data must be under reliable protection.
You yourself protect your own data using various passwords, on which the security of various accounts depends. So how do you make your password easy to remember and hard to crack?
Common Mistakes
Many users around the world do not pay much attention when choosing a secure password, due to which they become victims of Internet scammers who hack into their accounts in 5-6 attempts. For many years, users have been using the simplest combinations - 1234567, 12345554321, 1q2w3e4r5t6y - thereby exposing themselves to the threat of hacking.
Most cybersecurity experts point to two main criteria for a secure password - complexity and length. In their opinion, when creating a password, you need to use a long combination using various characters - numbers, letters, symbols, punctuation marks.
How to create passwords correctly
- Use more than 8 characters
- For each account, use your own unique password, because if you use the same password on all accounts, if one of them is hacked, the fraudster will be able to open other accounts as well
- Passwords should be changed periodically - at least once every 3 months. To do this, set an automatic reminder so as not to forget about such an important procedure.
- A variety of characters in a password is a guarantee of reliability. But do not use the recent replacements of letters with numbers or symbols, for example, "FOR" with "4".
- Use the full range of characters available on the keyboard
Also, do not forget - passwords must be stored in a place to which only you have access.
As much as possible, avoid using in creating passwords:
- Vocabulary words in any language
- Repetitions or characters placed consecutively one after another. For example: 1234567, 55555, abc where, etc.
- Passwords using personal data: full name, date of birth, serial numbers of documents, and so on.
In general, take password creation very seriously, as your financial well-being or reputation may depend on what they protect.